Introduction
Organizational security is a complex and dynamic phenomenon. It is essential for institutions to invest in the best practices and components to ensure the security of persons, information, and the physical set up. This means that the security plan must encompass all the aspects that pertain to it. Such aspects may include the accuracy of the adopted technology, its relation to the existing systems, and its usability by personnel. It is challenging to come up with a security model that suits a medical facility. This is because other than addressing the medical personnel and equipment, the model must consider the security of the patients as well. In essence, the past trends and experiences in the industry should inform the security scheme and put it in line with the contemporary perspective.
This paper will detail a security plan that includes three security technologies. The three forms of technology are firewalls, multifactor authorization systems to limit unauthorized users, and backup systems to limit the corruption of data. For each of the three technologies, the paper will highlight their descriptions, associated costs, expected return on investment, mitigation of risks, and the barriers to success.
Background Information on Technologies for the Security Plan
Technologies are mainly a function of the hardware, software and users. They function in defined environments that characterize their efficiency and range of applications. The users of a security plan must understand the interface between the real and the virtual world. A plan for the virtual world considers the security of information and the eventual functionality in the physical world. Information security includes aspects of access to the information, procedures of retrieval, guarding against destruction, and unauthorized modification. On the other hand, the real world security considers the physical harm to persons, the destruction of property, and the mechanical damage of hardware (Feruza & Kim, 2007).
Firewalls
Firewalls are electronic components and algorithms that characterize the flow of information between networks and individual user components. Computer networks are envisaged as systems while the individual user’s devices can be considered as the components that form the system. In essence, it serves the individual components of the system and the network on which the components function as a unit. Firewall is designed to sensor data according to its source, the dominant characteristic and the output compatibilities. Four aspects characterize firewall. First, it is contained in the hardware layer. The most common hardware layer is Ethernet, which serves devices and the network between them. The second aspect is the application layer. It aids in sending and receiving information to specific Internet Protocols. Protocols on mailing systems, domain names and the general transfer of information in text use the application layer. The third aspect is the transport layer. The function of firewall in this layer is limited to connectivity. It provides systems with clarity of information transfer and prevents the intermediary disorientation of data. The fourth characteristic is the Internet Protocol Layer. It comes in a number of versions such as version 4 (IPv4) and version 5 (IPv5) that specialize in the transfer of classified sets of data (Scarfone & Hoffman, 2009; Mellado & Rosado, 2012).
Firewalls function with corresponding router technologies such as the Network Address Translation (NAT). This technology facilitates the filtering of information coming to the system of connectivity and electronic devices. This is called ingress filtering. On the other hand, the information getting out of a system or component is called egress filtering (Scarfone & Hoffman, 2009). Information systems for health facilities get traffic related to medical records, drugs, consultations and general information on diseases. They also share information with other health facilities or other organizations related to them. Hospitals may also choose to classify certain information for a patient, medical procedure or research developments. Firewall comes in handy when it comes to filtering the requests from various clients and institutions seeking information.
Authorization System
The multifactor authorization system for limiting unauthorized users is a security procedure that seeks to verify whether the request of access is permissible. Physically, persons seeking to enter a hospital may be under authentication processes from the gate to the specific hospital unit, ward or room of the patient or the doctor. Organizations would like to ensure that the people accessing information are authorized. To achieve this, they employ a number of strategies. Technologically, organizations have different models to authenticate users who wish to access information or a physical location. For efficiency, the prospective user sends a request for registration. On accepting the request, the user is subjected to a process that allows them to give information about themselves, which is later on used for their authentication. Identity proofing is done using a Credential Service Provider (CSP). This tests the authenticity of the user against the information given during registration. The person who sends request for authentication is referred to as the claimant. On the other hand, the system that tallies the information of the claimant with the existing one is known as the verifier (Burr, Dodson & Polk, 2006; Feruza & Kim, 2007).
Multifactor authorization to limit unauthorized users is advanced to provide more security through the application of complex passwords, encryption of the system and sourcing services of an intermediary company. Organizations may cipher information that the claimant enters thus making the system to recognize different forms of information from the one it is receiving. The complexity of the system differs from one cryptographic key to another. Some cryptographic keys are to the order of 279 making it hard to crack the cryptographic operations. An intermediary company that wants to outsource security services should cede the organizational security to the service provider. Kerberos authentication protocol is known to offer intermediary services. It is susceptible to the risks of attacks from eavesdroppers, impostors and hijackers (Burr, Dodson & Polk, 2006; Feruza & Kim, 2007; Mellado & Rosado, 2012). Medical institutions need to authenticate both information and persons. Information to be authenticated includes the kind of treatment undergone by a patient, the results of research processes, and permission to use certain equipment may require authentication. However, personal integrity, confidentiality and privacy play an important role in ensuring that the right people access medical information, place and equipment.
Backup Systems to Limit Data Corruption
Corruption of data is the rearrangement of the order of information into information that is recognized or not recognized but far much different from the original one. Corruption also refers to disorientation of the connectivity between the systems and components. In this light, the corruption of data can be in either physical or logical form. In physical corruption, the database ceases to recognize an entire block of data. This may happen even when the content is still uncorrupted (Chlen, Pedregal, Schupmann & Carpenter, 2012). Medical institutions ought to establish a backup system that will serve them with records and information in case data gets corrupt. The presentation of data in multiple formats, such as text, images, audio, and a combination of audio and visual, provides a wider platform of storage and retrieval of information. Thus, it reduces the chances of corrupting important data.
The Schematic Representation
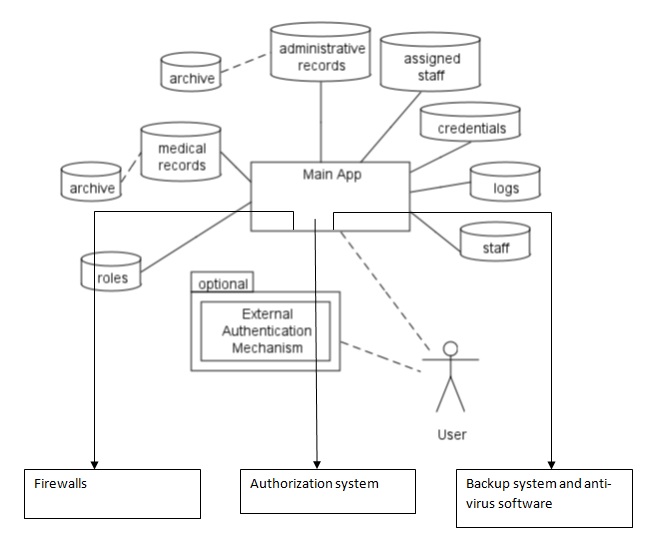
According to Holodiuk (2011), the above model is a classical centralized security system. This paper has adopted the concept of centrality and modified it to suit the technological components discussed in the plan (Firewalls, Multifactor authorization to limit unauthorized users, and technology to limit the corruption of data).
It demonstrates the individual components and their connectivity. Such components include the staff, credentials, administrative records, archives, medical records and the responsibilities of the employees. They are linked to the main application. The application is designed depending on the complexity of the medical institution. The external authentication mechanism should not necessarily function out of the medical institution. The institution may employ an independent system to monitor the one in operation (Swanson, Hash, & Bowen, 2006; Holodiuk, 2011).
Costing of the System
The costs of an information security system are subject to a number of factors, mainly, the extent of the system’s functionality and the technological ancillaries that are unique to institutions. The technological requirements and configuration differ according to the complexity of the institutions. The extensive analysis of the costing depends on the cost of purchase, the cost of setup, the cost of operations and the cost associated with configuration and changes on the system (NIST, 2011; Avitan, 2012; Brecht & Nowey, 2011; Swanson, Hash & Bowen, 2006).
Subject: Recommendations for Developing a Security Plan For a Medical Facility
The following recommendations are made in light of the information security plan in a medical facility. The plan is fit for a medium sized medical facility. The plan focuses on three technologies; Firewalls, Multifactor authorization system to limit unauthorized users, and backup systems to limit the corruption of data.
Recommendations
Medical institutions ought to balance between the technological domains of information security and the affective domains such as the organizational culture of trust and responsibility. In perspective, technological domain entails hardware, software and the details of connectivity. This will help to foster integrity, confidentiality, need for privacy, and availability.
Authentication of sensitive information should occur hierarchically and through a network that imposters, eavesdroppers and hijackers cannot tamper with. The schematic representation of the plan recommends that the three flagship technologies (Firewalls, Multifactor authorization to limit unauthorized users, and Technology to limit corruption of data) be applied in a centralized system. However, the operations and functionality of the technologies should take place independently.
The medical institution should develop a policy that will culture the staff on the best practices of the adopted technologies. The policy should detail the hardware (Computers and medical equipment), the software, and the interfacing operating systems. This will link the central system and the equipment, besides acting as a database.
References
Avitan, A. (2012). Controlling the cost of Firewall Operations and Compliance. Frost and Sullivan.
Brecht, M. & Nowey, T. (2011). A closer look at Information security costs. University of Regensburg, Germany.
Burr, E.W., Dodson, D. F., & Polk, T. W. (2006). Information Security, Electronic Authentication Guideline. National Institute of Standards and Technology. Special Publication 800-63.
Chlen, T., Pedregal, C., Schupmann, V., & Carpenter, M.L. (2012). Preventing, Detecting, and Repairing block Corruption: oracle Database 11g. Redwood shores, CA:Oracle Corporation.
Feruza, S.Y. & Kim, T. (2007). IT security Review: Privacy, Protection, Access Control, Assurance and System Security. International journal of Multimedia and Ubiquitous Engineering, 2(2), 17-32.
Holodiuk, S. (2011). Modelling a Hospital Information System with Decentralized Label Model. Kongens Lyngby: technical University of Denmark.
Mellado, D. & Rosado, D.G. (2012). An Overview of Current Information Systems Security Challenges and Innovation. Journal of Universal Computer Science, 18(12), 1598-1607.
NIST. (2011). Managing Information Security Risk. National Institute of Standards and Technology. Special Publication 800-39.
Scarfone, K. & Hoffman, P. (2009). Guidelines on Firewalls and Firewall Policy. National Institute of Standards and Technology. Special Publication 800-41.
Swanson, M., Hash, J., & Bowen, P. (2006). Guide for Developing Security Plans for Federal Information Systems. Information Security. National Institute of Standards and Technology. Special Publication 800-18.