Abstract
The present article sets out to employ the ever-evolving knowledge of design science in information science research to conceptualize the problem of incorrect academic certifications doing rounds in places of employment or in academic institutions, which primarily originates from illegal activities such as forgery or identity theft. To prevent these instances, we propose an electronic web-based Certification Verification Program.
Using the Stakeholders perspectives to understand the problem and implement an effective and efficient web-based artifact aimed at dealing with this menace, the article discusses the various phases and processes entailed in enlisting the stakeholder’s concerns, proposing a solution to the problem, prototyping, and building and evaluating the artifact against specific benchmarks, such as utility and efficiency of the proposed artifact in real-world settings.
Through the incorporation of various security levels, authentications, and user and content access control mechanisms in each of the components that function to serve the different stakeholders, in our case – the sender, receiver, and controller, this article sufficiently demonstrates how the Certifications Verification Program could be beneficial to all stakeholders, particularly with regard to ensuring transparency and accountability in policies and privacy practices, ensuring the quality of data, enhancing data collection limitation, guaranteeing purpose specification, and safeguarding the consent of users.
Introduction
Although the boundaries and contours of design sciences continue to experience numerous definitions and refinements as we progress deeper into the 21st century, and in spite of the fact that the sciences of design are seen as a comparatively new entrant to the prism of methodologies, paradigms, and perspectives that have been dominated by ongoing debates formerly only positioned as positivist versus interpretive and quantitative versus qualitative (Purao et al, 2008), academics and practitioners are in agreement about the fundamental importance and value of the subfield to the information systems discipline (March & Storey 2008). Although this shift became visible in the information systems (IS) discipline only since the mid-1990s, according to these authors, design science has in the past received widespread attention and indeed practiced as an important mode of research in other specialized disciplines, including architecture, building economics and engineering. The seminal works of Hevner et al (2004) highlighted design science research as a clear alternative to the IS discipline, leading to the progression of two paradigms that characterized research in the IS discipline, namely behavioral research and design science.
The present article seeks to utilize the knowledge that has so far been gathered in design science to design, implement and evaluate a proposed information technology artifact, known as the Certifications Verification System, which could be used not only to prevent some illegal activities associated with paper-based certificates but also facilitate the storage, management, and retrieval of academic certifications papers for students. Available literature demonstrates that such an artifact, if well designed and implemented, could have the capacity to improve the efficiency and performance of business/learning institutions (March & Storey 2008), but also maximize their value and competitiveness (Germonprez et al 2011).
To understand the dynamics of the proposed IT artifact, it is important to provide an overview of design science research, as follows.
An Overview of Design Science Research
Hevner et al (2004) acknowledge that the design-science paradigm in IS discipline “…seeks to extend the boundaries of human and organizational capabilities by creating new and innovative artifacts” (p. 75). The paradigm is placed at the confluence of people, organizations, and technology (Hevner et al 2004), and is endowed with the functionality of developing, implementing, using, and managing information systems within organizational contexts with the view to change existing situations into preferred ones. Design science researchers operating within organizational contexts can therefore utilize information technology (IT), among other resources, to design and outline work systems and processes through which critical organizational objectives are achieved.
Simon cited in March & Storey (2008) noted that design science research is grounded in two important phases, namely
- the definition of the problem space, and
- optimization techniques to search it.
According to these authors, the problem space denotes the desired end situation, the present organizational situation, and the variations between the desired end situation and the present situation. The optimization techniques, on their part, denote actions that may be taken by design and management professionals to eradicate acknowledged variations between the desired end state and the present state.
Hence, it is important to note that “…the representation of design problems and the generation and evaluation of design solutions are the major tasks in design science research” (March & Storey 2008, p. 726). As noted by these authors, the challenges for design science research in the IS field to develop and evaluate IT artifacts that facilitate management and IT, staff, too, among other things,
- describe desired organizational information processing capabilities and their relationship with present and desired organizational situations, and
- develop actions that enable them to implement information processing capabilities that move the organization towards desired situations” (p. 726).
It is the major purpose of this paper to develop and evaluate an IT artifact known as the Certifications Verification System, based on the central tenets of design science research in the IS discipline.
The Certifications Verification System
The emergence of information technology (IT) and related applications continue to create novel challenges for the education system, not only in terms of building IT-oriented infrastructure to transfer content and learning materials in between the students and the instructors but also in ensuring the students are graded efficiently and results disseminated to the students in a secure cost-effective way. Today, more than ever before, IT professionals and experts in the education sector are working with increasingly complex problems to come up with technology solutions that not only assist in moving information around from one region or place to another, but also facilitate connections between groups of students, learning institutions, and external learning resources (Rye 2009).
Most of these technologies, as typically suggested in Shields (2011), have been focused on the provision of on-line course materials, grading and distance education; however, this article seeks to design, develop and evaluate a unique IT-enabled artifact that can account for students’ academic progress and provide certifications to students who have successfully attained the set educational goals. The need to design and develop the Certifications Verification System arises from the corresponding demands to
- safeguard educational quality though the processing and dispensing of authenticated certificates to students and employers,
- expand access to the certificates for students,
- increase economic competitiveness for institutions which adopt the proposed system, and
- facilitate inclusion and equitable distribution of the certificates in a rapidly expanding global information system.
Every certification program, whether paper-based or automated, has its own vulnerabilities which include identity theft and forgeries (Gorard 2010). Considering that certificates are the physical evidence of our academic achievements needed to support further studies and gain formal employment, ensuring that the program’s design is flawless is of utmost importance to learning institutions. The proposed IT-oriented artifact must therefore not only expose and address challenges related to such system vulnerabilities but must also address privacy and confidentiality issues if the system is to achieve the desired end state and sufficiently meet its demands as outlined above.
Representation of Design Problems
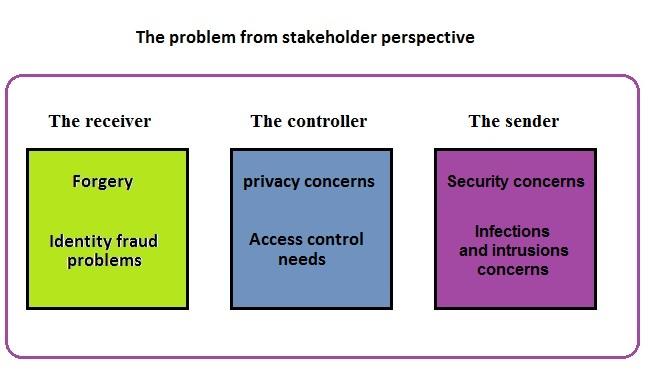
First, it is imperative to note that the representation of design problems for the proposed Certifications Verification Program will be conceptualized around three stakeholders, namely:
- the receiver – potential new employer or educational facility,
- the controller – a graduated person who is going to control the access permissions and authorizations, and
- the sender – an academic institution that processes the certification.
Each of these stakeholders has some demands and concerns (design problems), conceptualized, and illustrated as follows.
The receiver
This stakeholder demands the right certification and the right person, primarily driven by real or perceived concerns about the circulation of fake certifications and identity fraud. It has been reported in the literature that these illegal activities emerge due to paper-based certificates (Murthy 2011), not mentioning that some online sites engaged in providing fake certificates to potential customers (Shields 2011).
This article will focus on two such illegal activities, namely:
Forgery
Forgery is defined in State v. Lutes,38 Wn.2d 475, 479, 230 P.2d 786 (1951), as “… the false making of an instrument, which purports on the face of it to be good and valid for the purposes for which it was created, with a design to defraud any person or persons….”( State v. Goranson 1965). Unfortunately, the convergence of the technology revolution witnessed in the 21st century has made the creation of fake paper-based documents a reality. In recent years, there are a number of sites available on the Internet which issue fake degree certificates. It is a growing trade worldwide in counterfeit university degree certificates and academic transcripts, which in turn creates potential damage to the universities and employment systems. In May 2004, an audit showed that around 463 employees in the federal government in the US had fake academic degrees (Murthy, 2011).
Identity Fraud
Identity fraud occurs when an individual “…with malicious intent consciously creates the semblance of an identity that does not belong to him, using the identity of someone else or of a non-existing person” (Koops and Leenes 2006). In the scope and context of this article, identity fraud involves a person who, with prior knowledge, wrongfully and deceitfully obtains and uses personal or academic data of another person and passes them as own, characteristically for economic or academic gains. In recent years, the internet has become a fertile ground for criminals to acquire data of other people without their consent and passing them as their own to achieve selfish interests (US Department of Justice n.d.).
Identity fraud can best be described by the works of sociologist and criminologist Cressey (1973) cited in Malgwi & Rakovski (2009), who developed the Fraud Triangle Theory to argue that fraud is likely to occur due to one or more of the three elements in the fraud triangle: perceived pressure, perceived opportunities, and rationalization. Figure 1 illustrates the elements of the Fraud Triangle Theory.
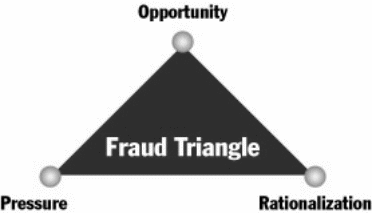
As described by Malgwi & Rakovski (2009), the pressure is what causes a person to commit fraud, and can be ignited by a multiplicity of variables, including medical bills, expensive tastes, and addiction problems, among others. Most of the time, pressure arises from a significant financial need/problem. Opportunity is the ability to commit fraud. Because fraudsters don’t wish to be caught, they must also believe that their activities will not be detected. Opportunity is created by weak internal controls, poor management oversight, and/or through the use of one’s position and authority. Failure to establish adequate procedures to detect fraudulent activity also increases the opportunity for fraud to occur. Rationalization is a crucial component in most frauds and involves a person reconciling his/her behavior (stealing) with the commonly accepted norms of decency and trust (Malgwi & Rakovski 2009).
The Controller
The controller, who in this context happens to be the graduate, must have the necessary control and access permissions and authorizations to ensure that his data are only accessed by the authorized person. Consequently, it is in order to conceptualize privacy concerns and access control needs in the proposed IT-oriented artifact.
Privacy concerns
Privacy is a serious issue in any electronic transaction. Culnan (2000) defines privacy as “…the ability of an individual to control the terms under which their personal information is acquired and used.” An individual’s privacy, as such, is always in an inherent state of tension, since it must be defined in conjunction with the capabilities of others to transact business and even to control their own privacy.
Privacy has four basic categories: information privacy, bodily privacy, communications privacy, and territorial privacy. Internet privacy is mostly information privacy, which means the ability of the individual to control information about one’s self. Invasions of privacy occur when individuals cannot maintain a substantial degree of control over their personal information and its use (Davies 1996).
In the last two decades, record access has received much attention from legislators and regulators. On the other hand, privacy protection laws have affected the accessibility and therefore the appraisal of records containing personally identifiable information. The privacy statutes have attempted to protect individual privacy by legislating what information may be collected, the circumstances under which it may be retained, and to whom the data may be released; and by prescribing remedies for violations and sanctions against violators (Barritt 1986).
According to above, the concept of (PII) had been defined as “any information about an individual maintained by an agency, including
- any information that can be used to distinguish or trace an individual‘s identity, such as name, social security number, date and place of birth, mother‘s maiden name, or biometric records; and
- any other information that is linked or linkable to an individual, such as medical, educational, financial, and employment information” (Gallagher 2010).
Access Control Needs
Access control approaches combine cryptographic protection and authorization access control to enforce access control via selective encryption, which implies the receiver can access and decrypt only the data they are authorized to access. Most of these approaches contain a structure called the user tree hierarchy, which represents the relationship between receiver and information items (Hue et al 2011). The challenge here is to satisfy the controller’s needs, depending on his rights, by giving him full control of access to his information, with a multi-level of permission such as the permission to view, download or print.
The Sender
The sender, who in this context comprises the academic institution charged with the responsibility of processing certifications, must put security concerns at the center of the whole exercise for the model to succeed. Security is defined as “…the protection of data against accidental or intentional disclosure to unauthorized persons, or unauthorized modifications or destruction” (Yazdanifard et al 2011). The sender concerns could be within some security attributes level or computer infections, conceptualized as follows.
Security Concerns
Security is the combination of processes, procedures, and systems used to ensure confidentiality, authentication, and integrity of data (Akhlaq et al 2006). The sender’s concerns are to make sure of the security of the information sent via the infrastructure by employing four security attributes, namely: confidentiality, authentication, integrity, and non-repudiation. In confidentiality, the sender must have the capacity to keep the information sent unreadable to unauthorized users, while in authentication, the sender must demonstrate the capacity to decipher the identity of the receiver to avoid identity fraud, which leads to loss of critical data to unauthorized users. The integrity component denotes the sender’s capacity to ensure that the information sent is not illegally altered or destroyed during transmission. Finally, non-repudiation entails putting in place mechanisms that will ensure the infrastructure will acknowledge that it indeed sent information or data to the receiver (Akhlaq et al 2006).
Infections and Intrusions
Computer infections, such as viruses and worms, spread over networks of contacts between computers, with different types of networks being exploited by different types of infections. The structure of contact networks affects the rate and extent of spreading computer infections (Balthrop et al 2004). The sender must bear concerns of being affected by any of these viruses and worms through his connection to other networks. Additionally, the sender must bear concerns for intrusion threat, which is defined as the potential possibility of a deliberate unauthorized attempt to access information, manipulate information, or render a system unreliable or unusable (Kumar 1995). The figure next page represents an illustration of the conceptualization of the problem from stakeholders’ perspectives.
Designing the Components of the Solution
In order to synthesize the solution, it is imperative to understand the critical components of the solution, described as follows.
The Internet and the Web
In common usage, the words ‘Internet’ and ‘Web’ are often used interchangeably. Although they are strongly related, there are some differences between them. The term ‘Internet’, in particular, is the more general term and implicitly includes physical aspects of the underlying networks as well as mechanisms such as email and peer-to-peer activities that are not directly associated with the Web. The term ‘Web’, on the other hand, is associated with the information stored and available on the Internet. It is also used to indicate other complex networks of information, such as webs of scientific citations, social relations, or even protein interactions (Baldi et al 2003). The Web has ushered an era of “anytime, anywhere, any place” communication. Widely accepted standards such as HTML use the Web to fully function (Aalst& Kumar 2003). Consequently, it is ideal to use the internet in designing the solution, particularly in availing a link between the different stakeholders, due to its availability, ease of accessibility, and low cost.
XML Exchange Language
The proposed solution is based on web service technology, which relies on XML for communicating the service request and response messages. XML is a data exchange technology, which has not only rapidly evolved into an international standard but has also permeated every sector of business – from aviation and accounting to weather and workflow. In technical terms, XML is a subset of SGML (Standard Generalized Markup Language), modified and optimized for delivery over the Web (Aalst & Kumar 2003).
By using structured data formats like XML the developers have the benefit to get great flexibility on the application because it has the capability to define the contents of documents through a set of elements or tags (Aalst& Kumar 2003). Additionally, XML provides a structured representation of data that can be implemented broadly and is easy to deploy. Evidence from the literature demonstrates that XML provides a data standard which can encode the content, semantics, and schemata for a wide variety of cases ranging from simple to complex, implying that it can be used to mark up a purchase order, an invoice, payment advice, a doctor’s prescription and information about people and organizations, among other functionalities (Aalst & Kumar 2003).
Overall, XML ensures that structured data will be uniform and understandable across a variety of applications, vendors, and customers. The resulting interoperability has provided the impetus for a new generation of business and electronic commerce Web applications to grow (Aalst& Kumar 2003). Consequently, with XML language, which gives us the ability to connect different applications with different data types, the solution will rely on its capacity to transfer massages among the different stakeholders.
Access Control
Identity Based Access Control (IBAC)
Under this model, permissions to access a resource are directly associated with a subject’s identifier (e.g., a user name). Access to the resource is only granted when such an association exists. An example of IBAC is the use of Access Control Lists (ACL), commonly found in operating systems and network security services. An ACL contains a list of users and their access rights such as read, write, or execute (Yuan & Tong 2005).
Role-Based Access Control (RBAC)
The RBAC model restricts access to a resource based on the business function or role the subject is performing. The permissions to access a resource are then assigned to the appropriate role or roles, rather than directly assigned to subject identifiers (Yuan & Tong 2005).
Lattice-Based Access Control (LBAC)
The LBAC model is manageable when there are a relatively small number of static security labels and categories (as the total combinations of labels and categories are potentially n*m), and therefore is only effective for certain coarsely-grained security scenarios and lacks flexibility and scalability (Yuan & Tong 2005).
In our solution, we think the most appropriate model to use is the Role Based Access Control (RBAC). With this access control model, the controller will be allowed to give permission to the appropriate role or roles to access the information.
Antivirus
An ‘antivirus’ can be described as a protective software primarily designed to protect computers and networks from malicious software, which include: viruses, Trojans, Keyloggers, hijackers, dialers, and other codes that vandalizes or steals the computer contents. Anyone who accesses other networks on a regular basis using the internet should develop and implement an antivirus strategy (Patil et al 2010).
Antivirus products are categorized into three major divisions: Internet Security [IS], Total Security [TS], and Antivirus [AV]. Antivirus products are primarily focused on detecting and remedying viruses and Spyware, while Internet Security products provide all the virus and Spyware removal features of an AV, as well as additional functions to provide greater internet protection. These features may include protection against phishing, rootkit detection, firewalls, and scanning of web pages and HTTP data. Total Security products provide data migration and backup features on top of all security features common to IS products (Patil et al 2010).
The most recent updated antivirus programs, that going to be used in the solution, will guarantee secure transaction of data among stakeholders.
Characteristics of the Solution
As noted by Hevner et al (2004), the solution to the problem will be characterized “…with respect to the artifact’s use (intention to use), perceived usefulness, and impact on individuals and organizations (net benefits) depending on the system, service, and information quality” (p. 77). Based on the above, it is in order to develop constructs and models that provide a unique problem-solving approach for developing an IT-oriented artifact that could allow all stakeholders to share information. A design framework for the Certifications Verification System would therefore entail the following key characteristics:
Components
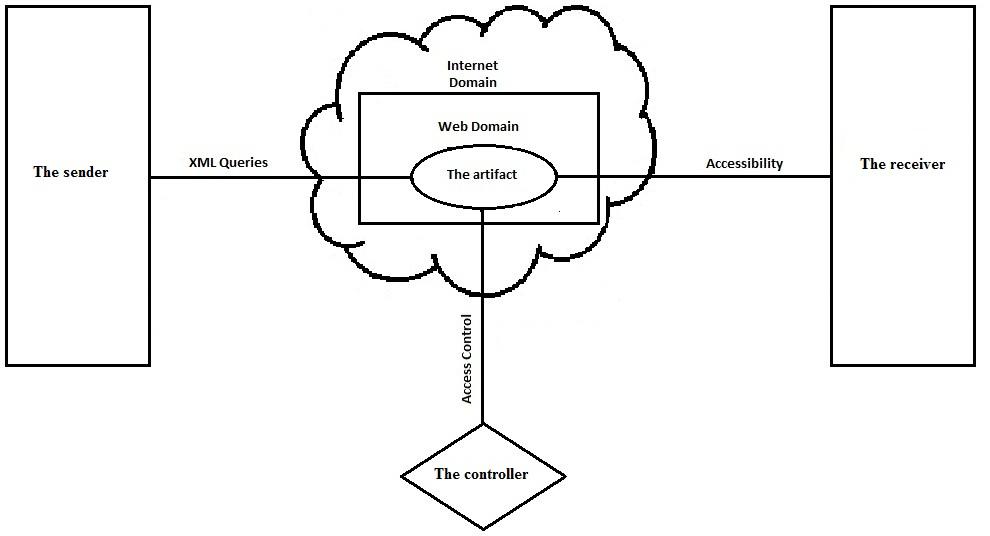
Components entail “…technological subunits that can be combined to form higher-level technologies” (Adomavicius et al 2008, p. 786). Here, we conceptualize the use of XML queries by the sender (institutions holding critical certifications information) using either synchronous or asynchronous techniques. The XML query will contain metadata fields for use by the controller, but will also be constructed in such a manner that it will allow for specific control attributes to be used.
Products
Products entail “…technologies that interact with the user in a given usage context” (Adomavicius et al 2008, p. 786). Here, we conceptualize the use of full access control by the controller, which inarguably allows them to provide access to the receiver (potential employers or institutions of learning).
Infrastructure
Infrastructure entails “…technologies that support and extend the use of product technologies” (Adomavicius et al 2008, p. 786). Here, we conceptualize the use of a website on the internet which provides the controller with a basic account. The controller can log into the website with the correct authorizations and access their certifications for downloading, printing, or sending to the receiver (potential employers or institutions of learning). The figure next page illustrates the proposed solution to this problem.
The Prototype
According to Ambler (2012), “…prototyping is an iterative analysis technique in which users are actively involved in the mocking-up of the UI [User Interface] for a system. This author further notes that prototypes serve several functions, which include
- analysis artifact – enables IT, professionals, to explore the problem space with other stakeholders,
- requirements artifact – enables the initial envisioning of the system, and
- design artifact – enables IT, experts, to explore the solution space of the proposed system.
The proposed prototype is design-oriented, implying that it will enable the developers to explore the solution space for the proposed IT artifact. This further implies that the proposed prototype will not only have the capacity to determine the artifact’s desired functionality and its architecture but will be instrumental in creating the actual artifact (Peffers et al 2008).
The prototype for the proposed solution will have three components, namely
- the controller component,
- the receiver component, and
- the sender component.
Each of these components is discussed in detail below.
The Controller Component
The Controller Registration Process
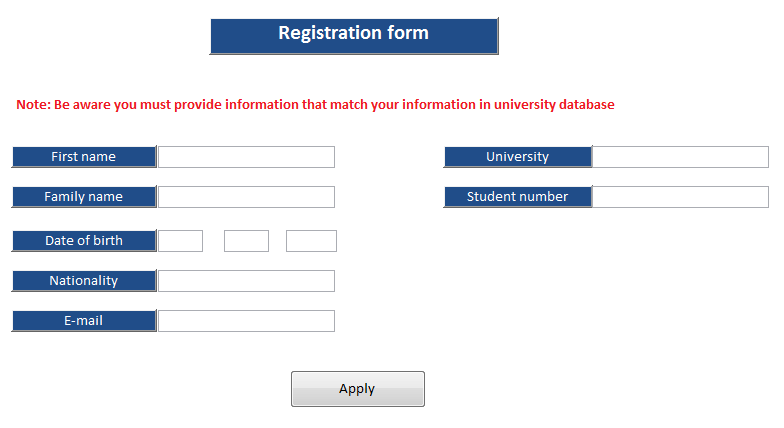
In order to use the artifact, the controller will have to register in order to get the subject identifiers (username and password). The registration process is made up of simple steps as elaborated in the figure next page, which illustrates the controller’s registration model. Considering that the artifact is web-based, the controller has to register through the proposed website.
This diagram represents the interface of the controller’s registration form. The form is designed to collect important information about the controller such as names, school ID, email address, and date of birth among others. This information is saved in the sender database and has to be matched by inputted data whenever someone wants to log in as a controller. This ensures that only the selected controller accesses the account, thereby guaranteeing accountability if the account is misused.
The second step is to verify the provided information with the sender database. If the provided data does not match with the sender data the registration process will terminate. If not the system will send an e-mail to the controller, including their user name and password.
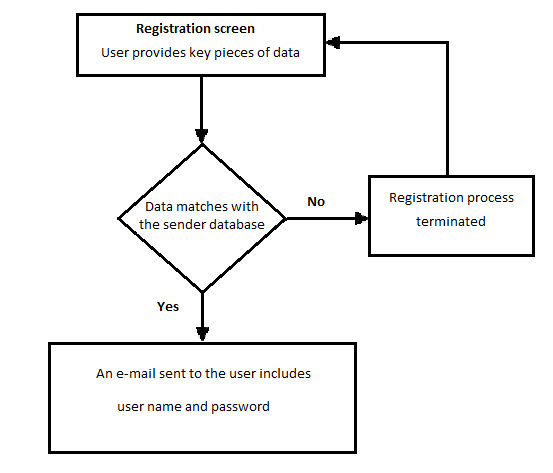
The purpose of using this method in the registration process is to implement the easiest way for the controller to create his account, rather than make them contact the university to apply for the account. We are assuming that only the controller knows this information, so, no one else can provide it but them. Moreover, we are assuming that the controller’s e-mail will be in the sender database, so no one will receive the user name and password except the real graduated person from the university.
The figure next page shows the interface of the controller registration form, and also demonstrates the key pieces of recommended information to create the controller account.
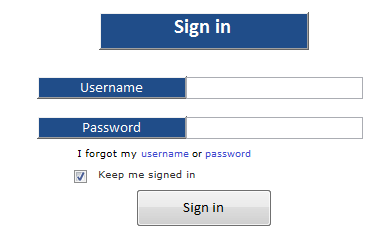
The Controller Sign-in Process
After the controller receives the registration e-mail which consists of their user name, password, and the link of the sign-in page, they can now enter the artifact web service, as shown in Figure 6
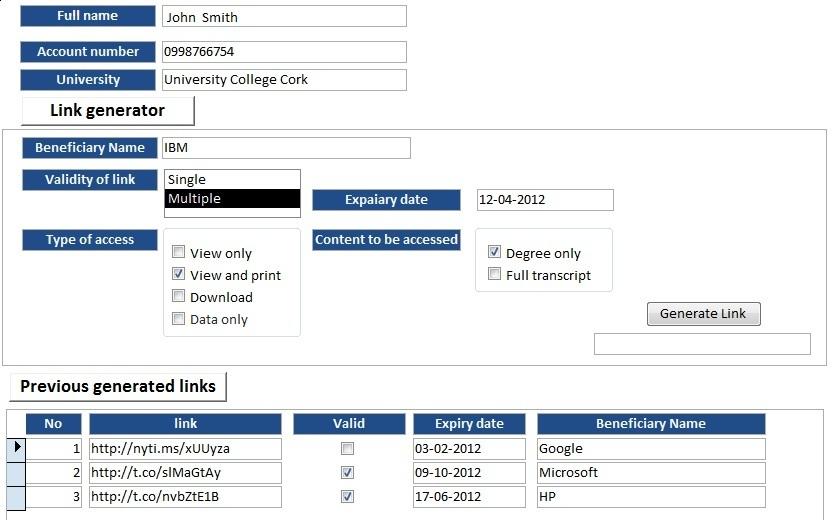
The Controller Interface Design
After the controller sign in successfully to the web artifact, he will be directed to the controller interface, which contains the elements that make him with full control generated from the web links to the receiver. These elements are outlined in the following table.
Once in the controller interface design web page, the controller starts with entering the receiver name and then chooses the validity of the link that they intend to generate (single or multiple accessed). If it is multiply accessed, they must enter the expiry date of the link. Next, the controller has to choose the type of receiver access view only, view and print, download or data only. Finally, the controller has to choose which type of content will be presented to the receiver – either degree only or full transcript. Additionally, the controller interface design consists of previously generated links, in order to allow them to modify their attributes from the same page. The following figure illustrates the controller interface design.
The Receiver Component
After the controller provides the generated link with his submitted application, the receiver can verify the certification via the internet by using the provided link. Figure (8) the next page shows the receiver interface in the scenario of view and print only. In this scenario, it can be seen that the receiver can access and print the certification, but they cannot download the certification copy. Also, in this scenario, it can be seen that the download button is disabled to meet the controller requirement. In the next Figure (9), the controller wants the receiver to access and view his full transcript, but without any printing or downloading as it shows the interface in the transcript view the only scenario.
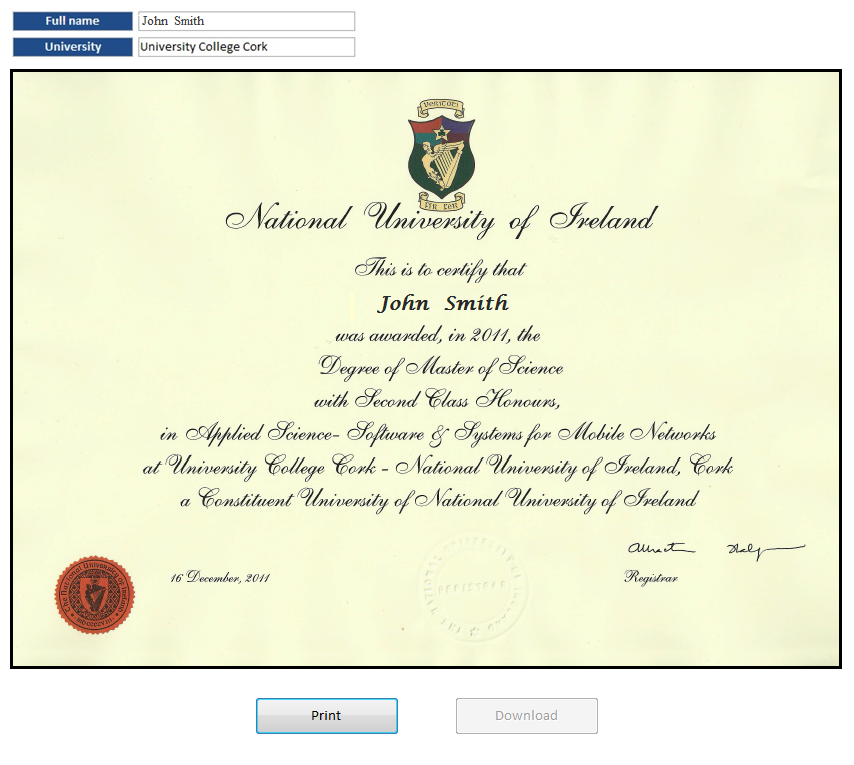
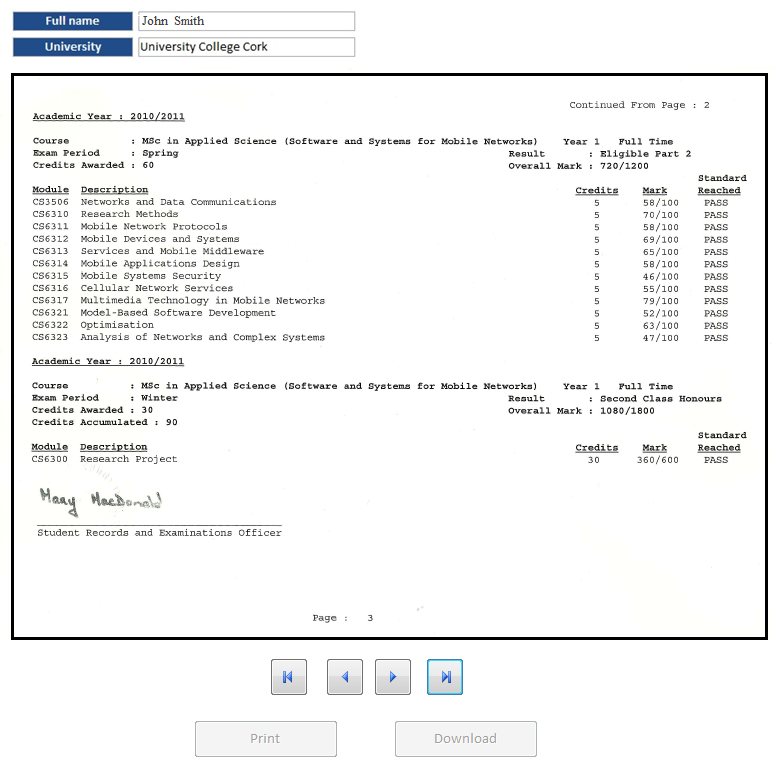
In the next scenario (Figure 10), the controller might want to restrict the verification to the “Data only scenario”. In this scenario, the receiver interface shows only data information about the controller status. Figure 8 shows the receiver interface in this scenario.
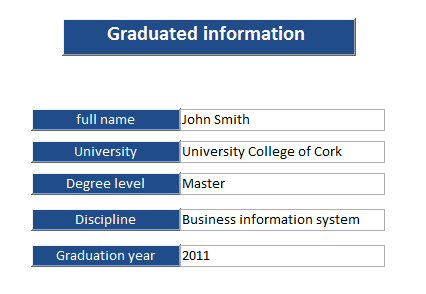
The Sender Component
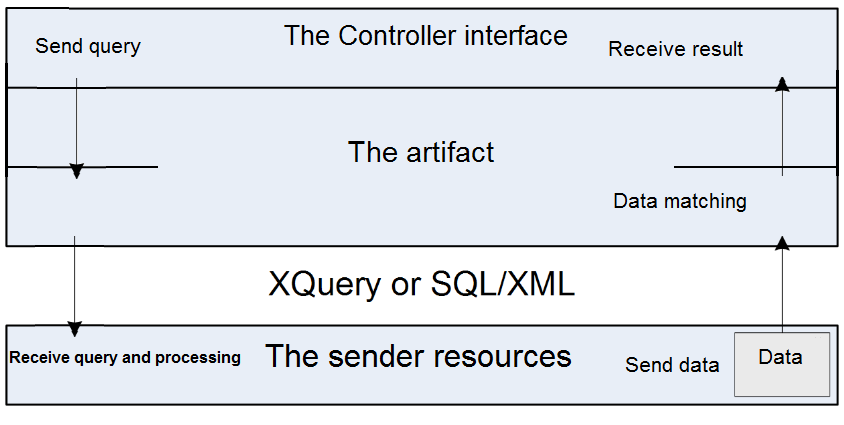
In the sender component, there are no interfaces at all as the connection with the artifact is only through XML queries via internet connection. The queries have two shapes: (1) the queries for match the date provided by the controller in registration level, and (2) the queries which may be demanded by the receiver in verification level.
Figure 11 illustrates a process model of the queries for registration purposes. In this scenario, the data of the controller goes through the artifact via an internet connection to the sender database after transforming it to XML language in order to verify key pieces of data that had been submitted by the controller. The sender processes the query by matching the received data with the sender database and sends the result back to the artifact. In this step, the artifact matches the received data with the sent data and sends the result to the controller interface. If the result matches the data that had been provided by the controller will receive an email containing a username and password. The registration process will terminate if there is a mismatch in data sent and received, or if no email is received by the controller.
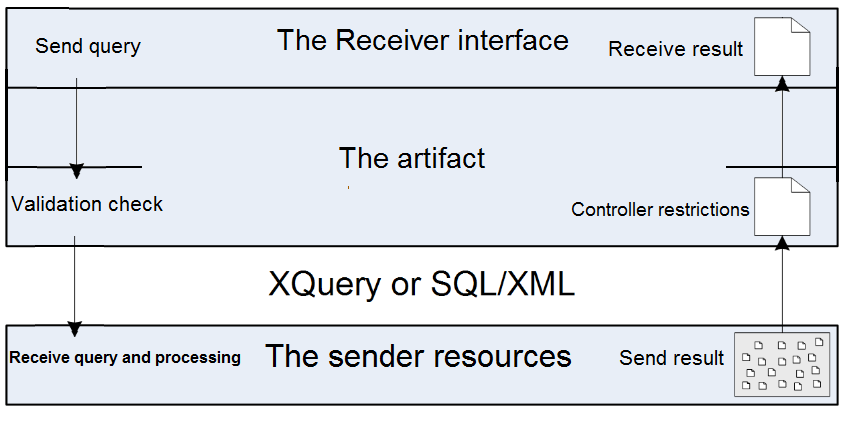
In the receiver query scenario, the process starts with sending a query by using the provided link from the controller. The artifact checks the validation of the query such as the expiry date and validity of use in order to filter the queries before sending it to the sender. If the validation check approves the legitimacy of the query, the artifact sends it to the sender after transforming it to XML language. If not the query process will end.
After receiving the validated query, the sender processes the query by searching the demanded data in the database and transforms it into XML language then sends the result to the artifact. The artifact, upon receiving the resultant data, applies the controller restrictions on these data in order to guarantee that the receiver will receive the information under controller restrictions. Finally, the artifact sends the restricted data to the receiver interface. Figure 12 illustrates a process model of the queries for verification purposes.
Evaluation
In this stage of design science, we must rigorously evaluate the utility, quality, and efficacy of the artifact via well-executed evaluation methods and test whether the prototype meets the requirements of the solution or not. In this phase, we must observe and measure how well the artifact supports the solution to the noted problem, implying that the artifact must be integrated with the technical infrastructure of the business environment to necessitate measurement (Peffers et al 2008). According to these authors, “…this activity involves comparing the objectives of a solution to actual observed results from use of the artifact in the demonstration” (p. 56). Here, the major objective of this exercise is the ongoing refinement of the artifact (Certifications Verification Program) as it is modeled and remodeled by the use context (Sein et al 2011), implying that evaluation should never be perceived as a separate phase that follows the development of the artifact. Table 2 illustrates the evaluation method which was created by Hevner et al (2004).
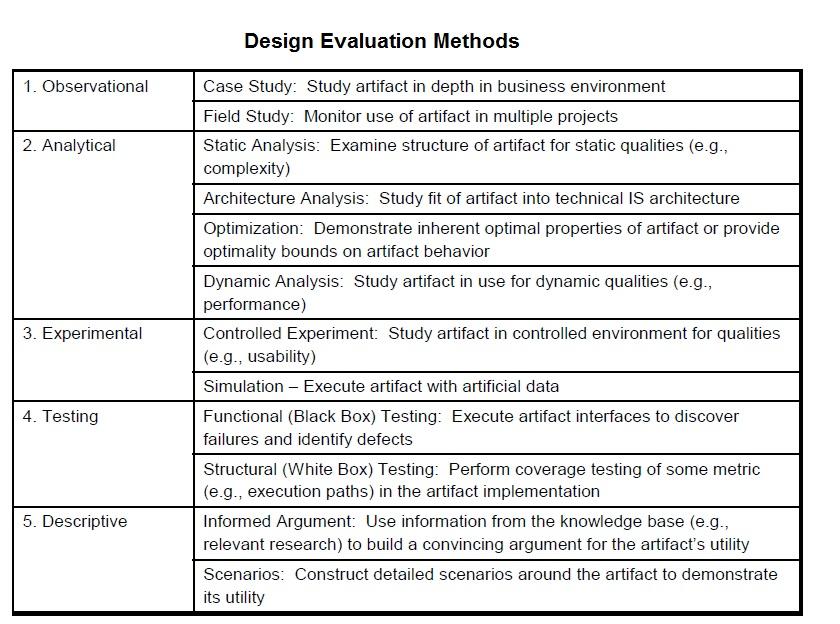
As acknowledged by Hevner et al (2004), one of the methods that could be used to evaluate an IT-oriented artifact is the descriptive method. The methodology utilizes two components in its evaluation, namely: informed argument and scenarios. In an informed argument, information from the knowledge base is used to develop a convincing argument for the artifact’s utility and quality, while the methodology of the scenario relies on constructing detailed scenarios around the artifact to reveal its utility as well as quality.
In this article, we are going to use the informed argument method to evaluate the artifact. The best way to evaluate this artifact, according to this method, is to see how the artifact meets the requirements of stakeholders and how the artifact utilities overcome their concerns. So, it is wise to evaluate the artifacts according to stakeholders’ concerns.
The Receiver Side
As discussed in this report, the receiver’s concerns focus on forgery and identity fraud. The artifact gives the receiver a reliable way to verify the certification via the internet. The permissions verifications processes integrated into the artifact will guarantee that there is no forgery on the certification aspect. Moving to identity fraud, with this solution the receiver would not accept the application without a certification link of the applicant. So, it is impossible to give a link to the receiver through fraudulent means because we assume the controller is managing their account. According to Mannan & van Oorschot (2011), these security features prevent unauthorized users from gaining entry into the website and easily collecting usernames and passwords by installing a Keylogger program or by embedding a JavaScript Keylogger with the intention to obtain information or change the stored information using fraudulent means. A protocol for online protection, according to these authors, will not only enhance transaction integrity but also effectively deal with instances of Keylogging, phishing, and pharming.
The Controller Side
The controller side focuses on privacy concerns and access control needs. With these requirements, the artifact guarantees by the pieces of data registration method that no one can provide the right information but him to create the account. Also, the login method requires a password and username to enter the account. On the access control aspect, the artifact gives the controller a wide range of controlling features. The artifact allows the controller to decide if he wants to let the receiver access data only, view, printing, or download which meets his access control requirements.
According to Ardagna et al (2008), these beneficial features enhance transparency in policies and privacy practices, individual control (users are able to specify who can gain access to what type of information about them and when), collection limitation (stakeholders collecting personal information for purposes of the transaction must gather no more data that what is stringently needed for undertaking the transaction, purpose specification (stakeholders who collect and disseminate personal data must specify the objective for which they need these data), and consent (users must have the capacity to provide their explicit and informed consent on how to use their personal information).
The sender side
The sender side focuses on security concerns and the concerns of viruses and intrusions. With these requirements, the artifact meets the sender’s confidentiality by ensuring that the information sent is unreadable to unauthorized users. In addition, the artifact ensures the identity of the receiver during the communication process, hence meeting the authentication requirement. Also, the artifact ensures to keep the data sent from being illegally altered or destroyed in the transmission by guaranteeing that no one can intercept the data transmission. Moreover, it ensures non-repudiation of data by giving feedback to the sender that the data has been received.
The other side of the sender’s concerns includes viruses and intrusions, which are indeed global concerns. However, the use of high standard and latest updated antivirus programs and firewalls by sender and artifact administration would guarantee the protection for the sender network from any viruses and intrusions attacks (Walter & Mernel 2010).
Conclusion
This article has comprehensively dealt with the design science issues related to unearthing a problem in organizational settings, enlisting the concerned stakeholders that are directly or indirectly affected by the problem, proposing a solution to the problem, building an IT-oriented artifact to effectively deal with the problem and, lastly, conducting an evaluation on the artifact to not only measure the utility, quality, and efficacy of the artifact but also to ensure that it has the capacity to meet the requirements and demands of all stakeholders.
Through utilizing the stakeholder perspective, involving the sender, receiver, and controller, all the challenges involved in relying on paper-based certifications have been exposed, and constructs and models put in place to build an electronic web-based Certifications Verification Program to deal with the predominant challenges of certifications fraud and identity theft. Through the employment of various security levels, authentications, and user and content access control mechanisms, the report has demonstrated how the Certifications Verification Program could be beneficial to all stakeholders, particularly with regard to ensuring transparency and accountability in policies and privacy practices, ensuring the quality of data, enhancing data collection limitation, guaranteeing purpose specification, and safeguarding the consent of users.
Reference List
Aalst, V & Kumar, A 2003, ‘XML-based schema definition for support of interorganizational workflow’, Information Systems Research, vol. 14 no. 1, pp. 23-46.
Adomavicius, G, Bockstedt, J.C, Gupta, A & Kauffman, R.J 2008, ‘Making sense of technology trends in the information landscape: A design science approach’, MIS Quarterly, vol. 32 no. 4, pp. 779-809.
Akhlaq M et al 2006, ‘Addressing security concerns of data exchange in AODV’, Transactions on Engineering, Computing and Technology, pp. 29-33.
Ambler, S.W 2009, User interface prototypes. Web.
Ardagna, C.A, Cremonini, M, di Vimercati, C & Samarati, P 2008. ‘A privacy-aware access control system’, Journal of Computer Security, vol. 16 no. 4, pp. 369-397.
Baldi, P et al 2003, Modeling the internet and the web: Probabilistic methods and algorithms, John Wiley & Sons, Ltd.
Balthrop J et al 2004, ‘Technological networks and the spread of computer viruses,’ Science, vol. 304, pp. 527–529.
Barritt, M 1986, ‘The appraisal of personally identifiable student records’, The American Archivist, vol. 49, no. 3, pp. 263-275.
Culnan, M.J 2000, ‘Protecting Privacy Online: Is Self-Regulation Working?’, Journal of Public Policy and Marketing, vol. 19 no.1, pp. 20-26.
Davies, S 1996, Big Brother: Britain’s web of surveillance and the new technological order, London, p. 23.
Gallagher, P 2010, Guide to Protecting the Confidentiality of Personally Identifiable Information (PII), National Institute of Standards and Technology, Special Publication 800-122.
Germonprez, M, Hovorka, D & Gal, U 2011, ‘Secondary design: A case of behavioral design science research’, Journal of the Association for Information Systems, vol. 12 no. 10, pp. 662-683.
Goranson v. State 1965, The Supreme Court of Washington, 67 Wn.2d 456.
Gorard, S 2010, ‘Serious doubts about school effectiveness’, British Educational Research Journal, vol. 36 no. 5, pp. 745-766.
Hevner, A.R, March, S.T, Park, J & Ram, S 2004, ‘Design science in information systems research’, MIS Quarterly, vol. 28 no. 1, pp. 75-105.
Hue T et al 2011, ‘An Experimental Evaluation for a New Column – Level Access Control Mechanism for Electronic Health Record Systems’, International Journal of U- & E-Service, Science & Technology, vol. 4 no 3, pp. 73-86.
Koops, Bert-Jaap and Leenes, Ronald 2006, ‘Identity Theft, Identity Fraud and/or Identity related Crime’, Datenschutz und Datensicherheit, vol. 30 no 9.
Kumar S 1995, Classification and Detection of Computer Intrusions, Ph.D. thesis, Purdue University, West Lafayette, IN 47907, 1995.
Malawi, C.A, & Rakovski, C 2009, ‘Behavioral Implications of Evaluating Determinants of Academic Fraud Risk Factors’, Journal of Forensic & Investigative Accounting, vol. 1, no. 2.
Mannan, M & van Oorschot, P.C 2011, ‘Leveraging personal devices for stronger password authentication from untrusted computers’, Journal of Computer Society, vol. 19 no. 2, pp 703-750.
March, S.T & Storey, V.C 2008, ‘Design science in the information systems discipline: An introduction to the special issue on design science research’, MIS Quarterly, vol. 32 no. 4, pp. 725-730.
Murthy, S.G. K 2011, Elliptic Curve based Signature Method to Control Fake Paper based Certificates, Proceedings of the World Congress on Engineering and Computer Science Vol. I WCECS.
Patil,b et al 2010, ‘A Comparative Study for Performance Measurement of Selected Security Tools’, International Journal of Engineering Science and Technology, vol. 2 no. 10, pp. 5130-5136.
Peffers, K, Tuunanen, T, Rothenberger, M.A & Chatterjee, S 2008, A design science research methodology for information systems research’, Journal of Management Information Systems, vol. 24 no. 3, pp. 45-77.
Purao, S, Baldwin, C, Hevner, A, Storey, V.C, Pries-Heje, J, Smith, B & Zhu, Y 2008, ‘The sciences of design: Observations on an emerging field’, Communications of the Association for Information Systems, vol. 23 no. 29, pp. 523-546.
Rye, S.A 2009, ‘Negotiating the symbolic power of information and communication technologies (ICT): The spread of internet-supported distance education’, Information Technology for Development, vol. 15 no. 1, pp. 17-31.
Sein, M.K, Henfrindsson, O, Purao, S, Rossi, M & Lindgren, R 2011, ‘Action design research’, MIS Quarterly, vol. 35 no. 1, pp. 37-56.
Shields, R 2011, ‘ICT or I see tea? Modernity, technology and education in Nepal’, Globalisation, Societies and Education, vol. 9 no. 1, pp. 85-97.
U.S. Department of Justice n.d., Identity theft and identity fraud. Web.
Walter, C & Mernel C, 2010, ‘An approach to capture authorization requirements in business processes’, Requirements Engineering, vol. 15 no. 4, pp. 359-373.
Yazdanifard, Rashad et al 2011, Security and Privacy Issues as a Potential Risk for Further E-commerce Development, International Conference on Information Communication and Management. Singapore.
Yuan, E & Tong, J 2005, Attributed Based Access Control (ABAC) for Web Services. ICWS.