Executive Summary
This report discusses cloud computing and information security in the area of information management and control. Information management is introduced and its risk to an enterprise is assessed and additionally, to provide more elaboration the ePrescribing system is provided as a case study.
This report concludes that in an enterprise, the information environment and information assets have to ensure that the confidentiality, integrity and availability of the enterprise’s information are safeguarded.
Introduction
In enterprises, risk management is an activity that is undertaken to lessen to acceptable levels the effects of risks. Three processes constitute risk management in an enterprise. The first process is known as risk assessment in which risk and risk impacts are identified and evaluated and also measures for reducing risks are recommended (Stoneburner, 2002, 8). The second process in enterprise risk management is risk mitigation in which the measures for reducing risks, recommended in the risk assessment process, are prioritized, implemented and maintained (Stoneburner, 2002, 8).
The third process in enterprise risk management is evaluation and assessment in which an enterprise’s risk management program is evaluated and assessed continually because changes in the enterprise are inevitable and that these changes can compromise the effectiveness of the enterprise’s risk management program (Stoneburner, 2002, 8). In enterprises, one risk that is of concern is the information technology risk (or information risk), which is associated with information systems that are the means of managing information in them.
The article “Why do organizations need information systems?” describes information as the lifeblood of an enterprise (Answers Corporation, 2011, 2). The article additionally points out that an enterprise that poorly manages its information attracts financial losses and liabilities such as lawsuits (Answers Corporation, 2011, 2). An enterprise’s information can be either physical or electronic and in most cases, it is both of these. In an enterprise, information management concerns itself with how to collect and manage information at its source and how to distribute it to the relevant audience.
Information management in enterprises is implemented using systems known as information systems whose main objective is to monitor as well as log the operations of other fundamental systems in these enterprises (Answers Corporation, 2011, 2). Typically, the main components of an information system are a central data repository e.g. a database and allied infrastructure. An example of information stored in an information system is detailed on an enterprise’s clients. The design of an information system has to take into account certain ethical issues; otherwise, the information system becomes a risk to an enterprise.
Cloud computing is another form of technology that is picking up in enterprises which is such that the enterprise’s information is posted on the web. In as much as it is a benefit e.g., it adds more flexibility to the information operations of an organization it is associated with risks that are discussed in the later sections of this paper. Cloud computing is computing technology that is developed to function on the internet or intranet of an enterprise and it can thus, therefore, be termed as an internet or intranet resource.
Discussion
Research
Sajjad et al (2010, 3080). in the article “Risk perception and adoption of technology: An empirical study of personal computer use for Pakistani managers” identifies information risk as an enterprise problem as it adversely affects the performance of enterprise members. In the article “Perceived risk of information security and privacy in online shopping: A study of environmentally sustainable products ” Tsai and Yeh (2010, 4057) identify information risk as a problem noting that it compromises the integrity of an enterprises information a situation which leads to poor turnover due to low sales. In the article “The challenge of risk management in Nigerian banks in the post-consolidation era” Owojori et al (2011, 24) identifies information risk as an enterprise problem (2011, 24). Owojori et al (2011, 24) points out that the risk is most likely to occur in any enterprise that adopts information technology and that it is controllable.
Moorthy et al (2011, 3526) identifies information risk as a problem in the article “The impact of information technology on internal auditing”. Moorthy et al (2011, 3526) points out that in as much as information systems have increased productivity in enterprises they have among other things been associated with data losses, which have a detrimental effect on enterprise earnings. In the article “Framework to identify and manage risks in Web 2.0 applications” Rudman identifies information risk as a problem in enterprises (Rudman, 2010, 3251).
Rudman points out that innovations in IT bring with them newer threats and newer ways to effect the threats that compromise the confidentiality, integrity, and availability of the enterprise’s information (2010 3251). Elky (2009, 1) in the article “An introduction to information system risk management” and Stoneburner et al (2002, 4) in the article “Risk Management Guide for Information Technology Systems” also identify information risk as an enterprise problem.
Alanazi et al (2010, 2065) in the article “Securing electronic medical records transmissions over unsecured communications: An overview for better medical governance ”identifies information risk as an enterprise problem noting that enterprise information systems should guarantee information disclosure and privacy. In the article “Sustainable economic development: A perspective from ICT loops in developing nations” Low et al identifies cybersecurity as an enterprise problem noting that it has the potential to paralyze the cyber-based operations of an enterprise. In the article “The genetic algorithm to management measures of information security systems” Wang and Wan not only identify information security as a problem but propose a novel genetic algorithm that is effective in managing information security (2011, 2934).
Risk Assessment
In enterprises, information risk management is a risk management activity that is undertaken to manage the risk associated with its information assets and information environment. Information security in an enterprise is a key issue in information risk management this is because the information environment and information assets of an enterprise have to ensure that the confidentiality, integrity, and availability of the enterprise’s information are safeguarded. In the risk assessment stage of information risk management, certain elements of information security have to be taken into account.
One element is identifying the vulnerabilities of a given information asset. A vulnerability concerning information security is a weakness present in an information asset which if exploited causes harm to it with the resultant effect of compromising the confidentiality, integrity, and availability of the enterprise’s information (ISACA, 2006, 85). Another element of information security that is taken into account in the risk assessment stage of information risk management is identifying the threats to the information assets. A threat can be artificial or not and can be situated inside or outside an enterprise’s information environment. A threat to an enterprise’s information asset is an object that has the potential to damage an information resource (ISACA, 2006, 85).
Another element of information security that is taken into account in the risk assessment stage of information risk management is identifying the threat-sources concerning the information assets. A threat-source as the name suggests is in information risk management is the source of a threat and this according to Elky (2007, 2) can take the form of a situation, intent or method. It is worth noting that a threat without a threat source is dormant and therefore is not harmful to an enterprise’s information asset (Elky, 2007, 2). To elaborate further on these information security key elements we introduce an e-health system case study and from it deduce its vulnerabilities, threats, and threat-sources.
Case study
The case study is the Swedish ePrescribing system that is a joint effort between the country’s county councils and Apoteket, which is the country’s national pharmacy (European Commission Information Society and Media, 2006, 2). The beneficiaries of the ePrescribing system are Swedes and the country’s health provider organizations. The system operates in two modes. In the first mode, a prescription is effected using Sjunet, an extranet, which is the country’s ICT healthcare network (European Commission Information Society and Media, 2006, 1). The second mode and which is not as frequently used, a prescription is effected using a secure web-based application (European Commission Information Society and Media, 2006, 1).
The benefits provided by the ePrescribing system to Swedes are increased awareness and knowledge of prescriptions, increased patient safety and greater flexibility in the acquisition of medicine (European Commission Information Society and Media, 2006, 2). The benefits provided by the ePrescribing system to Swedish health provider organizations are reduced illegible and duplicate prescriptions, improved knowledge on patient prescriptions, time-saving and lessened risk of fraud and falsification of prescriptions. According to the European Commission Information Society and Media (2006, 1), 42% of all prescriptions in Sweden are done using the ePrescribing system.
Case study discussion
From this case study, the information assets include Sjunet, the secure web-based application and the systems allied infrastructure. The information environment is the country, Sweden. Possible vulnerabilities to this system include poor choice of cryptography keys and message encryption algorithms and poor layout of the system’s allied infrastructure. A possible threat and threat-source to this system are acts of Nature such as earthquakes, floods, hurricanes, infernos and tornadoes that can damage the infrastructure of the system. Another possible threat and threat-source is an alteration of the system’s software through malicious codes such as Trojan horses, viruses, worms, logic bombs, etc. Targeted software in this thread is either the operating system or application programs that make up the ePrescribing system. The alteration involves modification, insertion, and deletion of this software.
Cloud computing
Using the ePrescribing system as an example and in particular, the fact that one of its modes of operations is web-based it is clear that health enterprises are adopting cloud computing as a future investment. In cloud computing these enterprises post their sensitive information on the web and as such are exposed to three main risks, namely, information security, e-discovery and computer forensics (techtarget.com, 2009, 1). By having this information on the web it becomes a challenge to monitor who is accessing information, what information is accessed and what alterations, if any, have been made to it and thus, the information security risk (techtarget.com, 2009, 2).
E-discovery exposes such enterprises to risk as it assumes that such enterprises have visible storage and backup processes but this is not the case and hence comprehension of the enterprise data becomes an issue at certain times a, state which can lead to leakage of the enterprise’s sensitive information (techtarget.com, 2009, 3). Computer forensics is useful in giving certain needed information on a computer resource e.g. when it was accessed and by who. With cloud computing, this is almost impossible as when the resource is uploaded to the cloud its trace is lost and thus no examination is possible hence the computer forensic risk (techtarget.com, 2009, 4).
Enhancing security in cloud computing is enhancing an enterprise’s internet or intranet security since, as mentioned above, cloud computing is an internet or intranet resource. In the face of attackers, cryptography boosts cloud computing security by ensuring the secrecy and integrity of information through encryption and decryption of messages by authorized principals who themselves are not a security threat (Coulouris et al, 2005, 276).
Another security defense against cloud-based attacks is credentials, which is a collection of evidence presented by one principle to another when the former is requesting for an internet resource (Coulouris et al, 2005, 284). Another security defense against cloud-based attacks is firewalls, which monitor and regulate communication in and out of a computer on the internet or an intranet (Coulouris et al, 2005, 109)certificates. The credentials of a given principle regulate or dictate the allocation of internet resources to the principle and thus in this way, credentials boost internet security.
Risk Assessment Methodology
In enterprise risk management the first process is risk assessment in which risk and risk impacts are identified and evaluated and also measures for reducing risks are recommended. A risk in enterprise risk management is the likelihood that an event will actuate that will hurt an organizational information asset (Elky, 2007, 1). Risk impact, on the other hand, refers to the magnitude of damage a risk can cause (Stoneburner et al, 2002, 8). Risk Assessment Methodology is the methodology applied in enterprise risk management and constitutes of nine activities (steps). These activities (steps) are shown in the risk methodology flow chart in figure 1 in appendix A. The inputs and resulting outputs of the activities are shown in table 1 in appendix A.
From the eHealth case study above, potential risks to the system have been identified as information security, e-discovery, and computer forensics. The risk impact, in extreme cases, can result in a shutdown of the system since it is no longer able to safeguard the confidentiality, integrity, and availability of its information, which is a basic requirement for it. Of the above-mentioned risks, information security is a high-level risk because its impact is costly to deal with and its threats and vulnerabilities (e.g. alteration of software) are difficult to deal with and are more likely to occur frequently compared to e-discovery and computer forensics risks, which are relatively low-level risks. Information security threats are costly and difficult to deal with because as technology advances the landscape of information security changes in tandem and these changes bring with them newer threats and vulnerabilities prompting enterprises to continually invest more and more on risk mitigation measures.
Communication of the risk
Communication of the risk is done through the risk assessment report, which is the output of the last activity in the risk assessment methodology (result documentation). A content of the risk assessment report is a description of the threats and vulnerabilities associated with an enterprise’s information asset or information environment (Stoneburner et al, 2002, 26). Other contents of the risk assessment report are a measurement of the enterprise’s information risk and recommendations on how to implement controls. The risk assessment report is presented to the senior management of an enterprise as a tool to aid in better decision-making on enterprise policy, budget, procedures and system changes concerning management and operations (Stoneburner et al, 2002, 26).
Recommendations
This report recommends that, as the business environment keeps changing enterprises should regularly do an information risk assessment owing to the fact the changes bring with them newer vulnerabilities and threats, which might compromise the effectiveness of their current risk management plan. Also, this report is of the recommendation that the findings and recommendations captured in the risk assessment report should be treated with the importance they deserve and enterprises should hasten to implement the recommendations made therein to avoid any financial losses or liabilities such as lawsuits. Another recommendation is that health enterprises and other enterprises that are using cloud computing technology need to invest more in information security measures targeted on monitoring and regulating access to information and communication channels.
Conclusion
In an enterprise, the information environment and information assets have to ensure that the confidentiality, integrity, and availability of the enterprise’s information are safeguarded. Naturally, in an enterprise information security cannot be fully guaranteed because an enterprise’s business environment is ever-changing and the enterprises have to change in tandem. Thus, an enterprise as to review its risk management plan as often as possible to ensure that it is not obsolete and useless in the face of new vulnerabilities, threats, and threat-sources.
References
Alanazi1, O. H., Jalab, H. A., Alam, G. M., Zaidan, B. B., & Zaidan, A. A. (2010). Securing electronic medical records transmissions over unsecured communications: An overview for better medical governance. Journal of Medicinal Plants Research Vol. 4(19). Web.
Answers Corporation. ( 2011). “Why do organizations need information systems?”.
Coulouris, G. Dollimore, J. And Kindberg, T. ( 2005). Distributed systems concepts and design. (4th ed.). Pearson Education Limited: England.
Elky , S. (2007). An introduction to information system risk management.
European Commission Information Society and Media. (2006). Apoteket and Stockholm County Council, Sweden – eRecept, an ePrescribing application. Web.
ISACA (2006) CISA review manual (2006). Information systems audit and control association.
Low, K. L., Lim, C. S. & Samudhram, A. (2011). Sustainable economic development: A perspective from ICT loops in developing nations. African Journal of Business Management, 5(15). Web.
Moorthy M. K., Seetharaman, Mohamed, A. Z., Gopalan, M., & Sans, L. H.(2011). The impact of information technology on internal auditing. African Journal of Business Management, 5(9). Web.
Owojori, A. A., Akintoye I. R. & Adidu F. A. (2011). The challenge of risk management in Nigerian banks in the post consolidation era. Journal of Accounting and Taxation, 3(2). Web.
Rudman, J.R. (2010). Framework to identify and manage risks in Web 2.0 applications. African Journal of Business Management, 4(13). Web.
Sajjad, M., Humayoun, A. A. & Khan, Z. (2010). Risk perception and adoption of technology: An empirical study of personal computer use for Pakistani managers. African Journal of Business Management, 4(14). Web.
Stoneburner, G., Goguen, A. & Feringa A. (2002). Risk Management Guide for Information Technology Systems.
Techtarget.com. (2009). Three cloud computing risks to consider. Web.
Tsai, Y. C. & Yeh, C. J.(2010). Perceived risk of information security and privacy in online shopping: A study of environmentally sustainable products. African Journal of Business Management, 4(18). Web.
Wang, P. & Wan, P. (2011). The genetic algorithm to management measures of information security systems. International Journal of the Physical Sciences, 6(12). Web.
Appendix
Appendix A
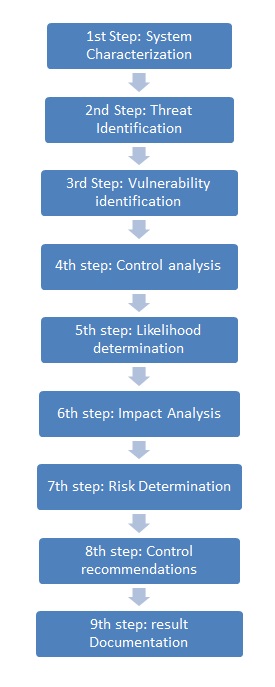
Table 1: Inputs and outputs of risk methodology steps