Understanding the operation of networks at a basic level is essential for any server administrator or webmaster. It is necessary for configuring all the services on the network properly, detecting possible problems properly, and troubleshooting. Today, in the conditions of multiple annual increases in information flows, it is almost impossible to imagine the clear interaction of business firms, banking structures, state enterprises, and other organizations without the modern means of communications. On the one hand, networks are a special case of distributed computing systems in which a group of computers performs a set of interrelated tasks consistently, exchanging data in an automatic mode. On the other hand, computer networks can be regarded as a means of transmitting information over long distances by using the methods of encoding and multiplexing data, which have been developed in various telecommunication systems. A variety of concepts and protocols requires the detailed study of the peculiarities of these channels, and visual schemes may be useful. Thus, the forms of multiplexing access to channels and resources have become an integral part of modern life, and their different features are the subject of this study.
Research Findings
Fundamental Networking Concepts, Components, and Functionality
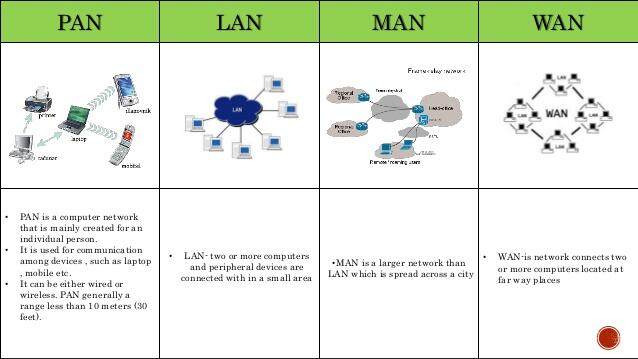
Any network is a connection between two or more computers that allows them to share resources. Depending on the size of the geographical area that they cover, they are divided into several main types. All of these networks are actively used today within different terrains, and their differences are significant. The following types should be mentioned: local (LAN), metropolitan (MAN), wide (WAN), and personal (PAN).
Local networks (LAN) connect computers within a small physical space, for instance, one or more nearby buildings. They serve users located at a distance of tens and hundreds of meters from one another, and the number, as a rule, does not exceed several thousand people (Ellingwood, 2014). Metropolitan networks (MAN) utilize global technologies to unify LAN in a particular region, for example, in a city. They have much in common with the previous system, such as high transmission speed and low error rate in the communication channel (Ellingwood, 2014). Nevertheless, they should have the ability to transmit a wider range of information. Wide networks (WAN) cover the whole globe, and for this purpose, additional means of communication are used – satellites, antennas, and other devices. Finally, personal systems (PAN) are designed for individual use and are utilized in a small location. In the figure, it is possible to see the aforementioned types of networks (“Computer networking concepts,” 2018).
Role of Each OSI Layer and the Role of Each TCP/IP Network Model
Each level of the OSI model performs a specific task in the process of transferring data over the network. The figure gives a brief description of all the existing levels (“Compare and contrast OSI and TCP/IP models,” 2018). Physical provides bit protocols for information transfer, the channel controls access to the environment, and the network is engaged in routing and converting network addresses into physical addresses. The transpose layer manages the transfer of data, the session layer supports the interaction between processes, the representative converts the data to a common format, and the application layer allows access to network services.
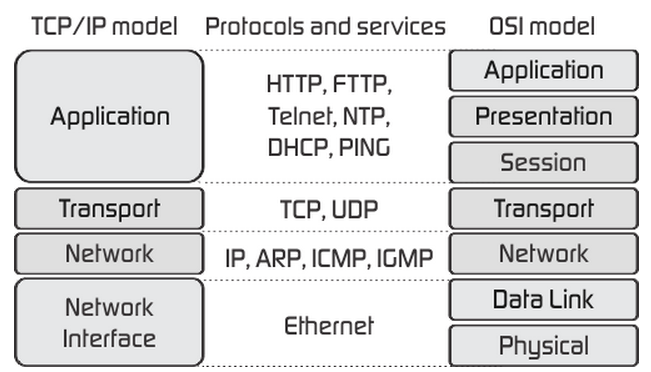
TCP/IP is a set of network protocols on which the Internet is based. Since such a system does not provide a unified data transfer protocol, functions for determining the data type are transferred to the application. According to Ellingwood (2014), unlike the OSI reference model, TCP/IP is more focused on providing network interactions than on a rigid separation of functional levels. For this purpose, it recognizes the importance of the hierarchical structure of functions but provides sufficient protocol flexibility for protocol designers.
Addressing and Naming Schemes
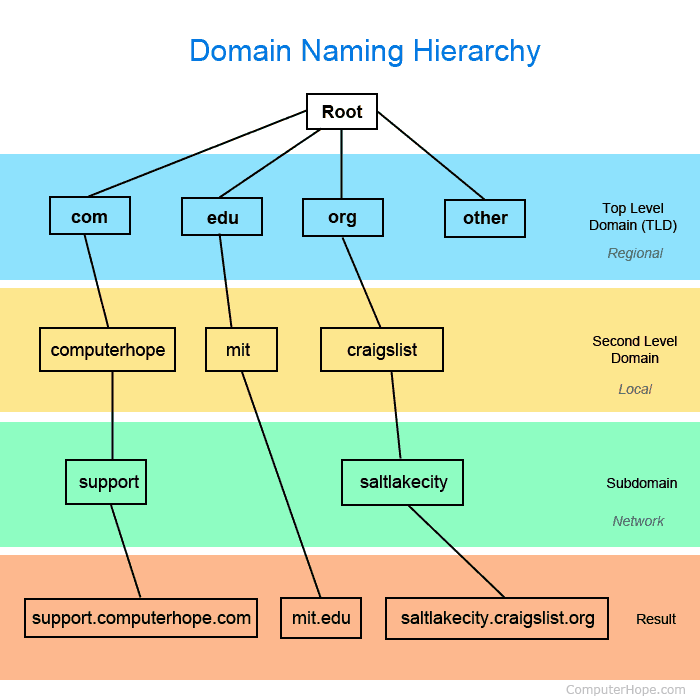
Each network node should have a name and address, and if the number of computers is hundreds or thousands, choosing a good scheme for assigning these parameters is of great importance. As Ellingwood (2014) notes, correct data will help to avoid troubles when deleting, adding, or moving hosts and routers. On the Internet, a successful delegation strategy has been chosen, which allows assigning names and addresses to those who are responsible for the operation of all or part of an individual network. Also, with the help of this information, the logical structure of any organization can be reflected.
As an example of the method of addressing and naming, a hierarchical structure may be considered. Each organization has a high-level content name, and the naming scheme is chosen independently, as seen in the figure (“Domain naming hierarchy,” 2018). Moreover, the use of a hierarchical structure simplifies the verification of the computer name’s uniqueness since it is assigned to appropriate personnel. To ensure the worldwide uniqueness of the Internet names, a registration service is needed to control that each company and organization has a unique (different from others) address.
Devices and Media Necessary for Network Communications
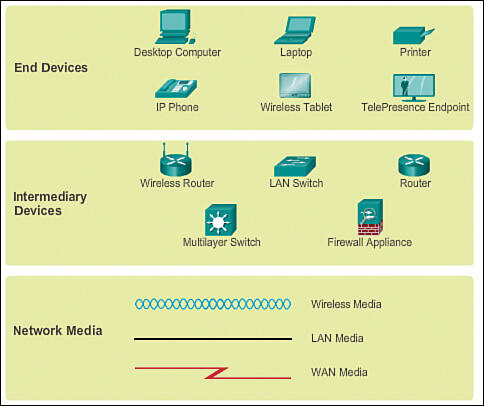
Network devices that are familiar to a large circle of users are called end ones. In the context of technological structure, end devices are called hosts (Han, Gopalakrishnan, Ji, & Lee, 2015). Such elements are either a source or receiver of a message transmitted over the network. To distinguish one host from another, each one is to be identified by an address. When a host initiates communication, it uses the destination host address to indicate where the message should be sent.
In addition to end devices that people are familiar with, networks also depend on intermediary systems that provide connectivity to the data stream. These objects connect individual hosts and can connect several networks, forming a separate complex, as shown in the figure (“LANs, WANs, and the Internet,” 2018). Examples of such devices are wireless access points, routers, firewalls, LAN and multilayer switches, and other components.
Basic Network Structure and the Flow of Communications
The basis of the network architecture is the multilevel principle of message transmission. The message is generated at the highest level of the OSI model. During transmission, it passes through all the levels of the system to the lowest one, as is shown in the figure (“Layers of OSI model,” n.d.). As each level of the system passes, the message is transformed into relatively short parts that are supplemented with additional headers that provide information to similar levels on the destination node. In this node, the message passes from the lower level to the upper one, taking off its headers. As a result, the recipient receives a particular file in its original form.
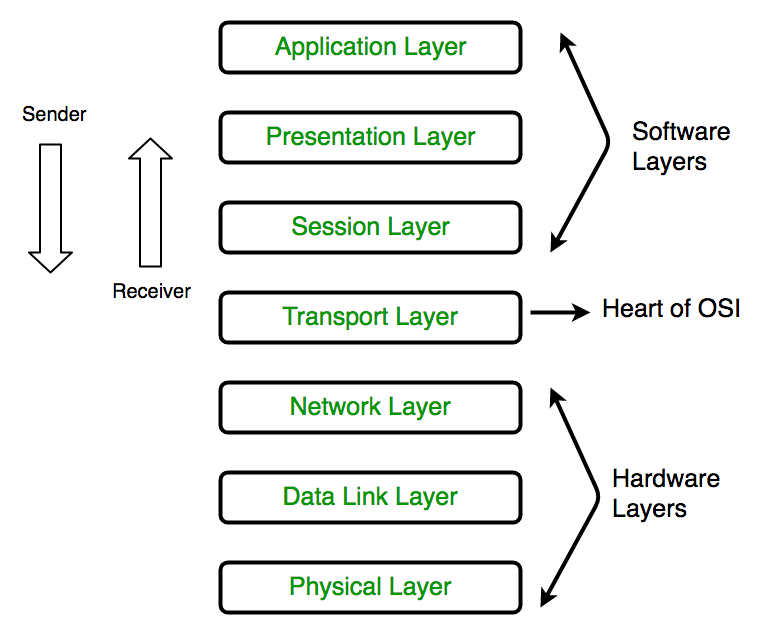
In metropolitan networks, data exchange is controlled by the top-level protocols of the OSI model. Each of them has the means to identify any network workstation by name, network address, or both. The activation of information exchange among interacting nodes begins after the node of the destination is identified by the one initiating the data exchange. The protocol provides opportunities for receiving or sending messages by the recipient and the source. In this case, restrictions are usually imposed on the length of files.
Commonly Used Network Analysis Tools
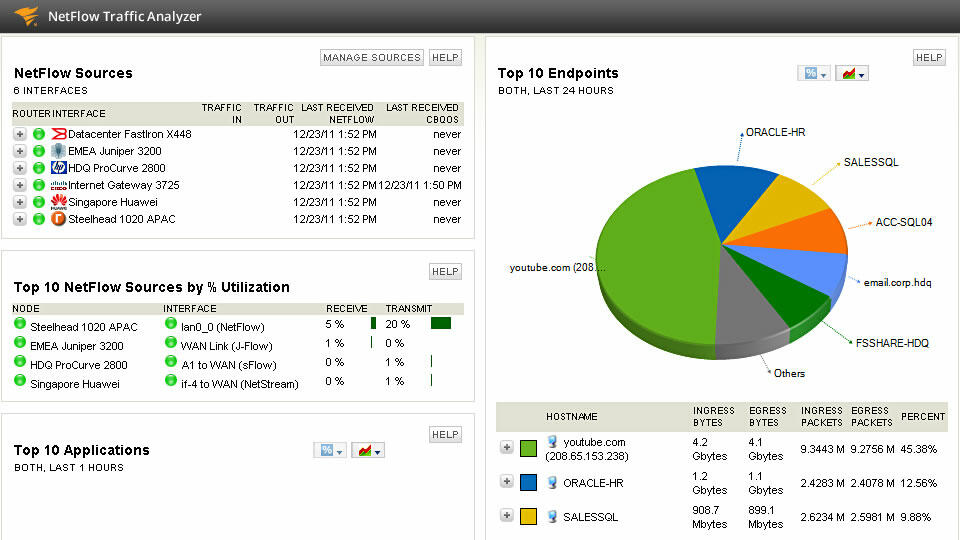
Network management systems are centralized software platforms that collect data on the status of nodes and network communication devices, as well as data on circulating traffic. These systems not only monitor and analyze but also perform control actions in automatic or semi-automatic mode. They can enable and disable device ports, change the parameters of address tables of bridges, switches, and routers, and perform other important procedures. The figure shows the appearance of the NetFlow Traffic Analyzer program where all running processes are displayed, and the traffic consumption is indicated (“Network analyzer,” 2018).
Methods for analyzing networks may be based not only on the work of popular online platforms. Cranmer, Leifeld, McClurg, and Rolfe (2017) argue that “many network analysis techniques are descriptive in nature” and propose their quadratic assignment procedure (p. 239). Its essence lies in the fact that it is not connected with statistical reports and “provides an unbiased test of association in spite of potential dependencies” (Cranmer et al., 2017, p. 239). This method of analysis is not the only one, but it may be used as a mechanism for monitoring network utilization.
Role of Cisco’s IOS, Commands, and the Classes of Devices
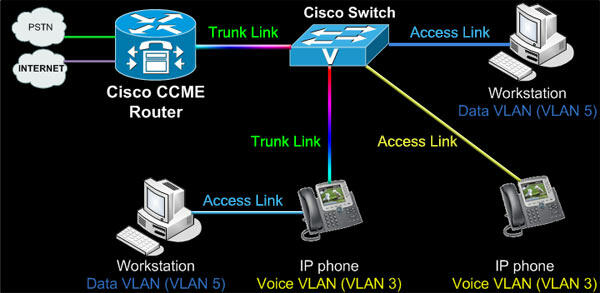
Devices running on Cisco IOS support many commands, and each of them has a specific format or syntax and can be executed in an appropriate mode. The general syntax is a command followed by any suitable keywords and arguments. Some commands include a subset of keywords and arguments that provide additional functionality. Commands are used to act, and keywords are utilized for identification. The Cisco Multifunctional Security Appliance software is the basic operating system that is introduced in all the devices of this network family. It integrates with other essential security technologies, which makes it possible to create multifunctional solutions that meet constantly changing requirements for protection against threats. The classes of protection devices can be low, medium, and high, and the latter ones are certainly the most advanced (Cranmer et al., 2017). The figure shows the role of such a network’s model and the examples of its use (“The role of CME in Cisco unified communications,” 2015).
Network Topologies, Standards, and Protocols
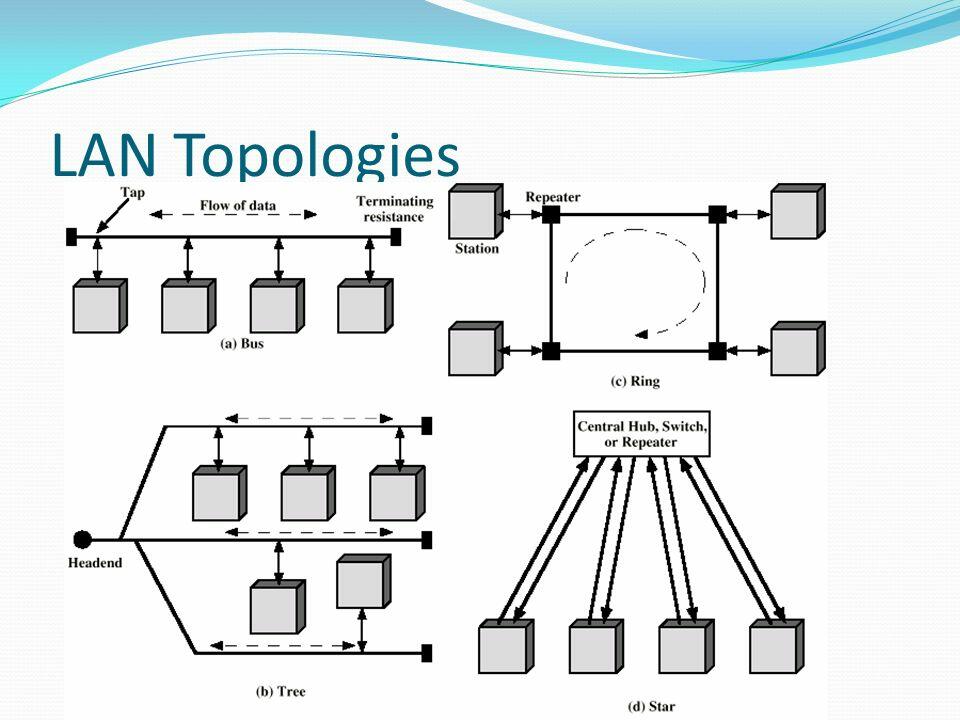
All the computers in the local network are connected by communication lines, and their geometric location relative to the nodes of the network, taking into account their physical connection, is called the physical topology. Depending on this parameter, the networks of bus, ring, star, hierarchical, and arbitrary structure are distinguished. The figure shows the examples of contacts in these topologies in local networks (“Local area network topology,” 2018).
As Ellingwood (2014) notes, “a protocol is a set of rules and standards that basically define a language that devices can use to communicate” (para. 14). For instance, the set of TCP/IP protocols is an open standard protocol approved in the field of network technologies, as well as by the standardization organization. The use of such data allows individuals, companies, and trade associations to analyze current networks and plan further work based on the ongoing monitoring of standards and protocols.
References
Compare and contrast OSI and TCP/IP models [Image]. (2018).
Computer networking concepts [Image]. (2018).
Cranmer, S. J., Leifeld, P., McClurg, S. D., & Rolfe, M. (2017). Navigating the range of statistical tools for inferential network analysis. American Journal of Political Science, 61(1), 237-251. Web.
Domain naming hierarchy [Image]. (2018). Web.
Ellingwood, J. (2014). An introduction to networking terminology, interfaces, and protocols. DigitalOcean.
Han, B., Gopalakrishnan, V., Ji, L., & Lee, S. (2015). Network function virtualization: Challenges and opportunities for innovations. IEEE Communications Magazine, 53(2), 90-97. Web.
LANs, WANs, and the Internet [Image]. (2013).
Layers of OSI model [Image]. (n.d.).
Local area network topology [Image]. (2018).
Network analyzer [Image]. (2018).
The role of CME in Cisco unified communications [Image]. (2015). Web.