Since the aim of the questionnaires was answering the question of “What are the threats to privacy in the twenty-first-century data collection?”, the analysis of respondents’ attitudes toward the key problem will focus on several important indicators. The first aspect relates to respondents’ demographic data about questionnaire’s respondents. This type of data is important because of the existing interrelationship between economic and social characteristics of a population and its approaches toward a particular phenomenon (Treiman, Lu, & Qi, 2012). The results are presented below:
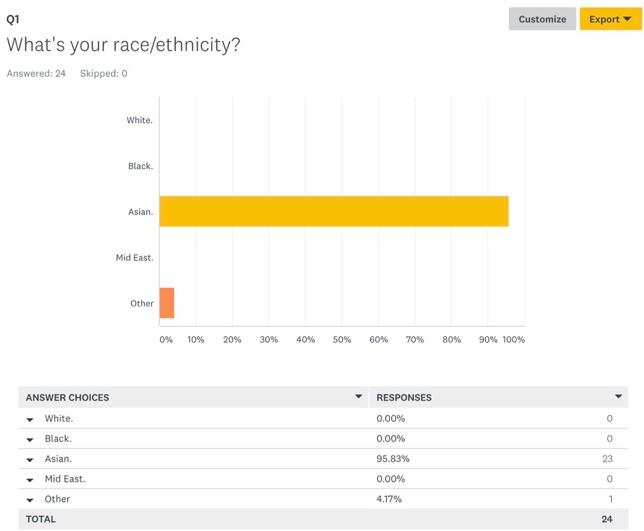
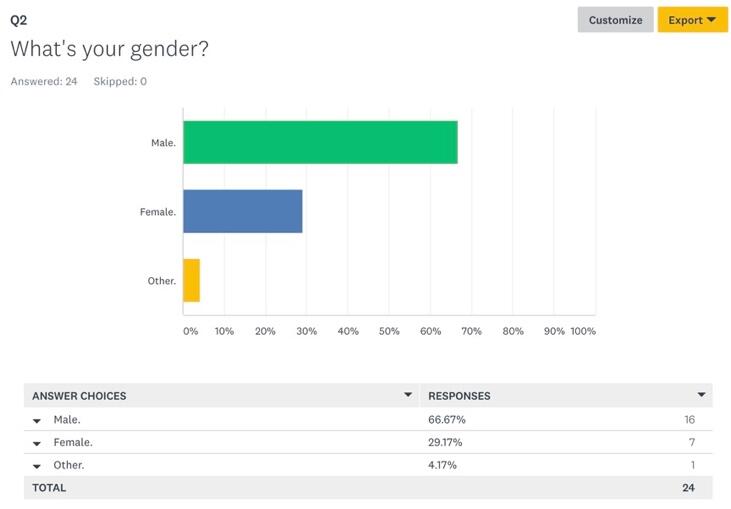
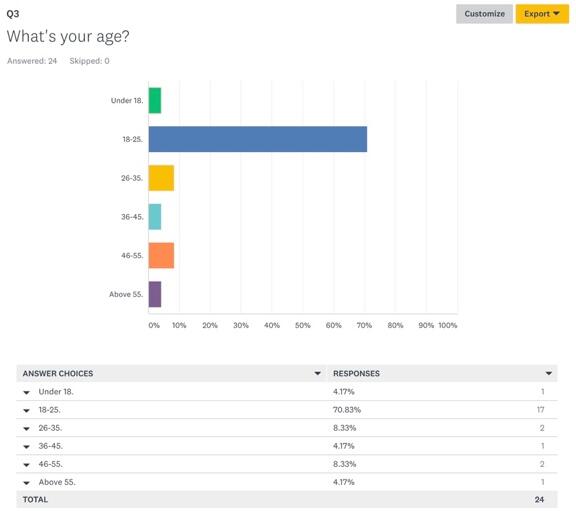
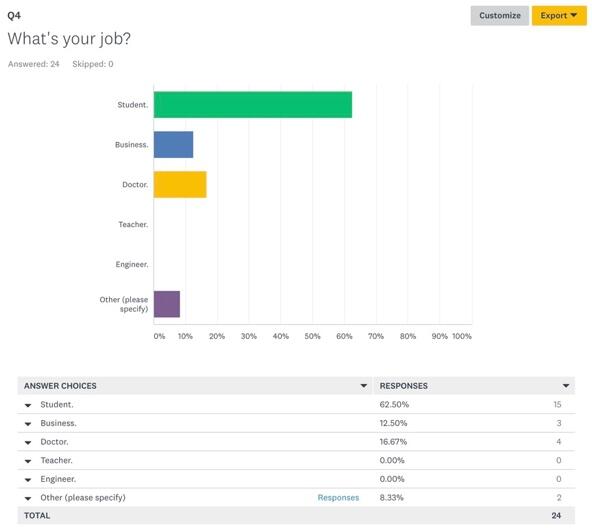
Thus, the first four questions that respondents were asked were directly associated with their demographic information. In terms of ethnicity (Figure 1), the largest majority of respondents was Asian (95.83%) while the rest identified as other (4.17%). 66.67% of respondents were male, 29.17% were female, and 4.17% were of other genders (Figure 2). In terms of age groups, the largest part of respondents was between ages 18 and 25 (70.83%) (Figure 3), which is important to answering the research question because this age group is considered the most proficient in the use of technologies (“Millennials: Technology equals social connection,” 2014). The last demographic aspect was related to respondents’ occupations and it was shown that 62.5% of them were students, which aligned with the findings on their age (Figure 4). The mentioned findings on respondents’ demographics show that there could be a high likelihood of participants having enough knowledge about threats to data privacy, especially in terms of technology use.
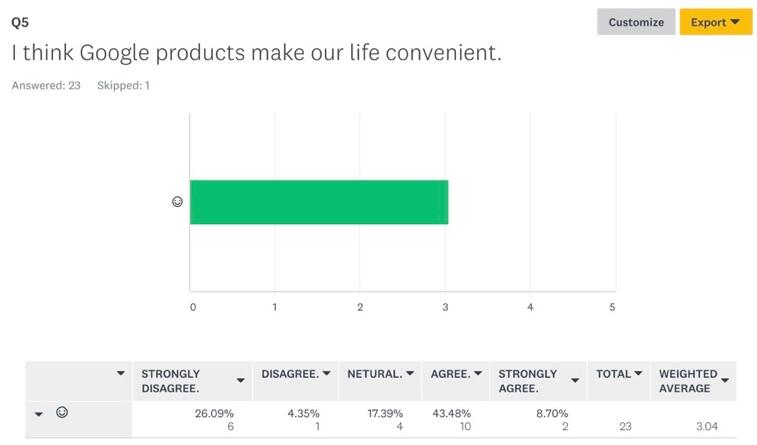
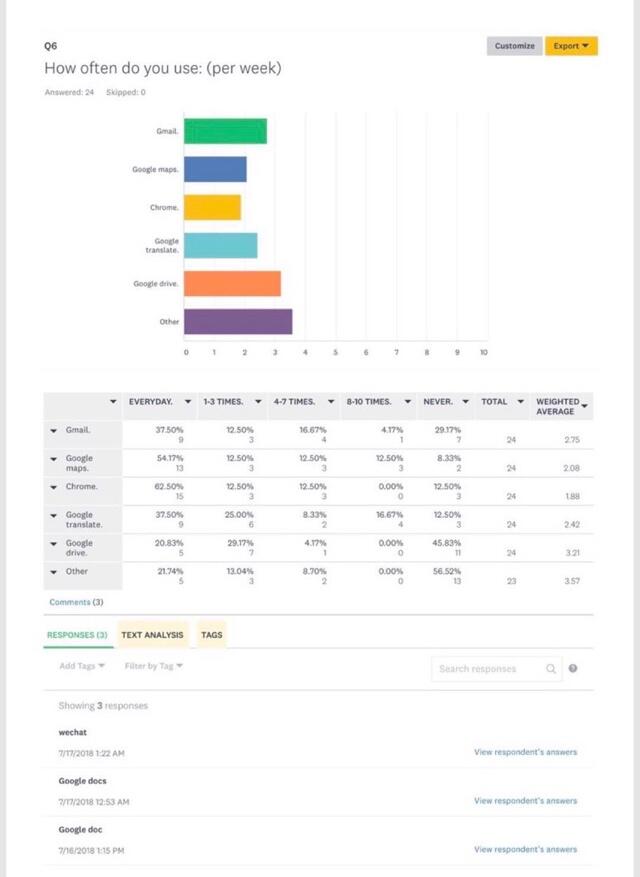
The next set of questions was targeted at getting to know the attitudes of respondents toward the use of the Internet and other technology-oriented tools used for collecting information. When asked whether respondents agreed with the statement that Google products made their lives convenient, the opinions were mixed. While 8.7% of respondents strongly agreed and 43.48% agreed with the above statement, it is important to account for the 26.09% of people who strongly disagreed and 4.35% who disagreed (Figure 5). These findings point to the fact that there is some doubt as to whether Google products enhance people’s lives. Next, the question of how often different applications and tools are used was asked. Tools classified as ‘Other’ were shown to be the most popular among the sample of participants, with Wechat and Google Docs leading in this category. By weighted average, Google drive was the second tool used frequently, followed by Gmail, Google Translate, Google Maps, and Chrome (Figure 6). Since all of the mentioned tools play significant roles in people’s professional and personal lives, the findings are important for enhancing researchers’ understanding about how often different applications are used in everyday activities.
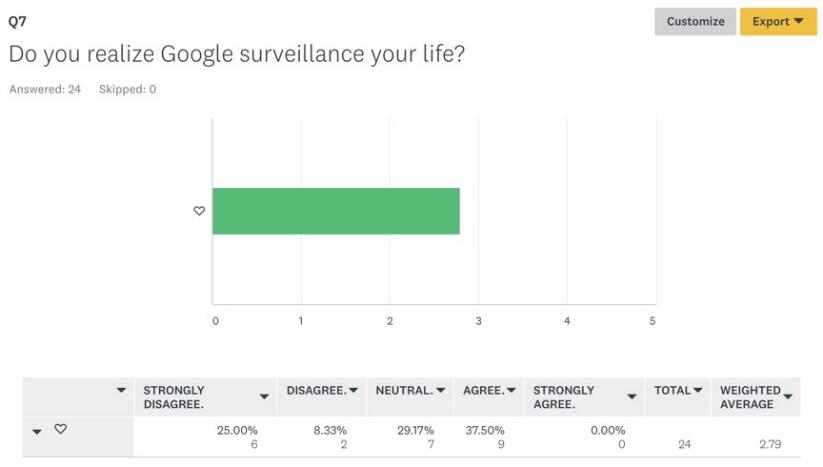
The next set of questions was concerned with getting the understanding of respondents’ opinions on whether Google products and technologies, in general, have a negative impact on preserving their privacy. As seen from the respondents’ answers presented above, most people use Internet-based technologies for various purposes, which means that some personal information could get exposed. 37.5% of respondents agreed with the statement that they realized Google surveillance of their lives, 29.17% had a neutral attitude toward the idea, while 25% strongly disagreed and 8.33% disagreed (Figure 7). These results show that despite being aware of the possible privacy and surveillance risks associated with the use of online technologies, people continue using it.
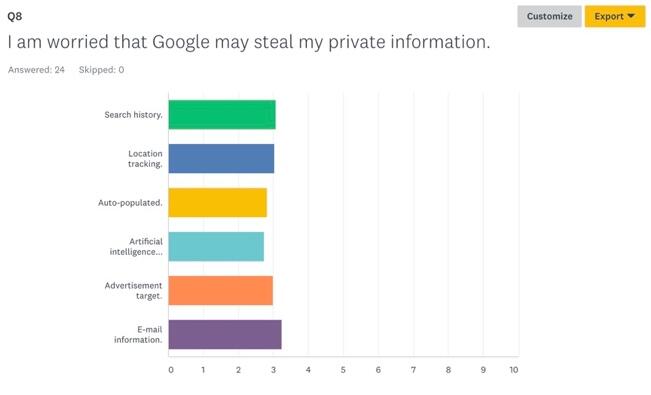
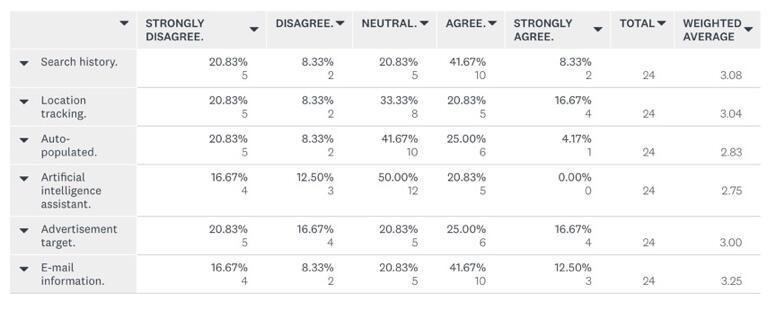
When asked about types of information that participants feel could be stolen, all presented categories received similar attention from the questionnaire’s respondents (Figure 8). E-mail information was considered the most valuable because hacking could lead to such outcomes as the theft of password information, credit card details, and personal correspondence, as reported by Larson (2017) for CNN. Search history was the second-ranked category of data that respondents feared to lose, followed by location information, advertisement targeting, auto-populated information, and artificial intelligence assistance. The fact that respondents showed a relatively equal attitude to all of the mentioned categories of information shows that the data users store online is valuable to them and that their loss could lead to serious consequences.
After getting to know more about how their information could be compromised through the use of online tools, the participants were asked whether they would change the patterns of Google tools use. 50% of questionnaire respondents indicated that they would continue using Google without making any changes or implementing security measures (Figure 9). 37.5% of respondents mentioned that they would reduce their use of Google products while 8.33% would increase it, which is an interesting result. Only 4.17% of surveyed participants concluded that they would resort to using other products.
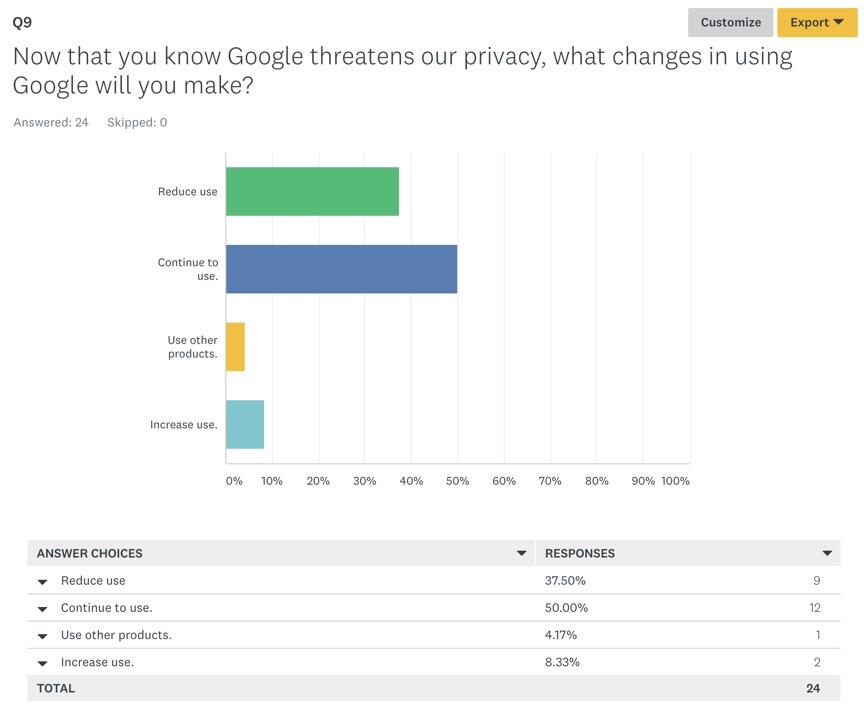
The last question in the survey is of special importance to the analysis of finding because it shows that despite high risks of personal information stored online, and in Google tools, in particular, being compromised, people will continue using them. This suggests that users are willing to take responsibility for applications the assistance of which they seek to enhance the sharing, processing, and storing of information. Unfortunately, when serious data breaches occur, most people blame companies rather than acknowledging the lack of their personal awareness (Shah, 2015). However, the responsibility of corporations should not be underestimated, especially in cases such as the recent Facebook scandal associated with the leaking of information to Cambridge Analytica (Wong, 2018). Given the current state of information security, committed efforts of users targeted at protecting their personal data are needed.
The findings of the questionnaire show that Google products are widely used for storing and sharing valuable information. However, there is a lack of awareness on the part of some users as to whether their personal data could be at high risks of being hacked and used for malicious purposes (de Bruijn & Janssen, 2017). Because most questionnaire respondents were willing to continue their use of Google products, convenience and effectiveness were more valuable to them than the preservation of information. Further efforts targeted at studying the use of Internet-based tools of data storage and processing can be associated with examining specific cases of information breaches rather than measuring the overall attitudes of the population. Nevertheless, the results shed light on the actual picture of online tools’ use, suggesting that they make everyday life convenient and more productive regardless of the risks that come with them.
References
de Bruijn, H., & Janssen, M. (2017). Building cybersecurity awareness: The need for evidence-based framing strategies. Government Information Quarterly, 34(1), 1-7.
Treiman, D. J., Lu, Y., & Qi, Y. (2012). New approaches to demographic data collection. Chinese Sociological Review, 44(3), 56.
Shah, S. (2015). Who’s to blame for a data breach? Computing.
Millennials: Technology equals social connection. (2017). Insights.
Larson, S. (2017). Every single Yahoo account was hacked – 3 billion in all. CNN.
Wong, J. C. (2018). Mark Zuckerberg apologizes for Facebook’s ‘mistakes’ over Cambridge Analytica. The Guardian.