Introduction
We are specialized in mobile development, web development, network design and engineering, and cybersecurity. Smart Link Networking Agencies have built our reputation from quality products and services in the last decade. Our prices, products, and services are extremely competitive, thanks to our extensive investment in research and design.
Computer networks facilitate communication between different digital devices through messaging, mail services, file and resource sharing, education, commerce, voice calls, video, teleconferencing, and databases. There are two main types of computer networks: client-server architecture and peer-to-peer architecture. The type of network adopted depends on the organizational needs such as services provided, the number of users, available technology, and any existing plans to expand or change the organization. A powerful computer called a server provides essential services to all other client computers in a client-server architecture, also called nodes. The clients sent requests to the server. The server processes the requests and sends responses to the respective clients.
Network design is the planning phase of computer networks. Professionals carry it out with respect to company (client) needs. This phase is carried out before the actual network is implemented. In this phase, the professional assesses the client’s needs and determines what networking equipment, hardware, operating systems, and application software are best suited for that particular network.
Office Layout
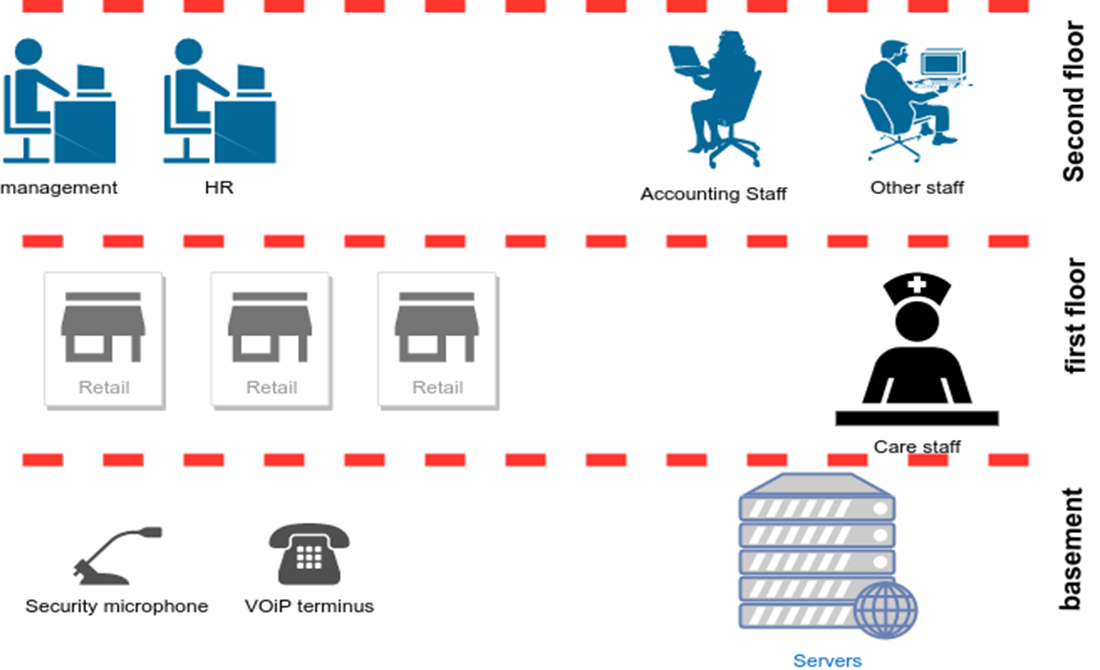
The Company building is comprised of three floors, as shown in the figure to the right.
The basement contains the warehouse. Based on the company proposition, the basement will not contain any computers except Voice over IP terminus phones. The first floor houses the retail section. This is where customers purchase and pick their products and services of choice. The second floor, which is the highest of all floors, houses the company departments: Management, Human resources, Marketing, Security, and Accounting. The proposed network is a hybrid collection of ring topologies
Each floor runs on its ring network. The network design for each floor is in line with the company requirements, and the respective activities carried out there.
Overview of the Network Design
Broadband routers are essential equipment in connecting networks to the internet. Usually, routers are the most common networking equipment used to connect local networks to the internet. Routers are also fast and essential for packet filtering and network rerouting.
Since the internet has become a playground for the bad guys, the network must be secured with a firewall besides any other security measures and applications recommended later in this presentation. Firewalls are an essential security apparatus in any computer network. They prevent virus attacks, promote privacy, monitor network traffic, inhibit hacker activities, and stop spyware from attacking the network computers and other resources. Firewalls come in two main types: hardware and software. In our case, we recommend both types of firewalls to provide an extra layer of security.
The three networks located on each office building floor are connected through a router that facilitates communication and resource sharing between computers in the different networks. The networks on different floors are linked by a router which facilitates communication and resource sharing between computers in the different networks. The router achieves this by forwarding the data frames and packets based on its routing table contents.
The topologies and sizes of the networks on the different floors differ depending on the purpose of the networking components and the number of target users. The basement and retail section networks are smaller and simpler than the second-floor network, which comprises many complicated networks for different departments.
Network Design Structure
The proposed network is a hybrid collection of ring topologies:
- Each floor runs on its own ring network
- The network design for each floor is in line with the company requirements and the respective activities carried out there.
- The basement and retail sections of the building have the simplest of all network configurations in the entire network
- The network is designed on the TCP/IP protocol
Network Equipment and Brands
- 2 Cisco 837 Secure Broadband routers
- 1 Cisco Wi-Fi Router 802.11ac
- ASA5545-K9 Cisco Asa 5545 X hardware firewall
- 3 Cisco SF350-24P switch
- 5 CISCO SWITCH Catalyst 3560-X Series
- 250 meters of CAT5 cable.
- 50 meters of fiber optic cable
1 broadband router will be required to connect the company network to the internet
A second broadband router will be required to connect all networks on the three floors.
1 piece of firewall hardware will be required to protect the company network
Every computer running on the network will be required to have firewall software installed.
The network nodes and devices in all networks will be connected through an intelligent switch
250 meters of CAT5 networking cables will be used to connect computers, printers, scanners, and telephones to the computer network. An optic fiber cable will be used to connect the network backbone, that is, the networks on different floors will be connected through fiber optic cables.
The local networks used by different departments will be connected through a workgroup switch.
The product description is provided in the current slide.
Network Server Technologies
- Dell PowerEdge T320
- Ubuntu Server Operating System
- Apache James Mail Server
- Oracle database server
- TL-WPS510U Wireless Print server
- Cisco network operating system
- Cisco 7811 SIP VoIP Phone
Dell PowerEdge T320 is a powerful server capable of handling up to 50 concurrent users. The device is not tied to any software technology and can accommodate any operating software and server-side services.
Ubuntu operating system is one of the most robust and secure server-side operating systems currently available in the market. It is built on the UNIX shell and is best known for its efficiency in resource allocation, security, and networking capabilities. Like any other Linux distribution, the OS is built to incorporate security, networking, and performance.
Apache James mail server is an open-source mail server available online. It is one of the best options available in the current technological era.
Oracle owns one of the most scalable and robust client and server relational databases today. Although the server is resource-intensive, the choice of the server computer is powerful enough to accommodate the oracle server alongside other applications.
The TL-WPS510U print server will be used to facilitate print servers for computers connected over the network.
Client-Side Technologies
- Operating systems
- Windows, Linux, Mac OS
- File browsers
- Web browsers
- Chrome, Firefox, Internet Explorer,Opera,MS Edge
- Mail client
- Network Interface Card and device drivers
- CISCO ASA firewall software
Manufacturers of networking equipment work under international standards, and hence, devices from different manufacturers can work together without causing any technical hitches. This phenomenon is called interoperability. As a result, any desktop operating software can be used in the network. The same case applies to the laptops used by the management staff.
However, the company should settle for one platform to reduce the cost of training new staff or acquiring new technologies.
Different OS distributions come with inbuilt file explore applications. The Ubuntu Server OS provides a simple mechanism to store and retrieve files from the file server.
There are several web browsers available for all platforms. Some of these browsers are also available for all desktop OS distributions; for example, Google Chrome, Firefox, and Opera are available for Windows, Linus, and Mac OS.
Web browsers can also be used as mail clients.
Modern computers are shipped with an inbuilt NIC. the devices also come with the right device drivers for internet connection.
CISCO ASA firewall is the most popular firewall which protects all devices connected to a particular network.
Network Security and Capability
- Antivirus Software
- All computers should have antivirus software installed.
- Intrusion Detection Systems
- IDS monitor can detect security breaches and thwarts security attacks.
- Firewalls
- Firewalls are an essential tool in protecting a computer network.
- Bring Your Own Device (BYOD) policy.
- To limit the threats brought forth by external devices, the company should white list company devices to block other devices on the company network.
Antivirus software protects computer systems against known security threats. updating antivirus software ensures computer systems benefit from security patches and updated security patches. IDS runs alongside network systems and is not resource-intensive. It works by monitoring users for unusual behavior or activities and prevents them from accessing resources should their actions be suspicious. A firewall blocks all unwanted traffic and protects networks from attacks. BYOD policy is common in most organizations. However, it should not be allowed here as it helps hackers attack networks with ease. To limit the threats brought forth by external devices, the company should white list company devices to block other devices on the company network
Key points
The network design leaves room for expansion in the future. Security is a key concern and will be embraced through firewalls and other security software. Antivirus software and firewalls should be updated regularly to fix bugs in current software versions. The network is designed to ensure high levels of performance and availability.
Reference
Radosavovic, I., Kosaraju, R. P., Girshick, R., He, K., & Dollár, P. (2020). Designing network design spaces. In Proceedings of the IEEE/CVF Conference on Computer Vision and Pattern Recognition (pp. 10428-10436).