Introduction
Computer security and data safety have become the stepping stone for most organizations and individuals. In general data protection and informational safety require increased attention and awareness of the users. Forensic software may be used for various aims, however, the key functionality range is closely linked with data safety, though, these may be used either to protect or to harm the data stored. The key aim of the paper is to analyze the forensic software tools available and, give a detailed description of the functionality range for each software tool or tool pack.
Penguin Sleuth Forensic
This software tool pack is the extended edition for WinHex codes. This involves numerous features that involve various analysis tools, disk editing software pack with lots of useful features and functions. The software is suitable for a range of file systems such as FAT, FAT32, NTFS, Linux Swap, and Raiser FS. Additional tools are Bates-numbering files, picture gallery creation and checking, file preview, and calendar functions for scheduling and planning tasks. The key functional value of this software is the opportunity for low-level disk monitoring and the opportunity of cloning.
Method
The method that is implemented in the Penguin Sleuth software tool pack presupposes bite-by-bite file analysis. On the one hand, this requires more time for analysis in comparison with other tools. On the other hand, this provides better analysis especially if the type of file is unknown. Moreover, this analysis type is more reliable for a low-level disk analysis. (Sturgeon, 2008)
Because Penguin Sleuth Kit is a bootable CD pack, hence, it provides an opportunity to reach every file which may be blocked after system startup. This software pack is aimed at adapting Linux resources to perform a forensic analysis of the entire system and providing effective Security Auditing measures.
How It Works
Penguin Sleuth Kit is aimed at working with various Linux models that are based on different principles of system file arrangement. In general, the key feature of Penguin Sleuth is the opportunity to examine an offender’s computer without leaving any evidence of examination: no data of examination is left on the hard drive. Moreover, it provides an opportunity to view and check multiple operating systems without any complications. The specification of the development presupposes that the pack may be run on Debian and Linux versions, as well as some desktop environments. It is used with OpenOffice.org, AbiWord, The Gimp, Konqueror, Mozilla. The default environment is KDE, which may be used with Gnome and several other environments. (Virtual Appliances, 2010)
Where Obtained
This software tool is free and may be obtained from the official Penguin Sleuth. Web.
Additionally several mirrors may be available, however, it should be emphasized that the software pack is free, and distributed without any restrictions. The version that was used for the analysis was downloaded using p-2-p network.
Author and Company
Penguin Sleuth Kit was created by Klaus Knopper, who works for Knoppix Linux distribution. (Cosgrove, Robi and Rismann, 2009)
Size
Archived version needs only 700 MB of disk space.
Functionality
The principle of its work presupposes searching files all through the system without interrupting the order of files. Hence, it may search files in accordance with the key word and in specific formats, browse internet history, search in recycle, temp files, favorites etc. As for the deleted files, it should be stated that the system generally does not delete files, however, it removes references for the file, so, the other information may be recorded to this place. Considering the fact that low-level structure involves this information (or part of it) until the disk is formatted, Penguin Sleuth may restore and review these deleted files. Actually, there is no need to extend the functionality by adding supplementary programs, however, it may be repacked by volunteers, as this is the open source project.
Screen Shots
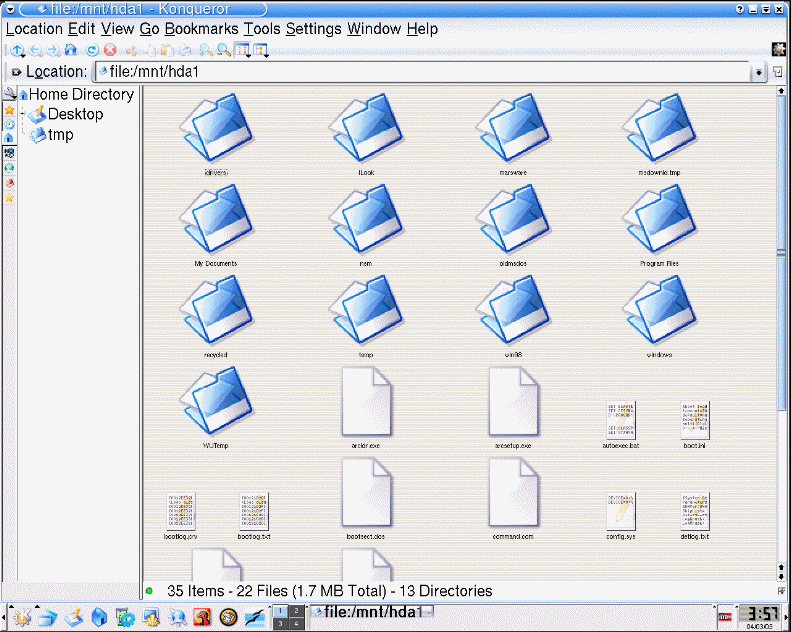
The system analyzes files independently of its extension, and defines the bit structure which differs in accordance with the file purposes.
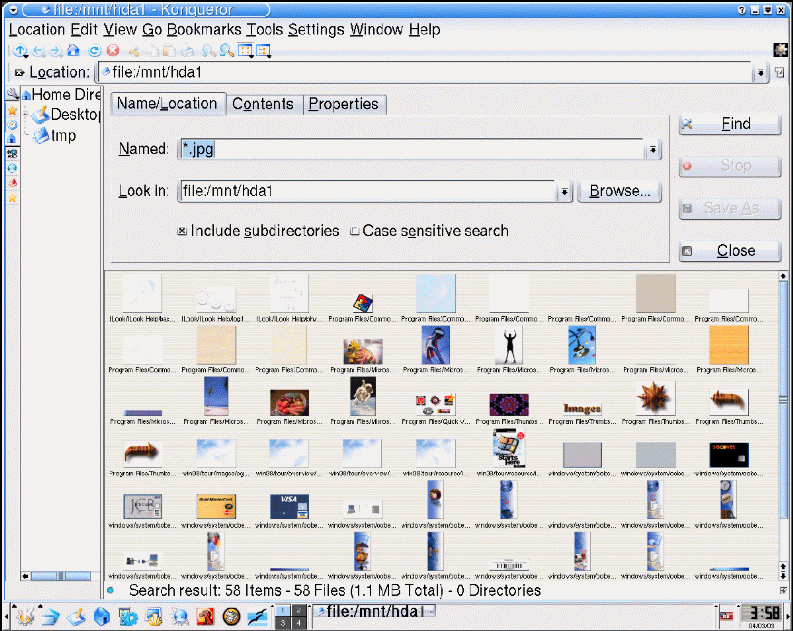
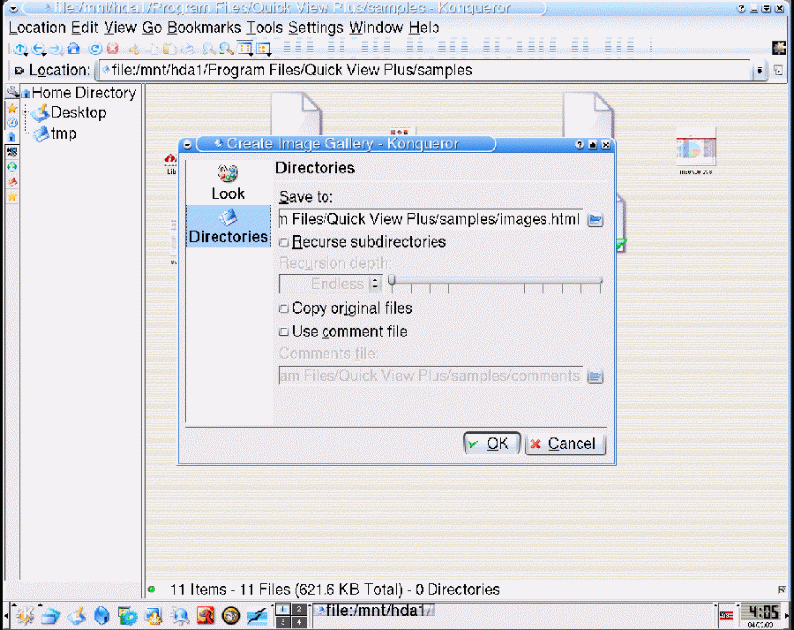
Actually, it is hard to evaluate software packs by reviewing their screenshots, however, the results that may be made in accordance with the offered screenshots are that the software is effective for searching files and analyzing the bit structure of files found. (Baca 2010) Picture gallery is not too effective, as it may be used only during the session. Forensic options of the tool presuppose effective and quick analysis of the files available, and provide the extended range of options associated with the matters of checking files for security (virus and worm check), availability and presence of the necessary system files, assessment of file browsing history and internet browsing history for checking whether prohibited files and sites were opened. (Baca, 2010)
As for the usage difficulty, it requires some knowledge of system structure and file origins, as extended analysis requires awareness on the matters of bit structure. This is of particular importance when renamed, deleted or files with changed extension are analyzed. Hence, the tool is not for wide usage, and may not be applied by inexperienced users.
Advantages and Disadvantages
The pack is intended for extensive file and system analysis using boot CD. This technology is helpful for analyzing the shutdown system when all the system files are available and not blocked by system processes. Additionally, the software tool is effective for analyzing various types of files, as the actual importance of forensic analysis is confirming the availability of files of particular origin.
The key advantage of the kit is that the project in general is open source, and it may be extended or repacked depending on the requirements of any user. Considering the nature of Linux environment malware is ineffective for these software packs, however, in order to avoid any harm, the kit may be downloaded from the official site.
The disadvantages are not evident: it is impossible to create search and analysis profiles, as the system does not have any operative space, and does not have an opportunity to leave anything on the hard drive or any other storage.
Project Executive Summary
The project itself is reliable and effective for file and system analysis, however, the target audience of the tool pack is essentially restricted. In general, this may be used or searching files of a particular contents, and this search is performed not only among the open and unrestricted files, but also among deleted and hidden files. The opportunities of this system are immense, and the functionality is wide enough, however, user needs to have essential experience with nix system operations, as Penguin Sleuth software pack is not intended for inexperienced user.
Reference List
Baca, E (2010) The Penguin Sleuth Kit. penguinsleuth.org. Web.
Baca, E. (2010) Kicking it up a notch!!!! New PSK Plans. Penguin Sleuth. The Ultimate Computer Forensics and Security Platform. Web.
Cosgrove, J., Robi, E., & Rismann, D. (2009). Should Experts Also Be Private Investigators?. The Forensic Examiner, 15(3), 7.
Sturgeon, J. (2008). CSI: Hard Drive Hate Groups, Terrorist Activity, Pimping. A Day in the Life of Local Law Enforcement? No, Just a Routine Sweep of School Computers. Digital Forensic Technology Is Uncovering the Bad, Sometimes Criminal Behavior Students and Faculty Are Guilty Of. T H E Journal (Technological Horizons In Education), 35(1), 22
Virtual Appliances (2010) Penguin Sleuth Computer Forensics and Security Appliance for incident response and Testing. VMWare. Web.