Cryptographic Basis of Encryption
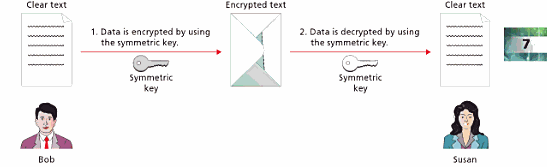
Encryption is the process of converting data into a coded format for security and confidentiality purposes. This process is achieved by passing data through a predetermined set of mathematical formulae known as encryption algorithms. The most commonly used techniques of data encryption include symmetric and asymmetric encryption algorithms. Symmetric encryption algorithm uses a unique key to convert data into a coded format. The same key is then used to decode the encrypted data by the recipient as illustrated below.
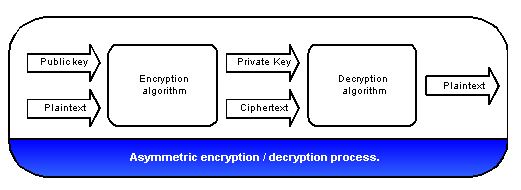
Asymmetric encryption algorithms, also referred to as public-key encryption algorithms, are based on the application of two different keys; the public key and the private key (Calabrese 2004). The sender uses a public key to encrypt data while the recipient utilizes a private key to convert it into plain text.
Symmetric and Asymmetric Encryption Algorithms
The similarity between symmetric and asymmetric encryption algorithms emanates from the fact that both of them utilize keys derived from digital certificates to encrypt and decrypt data. Both algorithms employ the concept of identity binding. This means that they embed a special character to the encrypted data, which is also used to authenticate the data at the recipient’s end (Kornievskaia 2002).
One of the major differences between these two encryption algorithms are in their computational complexity. In symmetric algorithms, the keys used to encrypt and decrypt data are similar, thus making its computational complexity relatively easy. On the other hand, asymmetric algorithms employ two different keys; a public key for encryption and a private key for decryption. This alteration of keys increases the algorithm’s computational complexity. In practice, symmetric algorithms are faster in decrypting large blocks of data as compared to asymmetric algorithms.
Applications of Symmetric and Asymmetric Encryption Algorithms
Symmetric encryption algorithms function in two ways. For example, block ciphers and stream ciphers. This implies that symmetric algorithms simply accept a string of characters called plaintext and convert it into cipher text, either in blocks or streams (Martin 2012). This process is quite simple and does not require expensive hardware or software.
Symmetric encryption is utilized in networks where security and authenticity of data under transmission or storage are not a priority, such as in a local area network spanning over a residential area. As opposed to this, asymmetric encryption algorithms can be used in military servers and networks since the level of security, authenticity and integrity of transmitted data are of high priority.
Possible Encryption Hacks
The major purpose of data encryption is to ensure security and authenticity of data and information under transmission or storage. However, despite the level of encryption complexity provided by symmetric and asymmetric encryption algorithms, chances of security breaches are still inevitable. Hacking of symmetric encryption algorithms can be propagated in a number of ways namely brute force attacks, related key attacks, and differential cryptanalysis.
Brute force cryptanalysis or exhaustive key search technique is one of the most common ways used by hackers in an attempt to break encrypted data. This attack is easier in symmetric encryption since the keys used are similar. In addition, symmetric encryption also involves key distribution whereby the key used to decrypt data is sent to every person performing the decryption (Oriyano & Gregg 2011).
This process undermines the privacy of the decryption key, and thus allows the hacker to employ purposive guesswork based on a particular party’s flaws to gain access to the encrypted data. Asymmetric encryption algorithms are much harder to hack since they use two different keys. However, hackers have been known to use advanced techniques, such as black bag cryptanalysis and man-in-the-middle attacks which allow cracking such codes.
Conclusion
Symmetric and asymmetric encryption algorithms are some of the most commonly used forms of data encryption. In symmetric encryption algorithms, a single key is used to encrypt and decrypt data while in asymmetric encryption algorithms, two different keys are used. Both of these methods can be cracked by using a variety of techniques such as brute force attacks for symmetric encryption algorithms and black bag cryptanalysis for asymmetric encryption algorithms.
Reference
Encryption Algorithms. (n.d.) Web.
Calabrese, T. (2004). Information Security Intelligence: Cryptographic Principles & Applications. Stamford: Delmar Cengage Learning.
Kornievskaia, O. (2002). Symmetric and Asymmetric Authentication: A Study of Symmetric and Complementary Properties and their Effect on Interoperability and Scalability in Distributed Systems. Web.
Martin, K., M. (2012). Everyday Cryptography: Fundamental Principles and Applications. Oxford: Oxford University Press.
Oriyano, P., S., & Gregg, M. (2011). Hacker Techniques, Tools, and Incident Handling. Sudbury: Jones & Bartlet.
Wright, B. & Plesniarski, L. (2011). MCTS Guide to Microsoft® Windows 7. Boston: Cengage Learning.