Executive Summary
Internet technology is by far the most important innovation in the world of communication. The evolution of communication from mere transfer of data to transfer of data, videos and pictures is the latest technology being used by many companies that desire to capitalize on the advantages of internet communication.
Teevo Corporation has developed an interactive TV broadcasting system that uses blue-ray technology, a system that interacts with its end users. This company’s expansion is an indication of the business’s success. However, the company’s expansion comes with many challenges such as the need for interconnection of the branches and equipping of staff in these branches with the necessary skills to use the technology.
However, an analysis of the company’s first branch in Sydney gives a framework of the internet connection that was being used, thus providing a head start in the provision of requirements for the office in Brisbane. The next step is to determine how the two branches are to be interconnected. This will be in line with the requirements of Teevo Corporation and the financial investment the company is willing to provide for the communication infrastructure.
The proposal, therefore, serves to merge the corporations’ requirements and the cost of the same. It is also a tool that will determine the structure of Teevo’s network communication. This is in addition to being a roadmap for improving the services and performance of the network infrastructure in this company.
It is therefore paramount to present the corporation with this proposal which will be a framework to meet the requirements of the Brisbane office’s staff communication needs alongside those of the corporation’s information sector. It is also an analysis of the steps which will be taken by the corporation to acquire the network set-up desired. The proposal will focus on the procedures that will help Teevo Corporation acquire the best network communication that will help it benefit more from the expansion.
Introduction
From the skills acquired in networking fundamentals, it is apparent that this project will require a wireless internet connection between the Sydney and Brisbane offices. This will be complemented by the remote connection to the Internet Service Provider. The company will have a network used mostly in the transfer of video, still graphics and numerous data-oriented information. The Brisbane office and the Sydney one will be connected by a WAN (Snmptools, 2007). This WAN will be protected by a firewall to ensure information security. The WAN will enable communication between Brisbane and Sydney offices. From the Brisbane office, the LAN will be connected to the LAN in Sydney. This is the basic structure or architecture that will be expedited. The internet connection will be two LANs connected by a WAN. Since security is a major concern, the proper structure will be put in place to ensure the presence of a secure internet connection both within and across the different offices. The external structure can also be a VPN. Virtual Private Networks will be used to connect different sites to a large VPN (Snmptools, 2007).
Purpose
The purpose of this proposal is to document the expansion of the internet connection between the Sydney and Brisbane offices. The aim is to enable smooth communication and transmission of programs.
Objective
The corporation presented the problems it faced with the whole idea of connecting the internet. It specified several requirements that were supposed to deliver an internet connection. The objectives of the project areas are outlined below:
- To meet the requirements of Teevo Corporation and to come up with a network design that fits the nature of operation in Teevo Company.
- To ensure that the network design is secure and functioning properly. It should be feasible and also efficient in serving the staff of Teevo Corporation.
Scope of the Project
The project has a wide range of tasks. They include the assessment of hardware and software requirements. The whole project will involve the following tasks:
- It will assess the cost of the whole project by coming up with a feasible plan to achieve its objectives.
- The processing of hardware requirements is subject to staff and company requirements. The processing ranges from specifications of switches for DSL or Cable, router and switch speeds determination and many more factors that affect the functionality of a network. Discussions on whether the client requires a wireless connection or a cabled one are also within the range of the project.
- The project will extend to the connection of the office LAN, hooking it up with the larger LAN. The completion of the project will be determined by setting up the network structure and ensuring that it is functioning properly (State Office of Education, n.d).
- Documentation and probably training of staff on how to apply the network and troubleshoot in case a breakdown occurs will also be parts of this project.
The Structure and its Function
The LAN Design
The local area network will be connected using a LAN switch. This is in the second layer (the data link layer). It increases performance and provides more bandwidth to meet the data requirements for Teevo Corporation. This will be the typical setup for the Brisbane and Sydney offices. It is called because a wireless LAN is not efficient and the data and network requirements of the client call for a stable and high-speed connection. The plan will be determined by the number of employees or users in the office (State Office of Education, n.d).
Internal Structure of LAN
Following the particular requirements specified by the client, the internal structure which is the Brisbane office will be a simple LAN but which has many features. To begin with, the LAN which will be set up in the Brisbane office will be from the DNS server that will assign both offices in Sydney and Brisbane the same IP address. Thereafter, the DMZ will be used in an area with limited access through data packets. Its server will also be set up in the same office. A firewall will protect the network from unverified intrusion (Kang and Balitanas, 2009). These public IP addresses will be similar in Sydney and Brisbane. The LAN will be further developed into VLAN and this will help in reducing the online traffic. A VLAN is a domain created by switches. The VLAN is vital in creating this broadcast domain (Snmptools, 2007).
The External Structure (WAN)
The external structure will be based on the idea of a WAN. The connection will be linking to an internet site in the Sydney and Brisbane offices. The two are independent LANs that have an interconnection to a WAN. The form of WAN that is more cost-effective in this case is the VPN (Ashraf, 2009). A Virtual Private Network is designed to accommodate the requirements of the corporation. The VPNs override the already existing and accessible infrastructure. It takes advantage of the existing network, such as the internet, and creates a system on it. Due to the security concerns of the corporation, it will also be advantageous since VPNs are encrypted, thus requiring critical user authentication in order to gain access (Mason, 2002).
The main difference between WAN and VPN is the ability of the latter to override on public networks (Mason, 2002). The WAN, on the other hand, runs on private leased lines (Mason, 2002). This gives a VPN advantage over the WAN since it can support the services of WAN and has a more stringent authentication process.
The wide coverage of VPNs is also a good investment putting into consideration future interests of expansion. The VPNs favor this idea since they are suitable for telecommuting. The VPNs are virtually everywhere since leased lines may not extend to private residences and travel destinations (Mason, 2002).
Sub-Netting Scheme
The networks of Sydney and Brisbane are on the same highway, and hence they do not need gateway devices to communicate. The hosts in the same VLAN use one IP subnet. In this case, all hosts will have IP addresses in one subnet which will be derived from the default private network address. The range of host addresses that will be allocated is 192.168.10.1 – 192.168.10.254. Thus, the company staff can adequately fit within the address range (Snmptools, 2007).
Configuration of the network (configuring DHCP Server)
The first step is opening the DHCP console by selecting the DCHP command in the server’s administrative tools. In configuring the DHCP we begin by giving the scope of the IP addresses that can be leased to the clients. In this case, they range from 192.168.10.1 – 192.168.10.254. The server is set in a way to give in-command prompts for entering the scope. Then the subnet mask is entered. Thereafter the exclusions of the IP addresses that are already leased you activate the length of time the lease should be given for each of the workstations to use the IP addresses (Posey, 2009).
This will also enable the DHCP server to allocate IP addresses only to staff desktops only. The next step is entering the addresses for the Local DNS (10.0.0.4/24), File Server (10.0.0.5/24), and Windows Server 2003 (10.0.0.6/24). The DHCP is then activated by clicking this on the authorization command. In this way, the server is going to allocate IP Addressed to the Desktops clients only and it can enable remote and external communication. (Posey, 2009)
Security of Network
LANs, WANs and VPNs
The emphasis on security by the corporation forces one to consider the issue seriously. This will help the client understand the way their network will operate and its stability. The single-site which is the offices in Sydney and Brisbane has a LAN. The security configurations for LANS are well protected from intrusion (Snmptools, 2007). The first option is the installation of web monitoring software. An example of such is Website Echo Server settings. It is a security tool that is installed, and for anyone to access the server, they are required to enter the IP address of the same and a service port number. The software goes ahead to monitor operations in the private network and can identify the IP addresses of machines that go beyond the perimeter of the private network. This type of security measure ensures strict administration of the systems and less intrusion (eEye Digital Security, 2010).
The software is compatible with Firewalls or a NAT device through particular ports (Mason, 2002). It involves an initial connection with the software’s server on a control port (Mason, 2002). This is also referred to as server port number (Mason, 2002). The VPNs are also well guarded. They have been divided into different levels of units that enhance their security features.
This is done through the use of various connections. The features used securely connect mobile users and branch offices (Mason, 2002). Intranet VPNs are very vigilant. They permit access to the network only to approved individuals (Mason, 2002). Extranet VPNs have a secure connection point for various users. These include external clients, business suppliers, and other pertinent stakeholders (Mason, 2002). This connection is over a shared infrastructure that utilizes dedicated connections.
The above security measures are an assurance that the internet security is up to date and the monitors and checks in the system regulate the security levels. The fact that a user goes through the authentication procedure and VPNs carry out the encryption of data before it is packaged as an IP packet and tunneled by the various tunneling protocols means that security is assured (Pillou, 2008).
Traffic Information Protection
Another aspect of security is traffic information protection. The protection of important information in the network is also vital to an organization. The VPNs work with robust security programs that make sure that when important information such as employee data is in the data traffic, the system is alerted, and responds by increasing the security of that information. There is different software, such as Iris Network Traffic Analyzer, which can be used. With this software in place, the network system of the organization is completely secure (eEye Digital Security, 2010).
Once the network is set, a choice of a security system that restricts access to the server and also monitors the activities of the server is facilitated. It can prevent imminent attacks on the network system before they happen and it can also secure information within the network. The protection of information in traffic is also important and putting in place software that monitors traffic flow and information will also be an option in order to take security to the levels required by the organization (Mason, 2002).
Firewall Protection
This is a form of protection availed to the network from non-vetted access via external sources. They have a single or a few peripheral networks. The latter are called demilitarized zones (DMZ) (Mason, 2002). A DMZ is a perimeter network that is weak in resisting attempted access into the internal network. All connections have to go through the firewall (Kioskea, 2008).
My option is to Use one DMZ server for the group and place it in the Sydney or Brisbane office. It makes it easier to administer the network. In this case, it will be in the main office in Sydney.
Access Control Lists
These are used to determine those individuals who can gain entrance into the system. This is done by sifting the routed packets either by forwarding them or blocking them at the router’s interfaces (Pillou, 2008). The router treats each packet on an individual basis. It decides whether to forward or drop the same (Pillou, 2008). This is based on the criteria a systems administrator specifies within the access lists.
The reasons why system administrators configure access lists include the following:
- To enhance security for the organization’s network.
- To manage traffic flow on the network and control what enters the network and what goes out.
- To filter packets flow in or out of router interfaces and limit network utilization by some specified sources.
Access lists are mostly applied in firewall routers (Mason, 2002). The latter is connected to the organization’s internal network and an external network (Msumeno, n.d).
Access List Configuration: An Example
An example showing a configuration of a DMZ with two interfaces, fast inbound and outbound can be configured as follows:
SYD-RTR#config t
SYD-RTR (config) #access-list 201 deny tcp any any eq 445
The first instruction tells the router to block TCP packets on port 445 from any source to any destination
SYD-RTR(config )#access-list 201 permit ip 192.168.10.128 0.0.0.7
any any
This instructs the router to permit any IP in this network 192.168.10.128
With mask 255.255.255.248(wildcard 0.0.0.7) to any network
When the lists to be configured are many, one can create an access list in another file and add them to the router.
It is to allow all internal traffic to the DMZ network and DMZ servers.
It only permits staff desktop computers to DMZ servers but restricts them to access the executive management database. The executive management staffs are the only ones who can access the database. All internal traffic to the external traffic is allowed. All external traffic to the internal network is permitted if only it is return traffic of sessions initiated by any of the internal staff desktops or any of DMZ servers. The HTTP Web server is accessible by the internal staff desktops and also by any client connections from the external network.
- access-list 201 permit tcp any any eq 1345
- access-list 201 permit IP 192.168.10.0/24 eq 1345
- access-list 201 deny IP 192.168.10.0/20 10.0.0.11/24
- access-list 201 permit IP 192.168.10.0/4 10.10.0.11/24
- access-list 202 permit tcp any host 10.0.0.10/24
- access-list 201 permit tcp 10.0.0.10/24 any any established
- access-list201 permit IP 192. 168.10.0/24 10.0.0.10/24
- access-list202 permit tcp 131.181.6.9/30 10.0.0.10/24
This is later added to the DMZ interface by going to the router configuration mode and applying all access lists at once. The operator then applies the access control list 201 as inbound access list on the DMZ interface and access control list 202 as outbound on the DMZ interface
SYD-RTR(config)#interface inbound 0/0
SYD-RTR(config-if)#ip access-group 201 in
The instruction tells the router to Exit from in LAN interface and go to the WAN interface
SYD-RTR(config)#interface outbound 0/1
SYD-RTR(config-if)#ip access-group 202 out
This instructs the router to Exit the interface and saves the configuration (Msumeno, n.d). This access-list configuration allows the communication needs in both Sydney and Brisbane.
Stateful Packet Filtering
This is a security check system that works with a firewall. When a TCP SYN packet requests a connection, the firewall crosschecks its rules to establish if the request can be allowed. The crosscheck is usually from top to bottom. For a request to be accepted, the rules must match the request, failure to which the connection is blocked. The process of verification continues when the firewall creates a translation slot in the table hence creating a session flow (Kang & Balitanas, 2009). Once the session flow notices a packet that is not a TCP SYN packet, there is more cross-checking, and if there is a connection that was earlier on established, the packet is allowed. If otherwise, an RST (reset) packet is sent to the origin.
This is after the connection is denied. The stateful packet filtering helps in reducing the time of connection. This is because since a table exists, there is less reading and fast transfer of packets. Another means of crosschecking the packets is called Stateless filtering. This is the opposite of the stateful and involves reading the source of the packet and the destination IP addresses of a TCP packet, then cross-matching the rules list to authenticate a connection. This is repeated for every packet in a session that requests entry into the network (Kang & Balitanas, 2009).
Network Address Translation (NAT, PAT, and Static)
This is how a range of global IP addresses are encompassed to the perimeter of a DMZ. There are four states of NAT. The first is Static NAT, which occurs when the IP addresses encompassed are unregistered and are mapped to a registered one.
A large number of unregistered IP addresses that are hooked into one that is registered leads to what Mason (2002) refers to as overloading. In a scenario where IP addresses on the network are registered and are applied by other networks, this is referred to as overlapping (Mason, 2002). Network address translation can only process incoming requests from the external network. This in extension means that the internal network machines can not operate as servers in relation to the external network (Kang & Balitanas, 2009).
The term “demilitarised zone” or DMZ means an isolated area that serves the purpose of hosting applications that are made available to the public. The DMZ acts as a cushion to the network which requires protection from any hostile network (Charania, Johnston & MacCallum, n.d). This is important because the machines need to have an interface that separates a network accessible from both the internal and external ports so as to minimize the risk of compromising company safety (Kioskea, 2008).
DMZ Architecture
“Bastion hosts” is the name given to the servers in the DMZ. This is because they act as outposts in the company’s network. The flow of packets is governed by a security policy. In the case of the DMZ security policy, it is stated that:
- Packet data coming from the external network to the DMZ is permitted
- Packet data from the external network flowing to the internal network is not allowed
- Packets of data from the internal network to the DMZ is permitted
- Packets of data from the internal network to the external network is permitted
- Packets of data from the DMZ to the internal network is permitted
- Packets of data coming from the DMZ to the external network is not permitted (Kioskea, 2008)
The DMZ forms a middle security level that is not strong enough to store important information of the organization. The DMZs can be set up internally so as to differentiate the internal network with the different levels of protection to avoid internal intrusion (Pillou, 2008). The diagrams below will outline this vividly.
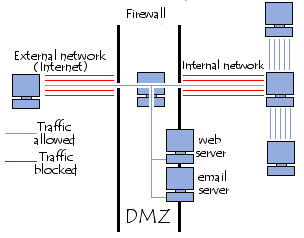
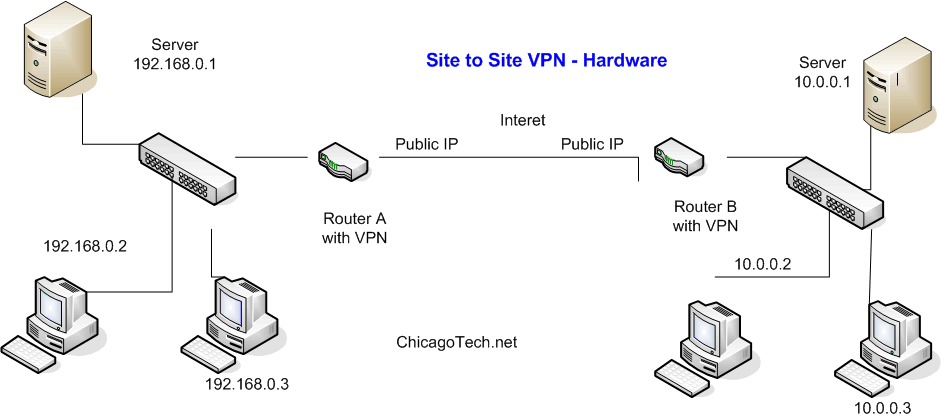
The server has to be located in both the offices; one in Sydney and one in Brisbane.
References
Ashraf, 2009. How to set up a WAN across the internet. Web.
Charania, S Johnston, N and MacCallum, T, n.d. ELEC 490/2/8/9. Web.
eEye Digital Security, 2010. Iris Network Traffic Analyzer. [Internet] IT Forensic Analysis. Web.
Kang, H & Balitanas, MO. (2009) Vulnerabilities of VPN using IPSec and Defensive Measures. International Journal of Advanced Science and Technology, 1(10), 1-10.
Kioskea, K, 2008. DMZ (Demilitarized Zone). Web.
Mason, A, 2002. VPNs and VPN Technologies. Web.
Msumeno, F, n.d. Access control lists. [Internet] London University. Web.
Pillou, J, 2008. NAT- Network address translation, port forwarding and port trigg. [Internet] McGRAW. Web.
Posey, B. M. 2009. Setting Up a DHCP Server for your Organization. [Internet] McGRAW. Web.
Snmptools, 2007. Network Basics: LAN, WAN, VPN. [Online] London University. Web.
State Office of Education, n.d. Sample network design proposal. [Online] State Office of Education. Web.
Textor, S. (2002) The installation and configuration of a Cisco PIX Firewall with 3 interfaces and a stateful failover. SANS Institute InfoSec Reading Room, 2(1), 2-31.