Introduction
In the modern digital world, data holds significant value. Cybercrime is one of the biggest threats to businesses and companies strive to protect digital assets. Cybersecurity is a critical part of business infrastructure, aiming at protecting consumer data, proprietary information, financial data, and potential security threats, among others. Virtually every business today has technical elements that either supplement or are critical to a company’s operations. These are becoming a target for cyberattacks and hacks due to the high profitability of data for cybercriminals and their evolving ecosystem. Businesses carry the burden of protecting their infrastructure with both technological and human component safeguards in cybersecurity. It has become not simply an IT issue of the past, but a strategic business problem. However, the complexity and sheer requirements of effective cyber security pose numerous challenges to businesses. Challenges to cyber security for business stem from human factors expanded opportunities for cyberattacks, vulnerable infrastructure, and regulation complexities all of which must be considered and managed when developing effective and comprehensive cyber protection strategies.
Background
Cyber security can be defined as the protection of valuable intellectual property and business-related data in digital form against theft and misuse. It is a critical management issue and cybercrime has been identified by the U.S. government as a serious economic and national security challenge. Cybercrime can take on various forms, ranging from cyberattacks in the form of hacking, distributed denial-of-service (DDoS) attacks, or malware to the release of sensitive information or fraud. Certain trends are resulting in increased cybercrime and simultaneous cybersecurity efforts by businesses. In the modern-day, most transactions are conducted online, alongside tremendous data mines on the transaction, consumer information, market data, and product development data which makes it financially attractive to cybercriminals. Supply chains, as well as mobile devices, are all interconnected within the same networks for accessibility and efficiency, but also reveal numerous vulnerabilities due to ease of access for hackers if a device is compromised (Kaplan et al.).
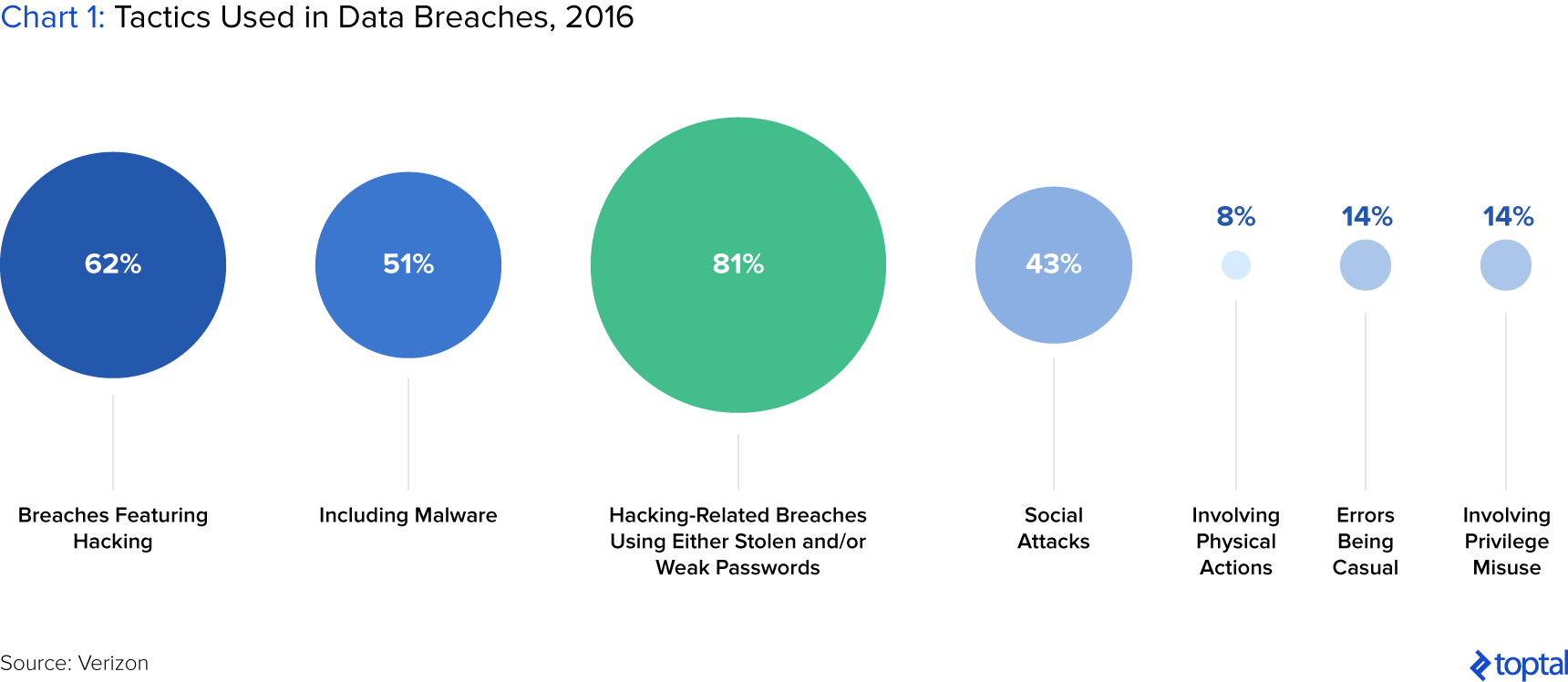
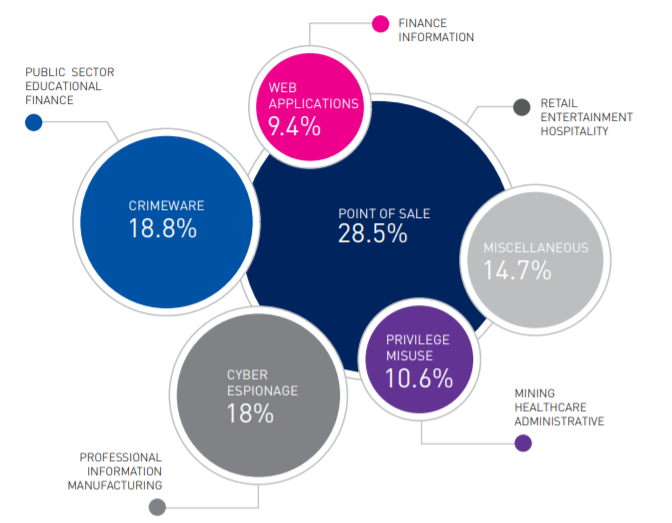
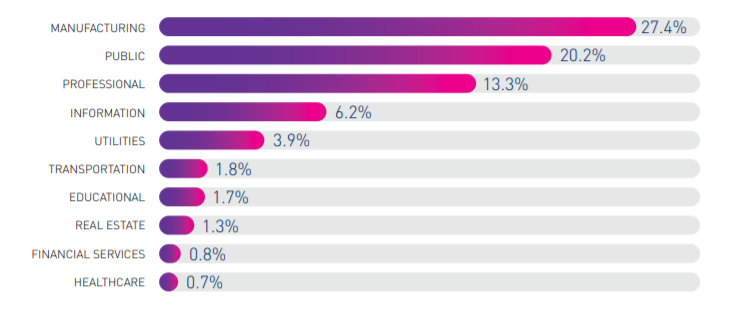
Furthermore, malevolent actors are becoming increasingly sophisticated, ranging from professional cybercrime organizations to state-sponsored groups and political hacktivists, all of which target major businesses with their intentions. These malevolent actors often outpace corporate cybersecurity teams in technology and methods as they consistently develop more complex malware or advanced targeted attacks while cybersecurity relies mostly on response, which puts it at a disadvantage (Kaplan et al.). Cybercrime is prevalent, costing U.S. businesses $3.5 billion in 2019 according to the FBI with more than 1,300 complaints daily. However, it is estimated the costs are much higher, as much as $9 billion annually due to businesses often weary to report exploitation of their systems and most ransomware incidents are silenced (Reynolds). Small- and medium-sized businesses (SMBs) which lack the sophisticated security infrastructure are also commonly targeted, costing on average $200,000 per incident, with as many as 60% going out of business after an attack (Steinberg). Virtually all sectors are affected, and each industry faces unique cybercrime challenges that target valuable data in its networks as shown in the charts below.
Some of the most difficult cyber attacks exploit human vulnerabilities rather than technological gaps. While technological vulnerabilities are easy to correct and remediate, human behavior is not, and remains both predictable and easy to manipulate. Criminals often engage in so-called ‘social engineering’ where a person’s connections and social behavior are analyzed to create highly targeted ‘phishing’ attacks. These entice an employee to click on a link or download a file that either inserts malware into the corporate network or spyware that can identify login credentials for further exploitation (Kaplan et al.).
Another aspect to consider as a category of threats are current or previous employees that are disgruntled with the organization or motivated by financial gain to launch attacks. Having current or recent authorized access to the company’s network or system can be easily misused to negatively affect confidentiality, integrity, or availability of the information systems. However, with proper mechanisms, insider threats can be detected and caught (Hadlington 48). Much less predictable are the factors of poor planning, ignorance, and lack of attention which lead to the rise of the ‘accidental’ or ‘unintentional’ insider without any malicious intent, but just as damaging to the business. Such failures can be caused by pressures of the job, task difficulty, lack of knowledge, or cognitive factors. These actions are of a greater security concern for the organization because they are random without direct motive or prior indicators that can be predicted. Furthermore, unintentional insider threats are taken less seriously by IT security professionals and executives, likely due to a lack of research and belief that technical solutions alone can mitigate the issue (Hadlington 51).
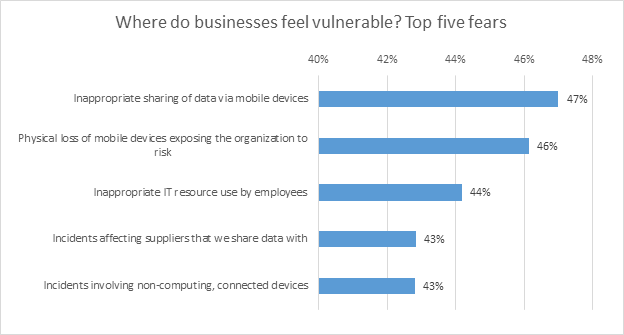
The human factor often plays a major role in making businesses vulnerable, with the non-IT personnel being the weakest link. Some prominent examples of such behavior include failing to update operating systems with the latest security patches, disabling security solutions on work computers, or opening suspicious emails. This internal risk comes from either the employees being incompetent or uninformed with actions such as inappropriate sharing of data via mobile devices, physical loss of a device, and inappropriate IT use. All of which leaves gaping opportunities for cyberattacks by malevolent actors that are difficult to protect from even with the best technological cybersecurity systems (“The Human Factor”).
Another human-related factor to consider in terms of challenges to business cybersecurity is a lack of qualified cybersecurity and IT talent. It is a critical issue in the sector, with a large workforce with generic IT skills, but few experts that are capable of protecting organizational networks from sophisticated networks. Unfilled cybersecurity positions are expected to reach 1.8 million in 2022, and the issue doesn’t stem from lack of formal education but rather due to often underpaid low-level employees and lack of investment by organizations and educational institutions to offer relevant skills in cyber security (Mickos). The cybersecurity expert shortage is exacerbating the number of data breaches. Furthermore, the lack of availability of highly competent professionals is creating a surge in costs of developing cybersecurity protections or hiring such individuals to the company, that only large enterprises can afford, leaving smaller businesses more vulnerable.
Expanded Attack Opportunities
As mentioned earlier, the transition of firm operations to online networks provides ample opportunities for cyber-attacks. The Internet of Things (IoT) envisions an interconnected autonomous network of devices and services that has a wide distribution, openness, and high processing power that presents it as an ideal target. More and more companies and homes are operating on the IoT principles and networks, as various nodes and points of entry are collecting and processing private information on employees and consumers. It becomes a data goldmine for malicious actors (Conti et al. 544).
With Internet penetration reaching 3.4 billion or at least 46% of the global population, opportunities for cybercrime have increased exponentially. The nature of cybercrime threats is multifaceted, and the tools and scopes of attacks vary significantly. It is an issue that is compounded by what is known as an attack surface, the initial size of a vulnerability. If a hacking exploit was found for Apple iPhones, and it is the official work device for business employees, the attack surface range increases as anyone with the device is vulnerable. Hardware and software provide multiple vectors for attacks, and vulnerabilities in both can be used in tandem to hack a device. Even in highly secure embedded systems such as those that power infrastructure or communications, attacks are possible, commonly with targeted and system-specific malware. The sheer scope of cyber threats and the fact that anything controllable by technology has a vulnerability makes cybersecurity challenging in fending off numerous points of attack on systems and networks (ACS).
Vulnerable Infrastructure
A critical evaluation of technology poses a question as to why the vulnerabilities exist in the first place. From the early days, protocols driving the Internet and other networking technology were not designed for a future where they would be targeted for exploitation. Despite much greater awareness of the issue in the modern-day, several devices or networks lack a security-focused design, lacking the consideration that it will be misused for nefarious purposes (ACS). In the context of digitized infrastructure, the focus is directed at creating improvements in efficiency or customer experience driven by new technologies. However, cybercriminals often operate in uncovering how new technologies share the same vulnerabilities of previous generations. Approximately 54% of exploited vulnerabilities in business networks in the recent year were publicly known for the past decade or more, essentially allowing for slightly modified attack patterns to work over generations of technologies (Kaplan et al. Critical Resilience).
The foundation of modern business operations through the IoT and the cloud also becomes its biggest vulnerability due to the numerous possibilities of attacks discussed earlier. Enterprises enabled server virtualization in the last 15 years without an appropriate risk assessment and with total reliance on vendors, believing that private cloud services were completely safe. IoT only further promotes vulnerability by encouraging the use of webs services, multitiered applications, distrusted databases, and trends for virtualizations. This new technology brings more ways to access new types of devices as alternatives to work personal computers and mainframe platforms, which was welcomed by businesses for its comfort and efficiency, but the technologies often lack the initiatives for proper controls of timely cybersecurity functions (Sharkasi 3). Cloud services have become popular due to cost-saving that transitions security costs on the vendor, but the centralized point of data makes such servers highly viable for the attack as well as the potential for establishing a backdoor that can compromise internal company networks (ACS).
Complex Regulation
One challenge that should be considered in the cybersecurity context is complex regulation. The regulatory environment in the sector can complicate cybersecurity efforts due to being outdated, lacking consistency, and requiring loopholes. One prominent example is the General Data Protection Regulation (GDRP) enacted by the European Union, which seeks to protect consumer data but creates numerous hurdles for businesses, that will negatively affect SMBs. Higher standards should be instituted, as they are with the GDRP, but it should be done in a way that allows all businesses to actively operate in a virtual environment, safely and legally. Various legal frameworks regulate cybersecurity and data protection in various industries. For example, HIPAA audits healthcare organizations to ensure compliance and protection of electronic health records (EHR). Meanwhile, the Sarbanes-Oxley act is a government law that regulates financial institutions. The issue is that with regulatory frameworks being vastly different and often outdated, it is challenging for cybersecurity efforts to build a unified and strong defense against the cyber infiltration of organizational systems (Cohen).
Strategies
To address the complex challenges described in this paper, it takes more for companies than simply hiring IT talent or building a strong system. The majority of organizations approach cybersecurity by creating sophisticated defenses around their networks. While these are important along with the most basic security functions such as two-factor authentication and strong passwords, a motivated hacker will likely find a vulnerability, or an opening will be created inadvertently by an employee. The most progressive companies reorient security architectures from focusing on devices and locations to data and role access. For example, one can use the Internet from a work laptop, but access to corporate data will require authentication of identity which is much harder to falsify by malicious actors. Cyber security is becoming a fundamental design element of technology architectures, with databases no longer holding all the single points of data or entry. For example, there is a limited number of people with access to production systems and data, as well as separating critical information such as credit card numbers and expiration dates on different servers, greatly complicating hacking efforts or usability of the data if only one piece of information is available (Riel et al. 173).
Companies must take an innovative approach to address cyber risks. New strategies must be developed that address the business aspect specifically. For example, instead of focusing on technological vulnerabilities, the most critical digital assets or processes should be protected first, such as customer data. This is known as the ‘business back approach. It has shown to be successful as large companies have implemented massive long-term programs to classify vital data and focus cybersecurity efforts on information assets. Businesses should also evaluate cybersecurity risks across the supply chain since as earlier discussed, the IoT results in the interconnectivity of networks and ease of access. Companies enhance cybersecurity collaborations with vendors and partners, ensuring protection across the board, and helping smaller enterprises that are unable to afford competent cybersecurity. Finally, it may be viable to address the concept of data collection on consumers, which is valuable from a business perspective in some ways but creates numerous risks. Businesses must find a balance between data and cybersecurity, being potentially just as profitable as end-to-end customer experiences are created that are efficient and secure (Kaplan et al.).
Conclusion
Protecting a company’s technology assets from malevolent actors and malicious damage either intentional or due to inappropriate use requires an intelligent approach to safeguards and constraints. Undoubtedly all stakeholders in an organization will be affected ranging from management and employees to clients and partners – anyone that uses or has access to corporate applications and data. Cybersecurity is inherently complex with its numerous challenges of the human factor, infrastructure vulnerabilities, and even regulation. There are divisions on how cybersecurity should be approached. Insufficient safeguards will result in economic loss and compromise of data, but unlike government institutions, businesses cannot afford to create stringent controls as it would interfere with growth and innovation. A business-driven cybersecurity model is required that will offer flexible resilience to organizations to deter highly skilled malevolent actors. Eliminating all threats is difficult but protecting against them without disrupting business operations is a vital issue in corporate cybersecurity.
Works Cited
ACS. “Cybersecurity – Threats, Challenges, Opportunities.” The Professional Association for Australia’s ICT Sector, 2016. Web.
Cohen, Natasha. “The Evolving Cybersecurity Regulatory Environment: Tracking Current Trends and Staying Ahead of the Curve.” Columbia Journal of International Affairs, 2017. Web.
Conti, Mauro, et al. “Internet of Things Security and Forensics: Challenges and Opportunities.” Future Generation Computer Systems, vol. 78, no. 2, 2018, pp. 544-546, doi.org/10.1016/j.future.2017.07.060
Hadlington, Lee. “The ‘Human Factor’ in Cybersecurity: Exploring the Accidental Insider.” Psychological and Behavioral Examinations in Cyber Security, edited by John McAlaney et al., IGI Global, 2018, pp. 46-63.
Kaplan, James, et al. “Critical Resilience: Adapting Infrastructure to Repel Cyberthreats.” McKinsey Digital, 2019. Web.
—. “Meeting the Cybersecurity Challenge.” McKinsey Digital, 2011. Web.
Lin, Melissa. “Cybersecurity: What Every CEO and CFO Should Know.” Toptal Finance. Web.
Mickos, Marten. ” The Cybersecurity Skills Gap Won’t Be Solved in a Classroom.” Forbes, 2019. Web.
Reynolds, Conor. “Cybercrime Cost Business $3.5 Billion in 2019, Says the FBI: It’s Likely a Massive Underestimate.” Computer Business Review, 2020. Web.
Riel, Andreas, et al. “An Architectural Approach to the Integration of Safety and Security Requirements in Smart Products and Systems Design.” CIRP Annals, vol. 67, no. 1, 2018, doi.org/10.1016/j.cirp.2018.04.022
Sharkasi, Omar Y. “Addressing Cybersecurity Vulnerabilities.” ISACA Journal, vol. 5, 2015, pp. 1-11. Web.
Steinberg, Scott. “Cyberattacks Now Cost Companies $200,000 On Average, Putting Many Out of Business.” CNBC, 2019. Web.
“The Human Factor in IT Security: How Employees are Making Businesses Vulnerable from Within.” Kaspersky Daily. Web.