In today’s Internet environment, where not only free access to materials is central but also ensures data privacy, it is essential to look for ways to protect corporate protocols and servers. This rule is particularly relevant for companies in the healthcare sector, where patient data must be securely encrypted, as postulated by GLBA: 501b (“What is GLBA Compliance,” 2020). Few companies, wanting to protect their clients or patients’ PIIs and comply with HIPPA regulations, choose to build PKI systems (“Healthcare solution,” 2019). In practice, the opposite is true: medical organizations’ software is rarely securely encrypted, either virtually or physically, which increases the likelihood of cybercrime. Thus, a hacker who hacked QMS will be able not only to access the data stored on the servers but also to exploit them. In this case, the company risks incurring reputation and financial losses, which justify the need to develop a robust protection architecture.
Such a decision is the public key infrastructure (PKI), directed on maintenance of authentication of users and resources, along with an increase of integrity of the system. It should be noted that the principle of operation of the PKI is based on the relationship between two types of keys: public and private. The Certification Authority (CA) issues a public key to the user, which postulates that the key is complementary to the private key, which is the only option available to the owner. This means that data that has been encrypted with the public key cannot be decrypted with the same key: an appropriate private key is required. Given that the two main algorithms for protecting data in such a system were asymmetric encryption and electronic digital signature, care had to be taken to ensure that the PKI developed could meet those criteria.
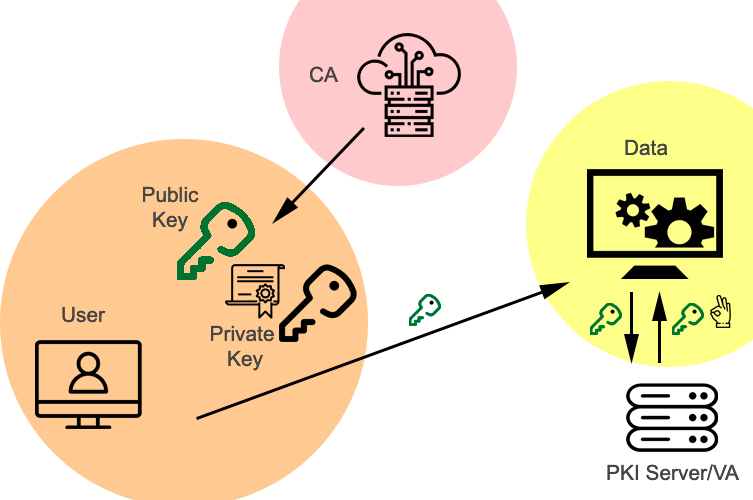
It is necessary to admit that in case QMS decides to introduce technologies PKI, heads of the company should realize the duration of construction of such complicated architecture. In particular, a workable PKI requires time to design a data center on a scalable basis, determine sufficient e-certificate formats for compliance, implement certification policies, including a code of ethics among employees, and finally, install software on each computer in the company. The information that the company will manage also includes sensitive financial data, both on the move and at rest, so it is necessary to implement control executions as prescribed by SOX: 404 (“What is Sarbanes-Oxley act,” 2020). In other words, the PKI development plan is not characterized by simplicity of implementation and speed of execution: on the contrary, it is necessary that all components of the architecture and compliance requirements are adequately fulfilled.
It should be noted that methodically the process of creating a PKI system includes a sequence of steps, each of which is accompanied by appropriate documentation and verification of performance criteria. In the initial phase, the requirements that the company needs to meet are analyzed. Such requirements traditionally include investigation of objectives, sufficient security levels, and consideration of potential risks. Immediately after, there is an abstract design of the architecture, which determines what exactly will represent the network. Including, at this stage, the necessary rules of differentiation of access to the corporate documentation, for example, through MAC are entered. The designed network is audited to determine possible vulnerabilities and weaknesses. If the audit does not identify any problems, the system is sent for implementation in the corporate practice with round-the-clock quality control. In other words, even after time, the PKI may show unsatisfactory results, so constant system reviews and modifications are required.
References
Healthcare solution. (2019). StrongKey. Web.
What is GLBA Compliance? (2020). Thales. Web.
What is Sarbanes-Oxley (SOX) act data-at-rest security compliance? (2020). Thales. Web.