Summary
Modern warfare has also undergone dramatic changes as a result of the Information Technology revolution. Information is integral to modern warfare, arguing that a military capability’s success depends on information supremacy. The justification for seamless operational activities, shared battlespace consciousness, location surety for hospitable and enemy troops, and genuine data transmission are essential. When it comes to using precision to strike valuable assets, it is most probable to achieve the desired outcome. As real-time data collection and defense systems get more capable of responding to such data, correspondence becomes increasingly essential (Godé, 2016). Using real-time communications, numerous forces can be linked asynchronously at a regional location and time, regardless of their global capabilities. Department of Defense S & T priorities include information systems, sensors, and simulation models. In addition, simulation has already contributed significantly to training, preparedness, weapons configuration, and acquisition management. Both human and equipment battle losses can be reduced considerably by combining these technologies.
A critical association exists between military technology, its tactics, and the psychological characteristics that connect its users into units, dating back to the dawn of history. For military organizations to succeed in combat and for military development to achieve their ultimate goal, combatant groups must coordinate their actions strategically and effectively (Ghani et al., 2016). Because of the department’s cohesiveness, its representatives are compelled to put aside their interests, and sometimes their lives, to serve its best interests. Strategies and technological advancements both have a direct impact on these forces. Innovation can have a substantial effect, with the positive influence seen in the classical Greek hoplite infantrymen’s experience (Ramirez et al., 2016). The phalanx was a tactically powerful formation because its weapons and armor were most efficacious when used in perfect shape.
The use of information technologies has transformed the battlefield. Currently available platforms, ammunition, sensors, and individuals can perform better thanks to them. Almost every dynamic network today is enhanced by electronic devices and software. Communication, intelligence gathering, assessment, and dispersion, precision strike capability, interface control, sensor data processing, and human performance all benefit from using information technologies. A timely and accurate battlefield report is essential to our troops’ safety.
Battlefield advantage depends on the ability to efficiently gather, integrate, evaluate, and deliver this information. Due to many available strategic reports, the team members are encrypting the information into relevant forms for frontline decision-making. Sustainment data analysis is becoming increasingly extensive, even when it’s not on the battlefield. To ensure that equipment is on hand, there seems to be too much administrative overhead. Programs utilize information analytics to reduce overhead costs and increase efficiency by tracking supplies using sensors and computers (Liu et al., 2020). The department’s goal is to rapidly sort through large amounts of data and provide logistic experts with information that will allow for operational excellence and reduce errors by utilizing advanced software programs and systems and digital technology. Also, technology is crucial to ensure that an enemy does not disrupt our information systems.
Operations can move much faster based on common battlespace recognition and actual information assurance, and enemies can be more accurately identified on the battleground. Information propagation and retrieval systems that are well-organized and well-connected allow tactical units to make more informed decisions on the frontlines. Command and control are exercised through the transfer of directives and guidelines by commanding officers to their underlings. All methods of transmitting messages, powers, and reports are included in this category (Ghani et al., 2016). This procedure includes techniques used in the sector or the water and ways used between the command center and distant infrastructure or ships. Long before the advent of modern warfare, military interaction played a significant role in the conduct of war. Thus, this discourse describes a comprehensive project plan to ascertain the significance of information communication technology (ICT) in promoting the revolution of the modern military.
Project Management Approach
When it comes to project success, it is usually a process of designing, along with talent and collaborative effort among team members. Each of the project’s key team members is essential, but it is not always confident in who they are or their roles. Organizations have been irreversibly altered by digital technology. It clarifies key concepts and definitions, highlighting major theories and research results. There are also categories that team papers based on micro and macro analysis (Liu et al., 2020). According to Liu et al. (2020), leading digital culture development requires leaders to build relationships with various and dispersed stakeholders, facilitate collaborative practices in complex settings, and participate in pushing ethical issues.
Stakeholders’ expectations are met or exceeded when a project meets its objectives. The term stakeholder refers to individuals who are interested in one project. As an outcome, they are tasked with doing their work and have plenty to lose or gain from it. Sponsors, usually senior executives in organizational performance to allocate resources and clear strategies regarding a project, are considered stakeholders in that endeavor. Stakeholders include the program manager, members of the project team, and managers from those other departments within the organization. In terms of organizational information communication technology (ICT), the conflict between system integration and departments, complex and dynamic, is probably the most prevalent (Ghani et al., 2016). Both the central and local perspectives are equally valid, and attempting to eradicate the discrepancies is neither feasible nor appropriate. Any organization’s information strategy must strike the right balance between centralized control and local execution.
An integrated system is replacing a service-oriented federated approach in recent years by defense organizations. Modern warfare requires the Air Force, Army, Navy, and other services to work in a more coordinated and integrated manner, in part due to the extreme nature of the conflict (Liu et al., 2020). As far as intelligent weapons are concerned, ICT has revolutionized the entire defense industry. In the past, the military sector produced unguided munitions using ICT. As a result, they are incredibly efficient, and their accuracy is excellent. Individuals are capable of communicating with their commanding officers much more frequently and reporting on their firearm status. Most strategic defense corporations have dedicated software design departments (Ramirez et al., 2016). In addition to battlefield management systems, long-range radars, GPS, and missile productive guidance systems, this software is used in various hardware devices.
Because of the military’s culture, their operations often have a different dynamic than civilian operations. Instead of manipulating everyone towards a shared goal, rank or military power can continually advance an initiative (Liu et al., 2020). By issuing instructions to subordinate institutions, this is attained. Because of this, some army project leaders assume that everybody will do one role for a venture since they will accept instructions telling them so. Also, military officers must keep in mind that their initiatives must align with the power and influence of multiple stakeholder groups. Stakeholders impact organizational change, so engaging them at all levels of the system is necessary to identify prospective barriers and facilitators. Although the government facilitates the accessibilities of technological advances, the senior troop members are responsible for promoting their adoption.
However, resource constraints will influence the success of the project by the military. Based on schedule, cost, and quality, as well as the absence of disputes, a project’s success is measured (Ghani et al., 2016). Thus, all the entrusted vital players need to collaborate amongst themselves to solicit enough resources. Also, the personnel’s preparedness is another aspect that might influence the success of the program.
The Specific Stakeholders for the Project
For any project to be successful, each representative or clique of the design team must have defined roles and responsibilities so that aspirations can be clearly set and obligations can be clearly understood (Ramirez et al., 2016). Depending on the project, these duties may vary from a different corporations. Thus, understanding the following key players have a role in overseeing the successful adoption of ICT in the military.
Program Manager
The program manager’s responsibility is to track how many initiatives are being made about goals such as company expansion. For all interlinked initiatives within that initiative, they are solely responsible. Each of these efforts is overseen by the systems engineer. They are responsible for ensuring the timely completion of a particular project. Programs can be linked to corporate goals, and correlations between initiatives can be seen (Godé, 2016). They draw up an action plan for the work that is to be done and an estimate of when the work will be finished. As a result, they can monitor cross-functional frameworks, establish priorities, and chart progress.
Program managers also measure the return on investment for the entire system. They also track budgets, timelines, resource consumption, risk prevention and mitigation arrangements, issues, and shipments according to plan, among other items. In organizations with a high level of maturity, program managers may monitor earned value. The project manager calculates the return on investment (ROI) for each project. These individuals are also responsible for keeping track of a project’s budget and schedule and its risks and issues. It is then the project coordinator who consolidates all of their metrics.
The managers’ responsibility is to oversee a program’s overall cost, timeline, and performance and report to Milestone Decision Authority (MDA). In the course of a network’s and a program’s life cycle, they provide leadership, make decisions and provide oversight. They have to be the system’s leader, understand specifications, balance limitations, manage contract workers, bolster momentum, and put core operational skills to work successfully. Acquisition Strategy development, management, and execution are all under the purview of the PM. System Engineering is also used to translate operations and maintenance needs and abilities into technologically possible, affordable, and functionally effective, and appropriate increments. To optimize layout, manufacturing, and acquirement processes, the Department of Defense (DoD) uses Integrated Product Teams (IPTs), a management technique that incorporates all vital acquisition activities (Ramirez et al., 2016). In addition to field support, IPPD facilitates cost and performance goals from new products through production and beyond.
Milestone Decision Authority (MDA)
The Milestone Decision Authority (MDA) is indeed the program’s executive sponsor (MDAP). As needed by the DoD Instruction 5000.02, the MDA officially begins each incremental acquisition program. Cost, routine, and performance are evaluated during a Milestone evaluation to ascertain if an initiative has achieved its transition period exit prerequisite and can move on to the next stage of development. In addition, MDA shall be responsible for the cost, timetable, and productivity reporting to relevant officials, including parliamentary reporting.
Finance Manager
Managers of financial affairs direct and synchronize budgeting functions, and they serve as consultants to leadership across all aspects related to computing, finance/accounting, and cost analyses. Their responsibilities include establishing performance goals and priorities for employees, establishing security standards for protecting sensitive information, and managing personnel. Accountable for managing accounting activities and advising on efficient asset use and reallocation within fund constraints, they also advise on efficient asset use and redistribution. Other than a four-year degree, an accounting degree or finance training may be required for financial managers. Various training ecosystems are used to train wealth advisors in the school environment and on the job (Liu et al., 2020). These officers also undergo a rigorous training program covering their responsibilities, military organization and etiquette, and leadership skills.
Integrated Product Team (IPT)
Team of delegates from various suitable disciplines that work together to create successful programs, address potential issues, and make logical and timely suggestions to facilitate decision-making evaluation and decision-making are carried out using integrated project teams (IPTs) in complex design programs/projects. As a cohesive forum, all interested parties are encouraged to participate in the IPT. It consists of a cross-disciplinary group of individuals who are collaboratively accountable for implementing a defined solution to a problem, such as a software development team or an engineering team (Godé, 2016). In complex programs and projects, IPTs are used for review and decision-making purposes. All partners are encouraged to participate in the IPT through a collaborative forum.
Oversight IPTs (OIPTs) and Working-level IPTs are examples of IPTs that can be discussed at the end of each stage. IPTs are often made as part of organized information systems methodologies, which focus on comprehending each stakeholder’s wants and needs. When the DoD in the United States introduced IPTs in 1995, it was part of significant acquisition reform. It refers to a system of partnership practiced between all parties involved in the daily execution of the project (Godé, 2016). It is a DoD strategic tool that optimizes design, production, and consistency processes through IPT.
Procuring Contracting Officer (PCO)
DOD 5000.1 designates the Program Manager as the person inside the Services accountable for planning a scheme acquisition program. His program’s success is dependent on the assistance of a merited Procuring Contracting Office PCO. The PCO must order all required documents to ensure that the contractor meets all conceptual, technological, and other contractual requirements. It could be held liable for any adjustments that the project manager makes due to improper official regulations. Despite not reporting to the PM on a formal administrative level, the PCO is still required to meet the Program Manager’s algorithmic and technical needs.
Communication Manager
Communication managers strategize, build, safeguard, execute, and safeguard communication systems. They are also responsible for maintaining and securing communications networks. In addition, they are responsible for overseeing the establishment and production of ideas and strategies that are vital to the operation’s successful completion. In addition, they may supervise the encryption algorithm processes and ensure that sensitive communications are routed appropriately. Four-year university education is typically required for entry into the military. They must also complete a rigorous training program that covers the military structure, etiquette, and traditions, as well as leadership development (Liu et al., 2020). It is their job to oversee the advancement of brand leverage to develop marketing and communications techniques for internal and external communication. To help the brand add value to the local, domestic and international mainstream press, they also maintain contact with the media. Thus, this manager shares information about the project with all the stakeholders.
IT Specialists
A profession’s ethical or technological standards are characterized or adhered to by information technology professionals. Every sector advances its technical standards, arguing that the IT industry moves at a faster and more widespread pace. A complex computer system is maintained by people who build and test the operating systems linked with it and install, fix, and sustain it in one or even more locations. IT professionals from around the world are hired by some companies to maintain their vast computer networks. Because of the capabilities of technology, IT professionals can work from anywhere (Ramirez et al., 2016). Whenever there is a mechanical issue, however, the IT expert will have to alter the system. IT professionals will continue to learn new IT knowledge and undergo training as long as they are employed. A corporation’s coding language, system software, database tools, and methodology may differ from another’s.
IT professionals come in a variety of shapes and sizes. Each type focuses on a different aspect of computer network analysis or maintenance. Using computer code, a programmer, for example, creates and browses the internet and programs. Senior programmers tend to have more accountability as they advance in their careers. In addition, they are responsible for overseeing their team members and fixing defective or malfunctioning programs. Fort Gordon, Georgia, will host a course for soldiers preparing to take on the responsibilities of a Telecommunications Specialist. Soldiers undergoing Initial Entry Training (IET) at Fort Gordon and soldiers reclassifying from other professional specialties or baseline service personnel receive training at Fort Gordon. MOS-I stands for Basic Training, and MOS-T stands for Re-class. Soldiers in coaching will be classified into one of several stages of coaching (Godé, 2016). All military personnel in basic training, irrespective of rank or length of service, will participate in this phase.
Contracts Manager
In an organization, the contract manager oversees the development of contractual agreements. As part of a firm’s business relationship with a supplier or partner, an employee, or other external stakeholders, the contract manager prepares, analyzes, and negotiates agreements. It is the responsibility of project staff to write and track contracts involving the purchase or purchase of goods or services. The managers’ primary responsibility is to optimize agreements to maximize their employer’s profits. From authorities to technology, contract managers work in a wide range of industries. Every organization has a contract manager in charge of creating and managing all deals (Ramirez et al., 2016). Contract managers must possess a wide range of skills to successfully supervise contracts from the drafting stage to the execution stage.
To expedite approval of any variants, contractors are often the primary contact between an organization and third parties. In addition, they offer suggestions and make deals with purchasing personnel. As a team, they produce a final draft that is acceptable to all involved parties. For an organization to be successful, communication and surveillance processes must be streamlined. Because of this, contract lifecycles and contractors are more efficient when they have access to a tool that automates processes and collects all dialogues, edits, and other information in one place. Therefore, contract managers need to establish contractual agreements with the potential suppliers of the IT materials to guarantee that the project becomes a success.
Military Personnel
Troop members are the key stakeholders in ensuring that the proposed project succeeds. The U.S. military is responsible for maintaining the nation’s defenses. Nurses, physicians, and lawyers are among the civilian professions that service members hold. In the military, there is a distinction between enlisted service and officer service. Godé (2016) indicates that about 82% of the Army are enlisted troops who conduct military operations. Only 18% are soldiers who oversee operational activities and enlisted men. Approximately 8% of officials are warrant cadets, who are tactical and strategic specialists in a particular area of the law enforcement field (Godé, 2016). Air force pilots make up one clique of permit officers, for instance. Thus, the other project players need to collaborate with the personnel to make sure that they understand their distinct aims during the project’s implementation phase.
Milestone List
Observing, measuring, and monitoring the progress and efficiency of a project is accomplished through milestones. They serve as intermediate steps before an ultimate objective is reached. Markers are helpful because they provide a basis for tracking progress. Their use as confirmation in trying to explain and disclose a project’s progress is also permissible. Its frequency and possibility to provide key factors and learning opportunities are two of its most essential features. To maintain oversight and motivate employees, milestones could be used. As a project progresses, milestones indicate how well it is going. This fact is because success criteria are by far the most apparent signs that the project is moving. Defining a milestone is a point of reference that marks essential decision points. Instead, it represented a vital incident for a current project or set of tasks without referring to a specific timeframe. Markers are often associated with outstanding achievements or reaching levels that no one has ever earned before. Auditing after the completion of the project will help in determining its effectiveness. However, additional two months will be added should the team experience any delay during the execution period.
Costs
With a budget of $703.7 billion, the project will consume less than a quarter of the resources.
Scope Quality
Project Scope and Work Breakdown Structure (WBS)
Project Scope
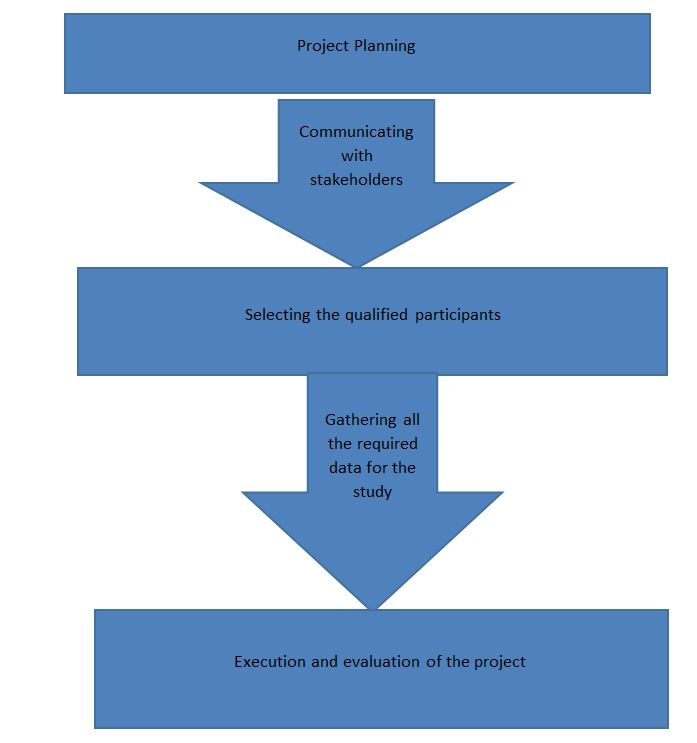
This study aims to ascertain the significance of ICT in the military. The project will take advantage of the available research findings on the internet. The participants have signed informed consent to prove that they take part in the research study willingly. This study will take about one year before the findings are shared with the military personnel and other ICT stakeholders associated with the success of the various industries.
Work Breakdown Structure
- Selecting participants and starting the project
- Gathering data about the research topic
- Evaluating the procedure to determine any potential loopholes throughout the study
- Analyze the collected data and share the findings with the entrusted stakeholders.
- Evaluate the implementation of the proposed recommendations to ascertain their reliability in the military.
Change Management Plan
- All stakeholders need to understand and acknowledge the need for change.
- The managements need to enlighten the military personnel about the need for change.
- Detailing the change plans, including the changed objectives and performance measures for the new project plans.
- Involving every key player to implement the change plans will oversee the execution phase.
- Assess the progress of the endeavor and cerate the successes. Importantly, the department’s Change Control Board (CCB) needs to approve the proposed change before involving the key players through the various execution phases.
Communications Management Plan
The communication Manager will use the available high-tech communication tools to enlighten all the key players about the project aims and expectations. Other than using the department’s official website, a written memo will include every key player’s distinct roles and the expected goals of the recommendations. During the planning phase, the communication will be shared to ascertain that all the players are included during the implementation stage. Notably, honest communication will guarantee the success of the programs.
Cost Management Plan
Even educational institutions have trouble allocating resources. The availability of precise ICT cost analysis hinders many institutions’ ability to make effective decisions in this area. ICT proposals are viewed with skepticism by resource budgeters because of inadequate information beyond cash payment and licensing fees. Extremely optimistic forecasts for projects that did not deliver have tarnished IT departments’ credibility, as have expenditures. ICT has a reputation for offering a significant return on investment (ROI) and a low-risk investment. Project managers must provide policymakers with timely and accurate information about the cost of any given system to counteract the generally inadequate responses to proposed ICT projects. This outcome means ICT will be equal with more mature competing companies, such as building maintenance, competing for scarce resource allocation metrics. Thus, all the key players will need to contribute towards soliciting enough resources and utilizing them efficiently.
Procurement Management Plan
Purchase needs are determined by a procurement plan, which covers all phases of a project, from document preparation to contract to close. One can think of this document as a blueprint for handling all procurement tasks and ensuring that all objectives are met with a maximum value of transactions. The procurement managers will work with the other key players to guarantee the ICT acquisition and implementation successfully within the department.
Project Scope Management Plan
The project manager needs to use the scope management plan to ensure that the specific initiatives achieve their respective aims. When it comes to scope, not only does it help define the project’s boundaries, but it also helps determine who will be accountable for which tasks and what procedures will be followed to ensure that all is done properly and approved. Although a change order form will help change the project’s scope, a quality management plan will guarantee the project’s life cycle.
Schedule Management Plan
The project scheduler will consider the Program Evaluation Review Technique (PERT) Chart to illustrate the project’s tasks for effective assessment. This initiative will take about a year until its completion, with the team targeting to begin on August 15, 2021, and end on July 25, 2022. The broken-down project will guarantee that the team evaluates the operations and ascertain their successful implementations. The PERT Chart will help the team determine their success when it comes to implementing the ICT project.
Quality Management Plan
To guarantee that the Americans and the global population are safe from sudden attacks, the quality of the ICT initiative will depend on society’s feedback regarding the security measures put in place. The ICT managers will monitor the tools to ensure that the military personnel access quality communication technologies, depending on how frequently the team monitors the initiative’s progress. Thus, it will be wise to guarantee the comfort of the team members to ensure they execute their distinct roles.
Risk Management Plan
Thorough research before the project will ensure that the team identifies the potential risks and measures to counter them. However, evaluation during the execution phase will detect unidentified threats and help recommend amendments to the initiative to ensure that they realize sustainable success. Any failure will undermine the project team’s efforts, hence the need to prepare a comprehensive risk management plan for the team to follow.
Stakeholder Management Plan
After identifying the potential key players for the initiative, the communication manager communicates to them, explaining the scheme’s objectives. Every party must have comprehensive details about their distinct duties during the project’s implementation phase. Creating a conducive environment will promote the stakeholders’ engagement, with their collaboration depending on the management’s efforts to monitor their engagements. Besides, the team needs to have enough resources to execute their various roles.
Staffing/Human Resource Management Plan
After identifying the need to recruit new partners in the project, the qualified individuals get recruited and undergo comprehensive training regarding their duties throughout their life cycle. Subsequently, monitoring the team will guarantee that they do not deviate from their responsibilities. Instead, the team will identify any loophole that might undermine their productivity. Notably, a reliable communication system will guarantee that the team relate well and share their experiences, hence realizing their successes.
References
Ghani, A. K. A., Ismail, M. N., Omar, Z., & Nohuddin, P. N. (2016, May). Establishing mesh network amongst infantry personnel during military operations: A preliminary study. In 2016 International Conference on Information and Communication Technology (ICICTM) (pp. 218-222). IEEE. Web.
Godé, C. (2016). Coordination practices in extreme situations: Lessons from the Military. In Project Management in Extreme Situations (pp. 203-214). Auerbach Publishers. Web.
Ramirez, T. L., Gatewood, D. P., Kirkpatrick, E. L., & Menon, K. K. (2016). Holistic Contract Administration in Army Forces Abroad. Defense AT & L Magazine. Web.
Liu, C., Xiao, B., & Wang, W. (2020). Analysis of project management of military barracks in high-altitude areas. In IOP Conference Series: Materials Science and Engineering (Vol. 780, No. 5, p. 052013). Web.
Appendices
Appendix A: Milestone List
Appendix B: Baseline Schedule
Appendix C: PERT Chart Development