Introduction
Communication is a process that people have used, developed, and improved since ancient times. In the majority of cases, it is necessary to make sure that information remains protected. The examples of ancient leaders, kings and queens in the Middle Ages, and modern generals show that privacy and confidentiality cannot be ignored to enhance efficient relationships (Singh, 2000). The desire for secrecy provokes the necessity to create some new codes and specific languages. Cryptography is one of such practices where the techniques of secret writing are developed with the purpose of hiding a message’s meaning (Paar & Pelzi, 2010). It is characterized by a list of specific goals and methods (algorithms) that were firstly introduced by Egyptians and have gained high importance today. The evolution of cryptography is a unique topic for discussion because it touches upon all the spheres of human life, including politics, economics, society, and religion. In this paper, attention will be paid to the progress of cryptography through ancient, technical, and paradoxical periods, the worth of common encryption methods, and the impact of coding on modern communication.
Evolution Details
When the use of the Internet as the main source of information is out of competition, society aims to develop critical services and protect individual thoughts, words, and lives. Online security is a concept that is usually associated with such words as “coding” or “cryptography” and the necessity to create a special system where safe data access is possible. Along with the peculiarities of electronic communication, cryptography may be interpreted as a military practice when the British experts broke codes of the German Enigma cipher during World War II (Paar & Pelzi, 2010). However, in fact, the first steps to encrypt information were taken by Ancient Egyptians when the development of writing standards was popular. Cryptography consists of two Greek words, “Kryptos” and “graphics,” meaning “secret writing” (Udugahapattuwa, Amarathunga, & Perera, 2019, p. 21). The names of Caesar, Al-Kindi, Rejewski, Rivest, Shamir, and Adleman contribute to the history of cryptography and promote the evolution of this study (Srivastava et al., 2018; Udugahapattuwa et al., 2019). One of the latest achievements in the chosen field is the use of Quantum computers to find solutions to different mathematical and writing problems.
Discussing the evolution of cryptography, one should identify three critical areas: ancient, technical, and paradoxical. The ancient period is the longest one, starting from the events of 3500 B.C. and ending in the 20th century when military cryptography was developed (Udugahapattuwa et al., 2019). According to Singh (2000), “history is punctuated with codes” that influenced battles and human lives (p. x). Therefore, as soon as the need for cryptography was identified, a number of codes and techniques were developed in regard to the development of humankind. Secret hieroglyphics were introduced by Egyptians, and their system has been used in different forms in many cultures where written language was developed. In the 500s B.C., Hebrew created an Atbash cipher, a well-known reversed-alphabet technique, meaning that the letter A stands for Z, B for Y, etc. (Udugahapattuwa et al., 2019). The next step in cryptography history was the scytale, a military cipher by Spartans, as it is shown in Figure 1.
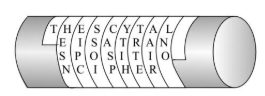
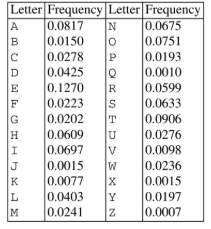
Al-Kindi was a well-known cryptographer who offered frequency analysis as an attempt to investigate the properties of letters through their statistical distribution. As a result, the users of this technique, as shown in Figure 2, had to look at combinations of ciphertext symbols. However, this approach was based on statistical properties that could be revealed by specially trained people because of the lack of randomity, and the story of Mary Queen of Scots and Anthony Babington served as one of the main weaknesses of this cipher (Singh, 2000). Their plan to kill Queen Elizabeth was revealed, and all conspirators were executed.
With time, the importance of strong and sage ciphers was evident, and almost every century, some new ideas were introduced. The most popular ones were Alberti’s polyalphabetic cipher in the form of a plate (the 15th century), Vigenere’s cipher that was easy to understand but hard to break, and Kasiski’s method of cryptanalysis against Vigenere. A technical period (1919-1975) began when people were in need of new codes to complete their warfare goals, and the creation of the Enigma machine by Germans was one of the most remarkable events. Arthur Scherbius designed this method, implementing three major elements such as a keyboard (to put a plaintext message), a scrambler (to encrypt a message), and a display board (to indicate a message) (Singh, 2000). There were 10,000,000,000,000,000 numbers for different states, and Rejeswki, a Poland analyst, cracked the code. Then, a new encryption method, Data Encryption Standard (DES), was created with a 128-bit key size (reduced to 56-bits) as a standard for technical cryptography. At the end of the 20th century, the Triple-DES algorithm replaced recent achievements and attracted attention due to its sized key length.
Each time, a new code is introduced with a thought that someone could break it once. The paradoxical period is known now as the era of public-key (asymmetric) cryptography to encrypt and decrypt messages. One of the latest algorithms was developed by Rivest, Shamir, and Adleman with 4096-bit key (maximum) and got its name after its creators – RSA. However, even this code has already been broken, proving the evolution of the art and introducing quantum cryptography as a limitless science with multiple mechanical properties.
The 1930s vs. the 1970s vs. Today
As it has already been mentioned in the discussion of cryptography evolution, each century is a new achievement with a possibility to learn from mistakes and make necessary adjustments. The period of the 1930s was known for its military ciphers and the necessity to break them and find out the required information. A distinctive feature of 1930s cryptography was the impact of the German Enigma machine. Many attempts were made to break the code, understand the interests of Germans and their tactics, and change the situation in the world. The art of cryptography was politically (war) driven in order not to invent some new techniques but to crack the already existing system. However, the decision of the Japanese to create a new method known as Purple proved that the desire to win the war was a serious motive (Singh, 2000). In both cases, encryption of the 1930s has to be defined as a military practice with the ambitions of global leaders being underlined.
Compared to the 1930s, the 1970s was a period when people were challenged and inspired by a number of opportunities and discoveries. Such organizations, like the National Security Agency (NSA), the International Business Machine Corporation (IBM), and many academic facilities (technology-based), introduced new standards and regulations. The emergence of digital data required the creation of a new encryption system and control devices to protect business and private life. Lucifer cipher was a technique with a secure cryptographic algorithm that was not as complex as DES but effective. The cryptography of the 1970s was based on quantum states and the first steps to connect people via the World Wide Web. Cryptographers and researchers had limited knowledge about the Internet and its potential effects on codes and algorithms. Therefore, unstable and unpredictable studies occurred to check the system and choose the best options.
Today, cryptography is a result of the most sophisticated mathematical algorithms checked by human experience and time. People have already discovered many methods to encrypt and decrypt information and continue improving their skills globally. Talking about modern applications and practices, one should mention the Cloud as one of the most captivating and dangerous things in technology. It is not a product or a service that belonged to one person or organization. It is a collective idea that remains uncontrolled today, and cryptography is the science that is used to understand and control such concepts as the Cloud. Compared to the war-driven era of the 1930s and a digitally challenged period of the 1970s, today’s cryptography is a combination of all the best and worst technological discoveries to gain power, enhance privacy, and promote security in the Information Age.
Encryption Methods
Regarding the history of cryptography, the major point of its development is the transition from mechanical ciphers to digital ones. The mechanical period of cryptography was properly identified during World War II when gearing mechanisms were applied to encrypt texts and protect communication. The most well-known mechanical technologies were the Enigma machine of the 1920s. Digital encryption methods gained recognition at the end of the 20th century when electronic data was promoted, and people needed to protect their data. Compared to mechanical encryption, digital methods vary, including the possibility to exchange information via phones, the Internet, e-commerce transaction, television, and other files.
The change of methods in cryptography means a possibility to overcome some challenges and discover new opportunities. For example, mechanical ciphers are limited to some extent, whilst computers offer ciphers of different complexity (Singht, 2000). The next achievement is connected with speed because electronic ciphers do not require much time to be developed because much work is done automatically. Finally, digital encryption technologies have completely removed the presence of numbers in messages and demonstrated how binary numbers could be applied (Singh, 2000). All these changes were not easy, but they were obligatory because the world continues changing, as well as the art of cryptography and the field of information technology. Digital signatures differ, and there is always a burning need for experts who are ready to recognize codes, read them, and discover the necessary information for protective purposes.
Impact on Modern Communication
Modern cryptography is a complex subject, and its effects and technologies are frequently discussed by researchers, theorists, and philosophers. On the one hand, cryptography is a means to protect people and make sure their communication remains private. There are many situations when people have to keep secrets in the presence of some third parties. They construct specific systems and analyze protocols in order to cover all the aspects of information security and content. Modern communication is full of codes and signs, and applications of cryptography turn out to be good money sources. Data privacy, authenticity, and integrity are the purposes of ciphers that enrich communication and human relationships.
On the other hand, the use of ciphers means the presence of secretes and, as a result, some danger. The governments of countries try to protect their people by any possible means, and the detection of codes is one of the major priorities of national security departments. NSA aims at mitigating its cryptographic standards to make sure quantum computers are compatible with communication protocols but never break the law (Udugahapattuwa et al., 2019). Therefore, multiple debates about the role of cryptography in communication remain open because people cannot come to the same conclusion about how to control the ciphers they create.
Conclusion
In general, one should never reject the fact that quantum computers, information technology, and cryptography are inevitable concepts in the modern world. The evolution of cryptography is one of the longest and the most sustainable practices because it is closely related to the development of humans and technological progress. Despite the fact people used secret information either in ancient times to gain power during the wars to choose the best military strategies in the modern world to be competitive, cryptography remains adaptive everywhere. Its positive qualities, like the protection of personal data or the safety of communication, are as significant as the possibility to hide facts and create threats. The development of cryptography is a human ability, and it has to be improved with time.
References
Paar, C., & Pelzi, J. (2010). Understanding cryptography: A textbook for students and practitioners. New York, NY: Springer.
Singh, S. (2000). The code book: The science of secrecy from Ancient Egypt to quantum cryptography. New York, NY: Anchor Books.
Srivastava, S., Gupta, R., Yadav, A., Sharma, A., Singh, A., & Kumar, S. (2018). Analysis of various factors for encrypted images. International Journal of Pure and Applied Mathematics, 119(15), 2783-2796.
Udugahapattuwa, D. M. R., Amarathunga, A. A. S. R., & Perera, M. A. D. S. R. (2019). The fate of cryptography in a post-quantum world. International Journal of Advanced Tends in Computer Applications, 6(1), 21-26.