Determining The Client’s Security and Privacy Needs for the Database
Identification and Definition of the Current Problem
Schumer Company is a private company that specializes in providing online services through its ecommerce platform, where it sells cosmetics to the public. Founded in 2008, Schumer Company is a mid-sized business with about 400 employees and annual revenue of over $400 million as of 2020. With more than 80 outlets across the country, the company boasts of an integrated customer relationship approach that involves its clients in an online business and customer support system. Currently, the company has advanced customer relationship software that manages its customer affairs, provides feedback, and analyzes customer responses on various issues and products.
In an effort to improve its customer base, Schumer Company has approached its internal information technology team authorizing the technicians to mock up an ecommerce solution. The idea is to provide a 24/7 availability and over 99% uptime for its customers. In addition, the IT team is requested to analyze the cons and pros, costs, and benefits of site services versus the infrastructure a service (IaaS) cloud solution. The company chief executive has commissioned the IT team to accomplish these tasks with the aim of developing a better understanding of the effect that the transition will achieve on the performance of the ecommerce platform.
The most important requirements are that the new system must be cost-effective, user-friendly, and provide the expected return on investment within the first five years of use. According to the plan, the company has set aside a budget of $100,000 for the project and the team is instructed to start conducting research on the cost of a cloud solution. The company chief executive wants the team to complete the mock-up within the next four months.
Problems and Issues
Schumer Company’s current ecommerce system is more than ten years old and is already a problem because of the dynamic nature of ecommerce. Specifically, the company runs a brick-and-mortar store in which sales representatives take orders from customers placed via telephone and emails and then manually enter them into the order system. In addition, Schumer Company has onsite servers that are already out of the life cycle. With an increasing online order due to the evolving ecommerce, the work is already becoming stressful for the staff and highly ineffective. Indeed, for the last one year, orders have increased tremendously as the need for online purchases increased due to the current policies that restrict movement due to the Covid-19 pandemic.
Objectives
The Schumer Company wants to provide a 24/7 availability and over 99% uptime for its customers. In addition, the company wants to analyze the cons and pros, costs, and benefits on site services versus the infrastructure a service (IaaS) cloud solution. The new system ought to maximize and optimize the security and efficiency of the database. In this case, the key users of the new system will be the staff, vendors, and the customers who place orders online via the ecommerce platform. Research and implementation of the database will be the role of the database security manager.
Requirements
The Schumer Company’s executives want the IT team to conduct a comprehensive research study and recommend a data input strategy through the web interface design, after which a cloud solution and secure database solution will be ultimate goals. In this case, the resolution is expected to include a CRM implementation that will keep track of the company’s needs and the customer’s needs as well.
Constraints
Currently, the budget allocated is limited to $100,000 and the company expects the results to be achievable within one year. In addition, the mock-up is expected to be achieved in the next four years. Furthermore, the new version should provide ROI within the first five years of its application for Schumer Company. The IT team, upon a preliminary investigation, has decided to settle on agile scrum methodology to develop and test the version.
Description of the Proposed System
The IT team has proposed that a web developer be included in the process to help establish the interface. Schumer Company IT team will have the responsibility of maintaining the physical security of the new version.
Logical Model
The system architecture follows the conventional applied by most developers. Specifically, it will consist of a client web interface and the back end database established and hosted by Oracle using the IaaS platform, as shown in Figure 1.
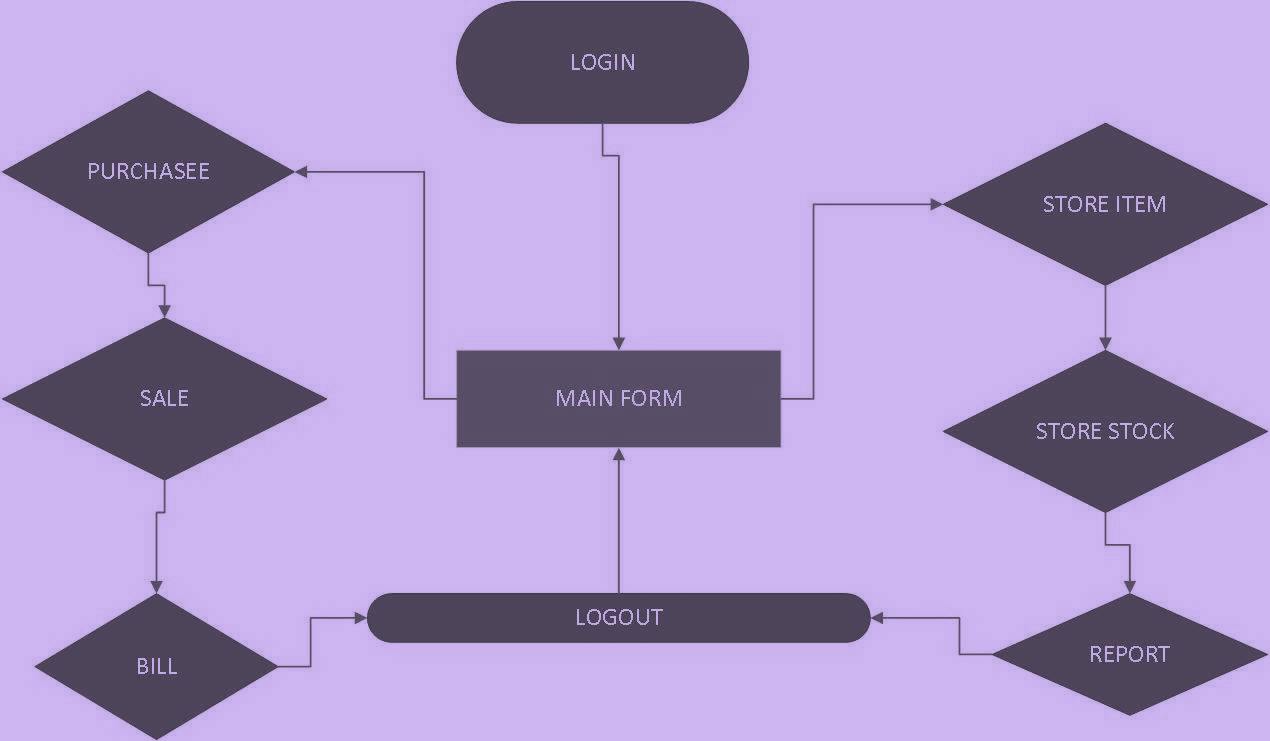
Context Diagram
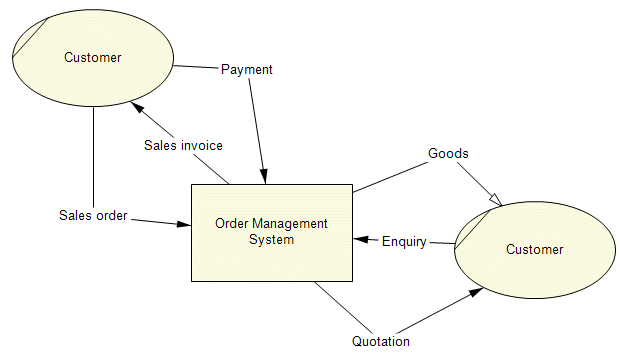
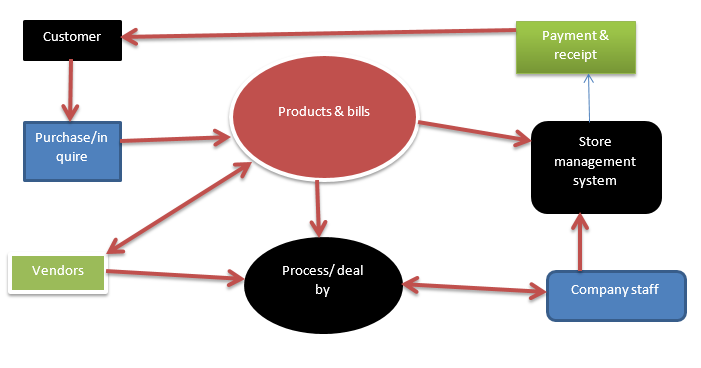
The Schumer Company has warehouses where they stock their inventory after receiving from the wholesalers and manufacturers who are their suppliers. Customers will only need to log in using the online interface on the website, create an account in a simplified way that allows them to provide their usernames, email or mobile phone number, and a password. Then, they are allowed to access the platform where they can browse through the available products, read the details, compare prices and other aspects of the products, create baskets for products, shop, and place orders. Then, the system will generate a bill for the ordered products and the customers will authorize by clicking the “order now” button.
The bill is then sent to the shipping department at Schumer Company for processing by the staff. However, it is worth noting that the system can allow customers to purchase as visitors without the need to create an account. The idea is to ensure that customers who do not wish to create an account for various reasons are also allowed to make purchases.
After completing the process, the application will enable the purchased order to be shipped from Schumer Company to the clients. Each customer will be given an automatic customer ID, a unique identifier provided to all customers, including those who purchase as anonymous visitors. The aim of this protocol is to ensure that the customers have their details protected at all times. It is the role of the staff and administrators to control the overall system.
High levels of error correction and input validation will help correct issues related to customers. The staff and administrators will use the Common Access Card (CAC) as well as the Personal Identify Verification as a means of identification when accessing the database. Different roles will be assigned to the different users based on their intended functions at the company such as vendors, staff, and administrators. Inventory will always be uploaded to the database using the current methods but the new database will exist in the cloud contrary to the current system that uses in-house servers.
Risk Assessment
After a preliminary research study, the IT team has decided to use the cloud platform instead of the current in-house servers. Noteworthy, cloud platforms are safe for the data compared to in-house servers that can be damaged by humans or natural disasters. In addition, a cloud platform is easily accessible, has mobility, and high productivity. Based on the pros and cons, the team has decided to settle on the SaaS system architecture and the IaaS software service. It is expected that the system will need frequent reviews, modifications, and updates as time goes and the ecommerce business matures.
Analysis of Pros and Cons
The new version has a number of advantages over the in-house services. First, it is cost-effective, especially because there is no need for upgrading and changing services frequently. In addition, it is almost 100% available, scalable, reliable, flexible, customizable, and agile. Scaling up and down will only require a few minutes to achieve. Moreover, it is proved effective in increasing revenue, meet the company targets, and improve the relationship with the customers.
However, it has some disadvantages associated with its design and applications. For instance, the company IT team will still be responsible for patching the services even though they are cloud-hosted. Secondly, it will incur some resources such as when transferring the legacy applications to the new providers.
Security Policy
The company will need to educate the end users as well as developers and maintenance team to eliminate insider threats to the database. Secondly, there will be encryption of the data to protect information at all times. Furthermore, to block threats and damages, there will be proactive database and network monitoring by the IT team and administrators.
To reduce risks of privilege escalation, the IT team has decided to apply the concept of least privilege, revoke unnecessary privileges, run and review reports displaying provides, roles, and permissions, and activate privilege capture mode functions. Furthermore, the team has decided to use a database firewall that will monitor logs and traffic and SQL injection. The firewall will also detect unauthorized activities on the database and help implement both backlist and whitelist rules.
The policy will further apply data masking, redaction, and fine grained access control measures. The aim is to protect sensitive information through redaction of all account numbers except the last four digits. In addition, it will help mask data programmers who are to use dummy data rather than the real information.
To support the security plan, there will be additional securities that Schumer Company must always implement. First, entry into buildings within the company’s premises will require the staff to have smart cards or finger identification to open locks on doors. Therefore, there is a need to train the users about the security such as making sure that they never allow any unauthorized parties to enter the buildings without authorization. Third, computers in the premises as well as those that workers use remotely at home will have antivirus software systems to protect intellectual property. Users will receive training on the importance of knowing how malware, viruses, and ransomware where work and how to avoid them in their computers. At all times, uses will have to use unique login details such as usernames and complex, strong, and unique passwords. Again, they need training on how to develop such passwords and the importance of ensuring that they do not expose or share them with another party, including colleagues, administrators, and others.
For the security model, the company is advised to apply web applications that will help achieve the above objectives. Specifically, the team has settled on Virtual Private Database (VPD) security. For employees, the company should use Common Access Cards (CAC), Personal Identity Verification (PIV) along with Oracle Label Security (OLS) and Role Based Access Control (RBAC). Moreover, the company should implement RBAC and Discretionary Access Control (DAC) on the file servers.
The IT team will have to create roles and permissions and assign each to the roles. Since different groups of users need to see only certain information only, the IT team has decided to instantiate views to ensure that there is an additional security layer. In this case, different users must be placed in specific groups with distinct permissions. The idea is to ensure that only the relevant information is accessible to each group of users such as developers, administrators, the staff, vendors, and customers. It is recommended that network monitoring tools like SolarWinds Network Monitor be used to identify all permissions that users have on the network. The idea is to help lessen privilege escalation as well as assist with the implementation of a least privilege policy as described above.
Reference
Tilley, S. (2019). Systems analysis and design. Cengage Learning.