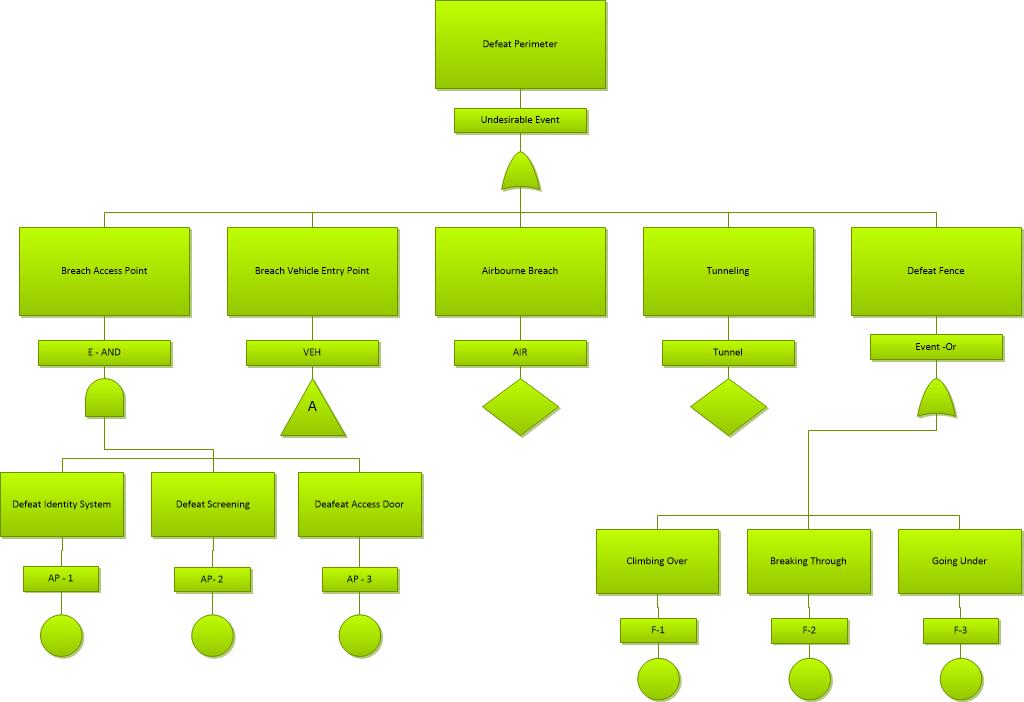
The Critical Infrastructure of the Site
The components of critical infrastructure include essential services and vulnerable points. On the one hand, an essential service is an ancillary process or utility that facilitates necessary role implementation according to the site requirements. Primary services include, without limitation, electricity, gas, fuel, oil, water, environmental control, equipment cooling, communications infrastructure (road and rail included), and telecommunications. On the other hand, the vulnerable point is that hostile organizations can damage using the means available to them. A security specialist may identify these means by conducting a threat assessment. Notably, damages to vulnerable points are not acceptable because they may significantly impair the role of the infrastructure. One can also define a weak point as one incapable of repair or replacement by current means accessible to the operator immediately after or during an attack and within the allowable outage. Some vulnerable points may be accompanied by standby, reserve, or bypass strategies providing response within the allowable outage time in case of a severe destruction of the main component.
Outage time measures the amount of time that services become unavailable due to an attack. It may also refer to the amount of time that a component fails to offer its critical services within a system without significantly affecting other components’ functioning (Drago et al., 2019). Depending on their nature and intentions, among other things, malicious individuals can attack both the essential service and the vulnerable points at the same time. In this regard, when planning to prevent or react to a security breach, it is necessary to understand the importance of the infrastructure elements. Thus, the Eagle Site’s critical infrastructure in the north of Tbilisi, Georgia, includes the radar aerial, intake substation, standby generator, on-site store, and the workshop and mess. The radar aerial is a critical infrastructure because it exists predominantly to offer aerial radar services to a civilian aviation institution. The main intake substation (MISS) is also an essential infrastructure because it is the source of all the power enabling the facility to run smoothly. The standby generator exists to provide emergency electricity in case of power outages in the primary grid, thereby ensuring service continuity and minimal or no disruptions.
An uninterruptible power supply (UPS) maintains the system before the standby generator switches on and supplies the needed electricity, without which there will be no services on the site. The store is also a critical infrastructure because it contains important equipment, tools, spare parts, and essential supplies for regular repairs, maintenance, and services. In case of an emergency, the response team would rush to the store to get equipment and tools as the first response before considering other options. If someone attacked and destroyed the facility, they will negatively impact the staff’s ability to respond to any events that could affect the essential services. Lastly, the workshop and mess are also critical infrastructures because they help those living and working on the site implement their activities. Like the store, the workshop contains tools for repair and maintenance.
Attack Path and Analysis
The attack path shows how accessible a critical resource is. Therefore, an analysis of the attack path can help understand the resource and make relevant changes (Appendix D: Target analysis process, n.d.). Figure 1 below shows a sample attack path. This understanding influences the utilization of physical security metrics.
Scored CARVER Matrix for the Site
The United States military originally developed the CARVER (criticality, accessibility, recoverability, vulnerability, effect, recognizability) matrix for target analysis and assessment for resource allocation. Since it is adaptable to individual and group needs and is simple to use, businesses now depend on critical infrastructure risk management and assessment. Its selection factors help organizations determine the best attack components and needs. A user assigns values (ranging from 0 to 10) to each of the six factors to determine the seriousness or extent of an issue. The higher the set value, the greater the extent of that issue; hence, it is more important to find and implement corrective measures. If the value is low (e.g., less than 5), one may ignore it as there is no emergency. After assigning weights to each factor and summing them up, the highest number represents the most critical component whose attack could cause catastrophe within the site requirement’s limits. Targets with the highest cumulative values are also the most likely candidates for an attack, given their importance. A brief description of each of the six elements is given below:
- Criticality refers to the value of a target and, undoubtedly, an attacker’s primary consideration. A resource or asset is critical if its damage or destruction significantly impacts operations (Appendix D: Target analysis process, n.d.). It depends on time, quality, surrogates, and relativity.
- Accessibility measures how easy it is for an operational element and its equipment and personnel to reach the resource and accomplish its mission. It is understood by measuring the components that facilitate or impede access (Appendix D: Target analysis process, n.d.). One may gain such information by identifying and examining critical paths taken by operational elements while attempting to reach the resource and implement its goals. Access occurs through infiltration, movement to the general location of the resource, move to the location of the resource’s critical element, and exfiltration.
- The recoverability of a target refers to the amount of time needed to repair, replace, or bypass the critical infrastructure’s damage or destruction. How fast a resource recover depends on various factors, including its nature and complexity (Appendix D: Target analysis process, n.d.). Discussion of recoverability issues may touch on substitution, restoration, on-hand spares, and equipment, among other things.
- Vulnerability refers to a resource’s exposure to attack by the operational element. It also considers how critical damage becomes (Appendix D: Target analysis process, n.d.). It depends on the target’s construction and nature, required damage, and available assets, among other things.
- The effect refers to the attack’s impact on the operations and other issues like society, the economy, and people’s psychology. Examples of adverse effects of an attack include unemployment, countermeasure triggering, collateral damage, and economic damage (Appendix D: Target analysis process, n.d.). The magnitude of the effect will depend on the nature of the critical infrastructure and the attack.
- Lastly, recognizability refers to how an operational element can recognize the critical infrastructure under different conditions. Some resources may not be invisible under certain weather conditions (Appendix D: Target analysis process, n.d.). In other situations, some level of knowledge and skill is needed to recognize a critical infrastructure.
One can rate the desirability of a potential target by assigning a value to all the six factors discussed above and adding the total for each factor together to determine its importance or weighted scale. For the Eagle site in Tbilisi, Georgia, the radar aerial has the highest attack risk, followed by the main intake substation shown in Table 1 below.
Table 1: CARVER Matrix for the Site
Considerations for the Resilience of the Site Operation: Managing Passenger Flows
One of the considerations for the resilience of the site operation is managing passenger flows. This understanding assists passenger flows and provides excellent insights into the reliable and effective matching of security screening operations to passenger flow. Since security screenings may develop technical problems at any time, it is essential to have contingency plans to address such occurrences (Yamada et al., 2017). The key to avoiding such a problem is ensuring enough security checkpoints and staff. At the Eagle Site in Tbilisi, Georgia, calculating the number of expected visitors is done by determining the number of people going through check-in, which varies from time to time. For example, if there are 30 check-in desks, the number of visitors in 10 minutes (600 seconds), assuming that the average processing time is 150 seconds, is given by:
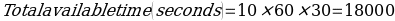
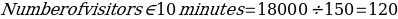
Suppose the average time for security processing is 12 seconds and ensure that the check-in desk and the security can operate simultaneously. In that case, the number of needed security checkpoints is given by:
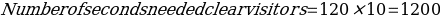
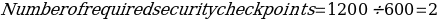
Therefore, Eagle Site in Tbilisi, Georgia, may require two security checkpoints if the assumptions made above are true. The number of desired security checkpoints depends on the number of expected visitors per unit time and the amount of time needed to clear visitors. If the check-in desk and the security scan operate at the same rate, the facility will avoid long queues, resource idleness, and other undesirable occurrences such as missed flights.
Recommended Countermeasures and Reasons for Recommending Them
One can implement various measures to improve the security of the Eagle Site in Tbilisi, Georgia. Thus, one of the recommendations is to build a perimeter wall around the facility. At present, it has a border with shreds of barbed wire on three of its sides while the fourth side, which is cliff-facing, remains open. With the absence of a perimeter wall, accessibility of the critical infrastructure to operational elements increases significantly. The following recommendation is to ensure that some critical infrastructure is inside a building or an enclosure. Presently, the radar aerial, MISS, and standby generator are within the compound but not enclosed. Therefore, they are highly accessible and could be targeted easily. The reason for making this recommendation is that an additional layer of a wall surrounding each of the three main critical infrastructures will prevent them from danger and ensure that their accessibility reduces. The following recommended countermeasure is to create an extra storage room to diversify risk. The owner of the Eagle Site could also consider separating the mess and the workshop. That way, a single target attack may not necessarily affect the other. Most importantly, the owners must embrace continuous improvement to develop the critical infrastructure and manage their risks.
References
Appendix D: Target analysis process. (n.d.). FAS. 2021, Web.
Drago, A., Marrone, S., Mazzocca, N., Nardone, R., Tedesco, A., & Vittorini, V. (2019). A model-driven approach for vulnerability evaluation of modern physical protection systems. Software & Systems Modeling, 18(1), 523-556. Web.
Yamada, H., Ohori, K., Iwao, T., Kira, A., Kamiyama, N., Yoshida, H., & Anai, H. (2017). Modeling and managing airport passenger flow under uncertainty: a case of Fukuoka Airport in Japan. In International Conference on Social Informatics (pp. 419-430). Springer.