Mobile Forensics is a term used in reference to the act of retrieving information from mobile phones (Mobile and PDA Forensics 2007). The current population is increasingly using mobile phones as a tool for personal communication and as such, the device is valuable in a majority of the legal cases, as a piece of evidence. Mobile phones will continue to find valuable use in the field of e-commerce in the coming days, while the importance of mobile evidence will become even more important (Vijayashankar, 2004). Nonetheless, if this technology is not properly understood by the police, judges and lawyers, there is a high likelihood that wrong judicial decisions may be arrived at. The police are however faced with legal and corporate bureaucracy in their attempts to retrieve information from mobile phones, as evidence from The Wire, the much-admired police procedural masterpiece by David Simon. The master piece depicts vividly how difficult it is for the police to obtain actionable mobile forensics (Simon 2002).
BlackBerry
Since 1999, Research In Motion (RIM) has been involved in the design and development of BlackBerry, a wireless, two-way and handheld Smartphone device. BlackBerry may be used as a portable media player and a personal digital assistant. These devices are mainly popular because they enable users to receive and send internet e-mail via Wi-Fi connectivity, or using mobile network. BlackBerry phones support various messages features, such as the BlackBerry Messenger. RIM first introduced the 850 as its first BlackBerry in 1999 in Munich, Germany, as a two-way pager (Unnikrishnan 2008). As an end-to-end wireless email solution, the BlackBerry enables users to access the Outlook Inbox, Contacts, Tasks, and Calendar, with full wireless synchronization. The local server to which the BlackBerry is continuously connected to monitors the exchange of data between the device and the Local outlook. Once a notification is registered on the Local Outlook, it is automatically copied by the server and relayed to the BlackBerry via internet connection (Unnikrishnan 2008). The same process may also be used to copy information from the BlackBerry to the Outlook mailbox. This means that any additional new contact to the BlackBerry shall automatically be added to the outlook contact list as well. One can access communication between the Internet and BlackBerry device without the need for physical connection because wireless technology controls the overall connection.
Motivation
The use of digital forensics in investigation is slowly gaining popularity. However, only a limited amount of research has been done on the field of mobile forensics. The current researcher visited the Abu Dhabi Police to gain further insight into the study of digital forensics in the UAE. Only a handful of the locals are involved in the digital forensics field and as such, this gave us the motivation to undertake an in-depth analysis of the Small Scale Digital Devices (SSDD) in the field of digital forensics. Specifically, the current research intends to examine various BlackBerry devices. The number of BlackBerry users in the UAE is expected to have doubled, meaning that as investigators we also expect a variation in the amount of data that we can retrieve from a single device.
Skills
The present research demands learning and application of various skills. Although we had background knowledge on mobile forensics, it was still necessary to read cases and books related to Digital or Mobile Forensics. This enabled us to enhance our reading skills and technical knowledge on the topic at hand. In this case, technical skills become a priority because we shall be using only a handful of BlackBerry devices, but a variety of software. The importance of communication skills cannot be underestimated in any project. In the current project, these skills shall enable us to communicate effectively as a team. In addition, communication skills enabled us to contact the Abu Dhabi Forensics Lab, thereby helping to answer our questions and increase our knowledge.
Literature Review
Efficient Forensic Tools for handheld devices
The use of hybrid hand held device has increased exponentially in the market and this could be an indication that these devices shall find increased use in criminal activities (Akkaladevi, Keesara & Luo, n. d.). These hand held devices are characterized y such technical capabilities as Global Positioning System (GPS), camera, and Personal Digital Assistant (PDA), thereby providing the user with greater capabilities. These hand held devices are now a great challenge to investigators and law enforcement officials alike because of the new and emerging features (Akkaladevi et al. n. d.). Although forensic investigations reports show a strong association between the approaches and applied methodologies, nonetheless, there is the need to develop better toolkits to assist in forensic investigations. Forensic experts undertake forensic examinations using the laid out procedures, analyzing the minutest of details using PCs. Afterwards, specialists are called in to carry out tests and examine the individual cases using available data. In this case, they have to use specific tools that have been tailored to suit certain design specifications. A number of these tools utilizes volatile memory prone to data loss, and are powered by battery. Nonetheless, while undertaking forensic examinations, it is important that forensic experts captures and recover deleted information using such portable devices as e-mail addresses. Some of the forensic tools that find application are discussed below.
Small Scale Digital Device Forensics ontology
The SSDF is a relatively new device in the field of forensics and may perhaps explain why the procedures and forensic methods that utilize this device still remain somewhat unclear. The paper intended to develop an ontology that would allow law enforcement officers access to the necessary knowledge on the various devices that constitutes the SSDD domain (Harrill 2007). Moreover, such an ontology so developed could find use as a platform for the development of a set of actions and standards for approaching SSDD. There are two main categories of Digital Device Forensics namely, the Small Scale Digital Devices and the Large Scale Digital Devices. SSDF is a relatively new addition in the field of Digital Forensics. The new addition entails new but growing technologies that besides being multipurpose, also happens to be smaller in size. Consequently, investigating or trying to identify such devices proves to be a tall order. On the other hand, the research paper has also endeavored to explore another technological breakthrough whose design would enable the achievement of a number of tasks. Various devices such as the Smartphone, memory card, the digital audio layer and notebook computer, among others devices, all finds their way into any scene of crime (Harrill 2007). When the various types of small scale devices were measured cell phones merged as the best example of small handheld devices. Nowadays, most cell phones acts as movable PCs and in the same way, some of their features facilitates their use in committing crimes. A focus on the small scale digital devices was also informed by the fact that ultimately, all storage devices will have to reduce in size. Sadly, the pace at which forensic tools are being developed is not in tandem with the rate at which these devices are reducing in size.
Guideline on Mobile Phone Forensics
The white paper gives a comprehensive review of emerging mobile phone technologies, their contribution in the field of forensic science, how they relate with the field, approaches and procedures in presenting and retrieving digital data in mobile phones, and software tools that finds application in emerging technologies and practices. The white paper provides a detailed guideline on the application of such advanced technical features as text messaging, data and voice communication in mobile forensics (Jansen & Ayers 2007). As a discipline in forensic science, mobile phone forensics focuses on how the digital data that has been retrieved from mobile phones is used as a source of forensic evidence, on the basis of established standards. Though not legally binding, the prime goal of the guide is to enable forensic specialists and organizations to tailor, formulate, handle and enforce procedures, laws and policies governing mobile phones under different circumstances.
Nonetheless, it is important to seek legal advice from the appropriate professionals on individual laws and cases (Jansen & Ayers 2007). There is a need for organizations to come up with explicit forensic policy statements that clearly defines the reporting relationships of external and internal workforce, their responsibilities and roles, handling and recording of sensitive information, management support, legal companies, endorsing of forensic activities, and policy reviews, if they are to effectively benefit from their forensic investigation efforts.
iForensics
The useful internet capabilities of Smartphones are one of the handy features that have led to their popularity. The Instant Messaging (IM) feature of Smartphones in interpersonal communication has led to their popularity as well. The increased popularity of Instant Messaging also makes Smartphones a cheap target for committing such cyber crimes as cyber bullying and cyber stalking (Iftekhar & Sridhar 2009). Various Smartphones are characterized by different storage devices and file systems and these features also present forensic examiners wilt new challenges as they attempt to retrieve and recover evidence of digital conversation while conducting an investigation. This is despite the fact that the current IM application feature in Smartphones is inferior to those in use by traditional computers (Iftekhar & Sridhar 2009). By Google talking the current topic on iPhone (using both the web and client based versions) the researchers realized the significant value of examining the IM application on Smartphones.
Mobile Device Analysis
As the use of mobile phones increases, there is a resultant increase in the design and development of mobile phone device techniques and analysis tools. The variety in handheld devices, each with its unique system, has also helped to expand the field of digital forensics (Punja & Mislan 2008). Nevertheless, the paper aims to provide background information on mobile forensics to forensic practitioners. In addition, the paper shall attempt to summarize the familiar cell phone technologies, deice handling techniques, and their characteristics. The paper also provides specific information on iPhone and BlackBerry devices. However, information on detailed methods for extracting/analyzing data from mobile devices, along with how different toolkits are used is outside the scope of the paper. This is because there are so many Cell phones in use, and the numerous details of their individual toolkits complicate the activity (Punja and Mislan, 2008).
Methodology
Overview
The main focus of this capstone project is on the application of Forensic tools to assess BlackBerry devices. The results from the various types of BlackBerry devices shall then be analyzed for purposes of comparison.
Timeline
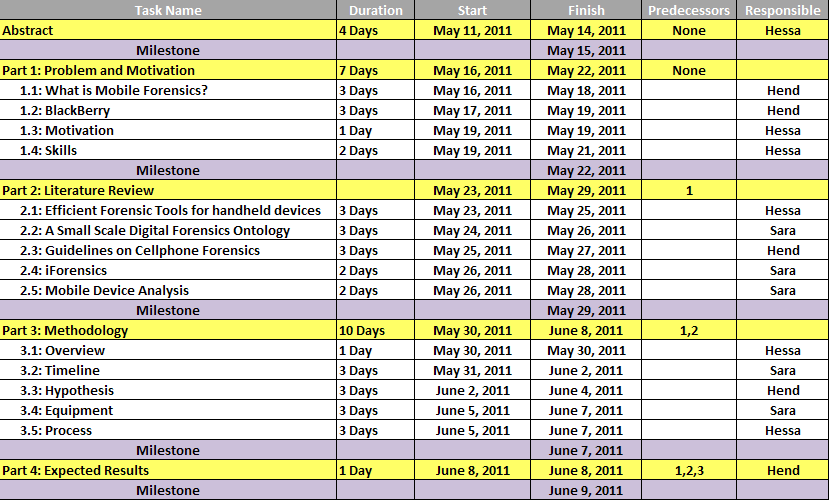
Hypothesis
Retrieving information from mobile devices with a view to formulating enhancement strategies remains a key objective of mobile forensics. Mobile devices facilitate communication between individuals, besides serving as entertainment tools. However, the use of these devices also poses high level risks to both individuals and organizations. As a result, they are valuable tools in as far as tracking of criminals and crimes are concerned. The aim of undertaking the current research is with a view to establishing the legitimacy of the stated tools in as far as blackberry forensics is concerned. The technological world is currently engulfed by a wave of revolution, a trend that is expected to shape the modern world in the coming years. Consequently, there is a dire need for additional modifications to improve the tastes and interest of the users. Mobile telephony devices are not an exception and for this reasons, they come with such enhanced features as personal digital assistance, camera, and global positioning systems. Each of these individual features has been customized to meet the needs of the users. However, this has only acted to enable criminals commit crimes using these devices without necessarily being physically present at the scene of crime. In addition, it has complicated efforts by law enforcers to locate criminals because using modified technologies, they can now forecast the movements of the police. The present case hinges upon the null hypothesis that tools employed by mobile forensics are ineffective because the authorities have failed to combat crimes. On the other hand, the alternative hypothesis states that tools employed by mobile forensics are effective, and the only modification needed is to update the features to match with technological changes.
Equipment
XRY
XRY is a forensic system written by Micro System, and has specially been developed to assess mobile digital devices. Running the software into a mobile digital device helps to retrieve information contained therein. It can either display the results immediately, or save files that when run on Windows, facilitates in the data analysis (Systemation 2011). The writing support level of XRY includes GPS units, Smartphones, as well as such mobile tablets as the iPad. The complete XRY package contains both software and hardware to further enhance the process of reading information from these devices. Examples of hardware included in the XRY package include SIM Card Reader, XRY Communications Unit, Write-Protected Memory Card Reader, Clone SIM Cards, and Complete set of Cables. A USB cable is connected to a Windows computer, and the hardware facilitates the display of results extracted from the device.
Mobiledit!
This tool has gained recognized worldwide as the most efficient toll in phone investigation. More than 70 countries use it for this purpose. The National Institute of Standards and Technology has rated this tool very high, and is also capable of extracting all the content and creating a full report acceptable for presentation in court (Labs 2011). The tool has enabled the presentation of flawless and tamper-proof reports in numerous courtrooms.
Oxygen
Oxygen Forensic Suite is a type of mobile forensic software that has found use in the undertaking logical execution of different kinds of Smartphones, cell phones and PDAs. The function of this toll includes extracting event logs and device information, data mining and message analysis, among others. In addition, the toll has been known to provide better data analysis when working with different devices. Although there are various versions of the device, the current research shall make use of version 10.
Process
The first step of this capstone project was the choice of topic, and the group settled on topics involving Mobile Forensics. With the support of Dr. Andrew, our advisor and Dr. Huwilda, his co-advisor, we managed to visit Abu Dhabi Forensics where we were able to obtain information on Mobile Forensics. Later, we compiled notes on the visit and held a meeting with the group’s advisors to facilitate a discussion on the topic to choose, what to focus on, and the next course of action. We then researched on the topic of digital and mobile forensics using journal articles and books. Considering that this is a new topic that is slowly gathering pace, we reviewed research and white papers as the main source of our literature. After introducing the topic, we stated the problem and motivation for the research. An overview of the topic was also provided in the Methodology Section, a timeline provided, the hypothesis stated and equipment mentioned and finally, the process of the project. The Expected results section finalizes the capstone proposal. The actual project shall be implemented in the forthcoming semester, starting with an introduction of how each software functions, followed by testing each of the BlackBerry devices on all software. Finally, the research findings shall be analyzed to yield results which will then be compared with each Blackberry device.
Expected Results
The current research does not allow for an unequivocal and ultimate conclusion. This is because the mobile tracking devices are involving in tandem with the rapid changes in technology. For this reason, security remains a big challenge for these devices, even as novel techniques of containing this challenge are continuously being developed. Even as mobile device developers come up with novel ideas on a daily basis to enhance communication, on the other hand, criminals make use of the same devices to enhance their crime rates. Furthermore, each of the two groups is hell- bent on ensuring that the invented technology advances its individual interest in a creative manner. There is a need to take into account the null hypothesis for the current research because much of the evidence obtained show that crime emanating from the use of mobile devices appears to outshine the original application for which it was intended. This may perhaps justify the need for forensic personnel to formulate novel techniques to contain mobile crimes, other than the application of mobile devices alone. On the other hand, the forensic experts may decide to keenly assess the operations of the criminals and formulate strategies to counteract such operations.
Reference List
Akkaladevi, S., Keesara, H., & Luo, X., n.d.. Efficient forensic tools for handheld devices. Web.
Harrill, D. C., 2007. A Small Scale Digital Device Forensics ontology. Web.
Iftekhar, M., & Sridhar, R., 2009. iForensics. Web.
Jansen, W., & Ayers, R.. 2007, Guidelines on Cell Phone Forensics. Gaithersburg: National Institute of Standards and Technology.
Labs, C., 2011. MOBILedit! Forensic Overview. Web.
Mobile and PDA Forensics., 2007. Computer Forensics. Web.
Punja, S. G., & Mislan, R. P., 2008. Mobile Device Analysis. Web.
Simon, D., 2002, The Wire [Television series]. Baltimore: Home Box Office Productions.
Systemation, M., 2011. WHAT IS XRY? Web.
Unnikrishnan, P. K., 2008. Blackberry Technology, A Seminar Report. Cochin Institute of Science and Technology, Kochi.
Vijayashankar, N., 2004. Mobile Forensics: a new challenge. Web.