Introduction
Technological issues and the desire to ensure that processes being carried out by individuals and corporate are performed efficiently have resulted in the increase in the use of automated systems. This means that an increased number of individuals have opted to use these systems to perform their tasks. The need to have adequate security in these systems in order to ensure that personal information and data is kept safe within the system has also increased. This has brought up the need to ensure that any person accessing the system is identified before access to the system is granted.
The security techniques that have been developed over the years involve the use of a database where information about all the members allowed to access the system is stored (Bishop, 2010, p. 120). When a user wants to access the system, he/she provides some information to the system. This is compared to the information that is stored in the database. In case of a match, the user is granted access. When the information provided does not match any data contained in the database, access is denied. Over the years, passwords have been used as a security technique to access systems. This meant that the users have to remember these passwords. With the technological advancement, this technique has been made easier by the use of tokens.
The authentication process that is available can be divided into three main categories. The first of these categories is referred to as knowledge based method. In this category, only the person who is allowed to access the system knows the authentication. This is mainly through the use of personal identification numbers or an answer to a secret question. The method that involves the use of passwords falls in this category. The second category is referred to as possession based method. In this case, the person who is allowed to access the system possesses the authentication. The authentication may be in the form of a smart card, a token or even a key (Grembi, 2008, p. 154). All these are tangible accessories and have to be carried by the individual to enable him/her to access the system that requires them for authentication.
The third category is the physiology based method. This is also referred to as behavior based. In this case, only the person allowed to access the system is the authenticator. This category uses the traits of the person. Biometrics can be categorized here. From these three categories, it is clear that for the knowledge based and possession based categories, the person has either to remember the authenticator or carry it. This is problematic as the person may forget to carry the authenticator or fail to remember it in case it is a password. The drawbacks of these techniques resulted in the need to come up with a way to counter these shortcomings. Biometrics offered a good alternative since the person just needed to be there and does not require the need to carry any component or keep a memory of the personal identification number.
Biometrics is an automated system that uses the traits of individuals for their identification (Wayman, Jain, Maoltoni, & Maio, 2005, p. 25). This technique uses various aspects of the human body to identify the validity of the request to gain access to a system. The various techniques that may be used include fingerprint recognition, face recognition, the use of a person’s iris to identify him/her, vein pattern recognition, DNA recognition, voice recognition and the key stroke pattern recognition (Woodward, Orlans, & Higgins, 2003, p. 56). These are not the only biometric techniques used as the advancement in technology has resulted in the development of new biometric techniques. For the biometric system to work, information is first obtained from the individuals and stored in a database from where comparisons will be made when a user requests for access. Therefore, biometrics is based on the fact that there are distinct characteristics between all human beings. The fact that these characteristics are permanent also means that the technique can be used for a long time without the need for changes. Some of the used techniques in biometrics are illustrated below (Nalini & Bolle, 2004, p. 154).
The main objectives of this paper will be to examine how biometric authentication technology is beginning to transform the user authentication process. It also touches on the problems that will be encountered due to the implementation of this technology. Also of importance will the analysis of the advantages and the drawbacks of using this technology in the user authentication process. Finally, the current practice of the biometric authentication process in the UK will be examined.
Literature Review
Biometrics is a term that is obtained from two Greek words. These are ‘bio’ which means ‘life’ and ‘metrics’ which means ‘to measure’. The biometric system is composed of various components. The components include sensors, signal processing units and algorithms, data storage devices, matching algorithms and a decision process (Reid, 2003, p. 111). The sensor is a component that is used to obtain analog data from the users of the system. This data is continuous and varies with time. It then converts the data into a digital form. This ensures that the data is in a form that can be interpreted by the computer. The signal processing units and algorithms are used to carry out the processing of the digital signal that is obtained from the sensor (Nalwa, 1997). The signal is converted to the required format for storage at this stage.
Signal conditioning and enhancement is also performed at this stage. The data storage unit serves the purpose of storing the processed signal. The stored data will be used as a reference during the identification process. The other component of this system is the matching algorithms. This refer to the guidelines that are followed during the comparison between the data that is stored in memory and the new data that has been acquired from the user. Once the matching process has been completed, the decision process follows (Chirillo, 2003, p. 136). In this process the decision to allow or deny access is made. If the provided details match the data that is stored in memory, then access is granted, otherwise it is denied.
The advancement in technology has aided in ensuring that the ideas which were only put on paper many years ago are implemented. Biometrics is also one of the ideas. In situations where implementation was conducted, the implemented process was not automated. For example, the use of the identification cards where identification was through looking at the image on the identification card. Comparison between this image and the card holder was then done. This method was ineffective since a person may be subjected to changes in his/her physical appearance and therefore making it difficult to for identification to be performed. The discovery of computers and the processing capabilities that come with them meant that the automation of the biometric techniques could finally be achieved. The fingerprint method was the first biometric technique to be used (Miller, 1994). It was initially used to identify criminals. These included those in custody and those arrested after committing crimes. This enabled the law enforcing agencies to be able to keep the records of the crimes committed by a particular individual.
The next technique that followed after the fingerprint technique was the proposal by Frank Burch, an ophthalmologist, to use the iris pattern in the identification of individuals (Lakhmi, 1999, p. 235). This was in 1936. This idea did not come to fruition at that time due to the limitations in terms of technology at the time. In the 1960’s face recognition came into play. At this time, the technique was not fully automated and required the assistance of another person to look at the facial features of the person requesting access. The process used the position of various facial features and compared these positions to identify a person. Technological advancements finally ensured that these biometric processes are automated and more biometric identification techniques are identified. Some of the biometric techniques that are used are discussed below.
Face recognition
This technique was used over the years but it was not automated (Phillips, Rauss, & Der, 1997). The advancement in technology enabled its automation and at the moment it runs independently without the supervision by another individual. The main techniques that are used in this process include a feature based technique which is also referred to as the geometric technique. The other technique is the view base technique also referred to as the photometric technique. The technique that was initially used for facial recognition was a two dimensional method (Adini, Moses, & Ullman, 1997). However, this technique had limitations and efforts were made to ensure that a three dimensional recognition system was developed. This is because a 3D system is more accurate.
Principal components analysis (PCA) is the technique that is mostly used in face recognition systems (Nanavati, 2002, p. 15). It is where the image of the face is acquired. The analysis of different parts of the face is then done. During this analysis, emphasis is made on the distance between different parts in the face. The results of this analysis is then stored as a weighted sum in the systems memory. Every time a person request to access the system, his/her entire face is scanned (Chellappa, Phillips, & Rosenfeld, 2003). This is important since the system will do the analysis of the image that is obtained then compare it with the data that was stored in memory previously. Other techniques that are implemented in the facial recognition technique include the Elastic Bunch Graph Matching (EBGM) and the Linear Discriminant Analysis (LDA) (Nanavati, 2002, p. 22).
Hand geometry recognition
The hand geometry method is mainly used since it is easy to use. Its implementation process is not complicated compared to other biometric techniques. The acceptability of the technique also makes its implementation easy. The first implementation of this technique was done in the late 1980s and it has been used since then. The system involves taking various measurements of the geometry of the hand. These include its length, its width, its thickness and also calculation of the surface area of the hand. This information is stored in the system’s main database for comparison to be performed during the matching process. A silhouette image of the hand is obtained by the use of a special camera (Ashbourn, 2000, p. 156).
The image is then processed to obtain the details that are required for authentication. The camera has charge coupled devices that are inbuilt. These assist it in the capturing of the image. An angled mirror is also incorporated in the system to ensure that the sides of the hand are also captured. This is important as the mirror will ensure that the width of the hand is also captured. Once all the necessary data has been collected, comparison with the data stored in the database is conducted. This is during the decision process and appropriate action is taken. The memory requirement for this method is small as only 9 bytes are stored in the memory for the purposes of comparisons.
Iris recognition
The pattern of the iris for every individual is unique. This feature led to the inclusion of the iris as one of the biometric techniques for the purposes of authentication. The iris controls the amount of light entering the pupil through the contraction or the expansion of its muscles (Dougman, 2004). The muscles of the iris are the ones that form the unique pattern that is used for the identification process. A digital camera is used to obtain the image of the iris to mark the start of the authentication process. The quality of the image captured by this camera needs to be very high. Care should also be taken to ensure that the eye lashes and the surrounding of the eye is not captured as this may act as noise and affect the recognition process. To achieve a high quality image during the capturing process, some cameras employ additional illumination.
The camera’s megapixels are high enough and the only factor that may prevent them from obtaining the required image quality is the lack of enough illumination. The most common form is the illumination by the use of infrared light. This form of light does not harm the person but only serves to provide illumination so that the image quality can be increased. Once the image is taken, it is filtered using Gabor filters (Deravi, 2008). These are high pass filters that are tuned to a specific frequency. The image is then developed and stored in form of vectors. The obtained vectors do not change and are not affected by physical parameters such as illumination (Huang, Luo, & Chen, 2002). These vectors are stored and when matching needs to be done during the recognition process, comparison is made between the calculated vectors and those that are stored in memory.
Voice recognition
In this technique, the voice is used to recognize the user. This is achieved by focus being made on the features of the voice that are affected by both the behavior of a person and the vocal tract of the individual (Campbell, 1997). This technique relies on other factors other than the way words are pronounced. A combination of the jaw movement, how the tongue is moved and the path through which air flows from the soft tissues in the vocal determine the voice that will be produced. These features result in the variations of the voice that is produced. The main technique that is used in the speech recognition process is where there is a preset phrase that is stored in memory (Ryan, 2009). The user requesting to be granted access is then required to pronounce this phrase. Once the pronounced phrase is captured, analysis is done to convert it to the required format. Comparison is then made between the obtained value and those that are saved in memory.
This is during the matching process. Another technique that is used in voice recognition does not use a pre-stored phrase. The user requesting access is prompted to say a word and the system performs the verification process. However, this requires the use of more complicated systems to ensure its efficiency and effectiveness. The characteristics of the voice that are compared may include the quality of the speech, the duration of the voice, the intensity of the voice and also its pitch (Jain, Ross, & Prabhakar, 2004). This system incorporates a microphone which captures the voice input inform of an analog signal and converts it to a digital form. This is the form that the computer can be able to understand and therefore analyze the data.
Key stroke pattern recognition
This involves the monitoring of how an individual inputs data to the system through the use of a keyboard (Monrose & Rubin, 2009). It is achieved by trying to recognize the habit of a person while inputting data through the keyboard. The aspects of the input that are measured include the speed with which the person types. This may be measured by the number of words the person inputs per minute. The precision of his/her typing and also the typing rhythm of the person may also be used for analysis. Therefore, this technique becomes effective when the data to be input is considerably long. This ensures that the characteristics mentioned above are able to be monitored. Short inputs may result in premature analysis resulting in the decision process being erroneous. The requirement of this system is a keyboard and monitoring software that is programmed to analyze the keystrokes from an individual (Bartmann, 2006).
Fingerprint recognition
This is a biometric technique that has been used for the longest time compared to the other techniques (Ratha, Cornell, & Bolle, 2006). Its automation was the first to be done as a considerable amount of research has been done on it. Various forms of research have been conducted to determine the uniqueness of the fingerprint and this resulted in the development of the fingerprint minutiae as a method of authentication. The fingerprint is composed of patterns of ridges which form on the surface of the finger. Research that was carried out indicated that these patterns are unique for every individual (Parziale, 2008). The identification process involves the use of discontinuities in the patterns of these ridges. The division of the ridges is also used to aid in the identification process. The discontinuities of the ridges are referred to as minutiae. The minutiae are extracted from the finger during the authentication process to be able to identify their orientation, their types and also their location. These are the features that make the fingerprint unique for every particular individual. The combination of all these features cannot be the same for two individuals as research has shown.
Initial research about the fingerprint recognition technique was conducted by Galton who identified the features that can be used to aid in the identification process (Galton, 1892). However, at the time the technology that was present meant that his ideas could not be implemented fully. With the advancement in technology, this has been made possible. The technological changes have also contributed to the identification of additional features that are used to make fingerprint identification technique more secure. Research has resulted in the identification of more unique features in the fingerprint. However, all these features are not incorporated in the recognition technique. The main minutiae types that are used in the identification process include the bifurcation and the points where ridges end. Bifurcations refer to the points where the ridges split and become two while the ridge ends refers to the points where the ridges terminate (Lin, Yifei, & Jain, 1998).
The importance of the ridges in this recognition technique means that their quality once the image of the fingerprint has been taken is of great importance. This is because their quality will ensure that the processing of the image and the matching stage will be done without encountering errors. However, the quality of the ridges that is obtained from the image is not always to the required standards. This may be attributed to the corruption of their clarity by noise that may have affected their quality (Pankanti, Prabhakar, & Jain, 2002). In such cases, the image that is obtained needs to be enhanced to ensure that the quality that is required is achieved. This process is done before the identification process is conducted. Different techniques may be employed to ensure that the enhancement of these images is conducted to obtain the quality that is required for identification. The main methods that are used include the use of Gabor filters and the directional Fourier filtering (Hong & Jain, 1998).
The first step in the technique is the normalization of the ridges. This is then followed by the estimation of their orientation and their frequency. Finally, filtering is conducted to ensure that the fingerprint image is enhanced. The normalization process in fingerprint enhancement aims to change the image’s mean and variance to attain the recommended values (Delak & Grgic, 2004). It also ensures that variations due to factors such as uneven contact between the finger surface and the capturing device when the fingerprint image is being obtained are taken care of. Also of concern is the uneven distribution of the finger print ink. This deficiency is also corrected by the normalization process. The frequency selectivity and the orientation of the fingerprint are enhanced through the use of the Gabor filters. These filters are band pass filters that are tuned such that their selectivity is very high (Moenssens, 1971). Their tuning is set to the required values and this enables them to enhance the image according to these values.
The other technique that may be used in the fingerprint enhancement process is the directional Fourier filtering. This technique has the advantage of cost when compared to the use of Gabor filters. The cost of using the technique is lower. In this method, the orientation of the fingerprint image is calculated. This is by the use of 16 directions in which the image is oriented during the calculation process (Weaver, 2006). The fingerprint image is rotated through these directions while obtaining information about the projection of the ridges after every rotation. The variances of these projections are also obtained during the process. The projection that has the highest value of projection is perceived to be dominant. This process is repeated for all the available pixels on the image and the combination of all the dominant projections results in the formation of a new enhanced image. The image is then filtered through the use of band pass filters that are tuned to a particular ridge orientation. The Fourier transform is used to convert the image into frequency domain. In the frequency domain, the image is then filtered by filters (Bahuguna, 1996). The number of filters used in this case is also 16 and their tuning is also done to a specific orientation. Once the image has been passed the directional filters, it is converted to the special domain from t6he frequency domain.
The image then undergoes a final enhancement stage where pixel values are used to obtain the enhanced final image. Therefore, these techniques that are used for image enhancement are mainly based on the use of filters. These filters are tuned to respond to the required characteristics of the fingerprint. These fingerprint enhancement techniques have four main stages. The first is normalization. After this process, estimation of the orientation of the ridges is done. This is followed by the estimation of the frequency of the ridges. Finally, filtering is done. Other important stages that are incorporated in the process include segmentation and thinning (Rhodes & Brtillon, 1956). Segmentation is the process where the actual part of the fingerprint is differentiated from the background (Brunelli & Falavigna, 1995).
This is done during the process where the fingerprint image is being obtained for authentication. This is a necessity during this process since it ensures that only the fingerprint image is acquired and would subsequently be processed without the presence of other components that may act as noise. Presence of the background in the image may distort the processing of the fingerprint and consequently resulting in errors being encountered as false minutiae may be obtained. The separation is mainly done through the comparison of variance values. Thinning on the other hand is done before the extraction of the minutiae is done. This is to ensure that the width of the foreground pixels is one pixel for each of them (Parks, 1991). This is achieved by the removal of any additional width if present.
The enhancement of the image is the initial stage of processing. The image that has been enhanced has to undergo other processes. The extraction of the minutiae is one of these processes. Once the extraction of the minutiae is done, the image that is obtained is then processed to ensure that there is no possibility of the minutiae being false. Minutiae extraction may be done using different techniques. The one used in this method is the Crossing Number (CN) concept (Jain & Ross, Multi-modal biometrics, 2004). This method uses the patterns of the ridges together with the enhanced image. The ridge pixels are scanned by the use of a 3X3 window to obtain the minutiae (Jain & Ross, Multi-modal biometrics, 2004). Computation of the Crossing Number is then performed. This involves the comparison of the pixels that are adjacent in the eight-neighborhood. The properties of the Crossing Number that are used are shown below.
The classification of the ridge pixels can then be done according to the details provided in the Crossing Number properties. This means that if the crossing number of 2 is obtained, the ridge pixels will be classified as a continuing ridge point. This process relies on the skeleton image to be able to extract the minutiae (Turk & Pentland, 1991). Once the minutiae are obtained, it is subjected to further processing to ensure that all the false minutiae that may be present in the image are eliminated. The structures that may represent a false minutiae include spur structures, hole structures, triangle structures and spike structures (Ashbaugh, 1991). When these structures appear in the minutiae they may act as either bifurcations if a hole, triangular or spike structures appear. They may also act as false ridge endings if the spur and spike structures occur. The appearance of the false minutiae may lead to errors during the decision process. Rules are set to govern the way false minutiae are removed. These rules are used to govern the validity of a ridge ending and also a bifurcation. If the identified ridge ending does not conform to the standards that are set by these rules, it is discarded as a false bifurcation of a ridge.
Current biometric authentication practice in the UK
The UK has adapted different biometric techniques in the activities that are managed by the private sector and also the government. This is due to the desire to enhance the security of an organization. The applications of the biometric techniques in the UK may be divided into three categories. These include the forensic category, the government and lastly the commercial applications. The forensic category is mainly used in the identification of dead bodies that isolated to ensure that the family of the deceased is notified. It is also used in the identification of the parents of a child for example if there is a dispute in the court. This is important since it servers to settle the cases. The UK government uses biometric for a number of purposes. Firstly the passports are electronically generated. Theses passports have a chip that holds the data of a particular individual (Condon, 2007). The schools in the UK have also implemented the use of biometrics in their systems. Schools use the fingerprint technique to identify their students before entry to the compound and also other points within the school compound.
The government has also implemented the use of biometrics in its security buildings and the prison department. The identification of inmates has also incorporated the use of facial recognition where the facial images of the criminals are taken. Border security is also enhanced in the UK through the use of the biometric techniques. This ensures that immigrants do not enter the country illegally. At the transport terminals such as the airports, biometrics is used to ensure that the people boarding the planes are counterchecked to ensure that those who are boarding the planes are the same people who checked in. Biometrics has also been applied in the financial institutions. These include the ATM machines where the fingerprint authentication technique is being used. The biometric authentication for transaction over the internet has also been enhanced (Condon, 2007).
Methodology
Introduction
In order to carry out effective research, the research method has to be identified. The choice of a particular design is dependent on a number of factors. The research design is a stepwise procedure that shows how the research will be carried out. These include the problem which the research intends to solve and also the duration of time that the researcher has. The research design ensures that all the information that is collected meets the requirements of the research and aims to solve the objectives of the research. Therefore the research design should be chosen to ensure that all the objectives of the research are met within the allocated time for the research. This section deals with the research design and the methods that have been used to collect information for the research activity.
The research that has been carried out previously in the field of biometrics mainly focused on the implementation process of the biometric techniques and how this affected the current systems that were being used. The researchers mainly focused on improving the system to ensure that a system that was as efficient as possible was developed. The recommendations on how they intended to achieve this are also included in their research. The research that I carried out aimed to collect information about various issues that affect the biometric techniques and how the implementation of biometrics has made a difference in the current society. Therefore, the research focuses on how the biometric techniques have been implemented and where they are used, how different techniques have been accepted and also their individual merits and demerits.
The availability and accessibility of the previous research that had been carried out is important to my research as it will act as a source of secondary data for my research. This data is very helpful when coming up with conclusions since it involves recommendations that were made after research was carried out. They can therefore act as very important documents for comparison between the data obtained and that which was obtained before.
The methodologies that may be used in carrying out the research vary. There are various methods that can be applied. These include; the exploratory research approach, the explanatory research approach, the conclusive research approach and the performance monitoring research approach. The exploratory research approach is used where very limited knowledge is known about the topic being studied. It is used to gather more information about the topic and ensure that the best possible solution is applied. In this research this method was employed to get information about the implementation of biometrics.
This information included details on which methods are preferred and why and also the reasons why other methods are not easily acceptable. An explanatory research approach on the other hand aims to establish the causes of certain results in a research. It relates the causes and the effects of those causes on the result that is produced. In this research, this approach was used to analyze the effects of the introduction of the use of the biometric passports in the UK. The descriptive research approach requires that the researcher has more information about the topic being studied. It may be used to compare the researches that were already carried out with the one that is presently being carried out.
Data Collection
Data collection is an important aspect when carrying out any research activity. This is because the data that is collected will act as a very important tool during the analysis and conclusion of the research. The choice of the data collection methods to be used in any research therefore becomes an aspect that cannot be overlooked to ensure that the data that is collected is of use for the intended analysis. The data collection methods that were used during this research included observation, the use of questionnaires and also interviews. These techniques acted as a source of primary data for the research. The records that are contained in journal articles that related to the research were also consulted to ensure that proper analysis was carried out. The advantages of using the primary sources of information such as the interviews are that the information is not distorted. It is obtained directly from the source and therefore in most circumstances it is accurate. The researcher can also ask for clarifications incase there are areas that are not clear and this ensures that the data collected is devoid of errors.
Information about the research was obtained from a sample of 50 individuals. These were selected carefully to ensure that they were representative of the entire population. The selection ensured that the members were from different age groups that captured the young, middle aged and also the old. The respondents also included people that were from different levels of education. As stated earlier, the aspects of the research that were being investigated included how the technology has been used, the various contributors to the efficient use of the technology, how the technology is accepted in the society, what biometric techniques are mostly preferred and the advantages and the disadvantages of the individual techniques. Interviews were conducted within the selected sample. Observations on the use of different biometric techniques were also made. Questionnaires that contained both open ended and closed questions were distributed to the samples and the results that were obtained were analyzed. The data that was collected and its analysis are discussed below.
The response of the respondents when asked which biometric technique they prefer and where the biometric techniques should be implemented are shown and explained below.
The above data may be represented in a pie chart as shown below.
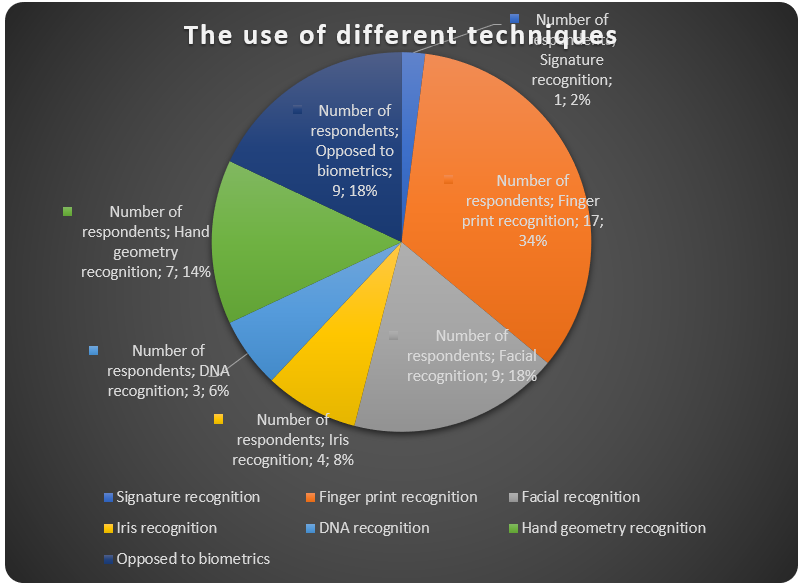
From the pie chart above, it can be seen that 34% of the respondents favored the use of the fingerprint technique, 18% favored the use of facial recognition technique, and another 18% were opposed to the use of biometrics, 14% favored the use of hand geometry for authentication, 8% favored the iris recognition technique, 6% were for DNA recognition and 2% favored signature recognition. It can be concluded that most of the people favored the use of the fingerprint technique as a method of authentication. When asked why the chose this technique, they gave the reasons as to why this was their preferred choice. These reasons included that the technique has been used for many years. Therefore, it has been subjected to advancements and the bugs that were initially in the system during its inception have now been removed. They also felt that the use of the current fingerprint authentication technique results in more accurate results being obtained. Most of the respondents who chose this technique also said that the technique is easy to implement and use. Its cost is also considerably lower than that of other techniques. Finally they said that the technique can be used anywhere since it is not affected by the prevailing physical conditions.
When the respondents were asked where the biometrics technique should be applied, their response covered nearly all the places where currently the technique has been applied. Most of them insisted that it should be applied at security checkpoints such as at the boarder points and also at the entrance of buildings. The also preferred it being used at transport terminals such as airports and at train stations. The use of biometrics at financial institutions was also mentioned with emphasis being made on its use in automated teller machines and transactions that are carried out over the internet.
The respondents were also asked of their thoughts on the role of the government, the businesses and the users in the biometric systems. Most of the respondents indicated that the government should ensure the implementation of the methods that will enhance security to its citizens since this is one of the prime functions of any government. The also felt that the government should be on the forefront in ensuring that the biometric standards are developed and implemented to ensure that there are laid rules and regulations for its use. Few respondents felt that it is the duty of the government to ensure that more research is conducted in the field. The response of the respondents on the role of businesses was that they should ensure that the techniques that are employed are favorable for the environments for which they are required to operate in.
The businesses should also be involved in carrying out research to ensure that the field of biometrics become more secure and new technologies that will ensure increased security are developed. The respondents also said that the role of the users is to ensure that they follow the standards that have been laid out for the use of all the biometric techniques. They should also ensure that the gain the necessary knowledge to be able to use the biometric techniques effectively without causing any damage to these systems. Finally, the users should ensure that their biometric information is protected and is not used for other purposes other than authentication.
The advantages and the disadvantages of biometrics as a way of authentication were also investigated. The compilation of the response by the respondents is summarized in the table below.
A graph illustrating this distribution is shown below.
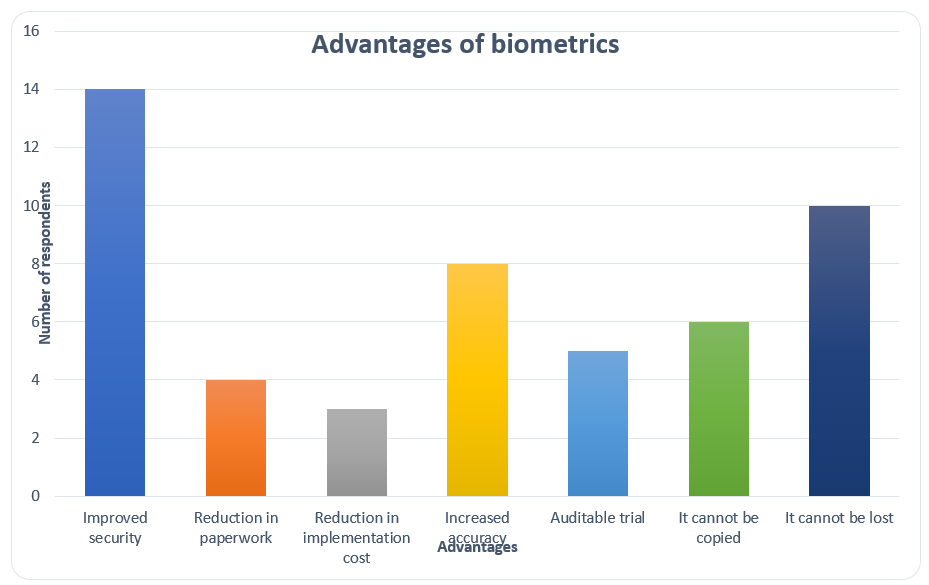
The data shows that most of the respondents felt that the main advantage of biometrics is the fact that it has resulted in increased security where it has been used. This if followed by the fact that the biometric data cannot be lost. This is compared to the other authentication techniques such as the use of passwords and also tokens. The passwords can be lost or even forgotten but when it comes to biometrics this is not possible. The low cost of its implementation, increased accuracy, reduction in the amount of paperwork required, its trial being auditable and also the fact that it cannot be copied were also the other advantages that were mentioned by the respondents. The research about the drawbacks of the system was also conducted. The main concern among most of the respondents was the privacy issue.
Most of them felt that the use of biometrics will make them susceptible to security lapses. Their privacy may also be compromised as a result of using the system. Other disadvantages that were mentioned included the reluctance of the people to respond to change. Most respondents felt that many people will still feel that using the authentication techniques that they are used to are more secure than changing to the use of biometrics. They felt that this will result in a decrease in the number of the people using the technique and the projections that were made on the number of people that will use the system may not be achieved.
Conclusion
The biometrics authentication technology has played an important role in the transformation of the user authentication process. Initially, the authentication process mainly involved the use of passwords. This was prone to certain disadvantages which included forgetting the password. In case of such an occurrence, the person was not able to access the system unless the password was obtained or the system was reset. The password could also be obtained by another person and gain unauthorized entry to the system. Tokens were also used and they needed to be carried anytime the person needed to authenticate and gain access to the system. Biometrics implementation has ensured that all these problems and difficulties are eliminated. This is because with the biometric system, only the availability of the person requesting for system access is required. The problem of losing the token or forgetting the passwords is also eliminated by this technique. The biometric technique has also posed an advantage in the fact that it has aided in the increase in the level of security. Since its implementation, the cases of insecurity as a result of unauthorized access have decreased considerably. This may be attributed to the personalization of the access methods because the technique requires the physical presence of the person who is allowed to gain access to the system
However, there are also concerns about the use of the biometric technique for user authentication. These concerns are mainly in the line of privacy. The users feel that once they give out their information to the biometric systems, the information may be used for other purposes and not just authentication. The tracking of their whereabouts once they authenticate at a particular point also acts as an issue that the technique should sort to correct. The users also feel that the technique may be used to gain more details such as the social security, insurance and even the savings of the individual by use of the provided information. These factors act as the drawbacks to the implementation of this technique.
Recommendations
The drawbacks of biometrics as a technique need to be looked at and eliminated to ensure that the system is adopted by an increased number of individuals and the corporate world. Measures should be put in place to ensure that the information that is provided by the users of the biometric system is used solely for purposes of authentication. Incase the information is used for other purposes; the consent of the user should first be sorted. This will ensure that the privacy of the users is observed and may promote the use of the system. More standards that govern the use of the biometric techniques should be developed to ensure that the systems are run efficiently and effectively. The users should also be educated on the techniques that are available and how to use them. This will ensure that the systems are not misused and only serve the purposes that they were designed to. More research should also be conducted in the field of biometrics to ensure that more biometric authentication techniques are established and those that are available are improved to enhance security.
References
Adini, Y., Moses, Y., & Ullman, S. 1997, ‘Face recognition’, IEEE Transactions on Pattern Analysis and Machine Intelligence, Vol. 3, No. 1, pp. 731-732.
Ashbaugh, R. 1991, ‘Ridgeology’, Journal of Forensic Identification, Vol. 1, No. 6, pp. 16-64.
Ashbourn, J. 2000, Biometrics, Springer, London.
Bahuguna, R. 1996, ‘Fingerprint verification using hologram matched filterings’, Proceeding of Biometric Consortium Eighth Meeting, Vol. 8, No. 3, pp. 26-35.
Bartmann, D. 2006, ‘Design of an authentication system based on keystroke dynamics using a pre-defined input text’, International Journal of Information Security, Vol. 1, No. 1, pp. 10-12.
Bishop, M. 2010, Computer Security, Pearson, Boston.
Brunelli, R., & Falavigna, D. 1995, ‘Person identification using multiple cues’, IEEE Transactions on Pattern Analysis and Machine Intelligence, Vol. 3, No. 6, pp. 955-966.
Campbell, P. 1997, ‘Speaker recognition’, Proceedings of the IEEE, Vol. 3, No. 1, pp. 1437-1462.
Chellappa, W., Phillips, P., & Rosenfeld, A. 2003, ‘Face recognition’, ACM Computing Surveys, Vol. 1, No. 7, pp. 399-458.
Chirillo, J. 2003, Implementing Biometric Security, McGraw Hill, New York.
Condon, R. 2007, ‘New biometrics see right through you’, Inforsecurity, Vol. 5, No. 1, pp. 24-25.
Delak, K., & Grgic, M. 2004, ‘A survey of biometric recognition methods’, International Symposium Electronics in Marine, Vol. 12, No. 4, pp. 16-18.
Deravi, F. 2008, ‘Biometric standards’, Advances in biometrics, Vol. 2, No. 12, pp. 473-489.
Dougman, J. 2004, ‘How iris recognition works’, IEEE Transactions on Circuits and Systems for Video Technology, Vol. 23, No. 14, pp. 21-30.
Galton, F. 1892, Fingerprints, Mcmillan, London.
Grembi, J. 2008, Secure Software Development, Cengage Learning, Boston.
Hong, L., & Jain, A. 1998, ‘Intergrating faces and fingerprints for personal identification’, Proceedings of Asian Conference on Computer Vision, Vol. 3, No. 10, pp. 8-11.
Huang, P., Luo, W., & Chen, Y. 2002, ‘An efficient iris recognition system’, Proceedings of First International Conference on Machine Learning and Cybernetics, Vol. 30, No. 17, pp. 4-5.
Jain, K., & Ross, A. 2004, ‘Multi-modal biometrics’, Proceedings of the 12th European Signal Processing Conference, Vol. 9, No. 6, pp. 1221-1224.
Jain, K., Ross, A., & Prabhakar, S. 2004, ‘An introduction to biometric technology’, IEEE Transactions on Circuits and Systems for Video Technology, Vol. 36, No. 11, pp. 4-20.
Lakhmi, J. ,1999, Intelligent Biometric Techniques in Fingerpring and Face Recognition, CRC Press, London.
Lin, H., Yifei, W., & Jain, A. 1998, ‘Fingerprint enhancement’, IEEE Transactions on Pattern Analysis and Machine Intelligence, Vol. 34, No. 23, pp. 777-789.
Miller, B. 1994, ‘Vital signs of identity’, IEEE Spectrum, Vol. 56, No. 18, pp. 22-30.
Moenssens, A. 1971, Fingerprint Techniques, London, Chilton Book Company.
Monrose, F., & Rubin, A. 2009, ‘Keystroke dynamics as a biometric for authentication’, Future Generation Computer Systems, Vol. 15, No. 8, pp. 351-359.
Nalini, R., & Bolle, R. 2004, Automatic Fingerprint Recognition, Springer, New York.
Nalwa, V. 1997, ‘Automatic on-line signature verification’, Proceedings of IEEE, Vol. 24, No. 10, pp. 213-239.
Nanavati, S. 2002, Biometrics, Prentice Hall, Boston.
Pankanti, S., Prabhakar, S., & Jain, A. 2002, ‘Individuality in fingerprints’, IEEE Transactions on Pattern Analysis and Machine Intelligence, Vol. 63, No. 17, pp. 1010-1025.
Parks, R. 1991, ‘Persona identification – biometrics’, Information Security, Vol. 3, No. 3, pp. 181-191.
Parziale, G. 2008, ‘Touchless fingerprint technology’, Advances in Biometrics, Vol. 2, No. 1, pp. 25-48.
Phillips, P., Rauss, J., & Der, Z. 1997, ‘The face recognition technology evaluation methodology’, Proceedings of the IEEE Conference on Computer Vision and Pattern Recognition, Vol. 14, No. 6, pp. 36-48.
Ratha, K., Cornell, H., & Bolle, M. 2006, ‘A case study in fingerprints’, Cancelable Biometrics, Vol. 13, No. 7, pp. 370-373.
Reid, P. 2003, Biometrics for Network Security, Prentice Hall, Boston.
Rhodes, F., & Brtillon, A. 1956, Father of Scientific Detection, Aberland-Schuman, New York.
Ryan, R. 2009, ‘Importance of biometric standards’, Biometric Technology, Vol. 1, No. 2, pp. 7-10.
Turk, M., & Pentland, A. 1991, ‘Eigenfaces for recognition’, Journal of Cognitive Neuroscience, Vol. 4, No. 4, pp. 71-86.
Wayman, J., Jain, A., Maoltoni, D., & Maio, D. 2005, Biometric Systems Technology. Springer: London.
Weaver, C. 2006, ‘Biometric authentication’, Computer, Vol. 6, No. 3, pp. 96-97.
Woodward, J., Orlans, N., & Higgins, P. 2003, Biometrics, McGraw Hill, New York.