Introduction
Online threats remain a reality for today’s businesses, especially those relying on the internet. Active and passive attack incidents are escalating every day and network administrators are having a daunting task of detecting, controlling or minimizing the effects of such attacks. Stewart, Tittel and Chapple concur in that one of the common methods to secure the facility includes “the common access control and auditing procedures” (23). Perimeter systems that are sensitive to intrusions can be set up to boost physical security. An intrusion detection system (IDS) is one of the tools in the organization’s network security armory that also includes a firewall and an antivirus. According to Magalhaes “the IDS will compliment a firewall to ensure desirable network security for any organization” (1).
The approach of layered defense-in-depth policy procedures and tools is well accepted as best practice for information security. The pressure for return on security investment (ROSI) has further exacerbated the difficulty of implementing technology. Since the September 11th attacks, security has been elevated to an area of critical liability for many business continuity providers. Based on this approach, service and business continuity providers such as Cisco have questioned how to protect the integrity of mission-critical operations without limiting the flow of business. Corporate information security officers have for a long time now been asking this question.
As computer networks continue being more complex the security of such systems has become a process not just a product. Formerly, a router’s access control lists provided necessary protection to keep out most threats. At the moment firewalls, authentication, web filtering and imposition detection, and avoidance form pieces of the puzzle.
Physical security is normally enforced to counter threats posed by humans, weather, nature or equipment. The implementation of the control mechanisms affecting physical security will cover administrative, technical, and physical controls. While establishing and maintaining control as well as physical security over computer networks and the internet, perimeter security controls are very important. Methods to secure the facility include the common access control and auditing procedures. Perimeter systems that are sensitive to intrusions can be set up to boost physical security. Other methods can also be established to check technical access. Typical in this category are like dry contact switches, pressure mats, photometric detection systems, passive infrared detection systems among others.
Based on these findings today’s best practices for any internet based service providers such as the university’s online registration and cashiering system can include the following:
- Security guiding principles written down approved as conditions for employment. These must be regularly appraised and updated.
- The enforcement of general security practices involving ‘deny all’, unless explicitly allowed.
- Encryption of all sensitive data transmitted across public connections using protocols such as IPSec, secure socket layer (SSL) and WEP
- Controlling traffic across all borders physical ~ external – internal, external – DMZ, DMZ – internal wireless, logical ~ HTTP services – database services; file transfer protocol (FTP); Telnet; Java-; ActiveX
- Properly configuring network access regulations across internal and external boundaries.
- Role based authentication and approval that includes dynamic passwords normally produced by hardware or software tokens. These can also be sent for instance, to mobile devices for network administrators, remote users (virtual private network (VPN), Citrix, wireless, modem users), employees or business partners accessing critical information.
- Filtering local as well as remote content that is likely to cause network vulnerabilities for example e-mail attachments, hacker tools and viruses, legal liability (pornography, criminal skills, anonymizers, and cults) and poor network availability resulting from MP3 content.
- Third party standard inspections and assessments.
Executive summary
Michigan State University is currently exploring the benefits of online computing. They have implemented and are using a registration and catering system for the last one and a half years. Since this is a web based system, certain threats to the system are likely even though the management has not laid down serious considerations during their initial operations
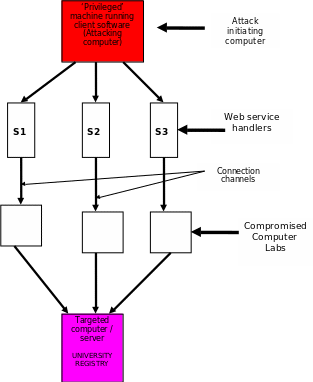
Due to the nature of the processes carried out by the system and the work involved, the university system has recently succumbed to one of the common online threats today; the denial of service (DDoS) attack. This attack has been initiated and implemented because the university has not laid down a suitable policy on intrusion detection and prevention. The DDoS attack has rendered the university system inoperable and the CIO has launched an investigation to determine the genesis and cause of this incident. The CIO has established the cause of the attack and written a report whose content is summarized here.
The genesis
The lack of a well defined LAN security policy has exposed the vulnerabilities within. The absence of concerted investment in network and host based intrusion detection systems has provoked the attack. The attack has been investigated and found to originate from within the university LAN, a clear indicator that the attack was carried out by one of the staff who had some ulterior motive. The person concerned was well aware of the system’s internal working and knew the computers on the network to target. The attacker must also have been technically advantaged in order to set up the attack. Having gained access to one of the controlling computers, the attacker was able to use this unauthorized access to implement the attack.
The Attack
Because the system within the university LAN lacks any intrusion detection systems, the attacker has used packet sniffing technique to capture the passwords to critical system components like the university LAN servers. The intention of this procedure was to gain unauthorized access to these servers. On gaining access to these university servers, the attacker has progressed on to cripple the processing at these servers by flooding them with internally generated and fictitious hypertext transfer protocol (HTTP) requests. This flooding has jammed and crippled the server operations thereby causing the system to fail to address any genuine requests. Due to this, the registration service offered by the university’s LAN servers has been shut down to any genuine requests and processes. In that perspective, this is an intrusion threat that has caused a denial of service.
The Countermeasures
Since intrusion detection systems (IDS) have become a necessary investment for any company, the university will have to design and deploy such a system.
The IDS will carry out the following:
- Detect any security breaches and attacks on university LAN
- Prevent such intrusions
- Document any intrusion attempts on the university’s network and isolated suspect network activities.
Whether to choose a host based (HIDS) or network based (NIDS) intrusion detection system depends on the university’s requirements. However, some points of comparison between the NIDS and HIDS must be carefully considered. It remains true that both the NIDS and HIDS can effectively protect the local area network (LAN) from attacks. However, over time HIDS have been known to be more versatile and affordable compared to the NIDS. It is also known that the NIDS unlike the HIDS will utilize network bandwidth, which is one of those expensive network resources. However, the NIDS can adapt well to cross platform networks, which is not the case with HIDS. In order to offer an effective intrusion detection system (IDS) for the university, the NIDS is considered suitable because it will be able to offer a comprehensive solution as a multi segment detection system. Based on its functionality, the NIDS will check for intrusions on network backbones, operating systems, or applications. Network based IDS uses network packets it captures to detect any intrusion. This type of IDS can be deployed in a stealth mode operating in a passive manner. This type of detection system is therefore recommended to secure the university LAN against internal based intrusion threats such as the one encountered. It is important to realize that though HIDS are comparably cheaper; these types of IDS are vulnerable to denial of service attacks and therefore unsuitable to secure the university LAN.
Conclusion and recommendation
The implementation of a suitable intrusion detection system (IDS) at the university will result in a more secure LAN and well protected university information and resources. The deployment of this system will be effective if it is carried out on the network and host levels. This intrusion detection system type can be deployed on a number of computers as well as servers in critical departments of the company.
Works Cited
Magalhaes, Roberson. Host based versus network based IDS. Windowsecurity.com, 2010. Web.
Stewart, James, Ed Tittel, and Mike Chapple. Certified information systems security professional study guide. New York: Wiley, 2003. Print.