Abstract
Biometric ID management systems have been thoroughly discussed in recent years and are now universally utilized for security purposes. At present, the two primary types of biometric systems include physical and behavioral approaches. The two models have distinct advantages and disadvantages, including cost-efficiency, simplicity of implementation, and accuracy rates. Most modern biometric ID management systems belong to one of these approaches and are utilized in diverse settings. The current paper thoroughly explains the underlying principles of biometrics and discusses the primary features and functions of various biometric ID management systems.
Introduction
In general, biometrics refers to measurements and analysis of certain biological characteristics, such as faces, fingerprints, or voices. However, this concept is commonly associated with biometric identification or authentication of individuals, which has become one of the most prominent security system types in the world (Akhtar et al., 2018). At present, biometric technologies are increasing in popularity due to the versatility of the model and are particularly efficient in border control, forensics, and law organizations (Drozdowski et al., 2020). Furthermore, private businesses and commercial organizations are also implementing biometric identification and authentication to improve data security (Drozdowski et al., 2020). Nevertheless, biometrics is a complex area of technological research, and people frequently lack a comprehensive understanding of the framework. Therefore, it is essential to continually improve the system and raise people’s awareness concerning biometric technologies. The current paper examines the primary features and functions of a biometric ID management system and provides a detailed overview of the biometric technologies in this area of research.
Theoretical Background
However, before discussing the features and functions of the biometric ID management system, it is essential to establish the theoretical background for further analysis. The underlying principle of biometric identification is the uniqueness of biological patterns in every individual; thus, every person has different biological quantitative information (Akhtar et al., 2018). This data ranges vastly from unique facial features to finger veins and brainwaves, making biometrics identification a highly versatile but secure system (Akhtar et al., 2018). The standard techniques primarily include fingerprints, faces, and iris authentication due to the convenience and relative simplicity of the methods (Akhtar et al., 2018). The standard mechanism of biometric identification is the following: the user inputs the data – the biometric sensor reads the input and extracts the necessary features – the received data is compared to the information in the database (Akhtar et al., 2018). Consequently, if the input matches the entry in the database, the user is granted access. The described approach is the standard biometric system implemented in a large variety of settings and locations.
Biometric Identification Types
Biometric identification refers to the recognition of personal features and is the most significant step in biometrics management. The two primary areas of biometric identification are physical and behavioral biometrics (Alzubaidi & Kalita, 2016). The former concerns unique physical characteristics, such as facial features, fingerprints, and brainwaves (Akhtar et al., 2018). The latter refers to behavioral patterns of individuals, such as the manner of talking and walking, or hand-waving, signatures, and keystrokes (Alzubaidi & Kalita, 2016). The underlying principles and complexity of the identification processes differ significantly, depending on the biometric type and standards (Akhtar et al., 2018). At present, physical measurements – fingerprint and face recognition, specifically – dominate the field of biometric security systems due to the ease of the methods and well-documented research (Alzubaidi & Kalita, 2016). However, it is possible that behavioral biometric ID systems become more prominent with the continual development of software, hardware, and the introduction of innovative technologies.
Biometric ID Management Systems
Having established the theoretical background of biometric identification, it is possible to examine the contemporary ID management systems based on physical and behavioral biometric patterns. At present, biometric ID management systems are taking over the traditional authentication methods, such as passwords or knowledge-based verification (Recfaces, 2020). While there are certain disadvantages to most biometric technologies, biometric identification demonstrates better security and convenience compared to traditional models (Recfaces, 2020). Each biometric ID management system has unique features, functions, advantages, and drawbacks; therefore, companies need to understand the specific characteristics of the models before implementing them (Recfaces, 2020). The current sub-chapter provides a detailed description of the most prominent biometric identification management systems and lists the advantages and disadvantages of the frameworks.
Fingerprint Recognition
The most standard and widespread type of biometric identification system is fingerprint recognition. This approach utilizes the conventional feature extraction from the sensors and compares the received data with the entries in the databases (Yang et al., 2019). Fingerprint recognition is used in various settings, including law enforcement organizations, border control, consumer biometrics, and financial services (Yang et al., 2019). This type of biometric identification demonstrates high accuracy rates and excellent security since every individual has unique fingerprints, and this measurement can be used to even distinguish identical twins (Yang et al., 2019). As a result, fingerprint biometric identification models are highly prominent in modern security systems and are universally utilized.
Nevertheless, there are certain disadvantages to the fingerprint recognition system. First, the biometric system might not capture the correct input if the minutiae (unique fingerprint patterns) are damaged in some way. It frequently occurs due to the intense friction of the fingers with a rough surface. For instance, the minutiae are damaged severely after rock climbing or hard physical labor and need a recovery period of several days to be recognized by the biometric systems again. Other types of physical biometrics have the same issues; however, the damage to fingerprints occurs more frequently than to the face or iris. Secondly, while the security of fingerprint recognition systems demonstrates better results than those of traditional approaches, the framework is not foolproof (Joshi, Mazumdar & Dey, 2018). At present, the improvement of biometric systems is a relevant topic, and various methods, such as neural networks, deep learning-based anomaly detection models, and vulnerability simulation, are used to enhance security (Joshi et al., 2018). Therefore, while fingerprint recognition systems are highly relevant in biometrics, there is still much work to be done to optimize the method.
Face Recognition
Face recognition is another type of physical biometric identification that is widely accepted throughout the whole world and is relatively simple in implementation. These systems are highly prominent in law enforcement and criminal identification (Abdullah et al., 2017). For instance, it is possible to utilize face recognition biometrics to compare people’s faces with the inputs from criminal databases to alert law enforcement organizations concerning potential illegal activity (Abdullah et al., 2017). The design of face recognition biometrics is relatively standard and is presented in the chart below:
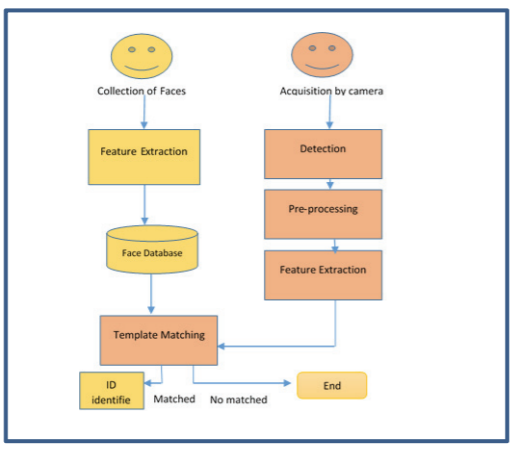
Ultimately, face recognition biometrics are not restricted to security functions but are also highly prominent in law enforcement for investigation and crime prevention purposes.
Similar to other types of biometrics, face recognition has a number of advantages and disadvantages. The advantages of the method include the simplicity of implementation, the non-contact nature of biometric input, and the capability to identify several people simultaneously (Ye et al., 2020). Face recognition systems might also be easily expanded by adding additional image inputs to the databases (Ye et al., 2020). However, this biometric ID management system is prone to several drawbacks. Specifically, face recognition demonstrates low accuracy rates due to environment lighting and can be relatively easily deceived via makeups and facelifts (Ye et al., 2020). Furthermore, the implementation of the system requires higher expenses compared to the fingerprint recognition approach (Ye et al., 2020). Ultimately, while face recognition is a relevant and easily accessible method, it has a number of drawbacks obstructing the efficiency of the approach.
Iris Recognition
Iris recognition is a type of physical biometrics that is frequently utilized to secure data of major significance. The primary reasons for such an approach include high costs of implementation, the necessity of complex hardware and software, and relatively inconvenient usage (Ye et al., 2020). However, the method is associated with excellent stability and accuracy due to the unique method of assessment and the impossibility to counterfeit the input (Ye et al., 2020). The structure of a human eye comprises the sclera, iris, pupil lens, and retina, and each of the said components has a unique sub-structure and personal characteristics (Ye et al., 2020). As a result, the stability and security of iris recognition significantly surpass those of other biometric systems and exceed the stability of fingerprint recognition (Ye et al., 2020). Ultimately, iris recognition is a highly secure biometric system; however, the implementation of the system is complex and associated with large expenses.
Voice Recognition
Unlike previous identification methods, voice recognition is a behavioral biometric technology. Similar to physical systems, behavioral technologies follow a structured and hierarchical algorithm – registration, preprocessing, feature extraction, and matching (Alsaadi, 2021). Voice recognition is one of the most prominent behavioral systems that continually become more popular in the field of biometric security (Alsaadi, 2021). The idea of voice biometrics has been derived from the established methods of speech recognition, which were first implemented in the 1960s (Alsaadi, 2021). Since then, technologies have been improved drastically, and nowadays it is possible to extract unique features from people’s voices and implement voice biometrics (Alsaadi, 2021). At present, voice recognition is a prominent biometric system that receives attention not only from the security perspective but also from areas of technological research.
The advantages of this approach are the reliability and convenience of authentication. The disadvantages of the system primarily concern the biometrics traits. The uniqueness of the voice features stems from the individual structure of people’s vocal organs, such as mouths and throats (Alsaadi, 2021). Therefore, if a person suffers from throat infections or other sicknesses, the accuracy of the biometric management system might be reduced significantly (Alsaadi, 2021). Furthermore, the voice is affected by emotions, the process of aging, and the overall state of physical health, which might further influence the reliability of the system.
Gait Recognition
Gait recognition is a relatively new type of behavioral biometrics and refers to the analysis of how people walk. The extracted features of this biometric system are generally the characteristics of a stride, such as a length, cadence, angle, and motion (Rida, Almaadeed & Almaadeed, 2018). However, the innovative approaches might also analyze the whole contours and silhouettes of people to identify them – this method is known as model-free gait recognition (Rida et al., 2018). The advantages of this system include the relative simplicity of implementation and cost-efficiency (Alsaadi, 2021). However, the accuracy of gait recognition might be significantly reduced due to clothes interference, injuries, or if the observed individual carries an object (Alsaadi, 2021). Therefore, if the silhouette or gait is obstructed in some manner, the biometric system will most likely provide inaccurate results.
Keystroke Recognition
Keystroke recognition is another type of behavioral biometrics that has been gaining increasing popularity in recent years. In general, this biometric system analyzes typing patterns via keyboards (Ali et al., 2016). Research has established that people have unique typing features, including speed, frequency, finger positions, and pressure on the keys (Ali et al., 2016). Naturally, it is essential to provide a special keyboard that is responsive to all biometric features for this approach to be successful (Ali et al., 2016). Despite the necessity of special equipment, keystroke recognition is the cheapest and easiest to implement biometric system; however, this approach also has the lowest accuracy rates (Ali et al., 2016). Ultimately, keystroke recognition is a cost-efficient biometric ID management system, but it should not be used to protect data of utmost significance.
Conclusion
Summing up, the current paper has provided a theoretical background to biometrics and examined the core functions of a biometric ID management system. The two primary types of biometric ID systems are based on either physical or behavioral patterns. The former is utilized in fingerprint, face, and iris biometrics, while the behavioral measurements are used in voice, gait, and keystroke recognition. The major function of all biometric systems is improved security; however, some of the frameworks, such as face recognition, are also used widely in investigation and crime prevention. Ultimately, biometric ID management systems provide better security than the traditional approaches and might become even more prominent in the future.
References
Abdullah, N. A., Saidi, J., Ab Rahman, N. H., Wen, C. C., & Hamid, I. R. A. (2017). Face recognition for criminal identification: An implementation of principal component analysis for face recognition. In AIP Conference Proceedings 1891. Web.
Akhtar, Z., Hadid, A., Nixon, M. S., Tistarelli, M., Dugelay, J. L., & Marcel, S. (2018). Biometrics: In search of identity and security (Q & A). IEEE MultiMedia, 25(3), 22-35.
Ali, L., Monaco, J. V., Tappert, C. C., & Qiu, M. (2016). Keystroke biometric systems for user authentication. Journal of Signal Processing Systems, 86(2-3), 175-190. Web.
Alsaadi, I. M. (2021). Study on most popular behavioral biometrics, advantages, disadvantages and recent applications: A review. International Journal of Scientific & Technology Research, 10(1).
Alzubaidi, A., & Kalita, J. (2016). Authentication of smartphone users using behavioral biometrics. IEEE Communications Surveys & Tutorials, 18(3), 1998-2016. Web.
Drozdowski, P., Rathgeb, C., Dantcheva, A., Damer, N., & Busch, C. (2020). Demographic bias in biometrics: A survey on an emerging challenge. IEEE Transactions on Technology and Society, 1(2), 89-103. Web.
Joshi, M., Mazumdar, B., & Dey, S. (2018). Security vulnerabilities against fingerprint biometric system. Web.
Recfaces. (2020). Biometric authentication, identification, and verification in 2021. Web.
Rida, I., Almaadeed, N., & Almadeed, S. (2018). Robust gait recognition: A comprehensive survey. IET Biometrics. Web.
Yang, W., Wang, S., Hu, J., Zheng, G., & Valli, C. (2019). Security and accuracy of fingerprint-based biometrics: A review. Symmetry, 11(141), 1-19. Web.
Ye, H., Pei, R., Mo, Z., Zheng, Q., & Chen, H. (2020). Comparison of the security of biometrics. Journal of Physics: Conference Series, 1607. Web.