Aircraft Solutions (AS) is a recognized leader in the design and fabrication of component products and services for companies in the electronics, commercial, defense, and aerospace industry. The mission of AS is to provide customer success through machined products and related services and to meet cost, quality, and schedule requirements. The company strategy is to offer low-cost design and computer-aided modeling packages to customers to reduce their development expenses. The business headquarters in San Diego, California, having its Commercial and Defense Departments in San Diego and Orange Counties. These geographical positions of different AS branches not only provide easy access to the global market through the truck, rail, ship, and air transportation methods but also require an enhanced information technology (IT) structure that would deliver and support constant digital communication. The company network is being used daily by employees, customers, suppliers, and contractors, which involves the transfer of significant amounts of sensitive and confidential business and customer data. Therefore, it is crucial for the AS IT group to ensure the safety and efficiency of the company’s security policies, hardware, and software. This paper analyzes the IT architecture and network infrastructure of AS to identify weaknesses in the system and suggest ways to improve the current model to prevent damaging outcomes and minimize security risks.
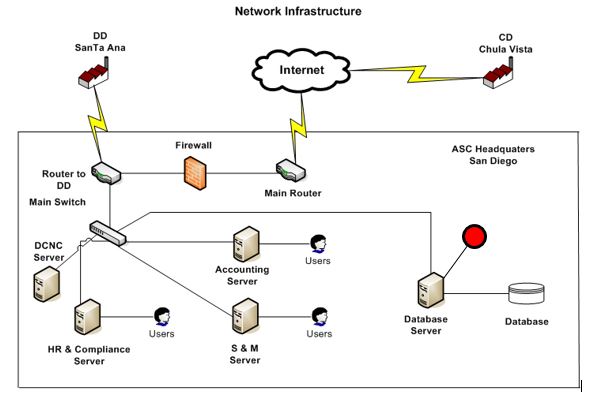
AS uses Business Process Management (BPM) to handle end-to-end processes that span multiple systems and organizations. The system functions in order to establish a timely business dialogue between customers, vendors, and suppliers. Since the business is highly-automated, the company’s IT structure’s efficiency and security should be carefully addressed. The production process consists of continuous file transfer and communication between different departments from the beginning of client information collection and storage until a project’s end and shipment stages. The current team of system administrators, responsible for selecting and installing hardware, software, and related upgrades, implementing information security measures and maintaining support to ensure the manufacturing execution system is working correctly, recognizes the need to ensure and maximize the company’s security. As a result, AS formed a skilled and knowledgeable workforce that can operate within its network system. The infrastructure divides accounting, S&M, and HR branches at AS headquarters through dedicated servers and has a separate server database. System administrators of the AS network implemented various security measures and minimized human error risk through good quality employee education and training. However, this paper identified one policy weakness in firewall and router rule check requirements and one hardware weakness related to the use of network-attached storage (NAS) backup. Considering the modern frequency of cyber-attacks, the geographical location of the business, and the company’s needs, these two issues will be described in detail in a search for increased security and minimized threat.
The first issue lies in the company’s firewall rule update frequency. Since AS IT architecture involves constant use by numerous parties, customers, employees, suppliers, and contractors, the information system is often exposed to security threats and vulnerabilities (Karoui, 2019). The business also promotes digital communication and data transfer between its distinct departments, so network security should be a crucial goal in ensuring timely and effective operation (Karoui, 2019). The current model used by AS incorporates extensive use of firewalls to prevent malicious attacks and minimize chances of unwanted data loss or damage. Safeguarding the company’s confidential and sensitive information should be one of the main priorities for the AS IT team. Despite the IT group’s work in providing good quality solutions in tackling cyber-attacks, the current security policies dismiss the need for increased attention and carefulness when dealing with network safety. Firewall can block potentially dangerous traffic and establish a clean, fast, and secure communication between AS network’s users. It has a set number of rules that recognize malicious data through their installed knowledge base and help firewall function and decide whether to allow or block incoming and outgoing traffic.
However, if these rules are not updated frequently, a firewall can fail to identify a newly developed or improved cyber-attack, exposing the AS network to major risks. The current network security policy adopted by AS requires firewall rules to be evaluated every two years. Unfortunately, a two year period, in which no system update and improvement occur, significantly increases a cyber-attack risk. According to one report, more than half of businesses were attacked in 2017, out of which only seven percent managed to defend themselves successfully (as cited in Brown, 2018, p. 10). These severely damaging events can lead to fatal financial outcomes for a company (Karoui, 2019). Generally, such attacks aim at “destroy[ing], corrupt[ing] or falsify[ing] data”, especially personal and confidential (Karoui, 2019, p. 105). Since the AS company network is used daily by many parties, there is a great risk that an outdated firewall rule can allow malicious data to enter the system.
The information system’s network security is crucial for the success and the future of AS. However, it is difficult to ensure complete protection of the system due to its “complexity and number of … components” (Karoui, 2019, p. 121). Thus, a weak network security equipment management, such as regular firewall updates and checks, “can lead to vulnerabilities that can be exploited by an attacker” (Karoui, 2019, p. 122). In case an attack occurs, affecting the network, the entire business will be damaged. AS will be unable to fulfill its main duties and mission of providing quality products on schedule because a considerable amount of time and money would be required for data restoration or replacement. Attackers can also change customer product requirements leading to additional safety and financial costs. Moreover, exposure to traffic risks associated with outdated firewall rules can prevent the company from achieving long-term, trustworthy customer relationships.
The second weakness is related to the use of network-attached storage (NAS) devices. Although these are the most common for hardware used by small businesses, NAS backup has several security risks vulnerable to the company’s geographical location and previously mentioned firewall rule update policy. Data storage is crucial for any business since complete security cannot be guaranteed even by the most enhanced and recent technology. Since “the information system is an organized set of resources for collecting, storing, processing and distributing information”, carefully and timely protecting the business’s servers and databases are the “most important” aspects of it (Karoui, 2019, p. 121). AS has a separate database server located in the headquarters in San Diego, which is backed up to NAS devices. Although the NAS hardware stores a reserve of company data, it is not protected from physical and environmental threats, which could occur in San Diego. Since “California is prone to various disasters, most notably … from excessive rain …, fires, and earthquakes”, the AS business locations are also vulnerable to these events (Legislative Analyst’s Office [LAO], 2019, para. 2). The city of San Diego also has an overall disaster risk rate of two, three being the maximum and zero being the minimum, while the County itself can face all of the previously mentioned possible occurrences (Sager, 2019, para. 2). These events should be carefully considered by AS management because in case the backup devices currently used were damaged, there would be no way to retrieve the previously available and crucial to business information.
However, a natural disaster is not the only threat associated with the NAS hardware currently used. The devices can not only be easily damaged due to fire, flooding, or earthquake but also stolen because of their weight (Iperus Backup C., 2020). Despite the low likelihood of large scale environmental catastrophes, fires and earthquakes are very common in the area, while the possibility of cyber-attack, which passed an outdated firewall, and in-office robbery exists. These vulnerabilities can significantly damage the company and affect the corporate image. Inability to access a data server backup in case the first is experiencing problems can shut down the entire operating process.
There are two weaknesses in the AS network identified in the paper: one is related to a security policy, while the second is related to the hardware used. Both weaknesses can lead to disadvantageous and costly outcomes if immediate action is not taken. Although some improvements involve an increase in funding and reevaluation of security methods, they can greatly benefit the company and help AS establish trustworthy, long-lasting, and secure relationships with its customers and vendors.
In order to resolve the issue with a firewall rule update policy, the network safety approach of the AS IT team should be reshaped. Currently, the policy requires firewall rule checks and evaluations every two years, which is not adequate, considering the recent frequency of cyber-attacks. For instance, the banking and finance sector implemented a quarterly review and update of their firewalls to ensure the safety of their documents and the trust of their customers (Brannon, 2019). Since AS tightly depends on constant digital communication and information transfer, maximizing the security of sensitive, financial, and customer data is crucial for business survival (Karoui, 2019). Considering the frequency and number of cyber-attacks that occurred and negatively affecting numerous companies and organizations in 2017 alone and emphasizing the importance of network security and existing vulnerabilities associated with firewall maintenance, AS has to quickly adapt to the new environment and make changes in the protection measures (Brown, 2018; Karoui, 2019). Therefore, a new policy should be introduced that would reflect contemporary cyber-security situations and provide a timely response. The period between firewall rule evaluations and updates should be reduced from two years to every three months. Also, additional funding reserve should be created to tackle network problems effectively to comply with the company’s mission of providing service that meets quality, price, and schedule standards.
The AS IT team performed well in the area of personnel training to improve the interaction with the company’s system and boost the speed of the operation process. Such work and progress minimize human error risk, which can also cause system breakdown and data loss. The effort resulted in the AS company having a workforce of a broad skill base: design engineers, programmers, machinists, and assembly personnel to work its highly-automated production systems. These employees ensure a smooth and productive interdepartmental communication as well as clear and quick correspondence between the business and its customers. Nevertheless, other threats related to external forces like cyber-attacks and natural disasters remain a problem, which can lead to devastating outcomes. Firewall check and update policy is a common vulnerability that attackers use, so measures stated above are necessary and should be adopted as soon as possible (Karoui, 2019). In addition to this vulnerability, natural disasters, emergencies, and other external forces continue to pose a threat to AS, especially due to the company’s geographical location and type of business. As Karoui (2019) noted, “the most important components of an IS are … servers and databases”, so emphasis should be made to address the current risks related to the protection of AS databases and servers. It is vital for the AS company as it uses the system on a daily basis.
The NAS devices that are being used by AS can be replaced by a more secure to environmental and physical risks backup method. Iperus company, which provides storage and backup solutions, has an off-site dedicated server for data backups, a license for which can be purchased (The professional remote backup storage, n.d.). This strategy can become a great solution in ensuring timely backups that are independent of location and space. Using Iperus remote backup storage server can considerably expand the database, allowing for the company’s future growth. An optimal solution would be purchasing the Iperus Storage 1000 for a little over $600 per year, which includes 1 TB of storage space and unlimited device connections (The professional remote backup storage, n.d.). This remote storage hardware would be connected to the separate database server in the AS network infrastructure, as seen in Figure 1. The critical aspect of the service agreement with the Iperus Company would be ensuring complete confidentiality and safety of the stored data, preventing any unauthorized access, not compliance of which would lead to legal consequences and compensation.
There are other data backup options apart from using the Iperus remote storage, but they are vulnerable to the same risks as the currently used NAS. Commonly known advancement from NAS is purchasing and introducing an additional local file server for database backup (Iperus Backup C., 2020). This method offers a business or a company with the biggest storage increase opportunity compared to NAS and off-site options (Iperus Backup C., 2020). Installing a file server for data backup can be beneficial when a future expansion and new office location openings are planned because it significantly enlarges the memory size. It is also easier to operate than NAS due to better software compatibility (Iperus Backup C., 2020). However, it is also much more expensive and requires large office space, which should be carefully considered (Iperus Backup C., 2020). Since a local server is still installed on-site similar to NAS, it is vulnerable to the same natural disaster, and emergency risks like fire, floods, and earthquakes frequent in Southern California (Iperus backup C., 2020; Legislative Analyst’s Office [LAO], 2019). In terms of security, space, and cost, the use of Iperus remote storage for database backup is better than the local file server and NAS.
Poor resource management leads to business security risks, which can become fatal for a company. Brown (2018), for instance, writes: “When it comes to budgets, businesses are doing one of two things: they’re either spending their budgets in the wrong place, or they are buying a tool and expecting security in return” (p. 10). Similar to this statement, the AS company expects to minimize the threats of cyber-attacks and network vulnerabilities only by having the IT team operate outdated firewalls and insecure server backup hardware. These measures are not enough as the system requires proper updates and maintenance to effectively protect a business (Brwon, 2018; Karoui, 2019). In order to fulfill its mission of providing customer success through machined products and related services, and meeting cost, quality, and schedule requirements, AS should reevaluate the company’s information system security budget. Thus, the company will be able to establish long-term relationships and secure repeated follow-on business with its customers.
Although the two previously mentioned solutions will be beneficial for AS, they require additional funding and resources. These financial costs might lead to an increase in production expenses and product prices. Nevertheless, network and data security will be ensured and guaranteed, which will enhance business and customer bonds and establish a long-lasting relationship. These measures are necessary to prevent unwanted damaging cyber-attacks and minimize overall vulnerability. No additional staff training is required as the actions outlined are only related to the AS company’s IT team. The two solutions effectively respond and address the need for system security, considering the contemporary state of network attacks and the company’s environment.
References
Brannon, B. (2019). Why it’s important to review firewall rules on a quarterly basis. Safe Systems.
Brown, T. (2018). Are miserly budgets putting businesses at risk of cyber-attack? Computer Fraud & Security, 2018(8), 9-11.
Iperus Backup C. (2020). File server backup vs NAS storage backup.
Karoui, K. (2019). Risk analysis linked to network attacks. In W. Tounsi (Ed.), Cyber-vigilance and digital trust: Cyber security in the era of cloud computing and IoT (pp. 105-140). John Wiley & Sons.
Legislative Analyst’s Office. (2019). Main types of disasters and associated trends.
Sager, L. (2019). Natural disaster risk areas and population in San Diego: How does the potential for various natural disasters affect population density?
The professional remote backup storage. (n.d.) Iperus Storage.