According to the ITU (the UN agency for digital technologies) report from 2023, about 2.6 billion people remain offline—approximately one-third of the world’s population.
However:
This percentage is steadily declining, which makes the remaining two-thirds are potential victims of cybersecurity threats.
Students, who frequently use public Wi-Fi in universities, libraries, and coffee shops, are particularly vulnerable.
The top-6 cybersecurity threats to students in 2025 include:
- Data theft, which occurs when hackers steal personal information such as logins, financial details, and other sensitive data, often exploiting weak passwords and unsecured networks.
- Phishing, a cyberattack in which scammers pose as trusted organizations to trick students into revealing confidential information.
- Scholarship scams, cyber security threats to students that deceive them into paying fees or sharing personal details in response to fake scholarship offers.
- Fake payment processors, malicious platforms designed to steal students’ bank card details when they shop online or pay tuition fees.
- Filesharing risks, which arise when students download academic materials or software from unverified sources, potentially exposing their devices to malware.
- Camfecting, a form of hacking where criminals gain unauthorized access to students’ webcams, compromising their privacy.
This article focuses on the actual cybersecurity concerns for students and offers effective tips to avoid the most serious threats.
Cyber Crime in 2021: Main Trends
We often view our new reality as an era of new opportunities. An astonishing 93% of US families claim to have tried some form of online learning during the COVID-19 pandemic. The same source specifies that the lower the household’s income, the greater the likelihood they would opt for online education resources. Only 20% of students used offline resources sent by their school, while 80% accessed their materials via the Internet. Still, even the 20% could access both variants, with the two groups overlapping.
Stanford research has shown that during 2020, more than 40% of Americans had to work from home, and more than 30% lost their job. Sadly, some of that 30% forged their own path through dark web technologies. Cybercrimes are flourishing because people are used to living, working, and studying in the World Wide Web, but they don’t know how to protect themselves.

These statistics make us think about emerging threats. According to the latest calculations, total losses due to cybercrime will make up $6 trillion by the end of 2021. This amount makes cyberterrorism the third largest world economy after the US and China. Cyberterrorism is operating at more than $11 billion every minute.
Cybercriminals attack households, not large companies. Thus, they often avoid large-scale prosecution. Largely, people do not turn to the law when their password is stolen. Learning and working from home (and sometimes both), we have not yet learned appropriate security measures. We really need to.
The main cybersecurity threats are phishing and ransomware. In the next section, we will discuss both in more detail. Cybercrime is increasingly becoming more sophisticated and can be waiting for us in the most unexpected places.
Cybersecurity Threats for Students
Surveys suggest that students are the most vulnerable group at risk of cybersecurity threats. They spend most of the day on the web. That’s why they must know where danger may come from. Below you can find the most frequent scam types that students can come across during their online studies and how to keep yourself safe.
Data Theft
Education and social networks are the most vulnerable spheres to data or identity theft. Students should be cautious on such websites.
According to Mimecast (a data security provider), over the first quarter of 2019, private educational institutions ranked first for the number of received malicious emails compared to any other industry sector. Criminals aim for students’ personal, health, and financial information.
To put it simply, when registering on your educational platform, you are expected to provide all sorts of sensitive information. If your account is cracked, your identity can get stolen by someone else. From that moment, they can use your data to access and register for other resources. It is mostly done to make payments without your consent or steal money from your credit card. But other more sophisticated fraud methods also exist.
Social networks are even worse for you (and better for cybercriminals). Many websites allow you to log in through Facebook or Google accounts. Thus, access to your social media opens the gate to hundreds of other resources. In 2021, half a billion Facebook accounts were hacked. Twitter is not protected from such problems, either.
How to Protect Yourself from Data Theft?
The attack news can scare you away from using social media, but there are better ways to tackle the issue. Here is what can be done:
- Avoid publishing personal data in social networks. Include as little personal data in your social network accounts and set the security settings to “available to friends only.” Mind that your full name, date of birth, home or office address, and family status are sensitive information. Hackers will use it against you if they access it.
- Think twice before sharing your personal information. Be extremely careful when sharing your private information. If your professor or college administrator asks you to provide your data via email, check if their email addresses are the same as before. Otherwise, call the institution to verify. And avoid sharing your information over the phone wherever possible.
- Use public WIFI carefully. Be careful when using free WIFI networks at your college, library, restaurant, or any other public space. The best method to keep your data secure is to use a VPN.
Phishing
Phishing ranks among the top cybersecurity threats. According to statistics, over 80% of reported cyber attacks can be classified as phishing. Furthermore, as of 17 January 2021, Google counted 2,145,013 websites that use phishing techniques, 27% more than in the previous year.
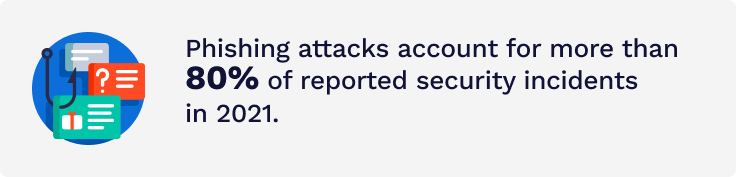
Phishing is a specific kind of data theft. Its key feature is a fraudulent incoming message in an email or a standard text message. It usually looks like it was sent by a bank, online store, educational institution, or social networkingsite. The text of such a message contains a link or an attachment and urges you to open it. The criminals may say there’s a problem with your payment information, or they’ve detected some suspicious activity on your account. Other popular scams feign the need to confirm some personal details.
Social media phishing is an entire “business sphere” of cybercrime. For Instagram, they create fake login pages to collect your login and password. It gives them access to your account. They will send messages to your friends to collect their login data. Attackers can also use these details to access your bank accounts.
For Facebook, criminals send emails, saying that there is some problem with the user account. They suggest logging in through their email to correct the issue. You will be redirected to a page that looks like Facebook. But if the URL is different from www.facebook.com, it is a scam. The same method is used for Twitter and other less popular social media sites.
How to Protect Yourself from Phishing?
- Use security software. Subscribe for automatic updates so that it can detect all the new threats. Use the same strategy for your mobile apps. Frequent updates can protect you from phishing.
- Use multi-factor authentication. Multi-factor authentication will protect your accounts. It means that you should provide two or more credentials to log in. This data may include your fingerprints, face, retina, or a passcode sent in a message to your phone number. Such options are not always available, but if they are, be sure to use them.
- Backup your data. Use the drives that are not connected to your home network. An external cloud storage or hard drive is best.
- Be attentive. Never click on an unknown link and if you do, check the URL address of the page carefully.
Scholarship Scams
For the most part, scholarship scams involve the exaction of money. They promise to give you a scholarship if you pay them a fee. However, in some cases, the criminals may attempt identity theft. Remember that no scholarship ever requires additional payments (except for a postal stamp to send a letter with your request).
How to Protect Yourself from a Scholarship Scam?
Beware if:
- The scholarship you apply for charges a fee. Even if it is small and reasonable (used as payment for taxes or application processing expenses), it is the first sign of fraud. Actual scholarships never ask you to pay.
- It asks for unexpected information. Scholarships never request your bank account number, social security number, or credit card for personal identification.
- You have received a letter with congratulations that you won a scholarship, but you’ve never applied for it.
- It offers you some kind of guarantee of acceptance or that it will increase your success rate.
- It requests your urgent action. On the contrary, typical scholarships have fixed application deadlines. The result does not depend on how early you apply.
- The organizer’s details are incomplete. For example, the announcement or email does not contain a phone number or physical address.
- The scholarship announcement contains grammatical errors or spelling mistakes.
If you’ve become the victim of a scholarship scam, you should report it as soon as possible.
- For the US: call +1-800-654-7060 (the National Fraud Information Center) or fill in the report form on the website. If you received fraudulent postal mail offering a non-existing scholarship for a fee, report it to the US Postal Inspection Service.
- For the UK: call +44-300-123-2040 (ActionFraud – the National Fraud & Cyber Crime Reporting Centre). If the scam was mailed to you via post, mark is as spam and send to Freepost Scam Mail with a cover letter.
Fake Payment Processors
This is the phishing type that often affects international students. According to Forbes, about 1 million international students come to the US every year and pay more than $14 billion in tuition fees. Many of them come from developing countries and do not know how payments should be made in America (or other countries they may have applied to).
Fake payment processors offer to save some percentage of your tuition fees if you pay through an intermediary. Unfortunately, all the money you pay goes to criminals. Sometimes they request fellow students to assist their scams for a percentage.
How to Protect Yourself from a Tuition Payment Scam?
- Always check who you are writing to. Many cyber criminals pretend to be college administration. It is easy to verify if they are.
- Be on alert for aggressive conversation or a lack of respect.
- Ask your college or university which payment methods are approved by their institution and follow their advice. Most colleges have a “how to pay” page on their website.
- Never share your personal information (bank account or credit card number, full name, and date of birth) with persons not related to your educational institution.
- The best option is direct payment to the college. The college staff can only approve any possible discounts. Direct payments are better, as they save you from additional fees.
- If you have noticed any suspicious activity, stop all interactions with the criminals. Then, report it to your college and the police.
- There is no such thing as “college tax.” If someone requests you to pay for it, they are criminals.
Filesharing Risks
Filesharing networks offer you free access to copyrighted content. The technology was created about 30 years ago and is known as P2P (peer-to-peer). A person who purchases paid content (films, music, audiobooks, software, etc.) uploads them to a website to share with other people. In return, they get access to other free materials uploaded by other users.
The most popular are:
- BitTorrent
- UTorrent
- BitComet
- FrostWire
The biggest issue is that such services are illegal. Moreover, they present a high virus-hazard level to your computer. Criminals can use malware to follow your activity on the computer, copy your passwords, and even bank details. You are also expected to share material from your own computer. There is the option to give worldwide access to some folders, but you can accidentally open the entire disc drive to anyone for download.
How to Protect Yourself from Filesharing Threats?
The best advice is not to use filesharing software. But if you do, make sure you employ the following precautions:
- Scan any downloaded file with reputable security software.
- If a P2P program requests modifications to your firewall settings, it is better not to install it.
- If your antivirus or security software marks any downloaded file as problematic, follow its instructions (and delete the file).
- Adjust your operating system and security software for automatic updates.
- Always check which folders you share with others.
- Closing the P2P software window does not terminate your connection to the filesharing network. Once the download is complete, click “exit” in the program menu.
Camfecting
Hacking your webcam is more common than most of us think. The Black Mirror TV series by Netflix shows us the possible future of humanity, but the technologies already exist. The episode Shut Up and Dance shows a 19-year-old boy whose webcam is hacked to film him for blackmail. Isn’t it scary to think that someone could watch you without your consent?
In reality, “Big Brother” is watching you. Camfecting is not a complicated task. Criminals upload trojan viruses to your computer, use internet connectivity features, and special-purpose spy software.
A trojan virus is a malware that users are tricked into downloading on theirdevices. It is masked as helpful software but opens the gate for malicious actions. Once you install it, the attacker gets access to your computer. They can install spy software to track your activity through the webcam.
Webcam internet connectivity is sometimes used for good. For example, smart home technologies are built on this feature. But criminals can hack access to your webcam to learn when you are not at home and rob you.
Spy software is a subcategory of remote administration tools. Have you ever shared your screen with another computer? Camfecting is similar to that.
How to Protect Yourself from Camfecting?
- Update your security software or subscribe for automatic updating.
- If you buy a webcam, let it be the simplest one. The more sophisticated features it has (e.g., watching footage in your home from any place in the world), the more access hackers can get.
- Enable the webcam only when you need it. In all other instances, disconnect the device or turn it off.
- For more security, put a tape over it. The old-school methods never fail!
Cybersecurity Threats for Students: Infographic
This infographic outlines the threats mentioned above and maps out the actions you should take. We advise saving it on your device for future reference because it is critical to act fast if your personal data is stolen.

10 Cybersecurity Tips for Students
- Create secure passwords. Try not to use your name and birth date, as this data can be easily found. Include lower- and upper-case letters, symbols, and numbers.
- Use different passwords for all websites and apps. If your device is stolen, or if one of your accounts gets hacked, criminals can access all other resources.
- If the two points above are a daunting task for you, use password apps. It is the perfect option if you are afraid you will forget all your passwords. It generates a unique and complicated series of symbols that are impossible to guess and hard to crack. It stores all login data with the respective passwords for autofill.
- Protect your social media accounts. It is a must if you’re not a public person and do not earn money through advertisements on social media. Adjust your privacy settings to “friends only’ and include as little personal data as possible in your account.
- Access your institution’s network through a VPN. It prevents your internet traffic from interception. Thus, your passwords will not be stolen.
- Avoid public WIFI networks. This is where you become the most vulnerable to all sorts of cybercrimes. Still, if you need to use it, connect through a VPN.
- Check the email addresses of your incoming mail. Never follow any links in emails received from unknown sources. Be especially careful with letters that have COVID-19 in their subject.
- Update your operating system and installed apps. Software developers constantly improve their products. This can make them harder to crack.
- Use websites and apps that encrypt data. If you can, always opt for such variants. URLs of encrypted websites start with “HTTPS.”
- Backup the most critical files on a removable disc drive. Needless to say, you should keep it in a secure place. If your accounts or devices are hacked, you will still be able to access the files from another computer.
Forewarned is forearmed! We hope that this comprehensive article will prevent you from ever having to deal with cybersecurity breaches. If you know of any other kind of cyberterrorism that’s not mentioned here, please share it in the comments below. Your experience may save other students.
