Abstract
Security in online payment is an issue that has gained massive attention in the recent past due to the increasing cases where online fraudsters gain access and steal from online shoppers. This is happening despite the effort made by banks and retail outlets to protect their customers.
This paper confirms that the main reason why online fraud is still common is the inability of online shoppers to take the measures meant to protect their private information. Online shoppers can make simple steps to protect themselves when making online payments by avoiding phishing sites, protecting their private information during and after payments, and having secure internet access.
Background
Online payment is becoming very common in the current globalized world market. According to Snider and Ziporyn (2012), technology has transformed the way businesses are conducted in the global market. With the improved communication system, a customer in New York can now order and pay for a car in Berlin without traveling to Germany. The emergence of the online payment system has made trade easier than it used to be in the past.
However, Ottenheimer (2012) notes that the emergence of online payment has given rise to a new problem. The issue of insecurity in the online payment has hindered the growth in popularity of this payment method. Fraudsters are now using their skills and knowledge in information technology to track the activities of online shoppers and steal from them. According to Keegan and Green (2013), statistics show that the number of people losing their money to online fraudsters is on the rise.
This makes it necessary to come up with measures that can be used to improve the security involved in online payments. Fazlollahi (2002) says that security in online payment starts with the user. Most of these online fraudsters take advantage of the ignorance or carelessness of online shoppers to steal from them.
That is why Aaker (2009) says that online shoppers should follow simple steps that would enhance their security when they shop online. These steps will reduce the capacity of these fraudsters to access the information they need to steal from online shoppers.
In this paper, the researcher will look at ways in which online shoppers can enhance their security when making online payments by avoiding phishing sites, protecting private information during and after payments, and having secure internet access. These are simple steps that are easy to follow as long as one has basic computer knowledge.
Discussion
According to Krutz and Vines (2010), many cybercriminals have learned the art of stealing from unsuspecting online shoppers who lack the knowledge of how to protect themselves when making online payments. Many institutions, such as banks or major retailers, have developed various means of protecting their customers. That is why these criminals are now looking at the shoppers as their easy targets when planning to steal from them (Lebow & Spitzer, 2002).
Taking security measures into one’s own hands may be the best strategy that can be used to ensure that one is protected from the fraudsters who may want to steal one’s money or personal information. The following are some of the basic steps that one may need to observe in order to be safe when making online payments (Zhu, 2004).
Avoiding any phishing site
Fraudsters are getting highly sophisticated in their effort to ensure that they steal money and private information from online shoppers (Mather, Kumaraswamy & Latif, 2009). One of the best ways of protecting yourself from these cybercriminals is by avoiding phishing sites. These are the sites developed by online fraudsters to help in getting information from the customers that will enable them to steal their money.
Instead of hacking into the personal accounts of online shoppers, online fraudsters sometimes manipulate their customers into giving them personal details, including passwords. This gives them access to the accounts (Bakos, 2001).
Once they access the accounts, they can make payments, transfer money from the targets’ accounts to their own accounts, or do anything they want with the personal information of the targeted individuals. The best way of avoiding this from happening is by detecting and avoiding any phishing sites (Winkler, 2011). No one should manipulate you into revealing your personal information, especially the details about bank accounts.
Protecting private information during and after payments
According to Schniederjans and Cao (2002), sometimes simple security measures taken during the online payment process may go a long way in protecting one from a possible fraud case. It is important to start by understanding the processes involved in online payments. The diagram below summarises the process of making online payments and the stakeholders involved in this process.
Figure 1: Diagrammatic representation of the online payment process
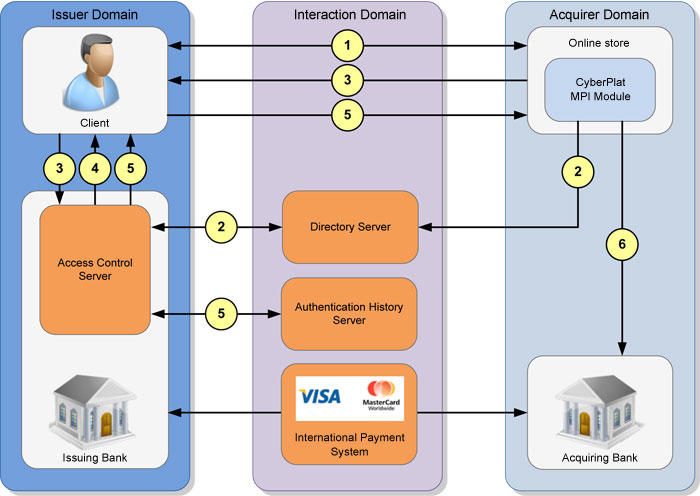
As shown in the figure above, when making online payments, there are four entities involved. They include the buyer, seller, issuing bank, and the acquiring bank (Temporal, 2010). The buyer communicates with the seller, and if the two reach an agreement on the sale and purchase of a given product, then the process of making payments will be initiated. The buyer will instruct his bank to release a certain amount of money to the bank account of the seller.
This can be done using international payment systems such as visa MasterCard (Laudon & Traver, 2014). The online shopper should be keen to identify any attempt by the fraudsters to access the details that are meant to be private. For instance, when the website of the seller demands the account’s password of the buyer, then this should be a cause for concern.
It would be more appropriate to use instant money transfer systems such as Money Bookers instead (Qin, 2014). The Money Bookers allows the shopper to keep the account details private while making any payment as long as there is enough cash in the account. Once this transaction has been completed, the buyer should check his account to ascertain that the correct amount has been deducted.
Jain (2011) says that it is very important for one to ensure that he is completely logged out of the payment website and the website of the seller after the transaction is complete. Closing the browser may not be enough because one can still have the confidential details if they use the same browser after a short while (Panagariya, 2000).
Having a secure internet access
The security of the internet used in making online payments or accessing one’s bank account is of paramount importance. According to Leung, Cheung, and Hai (2000), Wi-Fi networks have gained popularity in our world, where communication is very important. In a family or office setting, the use of Wi-Fi has become very popular. It allows all the family members or the members of a given office to share the internet without having to use a given portal.
However, Cook (2005) says that it poses an immense risk to an individual who may decide to go shopping online using such internet accesses. In the home setting, a neighbor can also have access to the Wi-Fi, and this allows him to monitor every move an individual makes when going online.
In the office setting, the same scenario may occur (Mowbray, 2009). Sometimes the cybercriminal may be a fellow staff member who is using the same Wi-Fi system but with ill-motives of stealing from their unsuspecting colleagues who prefer making regular online payments. When this happens, online shoppers get fully exposed to their attackers (Lynch, Kent & Srinivasan, 2001). This will enable these criminals to do anything they desire with the bank accounts of online shoppers.
Adams (2013) advises that one should avoid using publicly used Wi-Fi when making important and confidential online transactions. When using a privately managed Wi-Fi, it is important to ensure that it is protected using WPA software other than the older equivalent known as WEP, which has become more vulnerable to these fraudsters.
Child (2009) says that it may be necessary to change the router’s password and the SSID (Service Set Identifier) frequently to enhance security. Of interest will be to ensure that the name of the default network does not make it easy for the cybercriminals to compromise it (O’Brien & Marakas, 2011).
It is highly recommended that one should use a personal computer that is not accessible to any other person when making online money transfers or important transactions. Some hackers may use computers that an online shopper has just used to track all the details that may help them access the account of their target. According to Knight (2006), another important yet easily ignored fact is to ensure that a strong password is used to protect the Wi-Fi, the bank account, and the computer used.
Using one’s own name or the name of a family member may not be advisable because one can easily make a correct guess. The password should be unique, combining various characters that make it impossible for anyone to make a correct guess (Nash, 2000). This limits the possibility of hackers accessing the account details. The password should be changed regularly, just in case one is making positive progress towards knowing it.
Conclusion
Online payments require proper security in order to ensure that the details of the customers are protected. It is evident from the discussion above that online shoppers have a lot to do in protecting themselves when making online payments. Banks and retailers have put structures to ensure that their customers are protected from fraudsters. However, online shoppers can only remain protected from these fraudsters if they take initiatives to protect their personal information.
This starts by avoiding phishing sites. These sites are managed by cybercriminals who are keen on getting the personal details of the shoppers that will enable them to access their accounts. Once this happens, they get full control of these accounts, enabling them to steal from online shoppers.
Ensuring that private information is protected during and after the payment is another step towards enhancing the security involved in online payments. Online shoppers should make an effort to ensure that no one can access their confidential details about their bank accounts. Finally, having secure internet access is also very important. Using a shared internet may pose serious threats to online shoppers
References
Aaker, D. (2009). Strategic Market Planning. New York: John Wiley & Sons.
Adams, R. (2013). The emergence of cloud storage and the need for a new digital forensic process model. New York: Cengage.
Bakos, Y. (2001). The Emerging Landscape for Retail E-Commerce. Journal of Economic Perspectives, 15(1), 69-80.
Child, J. (2009). The business enterprise in modern industrial society. London: Collier-Macmillan
Cook, J. (2005). Understanding Marketing Strategy and Differential Advantage. Journal of Business Strategy, 49(2), 137-142.
Delone, W. & Mclean, E. (2004). Measuring e-commerce success: Applying the DeLone & McLean information systems success model. International Journal of Electronic Commerce, 9(1), 31-47.
Fazlollahi, B. (2002). Strategies for e-Commerce success. Hershey: IRM Press.
Jain, S. (2011). Marketing Planning and Strategy. Mason: Thompson Publishing.
Keegan, W. J., & Green, M. C. (2013). Global Marketing. Upper Saddle River: Prentice Hall.
Knight, G. (2006). Entrepreneurship and Marketing Strategy. Journal of International Marketing, 8(2), 12- 32.
Krutz, L. & Vines, R. (2010). Cloud Computing Security Architecture: Cloud Security: A Comprehensive Guide to Secure Cloud Computing. Indianapolis: Wiley.
Laudon, K. & Traver, C. (2014). E-commerce: Business, Technology, Society. New York: Pearson Education.
Lebow, R., & Spitzer, R. (2002). Accountability: Freedom and responsibility without control. San Francisco: Berrett-Koehler.
Leung, L., Cheung, W. & Hai, Y. (2000). A framework for a logistics e-commerce community network: the Hong Kong air cargo industry. Journal of Management Information Systems, 30(4), 446-455.
Lynch, P., Kent, R. & Srinivasan, S. (2001). The global internet shopper: evidence from shopping tasks in twelve countries. Journal of advertising research, 41(3), 15-24
Mather, T., Kumaraswamy, S. & Latif, S. (2009). Cloud Security and Privacy: An Enterprise Perspective on Risks and Compliance. New York: Cengage.
Mowbray, M. (2009). The Fog over the Grimpen Mire: Cloud Computing and the Law. New Jersey: Wiley.
Nash, E. L. (2000). Direct marketing: Strategy, planning, execution. New York: McGraw Hill.
O’Brien, A. & Marakas, M. (2011). Management Information Systems. New York: Cengage
Ottenheimer, D. (2012). Securing the Virtual Environment: How to Defend the Enterprise Against Attack. New Jersey: Wiley.
Panagariya, A. (2000). E-Commerce, WTO and Developing Countries. The World Economy, 23(8), 959-978.
Qin, Z. (2014). E-Commerce Strategy. Berlin: Springer Berlin Heidelberg.
Schniederjans, M. & Cao, Q. (2002). E-Commerce operations management. Singapore: World Scientific.
Snider, J. & Ziporyn, T. (2012). Future Shop: How New Technologies Will Change the Way We Shop and What We Buy. London: McMillan.
Temporal, P. (2010). Advanced brand management: Managing brands in a changing world. Singapore: John Wiley & Sons.
Winkler, V. (2011). Securing the Cloud: Cloud Computer Security Techniques and Tactics. Waltham: Elsevier.
Zhu, K. (2004). The complementarily of information technology infrastructure and e-commerce capability: A resource-based assessment of their business value. Journal of Management Information Systems, 21(1), 167-202.