Introduction
Information systems security remains a significant concern to many organizations since new risks arise as technology changes. To achieve security, organizations need to use proactive methods of identifying and managing these threats to information. Samimi (2020) states that “The concept of risk management also defines a codified process for identifying and evaluating risks and selecting management strategies and how to deal with them” (p. 131). In 2015, the National Institute of Standards and Technology (NIST), in partnership with other bodies such as the Department of Defense, developed the Risk Management Framework (RMF) to aid in this course (Irwin, 2018). The framework highlights risk management by promoting the creation of security functionalities into information systems throughout the system development cycle (Maclean, 2017). This paper focuses on the NIST Risk Management Framework and explores how it is used in risk management to help organizations in avoiding the consequences associated with organization risk.
NIST RMF
Organizations have to choose system security controls to be applied in risk management using an information security program. The Special Publication 800-53, “Security and Privacy Controls for Federal Information Systems and Organizations,” describes a structured process for integrating information security and risk management undertakings in the system development cycle (Grassi et al., 2017). The NIST RMF provides an efficient framework to aid in choosing appropriate security controls in the decision-making process. RMF uses a risk-based approach which contemplates organization policies, effectiveness, efficiency, regulations, and directives, among other rules (Grassi et al., 2017). Therefore, with an effective information security management system (ISMS), relevant systems can apply the RMF in their risk management process.
RMF Risk Management Process
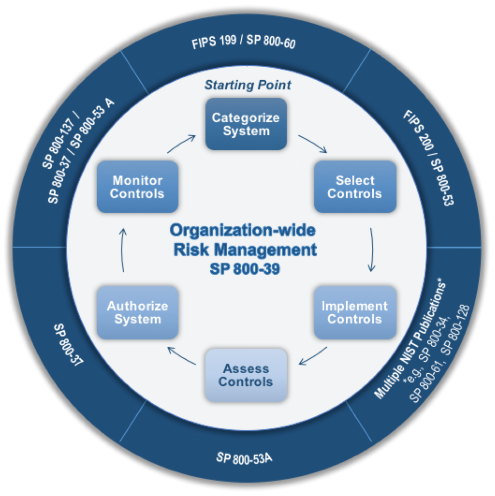
The RMF identified a list of the general activities in the risk-based approach (see Figure 1). According to Irwin (2018), these activities include:
- Categorization: Categorization involves classifying and labeling information processed, stored, shared, and the systems applied. This step is usually done according to impact analysis, which is evaluating the possible side effects of risk upon its occurrence.
- Selection: Involves reviewing the categorization process and selecting of standard security controls. The activity also revises and adds to the security control depending on the risk assessment and internal factors.
- Implementation: Entails the application of security controls and their integration with existing systems. It also involves the documentation of the arrangement of controls in the system and their environmental impacts.
- Assessment: Pertains to the evaluation of security controls to establish whether they are correctly applied or not. This phase also determines the effectiveness and quality of the controls.
- Authorization: At this stage, the security controls are already in use. The enterprise’s top management has to test and accept the information security system regarding how many operational and asset risks the institution is ready to bear. The administration also evaluates the systems’ implications on the employees, other organizations, and the United States. Upon determining how much risk the information system still faces, the management can either authorize, specify the adjustments needed, or reject the system.
- Monitoring: After the information security system has been implemented and approved, a monitoring and assessment program should be created to determine its efficiency (Samimi, 2020). This phase also involves the documentation of system and operation modifications, impact analysis of alterations made, and report findings to the management.
Conclusion
RMF complies with the EU General Data Protection Regulation (GDPR) for maximum security to customers’ personal and private data. This regulation is a significant improvement in the EU data protection policy (Irwin, 2018). The NIST Cybersecurity Framework, which is a voluntary framework, can help enterprises in implementing ISMS. The RMF also recommends adhering to the ISO 27001, among other standards and regulations, as best practices. As an international standard, ISO 27001 helps organizations acquire accreditation in ISMS.
References
Grassi, P. A., Garcia, M. E., & Fenton, J. L. (2017). DRAFT NIST special publication 800-63-3 digital identity guidelines. National Institute of Standards and Technology. Web.
Irwin, L. (2018). An introduction to the NIST risk management framework. IT Governance. Web.
Maclean, D. (2017). The NIST risk management framework: Problems and recommendations. Cyber Security: A Peer-Reviewed Journal, 1(3), 207-217. Web.
Samimi, A. (2020). Risk management in information technology. Progress in Chemical and Biochemical Research, 3(2), 130-134. Web.