Introduction
In the modern environment characterized by the frequent use of technologies and social media, in particular, the issue of privacy protection is imperative to discuss. Protecting social media privacy is necessary because the information stored on platforms can be further used for unethical or criminal purposes. Therefore, when agreeing to share one’s information online, users should pay special attention to the terms of service as well as be proactive in securing their information effectively. For instance, when Facebook users delete their images from the website, the latter can remain on the platform’s servers, causing a threat to the privacy of the user. The purpose of the current exploration is to provide an all-encompassing look at best practices that can safeguard users against the inappropriate use of their personal data.
Practices Against the Inappropriate Use ff Personal Data
First, it is imperative to examine how the use of online social networking (OSN) affects privacy settings and profile disclosure. According to Stern and Salb (2015), the most valuable commodity of ISN is the population of platforms’ users as well as the information that they share. The findings of the research revealed that OSN site use was significantly associated with both profile disclosure and the use of privacy settings. Tin addition, privacy settings greatly influenced profile disclosure. The results, therefore, imply that the use of privacy settings does not decrease the rate of exposure, which presents a challenge associated with the need to strengthen the capabilities to strengthen privacy. This shows that social media users must be educated on the methods they can use to protect personal information to increase safe disclosure. Besides, social media platforms should be held accountable in communicating transparently to their users in regards to the security setting features and access to enhanced protection.
The case of Facebook associated with Cambridge Analytica is highly important to discuss in the current exploration. The company has provided unauthorized access to personally identifiable “information of 87 million users of the platform […] this raised questions regarding not only the security of data but also about a more significant social impact of social media use” (Isaak & Hanna, 2018, p. 52). The ubiquity of data collection, storage, and analytics on social media platforms has the potential for disrupting the flow of ideas, access to information, as well as the advancement of innovation. The Facebook case is especially problematic because if the influence on the US election outcomes (Isaak & Hanna, 2018). By accessing user data, the analytics company was able to send targeted advertisements that were based on the profiles of their receivers (Isaak & Hanna, 2018). In order for users to safeguard themselves against such information breaches as the instance with Cambridge Analytica, several recommendations can be made.
Public transparency is an essential mechanism for ensuring data protection. This means that before signing up with a social media platform, users should read be aware of the types of data being collected by the website as well as how it is used later. Every platform should have a transparent policy that would disclose for users whether any third party could have access to their information (Isaak & Hanna, 2018). In terms of the actions that are in the direct control of users, ‘do not track’ requests should be used alongside with the blocking disclosures of third-party cookies. In addition, it is recommended to set notifications, where possible, that would inform them that their information is being used for various reasons. Being equipped with information is the desired solution for users to safeguard their data as the lack of knowledge leads to information breaches among website users.
Following the discussion on the need to be aware of the ways in which social media platforms, the study by Tayouri (2015) should be mentioned. According to Tayouri (2015), the human factor in social media security plays a defining role. However, providing the public with information on how they can use social media websites safely is not enough, with complementary layers needed. It was proposed to offer education, starting from elementary school through interactive and adaptive training on innovative technology means. This is necessary for strengthening the human factor, which becomes more considerate of the effects that technologies and social media have on their life integration into society. For children, interactive video games can be used as a method for engaging them in learning. In addition, tools for social media site monitoring can be used in order to identify the attempts of malicious intents of information breaches. To determine how social media affect the use of data, technologies should be used due to their broad applicability and reliability. Combining education and training with advanced technologies is thus the method recommended for strengthening the powers of the human factor.
Apart from educating users on the most effective methods of safeguarding their private information online, it is also recommended to hold the executives of social networks accountable for breaches in data privacy protection. Helman (2019) proposed a unique solution to ensure the privacy of social media users. The model is associated with the augmentation of the classical incentive contract, which provides a fixed wage and payment tied to the price of a company’s stock. The proposal lies in the reconsideration of the model by connecting the compensation of executives to the privacy practices that the organizations deploy. Therefore, setting high standards of privacy will incentivize company executives because their payment will depend on users’ protection.
The approach put forward by Helman (2019) is unique in the sense that it intends to influence the executives within firms to reflect the benefits and harms of their conduct. This solution is also dynamic, which means that it can be applied in different contexts. The level of privacy protection on social networks is thus expected to change in accordance with the shifting standards of privacy in society. Such a method is more flexible and multi-dimensional as compared to static policies within which privacy standards are rigid and remain unchanged for prolonged periods of time.
Increasing copyright protection for users of social media platforms is another solution to the issue of limited data security. The solution is necessary to mention because of the lack of certainty associated with the terms and conditions to which users agree when signing up for such platforms as Facebook, Instagram, Snapchat, and others. Despite the fact that the agreement grants users the ownership of their content, a non-exclusive license is given to social media platforms. Therefore, it is necessary to reconsider the way in which the ownership is approached within the agreements that users sign. There are numerous instances of content infringement under the Copyright Act of 1976 (Wichtowski, 2017). Moreover, the fact that the Act is quite dated implies that issues associated with the use of social media and content ownership are not clearly defined. In order to address this problem, Wichtowski (2017) proposed to amend the 17 U.S.C. § 501 of the Copyright Act in order to ensure that cases of social media users’ content infringement can be disputed. With the help of the amendment, a new protection measure for social media users will be created, thus helping them retain ownership of content that they create.
Online behaviors of users, apart from their knowledge, greatly contribute to the concerns of information privacy in social networks. Despite the debates of information technology experts in the recent years, very limited attention has been paid to privacy considerations from the perspective of users of social networks (see Figure 1). An interesting perspective on the problem was provided by Adhikari and Kumar Panda (2018) who suggested applying the Social Cognitive Theory and Protection Motivation Theory in order to understand the limitations concerned with privacy across social media use. According to the findings of the scholars that used structural equation modeling to reveal the privacy concerns and motivations, “perceived vulnerability, perceived severity, and self-efficacy significantly influence” users’ information privacy concerns (Adhikary & Kumar Panda, 2018, p. 96). The graph below shoes the structural model results as related to the information privacy concerns and privacy protection behavior:
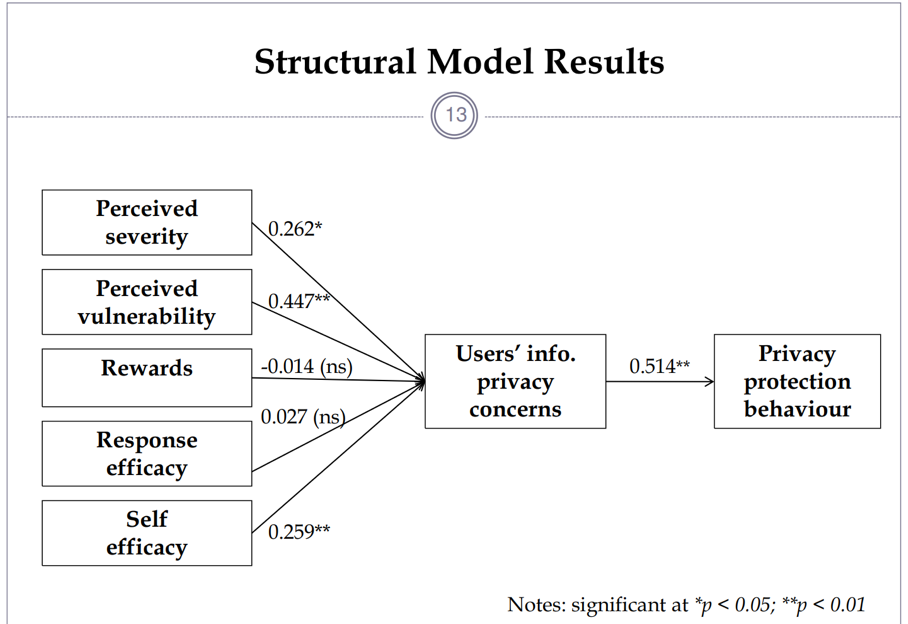
The perspective provided by the authors studying privacy offers new insight into the conceptual development of social networking use. There is a need to redesign the privacy protection strategies in order to safeguard users against privacy breaches. As Facebook has been subject to a recent scandal associated with the violation of users’ privacy, the Cambridge Analytica case, explaining how data can be secured on the website, is essential. According to Wardhono, Priandani, Ananta, Brata, and Tolle (2018), the increased instructiveness of social media environments is a call for concerns of privacy. The authors also pointed to the problematic nature of Facebook’s use of customer data, calling for the need for greater proactivity and effectiveness in data protection.
Cryptography was proposed as a method that can be used for encrypting chats between users on the basis of Advanced Encryption Standards (AES) and multi-layered MD5, which can facilitate privacy protection against social media companies that can use the information of their users as a commodity. MD5 is an algorithm that preserves the integrity of digital information through being safely compressed before encryption. The results of the encryption test that the researchers conducted showed that encryption was possible to conduct in a quick manner, with users not having to spend a lot of time on securing their information. The use of AES 128, in combination with MD5, enables to make chats safer and protect users against privacy breaches.
What is interesting to mention in the discussion of data privacy is the protection of users’ information after death. According to Chu (2015), there is limited research concerned with the protection of data the used to belong to a diseased individual, despite the platforms such as Facebook having policies associated with the use. The author proposed using two fundamental theories as a means of protecting the information of a person after death. The first such theory is associated with contract law, while the second is concerned with property law. Under contract law, it is imperative to analyze the terms of service agreements that social media users accept. This is necessary for determining the scope of posthumous privacy rights. Property law, on the other hand, is essential for evaluating whether the digital assets of a deceased person can be considered ‘real’ property. Nevertheless, despite the measures used for determining the status of information property of dead people, there is a lack of understanding of whether the rights to privacy are being protected sufficiently.
Conclusion
The problem of managing and protecting the rights to privacy of deceased individuals is highly personal. The current approaches, the contract and property law, are insufficient for protecting the confidentiality of deceased individuals. Therefore, Chu (2015) proposed extending tort law to privacy considerations. Not only such an extension would protect online privacy rights but also facilitate the use of tort damages as methods for deterrence to further secure privacy rights. Nevertheless, there is a need to establish an effective means of enforcement to go hand-in-hand with the extension of tort law. In addition, the author proposed to use common law as another aspect of protecting the privacy rights of deceased persons because posthumous dignitary interests are already accounted for in common law. Overall, the discussion on data privacy as related to deceased persons is an issue of dignity, which is closely intertwined with digital assets that individuals have. While extending tort posthumously is necessary to protect the rights of individuals who are dead, it is also imperative to facilitate further discussion of the problem and ensure the better understanding of how posthumous information should be treated.
References
Adhikari, K., & Kumar Panda, R. (2018). Users’ information privacy concerns and privacy protection behaviors in social networks. Journal of Global Marketing, 31(2), 96-110.
Chu, N. (2015). Protecting privacy after death. Northwestern Journal of Technology and Intellectual Property, 13(2), 255-276.
Helman, L. (2019). Pay for (privacy) performance: Holding social network executives accountable for breaches in data privacy protection. Brooklyn Law Review, 84(2), 523-569.
Isaak, J., & Hanna, M. (2018). User data privacy: Facebook, Cambridge Analytica, and privacy protection.
Stern, T., & Salb, D. (2015). Examining online social network use and its effect on the use of privacy settings and profile disclosure. Bulletin of Science, Technology & Society, 5(1-2), 25-34.
Tayouri, D. (2015). The human factor in the social media security – combining education and technology to reduce social engineering risks and damages. Procedia Manufacturing, 3, 1096-1100.
Wardhono, W., Priandani, N., Ananta, M., Brata, K., & Tolle, H. (2018). End-to-end privacy protection for Facebook mobile chat based on AES with multi-layered MD5. International Journal of Interactive Mobile Technologies. Web.
Wichtowski, R. (2016). Increasing copyright protection for social media users by expanding social media platforms’ rights. Duke Law & Technology Review, 15(1), 253-268.