Introduction
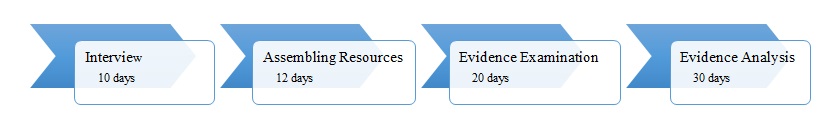
A concerned citizen has contacted the police regarding the selling of counterfeit public documents. He told the police that he was going to the state residents to apply for a driver’s license. When he was almost reaching the office, he was approached by a man who told him he could create registration cards for vehicles at an affordable price to evade tax. Undercover officers met with the suspect, and after providing them with registration cards, he was arrested. A search warrant was obtained, and two computers from his home and a flash drive were seized. The investigator contacted the computer forensic laboratory to examine the evidence. Figure 1 below provides a snapshot of the investigation timeline and plan. Also, a budget in Appendix 1 was created and submitted to the Police Department for review. It was approved, and an investigation of the case began.
Interview Protocols
Before starting the interview process, the digital forensic examiner must first ensure that they are provided with the required legal documentation. These comprise verifying consent, search authority, warrant, and subpoena. These documents will help identify what legal level of analysis and the files that the examiner can examine. In this case, a copy of the evidence chain of custody and consent form may suffice, as in the appendix. To further compound the legal extent of the investigations, digital forensic examiners can review the case in regard to possible concerns related to the relevant Federal statutes (the Cable Communications Policy Act (CCPA) and the Electronic Communications Privacy Act of 1986 (ECPA), State statutes, and local laws and policies (United States Department of Justice, 2017). After the forms were reviewed and determined to align with the legal mandate, meetings were scheduled with the victim and case investor.
Case Investigator Meeting Agenda
Date: 5/4/2021.
Time: 11:00 AM – 1:00 PM.
Attendees: Case investigator and digital forensic examiner.
Meeting Objective
To determine the state of the crime scene and how evidence was collected.
Agenda
- Review the documentation on the state of the crime scene (40 mins)
- Review the victim’s allegations (40 mins)
- Discuss possible investigative avenues regarding the type of evidence files sought (40 mins)
The following questions would be asked:
- What was the location of the computers? Were they found powered on or off?
- How were the computers collected?
- What was the location USB thumb drive? What is found plugged in the processor?
- How was the USB thumb drive collected?
- Were there any copies of public documents retrieved from the crime scene, for instance, driving licenses?
Notes and Decisions
The two computer drives and USB thumb drive were collected and preserved appropriately. The picture of the crime scene is represented in Figure 2.

- There were no gaps in the victim’s statement
- Digital forensic analysis should focus more on identifying graphic design files
Next Step
Interview the victim to re-evaluate their statement.
Victim Meeting Agenda
Date: 5/7/2021.
Time: 11:00 AM – 12:00 NOON.
Attendees: Victim and digital forensic examiner.
Meeting Objective
To review the victim’s testimony. This would be achieved by creating a comfortable and calm environment for them throughout the interview. I would also try to be emphatic to motivate the victim.
Agenda
- Victim narration of his encounter with the suspect (40 mins)
- Determines if there are gaps that need clarification (20 mins)
The following would be asked to the victim;
- What type of public document did the suspect offer to create?
- What personal data did he claim he needed, that is, fingerprints, and passport photo size?
Notes and Decisions
- Suspect approached him and offered to create a driving license
- No gaps were identified
Next Step
Compare the victim’s statement with the information collected by the case investigator.
Proposed keywords: They were created from the available background data and additional information from the suspect and investigator. This list of words will be searched on the computer to look for matches, and they are “vehicle title”, “vehicle registration”, and “car title”.
Tools and Software Needed
This investigation aims to determine whether the suspect used the two computers to commit crimes of forgery and uttering false documents. Therefore, data collection in the context of image files, documents, and applications will prove effective in investigations. This information can be harvested by using tools and software that are specifically designed for this purpose. These include (the United States Department of Justice, 2017):
- Forensic Tool Kit (FTK). It is used to perform keyword and index searches
- EnCase. It is a software developed by Guidance and is used by digital forensic experts to triage systems, collect files, decrypt encrypted files, and index information such that it is easily accessible.
- DIGit. It will then be utilized in carving images from the unallocated space.
Plan for Conducting the Investigation
The primary aim of the analysis is to determine their origin, and where and when data was created, modified, uploaded, downloaded, and the possible connection of files to storage devices, either physical or cloud-based. Generally, four types of analyses will be performed on the computers; ownership and possession, time frame, application and file, and data hiding (Gurjar, 2018).
Imaging
- Examination and photography of the hardware
- A thorough visual inspection of the physical make-up of the computers will be performed to determine the type.
- This will be followed by removing the CPU case and examining the internal circuitry and notating all media, including hard drives, removable media drives and flash memory. Identify them by model, capacity and condition.
- A controlled boot disk will be placed in the computer’s floppy drive. The devices will then be powered on and the BIOS setup program inputted. Information from the BIOS will be documented and the time on the computer compared to that from a trusted source, then be noted. The computers’ will be booted from the floppy drive and the boot sequenced verified and recorded.
- The computers will then be powered off without making alterations to the BIOS.
- Installed programs are scanned to determine if the computers have graphic design applications.
- Encase will be employed in creating an evidence file containing an image of the computer’s hard drive.
- Through their parallel ports, computers will be linked to the laboratory computer via a null-modem cable.
- The computers will then be booted to the DOS prompt using a controlled boot disk and EnCase started in server mode.
- The laboratory computer containing a magneto-optical drive for file storage will be booted to the DOS prompt using a controlled boot disk. EnCase will then be started in server mode and potential evidence files from the two computers obtained and written on the magneto-optical disks.
- After collecting the required files, the computers will be turned off, and the magneto-optical disks containing evidentiary files write-protected and stored.
Analysis
- The laboratory computers will be prepared with Windows 98 and EnCase for Windows, among other forensic software programs.
- The evidence files in the magneto-optical disks will be copied into the computer’s hard drive.
- Graphic design application file data consisting of file names, physical and logical size, date and times, and the complete path will be recorded.
- Keyword text searches will be conducted based on the information collected from the interview. All hits will be reviewed.
- The files are scanned for insertions.
- Metadata is examined for created files and insertions.
- Files deemed to be of evidentiary value will be copied from the EnCase file onto a compact disk.
- Encrypted and password-protected files will be copied onto a floppy disk. The FTK will be run on such files to open for viewing.
Conclusion
Digital forensic analysis is essential for the investigation of fraud cases. Using useful tools such as the FTK and AccessData scientists can easily retrieve data that is of vital importance and hold evidentiary value. Nevertheless, before beginning an analysis, it is essential that forms are provided to document the legal extent of the examinations. This helps improve the admissibility of evidence in a court of law.
References
Gurjar, C. (2018). Computer forensics investigation – A case study. Infosec, Web.
Moulin, J. (2015). Digital forensics/incident response forms, policies, and procedures. Web.
United States Department of Justice. (2017). Forensic examination of digital evidence: A guide for law enforcement. Web.
Appendices
Appendix 1: Investigation Budget
Investigation Budget.
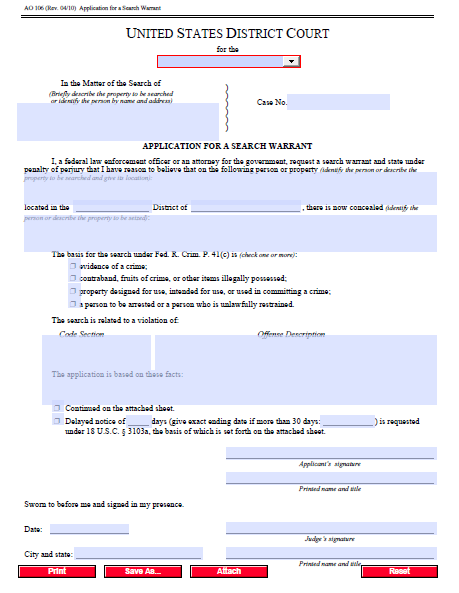
Appendix 2: Application for Search Warrants
Appendix 2: Evidence Chain of Custody Form
Source: Moulin (2015).
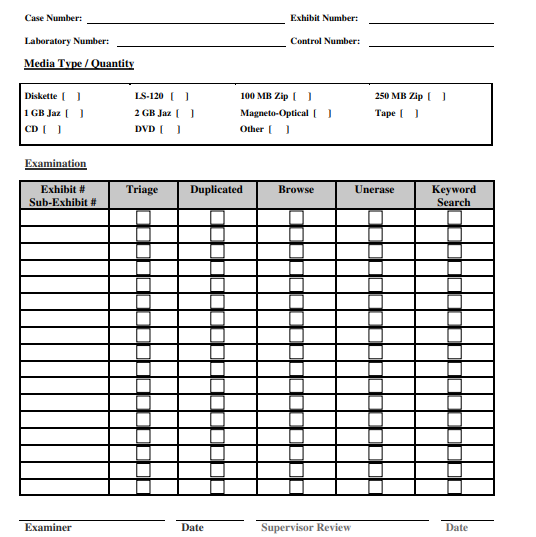
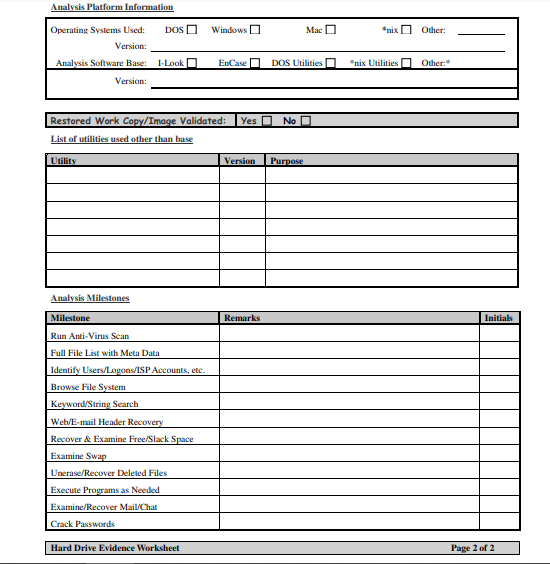
Appendix 3: Hard Drive Evidence Worksheet

Appendix 4: Removable Media Worksheet