Introduction
TCP/IP is the combination (protocol suite) of Transmission Control Protocol (TCP) and Internet Protocol (IP), also known as the Internet protocol suite. It is the most commonly used suite for both local area networks (LANs) and the broader internet (Schneider & Gersting, 2019). In the Open Systems Interconnection (OSI) framework, they primarily function at layers 4 (transport layer) and 3 (network layer), respectively (Schneider & Gersting, 2019). The purpose of these protocols is ensuring the formation, sending and delivery of data between host machines. TCP is concerned with establishing a connection and transporting data between two nodes on the network, whereas IP is responsible for the packet’s transmission through the network. Before transmission, data received from the application layer is split up into smaller pieces called packets, each appended with a header containing data required to determine its destination address and position within the finished message. Then, the packet is routed through the network using IP. Once the packets are received at the destination host, they are reassembled into usable data.
TCP/IP Packet Headers and Structure
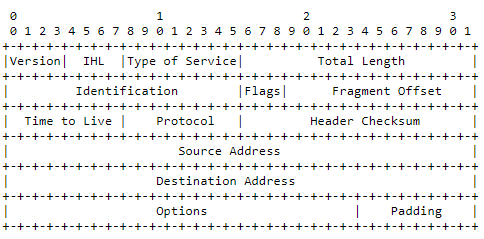
The IP header structure for IPv4 is shown in Figure 1, containing the following data:
- Version number, 4 for IPv4.
- IHL: the total length of this header in 32-bit words.
- Type of Service: bit flags indicating precedence, delay, throughput, and reliability parameters. These parameters are used by intermediary nodes along the datagram’s path to determine its route.
- Total Length: the total length of the datagram, in octets. Although a length of 65,535 is technically allowed, this size is impractical, and generally significantly shorter datagrams are sent.
- Identification: a value assigned by the sender, used in reassembling the datagram by the receiver.
- Flags: 2 control flags, describing whether the datagram may be fragmented and whether this is the last fragment.
- Fragment offset: indicates the fragment’s position in the datagram.
- Time to live: this field is reduced at each node processing the fragment. If it reaches zero, the datagram must be destroyed, preventing network congestion with undeliverable datagrams.
- Protocol: a numeric value representing the next-layer protocol for which the message is intended; in case of TCP, this is 6 (Internet Assigned Numbers Authority, 2020).
- Checksum: the checksum for the header. This field is modified at each processing point.
- Source and destination addresses.
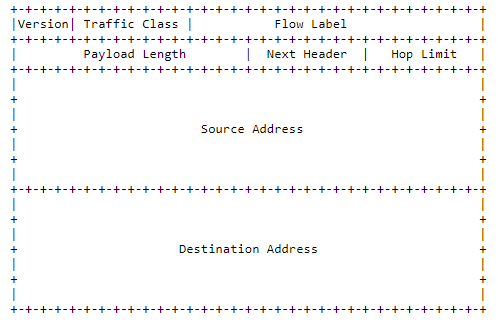
The IPv6 header is relatively simplified compared to IPv4; however, it allows extension headers to be appended, containing any additional relevant data to the datagram (Deering & Hinden, 2017). The protocol specification introduces the concepts of traffic class and flow, which are used for traffic management and packet identification (Deering & Hinden, 2017). The next header field is either identical to the IPv4 Protocol field or references extension headers (Deering & Hinden, 2017). A hop limit replaces IPv4’s time to live, but serves the same function. Notably, the source and destination addressing fields are larger to address the problem of IPv4’s address space running out. The IPv6 is less commonly used, but its adoption is gradually increasing.
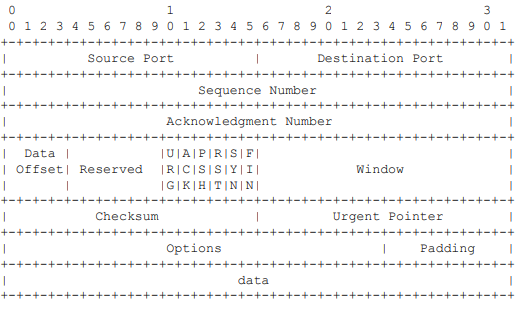
The TCP header structure is as follows:
- Source and destination ports: describe the addressing within the sending and receiving hosts.
- Sequence number: the number of the first octet in the segment, used to reassemble datagrams at the receiving end.
- Acknowledgement number: the next sequence number that should be received.
- Data offset: describes the size of the header.
- Reserved: currently unused.
- The following six bits are control flags for various service data about the packet, particularly, affecting the interpretation of sequence and acknowledgement number fields and an indication that the communications channel should be closed.
- Window: the amount of data octets the sender is allowed to transmit before requiring additional premission.
- Checksum: the checksum for the entire packet, used for error-checking.
- Urgent pointer: if the URG flag is set, indicates where the urgent data ends; not commonly used.
- Options: optional modifiers to the packet, variable size.
- Padding: as TCP headers must be multiples of 32 in size and options is a variable-size field, the header can be padded with zeroes.
The segment’s data can be of variable size.
TCP/IP Packet Transmission
TCP establishes connection between two programs (applications) running on different nodes of a network. This initial connection establishment process is achieved through a three-message handshake where the source and destination side exchange their uniquely chosen send and receive initial sequence numbers (ISNs) (ISI, 1981b). This handshake technically consists of four messages that contain SYN or ACK bit flags:
- SYN sent by the sending system.
- ACK sent back by the receiver.
- SYN sent by the receiving system.
- ACK from the sending system.
Messages 2 and 3, however, are combined into a simultaneous SYN-ACK message from the receiver.
Individual connections are assigned a port number within the system, identifying the sending and receiving applications internally (ISI, 1981b). The data passed down to TCP from the application layer on the sending system is divided into packets, or segments, which are then sent to the receiving node. Each segment is given a header that contains critical addressing and verification data. Once received, the segments are reassembled according to the enumeration assigned in the header. The receiving system also communicates back, acknowledging the reception of each packet; thus, if a packet’s delivery fails, the sending system can resend only that part of the data. This makes TCP a reliable and error-resistant protocol, although it also limits its transmission speed, compared to protocols like UDP.
IP encapsulates the TCP segment with an additional header concerned with routing the datagram to its destination node in the network. Thus, the TCP header follows the IP header in the packet. An addressing scheme is used to identify individual nodes in the network, consisting of a 4-byte IP address in IPv4 and 128-byte IP address in IPv6. A domain name is often employed to identify hosts (e. g. websites) in a way that is easier for humans to recognize and remember. In this case, IP obtains the IP address corresponding to the domain name through DNS before it can communicate with the destination (Schneider & Gersting, 2019). Then, an optimal route is determined between the source and destination through Djikstra’s shortest path algorithm, also accounting for the possibility of network failures when a path between two nodes is unavailable (Schneider & Gersting, 2019). The packet is then passed along the route by pairs of linked nodes until it reaches its destination, where it is finally processed. As seen in the IP headers above, the protocol has a built-in safety feature, time to live in IPv4 and hop limit in IPv6. These fields are decremented at each hop, and the packet is deemed undeliverable and destroyed if they reach zero, preventing network congestion.
References
Deering, S., & Hinden, R. (2017). Internet Protocol, Version 6 (IPv6) Specification). Internet Engineering Task Force.
Information Sciences Institute. (1981a). Internet Protocol.
Information Sciences Institute. (1981b). Transmission Control Protocol.
Internet Assigned Numbers Authority. (2020) Protocol Numbers. Web.
Schneider, G. M., & Gersting, J. L. (2019). Invitation to Computer Science (8th ed.). Cengage.