Introduction: Facts of the case
On February 06, 2014, Ioan Leusca and Dezso Gyapias were charged in a U.S. Federal Court for stealing customer data from automated teller machines (ATMs). The two men had used data acquired from the ATMs to steal from bank customers in Connecticut, New Jersey and New York (US Immigration and Customs Enforcement (ICE), 2014). When they appeared before Justice William Martini, Leusca and Gyapias were charged with installing ATM skimmers and pinhole cameras in ATMs across three states in the U.S. Each skimming device had the ability to steal and record customers’ account information whenever a customer used a compromised ATM. The pinhole cameras on the other hand, would record keystrokes as customers typed in their PIN numbers when using the ATMs. The information captured by the two devices, was then transferred to counterfeit ATM cards, which the fraudsters later used to withdraw money amounting to $5 million from bank accounts across the three states. The targeted banks were: TD Bank, Citibank and Wells Fargo. Of the stolen amount, Leusca and Gyapias admitted to having withdrawn $985,000. The rest of the $5 million was withdrawn by other Romanians in the same gang.
While Leusca and Gyapias were not the masterminds of the ATM skimming, they took part in installing the skimming devices, and also participated in withdrawing cash from numerous ATMs across the three states. For that, they were sentenced to 57 months in prison. Judge Martini also ordered the co-accused to “serve two years supervised release and to pay $985,000 in restitution” (ICE, 2014, para. 2).
Fraud opportunity Triangle
It seems that the fraud triangle is applicable in Leusca and Gyapias’s case since there was pressure/motivation, opportunity and rationalization.
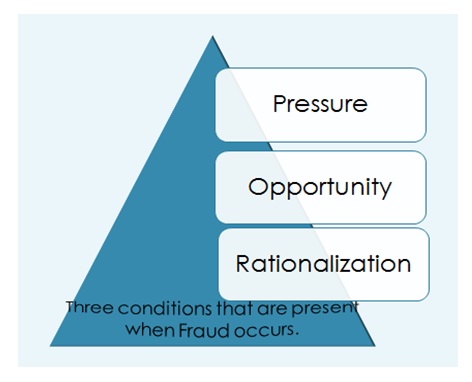
As indicated in figure 1 above, three conditions need to be present for a crime to occur. The first such condition is pressure, which is described as the motivation that one has to commit fraud, or the incentive one hopes to get thereof. In the Leusca and Gyapias case, it would appear that the fraudsters were motivated by possible financial gains. The two had withdrawn $985, 000 within two days, hence indicating that they were out to withdraw as much money as they could. It is also important to note that Leusca and Gyapias were part of a larger group of Romanians residing in the US who participated in the same crime. As such, there is a possibility that, as foreign nationals, Leusca and Gyapias succumbed to pressure from their peers to get into a get-rich-quick scheme.
The second condition present in fraud cases as indicated in the fraud triangle is opportunity. According to PricewaterhouseCoopers (PwC) (2012), technological advancements have led to a proliferation of fraud opportunities. In the Leusca and Gyapias case, for example, pinhole cameras and ATM card skimmers were the technological tools that were used. PwC (2012) specifically terms the picking of keystrokes as an “increasing sophisticated” type of skimming, which does not require fraudsters to stage long surveillance missions in order to access customer login details (p.6). Although not documented, it is also likely that Leusca and Gyapias were convinced that they would successfully conceal the fraud; after all, one would argue, they had successfully installed the skimmers and pinhole cameras in multiple ATM lobbies in three states without being detected. They must have believed that their actions would go undetected (or at least that no one would know who had made the withdrawals). Leusca and Gyapias may also have thought that they could convert the theft by misrepresenting the withdrawals in a manner that made the three banks believe that their customers had actually withdrawn the money.
The third condition that is present in fraud is rationalization. Rationalization refers to the reasons that fraudsters give for their crimes. According to PwC (2012), “rationalization of a crime varies depending on individual fraudsters, and is difficult for organizations to assess” (p.19). In the case of Leusca and Gyapias, their reasons, though not stated, may have included being a minority group in the US, and a need to earn money. Perhaps they even thought it was right for them to expose susceptibility of the current banking system and the ease with which fraudsters can steal from customers. Since this was a carefully planned fraud, perhaps the perpetrators did not see the need of being honest. Arguably, Leusca and Gyapias and their co-perpetrators did not value integrity and hence perceived theft as an ideal way of acquiring money.
Motivation for the crime and signals that could have been picked by the banks
Since Leusca and Gyapias were not the masterminds behind the ATM skimming fraud, in which they were implicated, one would easily think that they participated in the same out of pressure from their Romanian friends. However, it is reasonable to assume that every person who participated in the crime was motivated by something. Like most thefts involving money, the most plausible motivation for Leusca and Gyapias was the idea of getting ‘easy money’. Their acquisition could be described as ‘easy money’ in the sense that, they did not have to work in order to earn the money in an honest manner.
Had the targeted banks paid enough attention to their ATM machines, they would have noted that skim devices had been fitted. Grubisic (2009) notes that “most skim devices when fitted will obscure the flashing entry indicator” that shows customer where to fit their ATM cards (p.5). Notice the difference between the ATM card slots shown with an arrow in figures 2 and 3 below.

Customers may not have easily known that the ATMs were fitted with a skimmer, but people working in the banks should have easily picked this up. The fact that money was withdrawn for two consecutive days means that the banks did not inspect the ATM machines regularly, and if they did, those charged with the responsibility of doing so were not keen enough to notice the presence of the skimmers. As Grubisic (2009) notes, skimmers come in different designs. However, the bank staff should be trained to detect when alterations have been made on their ATM’s fascia.
Additional controls that can be used
Fraudsters are seemingly an innovative group of people, who spend time designing and testing new ways of defrauding people and institutions. The fact that they dedicate time and effort to generate new ways of perpetuating fraud, does not, however, provide people and institutions with a reason to become lax in risk management. According to PwC (2012), creating awareness in the leadership team regarding fraud is one vital control that each bank needs to adopt. Banks therefore, need to create a culture where all employees understand the risks facing them, and how best to manage such risks.
Having a robust security framework is another control that banks can use in order to minimize fraud. If the three banks that Leusca and Gyapias targeted were fitted with surveillance cameras whose content was scrutinized, it is possible that suspicious activity by the two fraudsters would have been noted. Additionally, the surveillance cameras would have picked the skimmers and/or pinhole cameras as they were being fixed by Leusca and Gyapias.
Regular risk assessments would also provide an additional control for banks. PwC (2012) recommends that banks should consider how fraudsters can use information technology (IT) systems such as ATMs to commit fraud. Usually, such fraud is only possible where data theft has been committed successfully. Banks should therefore assess how data theft in the ATMs occurs. The foregoing recommendation would enable banks to anticipate methods that data thieves would use, and as such, would be in a better place to put mitigation measures in place.
Lastly, banks may need to enhance the knowledge and skills of their employees in fraud-related matters. As noted above, fraudsters dedicate time and effort to designing and testing new ways through which to commit crimes. If banks are to prevent such crimes, their employees need to have the knowledge and skills needed to handle emergent fraud methods. PwC (2012) notes that bank employees need to be conversant with new methods that fraudsters use to commit financial crimes. After all, only knowledge can enhance employees’ abilities to mitigate risks associated with new ways of committing fraud.
An analysis of the verdict
The verdict by the Federal Court to imprison Leusca and Gyapias for 57 months was arguably fair, because, in addition to their time in prison, they were also ordered to repay the same amount of money they had stolen. Moreover, the two would serve another two years of supervised release. From the sentence, the two would have gained nothing from their crimes. Their time in supervised release will also reduce their freedoms, because as Santos (2014) notes, the conditions of a supervised release are at times too tough for ex-prisoners. For example, a person under supervised release cannot move outside their judicial district without notifying a probation officer. Additionally, changing addresses, associating with specific people, engaging in specific activities (e.g. drinking) and working in some sectors must be expressly permitted by the probation officer. Arguably, the sentence provides enough deterrence to Leusca and Gyapias against engaging in fraudulent activities in future. The sentence is also a lesson to other aspiring fraudsters because it shows that there are no gains in fraud if one is caught and prosecuted, and that a person will only end up wasting many years in prison. Since Leusca and Gyapias were not the masterminds of the fraud, the sentence further shows that even being a co-perpetrator does not shield people from the harsh reality of spending life behind bars, and re-paying the victims of the crime. The sentence as issued by Judge Martini is also punitive in the sense that in addition to repaying everything they had stolen, Leusca and Gyapias would have to spend more time in prison as punishment for having stolen from bank customers.
References
Grubisic, S. (2009). Group security: ATM card skimming and PIN capturing awareness guide. Commonwealth Bank, 1-24.
PricewaterhouseCoopers (PwC). (2012). Fighting fraud in financial services: 6ths PwC global economic crime survey. Web.
Romney, M.B., & Steinbart, P.J. (2011). Accounting information systems (12 ed.). Upper Saddle, NJ: Pearson.
Santos, M. (2014). Supervised release: how will it influence your life? Supervised release after a term in the Federal Bureau of Prisons. Web.
U.S. Immigration and Customs Enforcement (ICE). (2014). Queens men sentenced for $1 million ATM skimming. Web.