Introduction
In modern organizations, much attention should be paid to the role of Chief Information Officers (CIOs), who are responsible for establishing effective governance designs and security in companies. In the company under discussion, security issues have led to the problems in the work of the information system (IS) and caused searching for another CIO to address the problem. The purpose of this discussion is to explain the use of the containment strategy against the acceleration strategy and propose the most appropriate governance design for the case.
Essence
In order to support user computing in an organization, it is necessary to follow the containment strategy in contrast to the acceleration one. The containment strategy is based on adopting new and advanced user technologies slowly, with a focus on reducing and preventing organizational risks (Brown, DeHayes, Slater, Martin, & Perkins, 2011). As a result, units and departments do not purchase or install new technologies without the permission and control of the CIO and other responsible persons to guarantee efficiency and security (Tiwary, 2011; Tse, Xie, & Song, 2017).
Thus, the rationale for selecting this strategy is that all departments and units in the organization will follow certain rules and guidelines regarding the use of technologies to increase security and prevent IS challenges. The acceleration strategy is not appropriate for this case because minimal control can be ensured, and the focus is on implementing innovative applications, which is not a solution to the discussed case.
The governance design to be used in this organization is a centralized IS design (Figure 1). The reason for selecting a centralized design in contrast to decentralized and hybrid ones is that this approach allows for controlling all operations, applications, and networks in a company (Brown et al., 2011). Thus, the infrastructure, operations, support, applications, and system development become centralized for all the units and departments. This solution is less expensive and highly controlled with the help of a central IS unit (servers) (Sharibudin et al., 2018; Tse et al., 2017). It is possible to state that the security and productivity of the organization improve significantly when this model is applied.
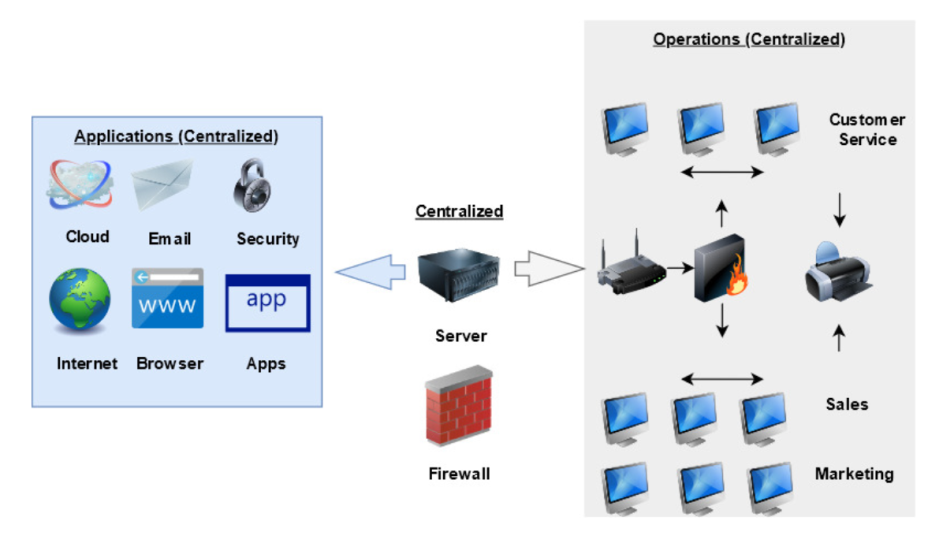
Implementation examples to support the use of the design and strategy are associated with the necessity of applying these systems in a comparably small company suffering from security issues. First, the execution of a centralized design is usually associated with following the containment strategy based on control. Second, in small companies, these solutions contribute to decreasing expenses and hardware costs (Brown et al., 2011). Third, using a centralized structure and a containment strategy, companies adhere to regulations and improve productivity because of eliminating security issues and problems with the flow of information.
Conclusion
The analysis of the CIO role in organizations indicates that this person guarantees that the applied IS governance responds to a company’s needs. As a result, the high-level security of data is provided at minimal costs. If a governance design is selected appropriately, all the IS-related activities are cost-efficient, and all possible challenges can be effectively met. Thus, the decisions of the CIO influence the overall work of the information system in an organization to contribute to its progress and efficiency of operations. In this case, the selection of a centralized governance design and the containment strategy seem to be reasonable decisions.
References
Brown, C. V., DeHayes, D. W., Slater, J., Martin, W. E., & Perkins, W. C. (2011). Managing information technology (7th ed.). New York, NY: Pearson.
Sharibudin, N. H., Asraf, N. S., Razak, M. S. A., Yatin, S. F. M., Ismail, S. A., Ab Rahman, A., & Yu, H. (2018). Ethical issues in managing information in organization. National Academy of Managerial Staff of Culture and Arts Herald, 1(1), 985-989.
Tiwary, D. K. (2011). Security and ethical issues in it: An organization’s perspective. International Journal of Enterprise Computing and Business Systems, 1(2), 1-13.
Tse, D., Xie, Z., & Song, Z. (2017). Awareness of information security and its implications to legal and ethical issues in our daily life. In 2017 IEEE International conference on industrial engineering and engineering management (pp. 1236-1240). Singapore: IEEE.