Summary
The primary problem of the current project concerned the persistence of cyberattacks and other types of web-based malicious activity which affect numerous organizations and individuals worldwide. All data on networks is transferred in the form of compressed packets, and a proper mechanism is required to ensure that they are safe. The current project attempted to test the viability of Deep packet inspection (DPI) together with Traffic Steering Application (TSA) as a solution to track and prevent various cyber crimes, unauthorized accesses, and intrusions. The main client in the project was the provider of the network service whose network was used as the setting for the implementation of the solution. The project was successful, and all objectives set in advance were accomplished. The DPI solution established effective filtering of traffic in the network systems by white and blacklists of sites and site categories. A dynamic signature library, which could be replenished, as well as actual-time traffic control and dynamic ratification, were deployed. The DPI system allowed information with high priority to pass through immediately while holding the low priority information.
The project took one year to accomplish and was executed in several major steps necessary for its success. The longest period during the project was allocated to the market research and development of the best-possible DPI solution. The following stage involved the installation of the newly-created DPI packets, which were conducted successfully. During the project, the team faced certain issues, including a leave of a key specialist and an unexpected need for more frequent updates to the DPI software. Nevertheless, all of the problems were resolved, and the project demonstrated its utility to the client.
Review of Other Work
The research and development stage of the project required solving multiple challenges and finding ways to make the system work more efficiently. An innovative method proposed by Yin et al. (2019) helped reduce data usage in the project’s DPI by utilizing multiple consecutive characters in the interval of characters. The paper presented a thorough analysis of the finite state automata and the issue of heavy memory usage in compiled time. The use of multiple consecutive characters in the interval of characters reduced both memory usage and the number of automata conversion edges. The decrease in memory caused by the lowered amount of conversion edges offset the extra memory overhead of the maintenance interval tree.
Another problem encountered during the development period concerned the necessity for ensuring privacy when working with encrypted traffic. Research done by Fan et al. (2017) helped the developers realize that SPABox, a system that allows retaining all DPI functions without infringing upon privacy, was the best solution for the current project. Essentially, the system described in the aforementioned paper does not entail any data transmission or interaction between clients and a middlebox. SPABox utilizes a Token Hash Table instead of a searching tree, which allows the middlebox to quickly perform keyword matching and detect malware without violating users’ privacy.
Additionally, there was an issue with ensuring a faster response of the whole system and better responsiveness. Huang et al. (2016) offered a solution for minimizing the size of the delay of flows from switches to DPI proxies, which was particularly helpful for the current project. The paper in detail analyzes the integrated DPI proxy allocation and routing, determining the issue, and offers its method to resolve it. The solution involves using a two-phase algorithm during the first phase of which the K-Median is implemented to solve the proxy selection problem. During the second phase, based on the selection of the proxy, the classical Dijkstra algorithm is employed to find routing paths. Thus, the developers utilized this approach and managed to enable the system to work seamlessly and much more effectively.
Changes to the Project Environment
Original Environment
Currently, most organizations embrace putting on measures to ensure that their information and details are safeguarded. Since most communication agencies, government agencies, and organizations have realized that the pressure piling from their customers is massive, they are calling for safety measures to be put in place to safeguard their information and details. However, despite the efforts by organizations and individuals, there has been a great increase in cases related to cybercrimes and insecurity. As technology advances, the knowledge about hacking and such related crimes has also advanced, especially due to the availability of information in many forms. Proactive measures must be taken to ensure that all networks are safer. Taking more progressive action will help salvage such difficult situations.
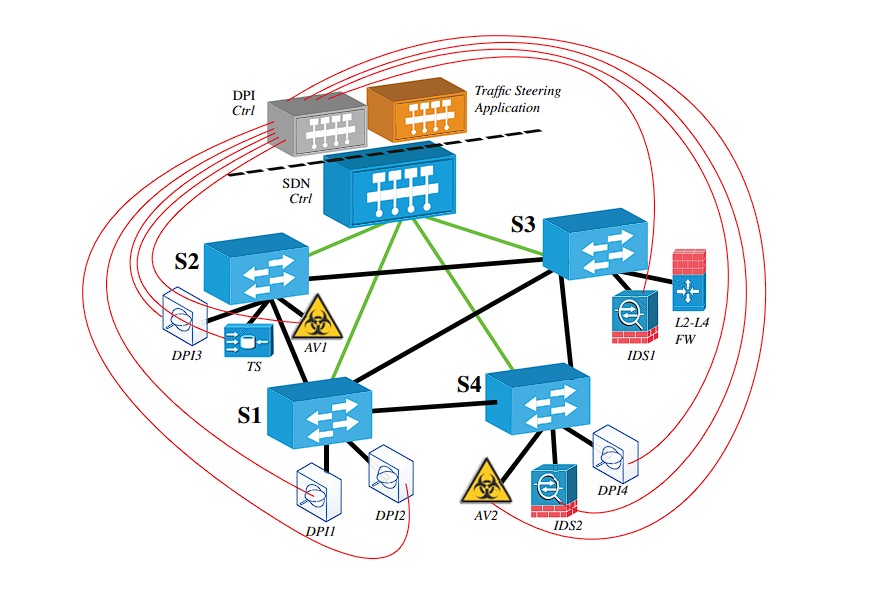
The current programs and systems have done an excellent job in curbing cyber insecurity. However, there is a lot to be done considering that the human population is still growing and the need to have more robust networks. Looking at the users of networks ten years ago and the users now, we can conclude that a lot needs to be done to strengthen the available networks to suit the needs of the world population. In the modern world, nearly everything is done online. Transactions, classes, meetings, and other vital activities are being conducted online, thus creating much stronger networks. The rise and impact of the COVID 19 have made the need for much more potent networks more urgent. Most people and institutions prefer to have their businesses done online, unlike in the past. This has become an opportunity for hackers to exploit the many unsecured networks operational in the network domain, as shown in Appendix D.
Sniffing the network ensures that the information flow within your domain is safe and confidential. With increased communication within the technological environment, sniffing of networks with a DPI is an assurance that insecurities will have lowered, and the chances of any hacker attack will decline significantly. Installation of a DPI in a network domain enables people to monitor network traffic accurately and helps in the identification of the users in the target network environment. Monitoring any abnormal activity within a network domain is more straightforward, especially when people can see all the users in a certain network. Sometimes, because of too many users, there is traffic in each network leading to slow operations sometimes, which users notice from their points of operation. Network service providers do not need to wait for the users to complain about them to realize the network is not operating effectively. With a DPI tool, they will get alerts immediately if the network is not functional or not effective in its operation.
The DPI tool is an effective tool for solving communication problems, and this is the goal of a proper communication tool. Embracing DPI will help to identify a problem before it reaches the end-users hence smoothening the process. For example, when there is one computer connecting with the other, people can identify the specific computers with fault and are in a place to identify the problem and its solution. This is the current situation and the projected future with a DPI tool in a target network.
New Environment
In general, cyberspace today is still under significant threat of intrusions and data breaches since hackers are constantly perfecting their software. Thus, no considerable change has occurred over the period of project implementation on a large scale. Nevertheless, the current project was successful in terms of reducing the incidence of malicious attacks on the network, which was used as the subject of the experiment. In other words, once the team of developers launched the newly-designed DPI and made it active, in the next weeks, an improvement was already observed. The DPI demonstrated its utility in filtering all types of anomalies, including viruses, spam, and intrusions allowing the users to be more protected. Nevertheless, during the first weeks after the launch, the network experienced a slight slowdown due to the DPI requiring a considerable amount of resources. Yet, the problem was later solved by utilizing multiple consecutive characters in the interval of characters and thus reducing data usage.
Methodology
The specific methodology employed in this project was prototyping the DPI packets. The most important and crucial step was to ensure the DPI controller was well implemented since it was the major component of the DPI packets. There was a need to maintain proper communication between all the parts using the DPI services, such as the middleboxes, instances, and traffic steering applications. An appropriate inspection of all the DPI instances available in the network and all the rules and policies was conducted since it was crucial for division of management in the dpi instances and facilitation of where each dpi instance has to be placed in the policy chain.
Ensure the DPI Controller Acts as a Server for all Instances and Middleboxes
Since the DPI controller acts as a mediator for all other parts in the DPI packets, it was set to act as a server. Proper settings enabled the controller to capture all the instances and middleboxes, communicate with all other components of the DPI network, and register any new connection. Setting the DPI controller to act as a server also enabled it to detect any disconnection in the network and act accordingly.
Matching of the Set Rules
Matching the rules enabled the DPI controller to assign a specific id to each practice and ensured that each identical regulation had the same id. With matched rules, the DPI control had the ability to aggregate all similar laws from each middle box and then inspect each packet only once. During this stage, the developers introduced a mechanism to prevent repeating inspections every time the rules did not match. To achieve such workability, the DPI controller was made to recognize each internal id. With matched controls and assigned Id, the controller had a memory of all the rules added or removed from the network throughout its lifetime; hence no foreign activities or intrusions occurred in the network without its knowledge. Such a decision allowed the system to detect all malicious activities on the network.
Division of Match-Rules to Instances
When implementing the DPI packet, it was crucial to understanding how to divide rules among instances. Thus, the developers properly examine any change in the configurations, such as removal or addition of middleboxes, changes in the policy chains, or instance or match rules. The developers did a thorough examination of all previous considerations, designed algorithms, and tested them in various situations and different environments before they found the optimal solution in the division of the match rules. To create a system that can work well and demonstrate this design, network providers needed to employ these simple division policies.
- Balancing of the matching rule load-The goal of this policy was to ensure utilization of all instances available in a network and still maintain the same number of rules in each instance.
- Balancing of the policy chain load-The goal of this policy was to make sure all the policy chains were divided equally such that every policy chain assigns one instance. If the instances were not enough for each policy chain, then some could share a model.
Development of the Corresponding Policy Chains
After the division of rules, the DPI controller placed all the dpi instances in the correct position in the network, where each middlebox was placed after every model that served it with rules. The controller applied its knowledge of the middlebox and instance rules to map each of the policy chains to achieve this. Balancing the chain load policy was applicable here to retrieve a strategy for each approach, then assign it and place it at the beginning of the chain.
Pushing and Pulling Policy Chains
The DPI controller pulled and pushed all the policy chains to the traffic steering application in both buildings of the new policy chains and division of the match rules.
Reacting to Changes in the DPI Network
The DPI controller system received all notifications regarding instances going up and down, added, or deleted rules, middleboxes, or changes in the policy chains. During such instances, the controller reacted immediately and acted according to the previous requirements.
Project Goals and Objectives
Goals, Objectives, and Deliverables Table
In detecting the applications being used in a network, the DPI packets used certain checkpoints in the network to evaluate all the activities taking place in a specific network. In addition, the DPI system applies the rules provided by the administrator, network provider, or the network system and determines what to do with the data to ensure no unauthorized applications. In the analysis of the data usage, the DPI inspected the data being sent across the networks and then acted by blocking, alerting, or re-routing. When there were too many users within a given network, the DPI also played a crucial role in redirecting the network traffic to avoid congestion and hence ease congestion, therefore, facilitating smooth operations. DPI facilitated network management in that it allowed information with high priority to pass through immediately while holding the low priority information.
In addition, it prioritized mission-critical packets before the ordinary browsing packets and slowed down the rate of data transfers if problems arose with peer-to-peer downloads. Once the DPI packets had achieved the goals and the objectives outlined above, they automatically accomplished the deliverables such as easing traffic congestion in a network and preventing and detecting cyber-attacks; hence, people were not able to access other people’s information and data security. With such packets, people could send their emails, Skype, tweet, and operate on all social media platforms without being worried about the safety of their information. In addition, all businesses, organizations, and government agencies doing their jobs online could store their data safely without fear of intrusion or loss of data.
Apart from providing an analysis of all the content that entered the network, DPI packets also monitored, slowed down, speeded up, filtered, blocked, and made decisions about traffic in the network. DPI also served as an effective method for detecting intrusion in the systems and preventing these intrusions. DPI protected users’ computers from spyware, fireworks, and other forms of viruses.
Project Timeline
Initially, the project was divided into two main stages, and equal periods of time were allocated to each of them to ensure a well-balanced workflow with attainable deadlines. Nevertheless, during the first stage, the project did not go as planned, and certain elements of the work were delayed. Primary, the delays were associated with various challenges which arose during the process of development of the new DPI. Thus, the decision was made to prolong the first stage to seven months total. Yet, despite taking a month away from the second stage, the team was able to improve its performance, and eventually, the installation of the TSA was done in five months.
Unanticipated Requirements
As it was stated earlier, the project encountered numerous issues along its way, which had to be resolved to guarantee its success. One of the main problems the team faced during the first stage was the leave of the leading advisor to the developers on the DPI topic. The person decided to abandon the project, which led to a situation where the team had to quickly learn and test different solutions to ensure the proper functioning of the system. Additionally, after the launch, the need to update the DPI software emerged since new types of anomalies were being generated every week. Initially, the team did not expect the software to require updates so often, and, as a result, it made the new solution harder to manage. The team resolved the issue by creating a task force committed to revising the code and adding new segments to it.
Conclusions
The projected outcomes of this project were quantified in terms of the expected impacts. After the launch of the project, users experienced the following deliverables and outcomes.
- There was effective filtering of traffic in the network systems by white and blacklists of sites and site categories.
- There was a present signature library that was dynamic and could be replenished.
- There was an actual time traffic control and dynamic ratification.
- The DPI system also detected any application traffic based on signature and statistical analysis, which included IM, Voice P2P, game traffic, video streaming, video over IP applications, and encrypted data.
All of these results were achieved through the successful implementation of various features, which not only protected the networks but also minimized the DPI’s negative impact in terms of their speed. The primary metric used to assess the effectiveness of the project was the number of anomalies detected weekly before and after the launch of the project (Appendix A). The new DPI solution demonstrated a significant increase in the number of detected anomalies after its full launch in January 2021.
Project Deliverables
There are various types of materials that demonstrate the completion of the project and its success. For instance, Appendix B depicts the DPI system and how connectivity among each of its elements is maintained. The image features the complete DPI system of the current project, which shows that there are no breakages of the plane’s abstraction. Moreover, Appendix C contains one of the interfaces of the DPI software, which lists all of the anomalies and makes them visible to the user. Such data can be important for determining which types of malicious activity are more persistent than others. Finally, Appendix D demonstrates how the project’s DPI controller exercises control over DPI service instances on the network while packets are distributed through the network as policy chains dictate.
References
Fan, J., Guan, C., Ren, K., Cui, Y., & Qiao, C. (2017). SPABox: Safeguarding privacy during deep packet inspection at a MiddleBox. IEEE/ACM Transactions on Networking, 25(6), 3753–3766. Web.
Huang, H., Li, P., & Guo, S. (2016). Traffic scheduling for deep packet inspection in software-defined networks. Concurrency and Computation: Practice and Experience, 29(16), 1–8. Web.
Yin, C., Wang, H., Yin, X., Sun, R., & Wang, J. (2019). Improved deep packet inspection in data stream detection. The Journal of Supercomputing, 74, 4295–4308. Web.
Appendix A
The Monthly Detection of Network Anomalies
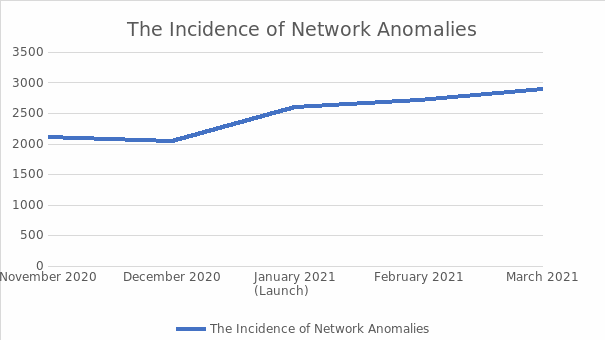
Appendix B
DPI Controller Architecture
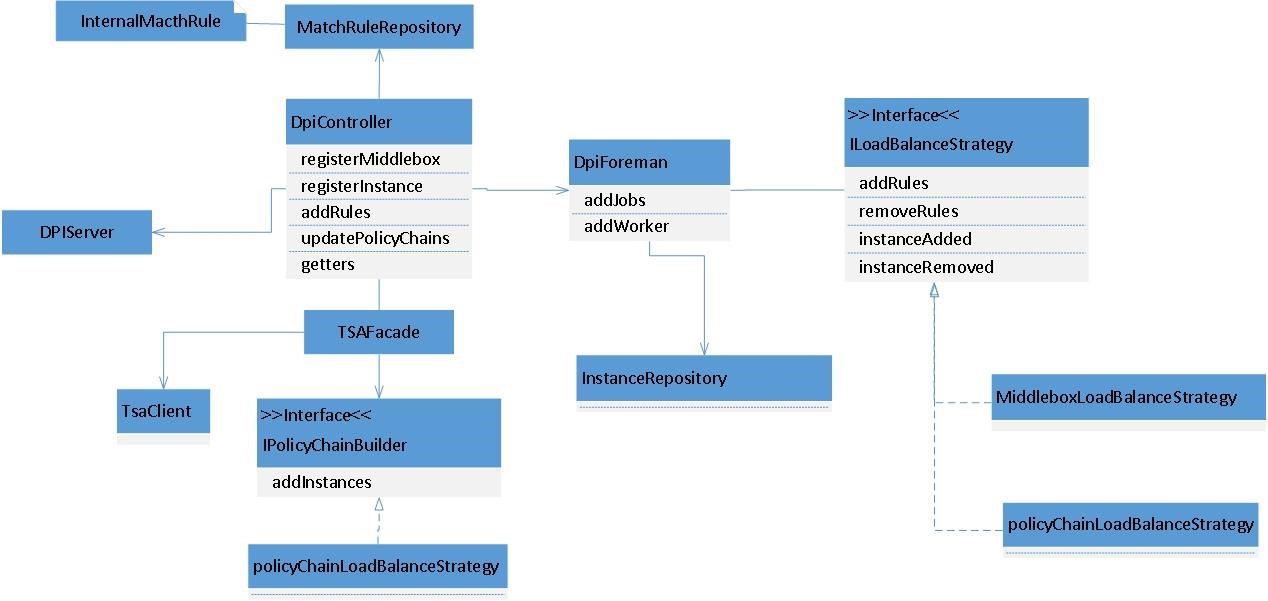
Appendix C
The Interface of the Project’s Software
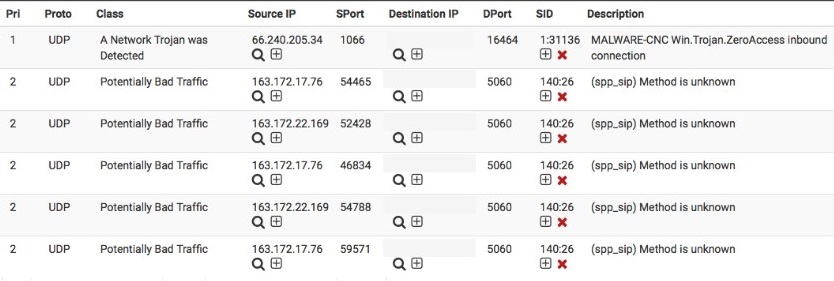
Appendix D
The Architecture of the Project’s DPI and TSA System