Sony Pictures Entertainment was established in 1987 and is located in Culver City, California. The corporation is a mass media and entertainment studio dealing with creating, developing, and delivering movies and television. However, in 2014, the international firm experienced a significant data breach from Guardians of Peace (GOP) that disclosed a large amount of sensitive data about their customers and workers. The movie The Interview, which centered on the murder of North Korean ruler Kim Jung Un, served as the impetus for the attack.
Sony’s Response to the Attack
I think Sony’s approach to the hacking was inappropriate, despite the likelihood that the attack was cultured. The company was unable to detect the attack when it first occurred. Before the invasion, company’s attackers had direct exposure to the corporate servers for a while. Furthermore, the company made a mistake by canceling the film “The Interview” and accepted the Guardians of Peace’s demand because they did not make any significant threat (Shaw, Tony & Tricia Jenkins 6). Sony’s leadership failed to acknowledge the security incident and produce countermeasures. On the other hand, the corporation getting in touch with the Federal Bureau of Investigation was a good idea to let their forensics specialists find the guilty party. The National Security Agency (NSA) identified North Korea as the attacker using the digital fingerprint the cyberpunks allegedly left in the software.
What Sony and the United States Administration can do differently
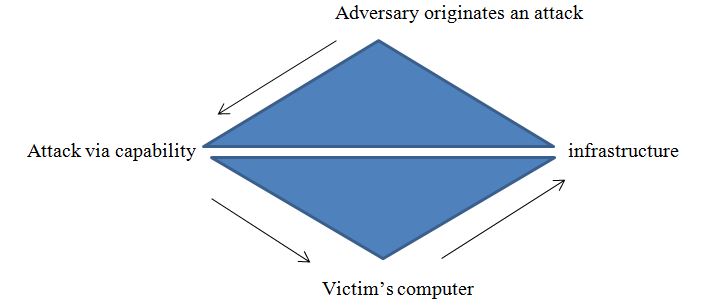
Sony and the United States government can take steps to reduce their exposure to cybercrime while also shielding them from any physical harm. There are several things companies and administrations can do to prevent hacking in the future. For instance, corporations can ensure that crisis intervention rules and practices are written. Staff training is also necessary so they are always informed about potential threats and countermeasures. Attending conferences such as Defcon (DC) can help corporations’ personnel stay updated on the latest developments in information technology security and malware patterns (Leal, Marcelo & Paul Musgrave 45). Additionally, national governments must update or develop the legal and administrative system governing digital information. The diamond model of instruction scrutiny shows how an opponent utilizes skills over infrastructure to unveil a cyber-attack on people.
Measures to Prevent Real-world Terrorist Violence and Cyberattacks
Organizations and the American government should stay steadfast in providing signals and caution against any attack that is taking place. The United States administration and companies can adopt passive protection as a target-hardening mechanism. Passive defense entails utilizing various technologies, items, and processes such as firewalls, cryptography, and access control. The authority can command the attackers to face severe risk or punishment. To fight against assaults, organizations, and the government should create security plans and guidelines (Shaw, Tony & Tricia Jenkins 26). Corporations must frequently reconfigure their networks, employ proper monitoring strategies and antivirus software, and deploy firewalls and antimalware to safeguard themselves from cyber-attacks and other assaults.
Conclusion
Everyone is susceptible to cyber-attacks; thus, authorities and the business sector should collaborate to create universal awareness programs. Furthermore, attackers have the potential to harm infrastructure, including data systems. Leaders can organize summits to address businesses’ growing susceptibility to online threats, including those sponsored by international bodies. Businesses must adopt information technology security rules, including imposing stringent passcode and verification policies, such as two-factor identification, and restricting access to critical data to safeguard data.
Works Cited
Leal, Marcelo M., and Paul Musgrave. “Hitting back or holding back in cyberspace: Experimental evidence regarding Americans’ responses to cyberattacks.” Conflict Management and Peace Science 40.1 (2023): 42-64.
Shaw, Tony, and Tricia Jenkins. “An Act of War? The Interview Affair, the Sony Hack, and the Hollywood–Washington Power Nexus Today.” Journal of American Studies 53.1 (2019): 1-27.