Abstract
Corporate identity thefts involving unauthorized drawing of vital client information is currently on the rise as the most prevalent type of computer crimes. Processing of large volume of personal data, without proper security protection mechanisms make organizational information base vulnerable to malicious attacks by both external and internal agents. Based on a quantitative questionnaire survey method, this research identified theft/disclosure of corporate information and virus attacks as the most common form of security threats. Access control and firewalls are found to be the most common form of information security measures used by the corporate undertakings. Suggestion to compare the quantitative damages in case of potential security threats to organizational information security and the cost of installing appropriate protection mechanism is recommended.
Introduction
Proliferation of e-commerce has made the global business transactions easier and convenient. The consumers have found a comfortable way of purchasing goods and services through e-commerce using the internet as the medium. With the continued growth of internet along with technological developments and large volume of sales the crime of computer fraud has also become an issue larger in magnitude than the experts ever imagined. In modern times, sophisticated professionals have turned to be cyber criminals who have chosen to use their talents for fraudulent purposes. With their professional knowledge and skill these professionals get access to advanced software which enables them to activate computer systems of others to retrieve any sensitive information they can use for illegal purposes. The highlight of such an event is that the user may not even know that his/her computer system has been subjected to fraud. In this context this research extends to computer frauds and protection of information security.
Information Security – an Overview
Generally, organizations are concerned with the threats and vulnerabilities to their information systems and resources from the purview of confidentiality, integrity and availability (Gollmann, 1999; Pfleeger, 1997; Sebastian et al., 2003). Information security covers any action designed for the protection of information and information systems within an organizational context (Gordon & Loep, 2006). Information security relates not only to the information content but also to the entire spectrum of infrastructure that facilitates the flow and storage of information. Thus, information security is concerned with hardware, software, threats, physical security and human factors. It is to be appreciated that each of these components of information system has its own characteristics which has an influence on the overall information security. With the increased use of advanced information technology and internet, the role of information security has become overwhelming. With the increase in the number of security breaches in the commercial and government organizations and more accessibility to the information, there are increased threats to the security of information (Brown & Duguid, 2002).
Computer security as an integral part of information security is a general term that encompasses a wide range of processes involving computing and information processing. Business organizations that depend on different computer systems and networks for transacting their daily business dealings and for accessing crucial information consider their data as an important part of their overall assets. In the case of some industries like electronic commerce industries, the success or failure of individual organizations depends largely on the availability and trustworthiness of data. The issue of managing information security has taken the centre of focus with the increase in the magnitude and capacities of the networking facilities. The increase in networking facilities has put the information security at a very high priority especially in the wake of increased cyber crimes that are being perpetrated largely. Private business houses like those engaged in providing financial and investment services to their customers and several other customer centric business establishments carry a large amount of vital data pertaining to their valued clients in their computers, which are always subjected to the vulnerability of data and identity theft by unscrupulous hackers and perpetrators of cyber crimes. Thus, in the present highly mechanized business environment development of secure identities is one of the issues of critical importance for the protection of information and data stored in the computer systems. One type of computer crime as identified in the recent surveys is the perpetration of frauds on information technology and information systems (Graycar & Smith, 2002).
The proliferation of the Internet as the largest means of communication has led to the availability of a number of avenues for illegally breaking the security of information and to access them for illicit uses. Organizations both private and governmental face overflow of security threats both known and unknown from any possible source. The threats may emanate from outside the organization’s premises through people known as hackers. The hackers often make attempts to invade corporate networks for monetary gains or just for fun. They also use programs which use the network vulnerabilities to extract information or obstruct the smooth information flow. Organizations protect their information networks and systems from unauthorized intrusion using several techniques. Firewalls and anti intrusion detection systems are some of the commonly adopted techniques. The information stored in the computer systems of any organization is subjected to the risk of disclosure by the employees either by mistake or intentionally.
With the increase in the potential information security threats from worms, viruses, and hackers coupled with the adoption of open system architecture to facilitate e-commerce, security professionals have been trying to find suitable solutions for meeting the challenges posed by these real threats. However, it needs to be understood that there is no single solution in the form of technology or methodology that will meet with the security needs of the corporate entities. Effectively securing data and other assets, calls for a holistic approach that covers all aspects of security including systems architecture and other policies and procedures in addition to educating the users. The holistic approach encompasses not only engaging the right solution but also getting the entire organization embrace a security state of mind.
Implementation of a holistic security strategy involves making the organization a business centric security process from a technology-centric entity. This process involves assessing risks and managing potential threats.
A secure environment is an important element of meaningful knowledge management. Knowledge represents an important asset of any organization signifying the need to protect it securely. The security is to be applied both within and outside the organization. However, information security is not perfectly secured by nature and is always vulnerable to breaches. Therefore, organizations cannot completely eliminate the danger of misusing the information by applying a single solution. It is necessary to arrive at a level of information security suitable to particular situations. The organization should decide on the level of security as a proportion of the value the information possesses. The potential loss that may arise to the organization because of the misuse of information should also be considered in deciding the level of security. This substantiates the statement that information security is about risk management.
Aims and Objectives
This research aims to make an overall review of the corporate identity frauds and the protection of loss or misuse of information from such corporate identity frauds. In order to achieve this overall aim, the research undertakes to accomplish the following objectives.
- To have an overview of information security at corporate level to understand the nature and ways of ensuring information security;
- To identify and study the features of most common corporate identity frauds;
- To study and present an overview of the nature of crimes associated with corporate identity;
- To study the existing ways of safeguarding information security and to make a critical analysis of the current solutions to information security;
- To make a risk assessment with the emphasis on cost, social effects and corporate effects.
Significance
Information security clearly establishes the setting for the creation and use of more comprehensive approach to the creation of information security systems that can guarantee the protection to the security of information (Cranor & Garfinkel, 2005). This presupposes the necessity of creating and using better security systems to ensure basic security of information stored in the computer systems. This has made the study of the salient features of the security aspects relating to the creation and use of meaningful information security systems an important one. Past research has identified that improperly used or badly designed protection systems are one of the major causes for information security concerns (Tari et al., 2006). Ultimate purposes of computer fraud is either financial and many other resources and privilege gains which might affect the reputation of an organization. Computer frauds and corporate identity thefts may lead to financial and criminal repercussions of significant impact. This has necessitated a reexamination of the existing information security systems to comment on their shortcomings and at the same time to suggest new systems of information security so that the information remains secure. Thus, this study has taken the objective of critically examining the computer frauds and corporate identity thefts and the ways of protecting these identities and to suggest any possible improvement in them.
Structure
In order to present a comprehensive and cohesive analysis, this paper is structured to have different chapters. The first chapter introduces the topic of study and details the aims and objectives of the research. The second chapter reviews the available literature on computer fraud and corporate identity thefts. This chapter also details the research methodology chosen to complete the research. While the third chapter presents the findings of the research and an analysis of the findings, chapter five is the concluding chapter which also contains few recommendations for further research and an evaluation of the research undertaken.
Literature Review
Introduction
The following finding of a recent study brings out the magnitude of computer crimes in relation to business organizations.
“the complexity of modern enterprises, their reliance on technology, and the heightened interconnectivity among organizations that is both a result and a driver of e-business—these are rapidly evolving developments that create widespread opportunities for theft, fraud, and other forms of exploitation by offenders both outside and inside an organization” (KPMG, 2000).
Computer frauds have been one of the major concerns for all types of organizations, whether public or private. The computer crimes have also affected consumers, regulatory agencies and the society in general. A survey taken in the United States during the year 2002 has identified that more than 90% of the organization out of the 500 participants have experienced computer security breaches within the last one year (Power, 2002). Investigations conducted on similar lines in Australia have also revealed that computer frauds occur at somewhat lower levels compared to US; however there is an increasing trend observed. Investigation conducted by Australian Computer Crime and Security Survey reports that the security breaches have doubled during the period between 1999 and 2002 and during the year 2002, 67% of the organizations participated in the survey have experienced computer frauds (Power, 2002).
A number of reasons are attributed for the proliferation of computer frauds. These include the increase in the connectivity within the community and increased use of internet services gives more opportunities for perpetrators of frauds. The complex nature of the recently developed computer software makes them open to different types of attacks, easily performed by the hackers. The attackers have abundant chances of getting malicious codes and tools which enlarges the opportunities for computer frauds. Increased use of high speed internet access provided for home users with the aid of cable modem or DSL with their lesser security capabilities provide the necessary bandwidth and availability for the attackers to indulge in more crimes. The rates at which technology changes take place increase the rate at which the computer frauds are committed. The slow pace of adoption of established safety practices by the users as against the range of connectivity and use of internet by them is one of the most important reasons for increased rate of computer crimes. One of the most common types of computer crimes is concerning the information technology and information systems engaged by any organization. Power found that the rate of computer crimes having financial implications have doubled from 3% of the participants in a 2000 survey to 6% of the participants in the 2002 survey in the context of the United States. The cost of these frauds has been found to be disproportionately high in the overall cost of all computer frauds. This trend has necessitated identifying and installing suitable system-centric security applications to prevent the occurrence of frauds and unauthorized access of information for illicit uses.
Methodology
Research Philosophy
Social science research follows several research methods to collect information and data relating to the issue under study. Ontology and epistemology enables the formation of the basic framework for many of the social research methods. The term ontology is defined as a branch of philosophy concerned with communicating on the environment and arrangement of the world (Wand & Weber, 1993). Ontology thus is concerned with what is said to be in existence in the real world. The ontological questions always try to find the arrangement of worldly truth and the things that need to be learnt about the real things in the world.
On the other hand, epistemology talks about the nature of human knowledge and understanding (Hirschheim et al., 1995). This philosophy advocates that such knowledge and understanding can be acquired by employing various types of inquiry and alternative methods of investigation (Hirschheim et al., 1995). According to Guba & Lincoln, (1994) the inquiry paradigms can be considered in ontological, epistemological and methodological questions. The methodological questions decide the ways in which the researcher can proceed to find out what he or she believes that can be known about the existing things in the world. The research methods generally follow:
experimental,
correlation,
natural observation,
survey,
case study methods.
The researcher must evolve a suitable research design specifying the research method the researcher intends to follow for completing the study. In choosing the particular research method to be followed, the researcher has to take into account a variety of variables like the subject matter under research, and the range of interests of the researcher, difficulties involved in accumulating the time and resources and other funding issues. The major classification of the research methods takes the form of qualitative and quantitative research methods.
Considering the nature of the current research to assess the necessity of using information security techniques and tools by the corporate entities, use of epistemology was considered appropriate. Since epistemology is concerned about the ways in which the human actors would act to inquire and acquire knowledge on things, which really exist in the world, this research proposes to follow an epistemological approach. Moreover according to Hirschheim et al., (1995) since epistemology talks about the nature of human knowledge and understanding and that such knowledge and understanding can be acquired by employing various types of inquiry and alternative methods of investigation this research proposes to use an epistemological approach.
During the process of this examination, the research will also extend to analyzing the salient features of information security and the impact of computer crimes on corporate identity theft issues. This includes the study of various techniques including firewalls and intrusion protection systems to safeguard the information resources of companies. In the present business models of large corporate undertakings there is an excessive dependence on networked applications and this naturally leads to innumerable chances of perpetrators attempting to gain unauthorized access to corporate data systems and networks. Therefore it is proposed to use a quantitative research method of questionnaire survey among the IT professionals of large and medium companies to gather the necessary primary data for completing the study.
Research Design
For any research in the realm of social science, research design provides the bondage that keeps the research project together (Webcenter for Research Methods, 2006). The research design is expected to attribute a formal structure to the research. This is accomplished by exhibiting the manner in which different components of the research project will proceed to deal with the central research question. The research design may take the form of a randomized or true experiment, quasi experiment or non-experiment (Webcenter for Research Methods, 2006). It is necessary to have this three-fold classification for describing the research design with respect to internal validity. In general, although the randomized experimental basis is the strongest for establishing a cause and effect relationship, since the research adopts a quantitative research method and is non-experimental in nature it adopts a non- experiment research design for conducting the research.
Quantitative Research Methods
Quantitative research methods have their root in natural sciences. In the realm of natural sciences the quantitative methods involve themselves in diagnosing and analyzing natural issues. There are certain generally adopted quantitative methods. Questionnaire surveys and laboratory experiments are some of the techniques being used by quantitative method. According to White, (2000), there are various investigative processes which will provide the results of the research in quantitative and numerical values form part of the quantitative research method. The quantitative expressions represent the results of the research. Such quantitative results are put under a variety of statistical analysis so that the findings of the research can be reported in a comprehensive way. Quantitative research is rooted on positivism supporting measurements made in researches considered attaining precision and exactness (White, 2000). A quantitative research is said to be well conducted when objectivity in the treatment of results and the process used to generate the results is attained (Cavana et al, 2001).
Qualitative Research Methods
Qualitative research methods of employed to help the researchers to make an extensive study into various aspects covering social and cultural issues. Action research and case study are some of the techniques being used by the qualitative method. According to Creswel, (1994) qualitative research is an enquiry process which is undertaken to analyse the issues connected with the social or human behaviour. The success of the enquiry process under qualitative method depends on the viewpoints of various informants to the research who express their views in a natural setting. The impressions, viewpoints and expressions of the researcher would also be a part of the data source. Byrne (2001) believes that defining qualitative research using a single definition is not at all practical because the term qualitative itself a broad term. In addition, inferential statistics that is usually applied to data that are generated from quantitative researches is not used for qualitative research.
Since the research aims to examine the role of information security and the use of different techniques to safeguard the security, it is considered appropriate to employ the quantitative research method for completing the research. The study of information security and the techniques to safeguard the information involves the expression of viewpoints and perceptions by the industry professionals and managers with any numerical values it was considered appropriate that the perceptions of the respondents are observed through a set of pre-designed questions contained in a questionnaire and for this purpose the quantitative research method was considered suitable. In view of the decision to adopt the quantitative research method of questionnaire survey among the IT professionals and its suitability the qualitative method was not considered necessary.
Research Methodology
The process of this research engages the methodology primarily involving collection of the required data. The collection process is followed by the activities of organizing and integrating the data collected. The major step in the process of this research is the collection of data from the informants and the success of the research depends largely on the data collection process. Efficient data collection process ensures and leads the researcher to valid and credible findings from the research. This research will be founded on a quantitative study on information security in the context of corporate undertakings. Collection of primary data using the information and data collected from a number of participants based on questionnaire will provide the base for a firsthand experience of the researcher. Therefore this research uses the research technique of questionnaire survey method for conducting the research. The questionnaires containing closed and open ended questions were distributed to respondent organizations chosen from the yellow pages and through references from friends through email. The respondents were requested to send back the completed questionnaire by email to the researcher for further analysis.
The subject matter of study as such can invariably be supported by primary data collected through quantitative research method of questionnaire survey. The researcher considered using a qualitative method of face-to-face interviews in the place of survey. However, since the samples would be having the opportunity to express their views more freely when they were asked to respond to survey questionnaire, the survey method was considered more appropriate. This would enhance the credibility of the study. Further, since the interview method is a time consuming process and there is the likelihood that the industry professionals and managers may not find time to answer the interview questions. Since the topic of information security being an exhaustive one it was considered better to have frank opinions and viewpoints expressed as answers to the survey questionnaire to add value to the findings.
Research Approach
In order to collect the required information and data for conducting the study it was necessary to conduct the survey through a questionnaire distributed to a certain number of construction organizations. 150 such organizations were chosen as respondents to the survey, from the industry database collected from industry directories and yellow pages. Out of the 150 respondents to whom questionnaires were sent, only 31 of them returned the questionnaire duly filled with their views. The questionnaires were sent to the chosen organizations through email along with a covering note explaining the background and the purpose of the survey. The sampling method that was used for this research is by choosing the organizations based on the sizes of the firms based on their turnover. It is important to arrange the distribution of samples as fully representing the total population. Therefore, the researcher took maximum care in the selection of samples for the survey.
Construction of the Research Instrument
The research instrument in the form of a questionnaire (as exhibited in Appendix 1) contained two different sections with questions in a broader in perspective on the information security in general and with respect to the experiences of the participants in the individual firms in particular.
Section 1of the questionnaire contained questions on the general information relating to the respondent companies such as nature of business, activity undertaken by them, volume of business and the status of the respondent in their respective organizations. This information is required to analyze the homogeneity of the samples. Section 2 of the questionnaire contained questions on the general perceptions of the samples towards information security and measures being adopted by the companies to mitigate the issues relating to information security. Questions on the specific context of information security with respect to the individual firms were also contained in Section two of the questionnaire.
The objective in preparing the questionnaire was to keep the respondents answering the questions quickly and efficiently. The questionnaire has utilized simple questions with numbered ranking scale and yes or no type questions along with open ended questions where the respondents have to provide specific replies. There was one question requesting respondents to make suggestions for better information security. The questions at the beginning of the questionnaire were introductory in nature to assist the respondents to get a ‘feel’ for the answering style and the sections have been ordered with more taxing questions placed in the later parts of the questionnaire. The questions contained in the questionnaire might have required the collection of additional information before answering the questions on estimating the monetary value of information security risks and cost of security measures in the individual organizations. However this was not expected to be a problem as all the respondents have been chosen to be IT professionals having fuller knowledge on the topic of information security and the tools available to mitigate the issues. The layout and question sequence and even the wordings of some of the questions of the final version of the questionnaire were subjected to many changes before it was finally sent out to the samples.
Information Security and Computer Frauds
Even though there have been a number of studies focusing on human computer interaction and role of passwords and information security, not much of research has been conducted in the area of computer frauds and associated crimes from the perspective of a total understanding of the phenomenon of computer frauds. Studies have been conducted from business perspectives (Tan, 2002), from a general/legal perspective (Graham, 2002), from a specialized computer crime perspective (Graycar & Smith, 2002), from a technological perspective (Power, 2002; AusCert, 2002) or a victim perspective (Graycar & Smith, 2002). Within the scope of this limited literature there have been a number of definitional issues pointing in the direction of a lack of common understanding of computer frauds or their financial and other impact on the different organizational activities. Along with this, the alarmingly increasing rate of e-fraud and the importance of creating awareness among the users have underpinned the need for further research in the area towards better understanding of computer fraud in the context of corporate identity thefts. The findings of the research are expected to be beneficial to those who are entrusted with the controlling of this problem and those who are interested in pursuing further research.
Computer crime or e-crime can be defined as “offences where a computer is used as a tool in the commission of an offence, or as a target of an offence, or used as a storage device in the commission of an offence”. (Etter, 2001) This definition of e-crime purports to be inclusive of fraud, theft, unauthorized access, sabotage and abuse of computer resources. For the purposes of this paper the term ‘computer fraud’ would be construed as e-crime as quoted in the definition of the term by Etter. Theft in this context includes theft of intellectual property, hardware and software, while abuse of computer resources denotes the use of a wide range of mediums extending from facsimiled to email with ulterior motives.
Such computer frauds perpetrated against corporate undertakings and government organizations impact the security of their intellectual property. The concerns in this context from the commercial and government organizations may include: (i) Flow in and out of their corporate information network of unwarranted, unauthorized and unscrupulous data undertaken with fraudulent intentions (ii) Stealing and/or exchanging for monetary or other considerations confidential data over corporate network in any electronic format (iii) Running parallel/personal businesses on corporate networks (iv) subscribing to emails or internet sites containing malicious contents or with intent to view pornographic materials and (v) creating adverse publicity through misuse and abuse of corporate network.
Stages in Information Security
With the increase in the number of employees, applications and sophistication of information systems, the information management within an organization becomes more complex, and it also leads to potential increase in the vulnerabilities. VonSolms, (1996) observes three stages in the evolution of information security. In the first stage during 1960s the primary concern of information security was to ensure the existence of physical security control of the infrastructural facilities that aided information generation and flow within the organizations. For example, the printouts of reports were circulated in protected ways just to prevent misuse of information. During the second stage, in 1970s information security was in place to meet the specific needs of the individual organizations, without really taking in to account the enlargement in the scope of information security In the third stage, organizations by reason of using advanced information and communication technology, had to interlink their IT services. This has made the organizations to move from a closed environment to a networked environment which is more complex as the information flow was based on distributed and connected networks of machines.
Even in the third stage of evolution, different waves of information security could be observed (Kansal, 2006). Before mid 90s there was no connectivity to internet making the inter-office connectivity rare or intermittent. Confidentiality and integrity of information were regarded as the main purposes of ensuring information security. The objective of Information security is to control the access to information and later on to make it available to those in need of such information and are authorized to use. During the mid to late 90s connectivity to internet improved and increased security threats took the form of worm and viruses which exist even today. This made anti-virus products as the prime solution for tackling information security related problems. This also resulted in perpetrators using improved software to commit computer crimes. This has also affected corporate web-servers by innumerable attacks from malicious spyware and fraudulent emails. Internet servers were also subjected to malicious attacks by sophisticated hacking techniques. Firewalls were the means used by the organizations to meet these challenges. Firewalls segregate the malicious spyware and remove them to protect the networks. During the next line of threats to networks and computer systems worms with their advanced technological background are made to spread within the shortest time. They are designed to disrupt the corporate networks and exist even today. Hackers have more serious motives of financial gains by stealing individual identities or competitor information from corporate servers. The expanded e-commerce environment has necessitated sophisticated networks for enabling the global customers, mobile executives and staff working with remote access and suppliers to access information. This requires more sophisticated security tools to keep the undesirable people away from networks and for letting genuine stakeholders into the networks. Sensitive information while in transit needs higher level of security for protection and this involves use of new and improved tools like encryption and digital signatures, intrusion detection systems, virtual private network, and access control mechanisms (Kansal, 2006). The future trend is the security audit and certification covering the network systems and technology. They also deal with processes involved in the information flow. Organizations are now following the approach of ensuring information security from the attackers’ end. This enables the organizations to safeguard themselves against new risks like social engineering and dumpster-diving to prevent threats from insiders (Kansal, 2006).
Nature of Information Security
It is a common misconception that information security denotes computer security. However, information security may be computer and network security, information technology security, information system security, information and communication technology security with each of these having a different emphasis. However protection of electronic information is the central focus of information security and therefore security of all other aspects fall within the purview of information security. Information security in effect deals not just with the electronic information but all other resources, which influence the information flow including voice and data networks (Kansal, 2006).
Information security is often considered to be an issue concerned with the technology involved in the information system and it is assumed that information security needs a technological solution to mitigate the problems connected therewith. However, Whitman et al., (2005) dispute this view and state that information security is more a managerial risk requiring larger attention from the management. The following diagram illustrates a networked organizational design. This design includes different components like people and agents that affect the network. The agents include security threats such as spyware, Trojans and other malicious programs, machines and data. According to the diagrammatic representation, people and the agents are the active constituents and these constituent elements process data and are involved in communication and information flow.
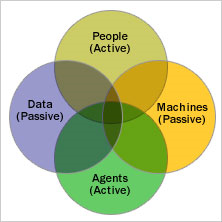
Managing the information security risk encompasses the process of discovering and measuring potential threats to information resources of the organization and taking necessary control measures as response to those threats (Lampson, 2006; Garbars, 2002). The failure on the part of the organizations to properly manage their information security leads to great compromise on the integrity of the organization and huge financial losses also. Example may be found in the case of Nationwide, UK’s largest building society paying about £ 1 million as fine after the organization lost one laptop containing important customer details stolen from the house of an employee (BBC, 2007). Therefore it can reasonably be concluded that information security is more concerned with people and the managerial ability to control the problem rather than a technical issue. It naturally follows that information security cannot be dealt with by a pure technical solution. Organizations should follow effective approaches and strategies that would help them achieve efficient information security.
Need and Strengths of Information Security
With more and more dependence on computers and more people working in computerized environment, need for computing control has evolved in greater magnitude in which the information security has to be extended to the individual desktop level. With a greater number of employees interacting with the information system backed by technology, in order to complete their daily tasks, employees themselves constitute a major threat in many occasions (Madgina et al., 2004). This is so because the employees have a direct an unrestricted access to the intellectual assets of the company. Lampson, (2006) is of the view that despite thirty years of efforts put in the development of sophisticated information security, organizations’ information systems still appear to be vulnerable to security breaches. One of the reasons cited for inadequate security is that probably setting up the required level of information security is expensive and is also difficult to sustain. Employees of many organizations perceive that information security comes in their way of their ability to accomplish the tasks assigned to them (Sandhu, 2003).
Straub and Welke are of the opinion that information security is being ignored by all levels of management as well as by the employees. This neglect has caused organizational systems to be less secure than they otherwise might be. The neglect by the management also results more frequent and intensive security breaches causing resultant damages above the normal level (Straub & Welke, 1998 p 441). Organizations have to recognize the major threats facing the organizational information system on an urgent basis to achieve a stronger protection of their information sources (Whitman, 2003).
Types of Computer Crimes
Threats to information systems can be viewed as circumstances that have the potential to cause loss or harm to the information resources of organizations (Pfleeger, 1997, p 3). Such threats can be classified into internal and external (Hind, 2002). Many of the past research and academic works have identified and quantified the sources and consequences of threats to information sources faced by organizations (Whitman, 2003; Ernst&Young, 2004; Doherty & Fulford, 2005; and DTI 2006). External threats identified by literature include, computer viruses, natural disaster, spoofing and hacking. Internal threats include:
- installation and use of unauthorized hardware and other peripherals,
- abuse of computer access controls,
- damage by employees with lower morale,
- use of organization’s information resources for illegal communication or activities,
- installation and use of unauthorized software.
Luehlfing et al., (2003) state that cyber crimes, even when they do not cause any direct financial or other losses to the company or its customers can still prove to be detrimental to the reputation and well being of the company.
The most common form of cyber crimes is the computer virus, which is a computer program that fixes itself with any application software. Virus also affects other system software embedded within a computer. When the virus gets activated subsequently, it causes serious damages to computer system itself or the files stored within the computer.
The following table illustrates several types of cyber crimes.
Examples of Cyber Crime
The basic steps involved in the virus infection process are exhibited in the following presentation.
Virus Infection Process
- Creation of virus by programmer; the virus program is typically an executable file, e.g. an exe, com, or vbs file.
- The virus program is attached to an email (or alternatively attached to a public domain software program).
- The email with the infected attachment file is sent to unwary recipients.
- When the email message is opened, the infected program runs on the user’s system and the virus replicates itself onto an operating system file.
- In some cases, the virus spreads from the user’s system to other user systems through infected diskettes. In other cases the virus gains access to the user’s email system address book and sends itself to all the addresses.
- At a predetermined point (e.g., a specific date), the virus activates often leaving programs and data files unusable.
There are indications that the menace due to computer virus is being put under check with the use of better anti-virus software. In addition, new laws acting against the perpetrators, and criminal prosecution of computer fraud perpetrators also has reduced the proliferation of this type of e-fraud. With the initiatives of the governments the rate of cyber crimes tends to come down (Grow & Bush, 2005).
Cyber terrorism is a high profile version of cyber crime in which the cyber terrorist employ malicious tools like computer viruses and online denial of services to incapacitate or reduce the normally available computer resources of an organization. While in the case of a private company, this would mean a loss of business and profits, in the case of a government organization this acts as a deterrent to the organization to pursue and complete its mission.
E-fraud is one type of computer crime. Some common type of e-fraud includes email spoofing, phishing, and online credit card fraud. Email spoofing is attempted by the fraudster by through the use of email in order to gain the confidence of an individual to make him/her part with the personal information to be used later on for unauthorized purposes such as making unauthorized purchases, obtaining fraudulent loans or other identity thefts. Spam is the prominent method used by email spoofers to trick the individuals to part with their personal information.
E-theft is said to take place when a perpetrator illegally enters into the computing system of a bank and diverts funds to an account which is accessible to the fraudster. Because of this potential risk major banks normally put several restrictions on the actions that a client can perform in online banking. In some of the case fictitious bank accounts might be opened by the perpetrators with intent to collect money from the clients who are unaware of the tricks of the criminals.
Netspionage implies the action of a perpetrator who makes unauthorized entry into the PCs of individual in order to access confidential information for selling such information to criminals for monetary gains. There are online frauds committed by people residing in other countries which are known as ‘offshore online frauds’. It is often difficult for the domestic law enforcement agencies to identify and frame the individuals perpetrating frauds from foreign countries due to limited resources or stringent extradition laws. Phishing is the tool widely used by the foreign fraudsters for perpetrating online crimes.
Online criminal act involving credit cards is another prominent cyber crime committed by the perpetrators, where the fraudster obtains a credit card number over the internet. The credit card number so obtained is used for unauthorized purposes such as making fraudulent purchases. Alternatively, the perpetrators use a fraudulent website to extract the credit care information from the victims by tricking them into it.
Online denial of service is attempted by the use of email barrage, computer viruses or other techniques which damage or shut down online computer systems. This results in loss of business and reduced profits. In some cases, online denial of service leads to permanent damage to the computer system and the information stored in the files in the system. Such damages require a large amount of money to be spent for rebuilding the system and to recreate the lost files.
Phishing is an act undertaken by the perpetrators to send fictitious emails to individuals providing links to fraudulent websites created by the perpetrator for obtaining personal information from the victim. The personal information fraudulently obtained is used by the perpetrator for illegal purposes such as making unauthorized purchases, obtaining illicit financial advantages or identity theft for other illegal purposes.
Software piracy is another form of computer crime associated with theft of intellectual assets using computer programs. Software piracy leads to loss of profits to the companies owning the intellectual assets and at the same time rewards the criminals who did not take the pains to develop the software.
Smith et al., (2003) identify the sources of threats to computer security and they are: (i) natural disasters, (ii) dishonest employees, (iii) disgruntled employees, (iv) persons external to the organization and (v) unintentional errors and omissions. Of these, the greatest threat has been identified as unintentional errors and omissions. However over time, this may get changed to other source with the increased activities on the business and personal front through internet.
Information Security Measures
Although most of the companies are well versed with the physical security of their information resources, they are not having adequate knowledge about the security of the computer network. It is important that the companies should ascertain the network and system vulnerabilities and adopt suitable measures to protect them from perpetrators making unauthorized entries. “Such information security breaches can lead to loss of competitive advantage, disclosure of classified information, network intrusions, tarnished brand image, and loss of business”. (Kansal, 2006). Generally organizations adopt the following security measures to safeguard risks associated with information flow.
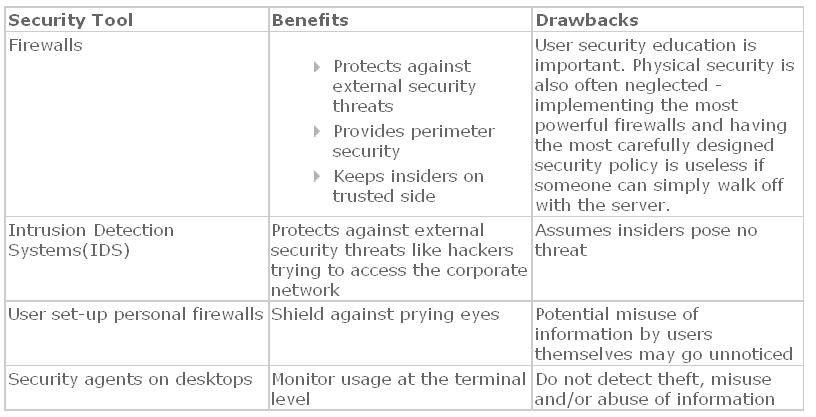
Costs resulting from Breach of Information Security
While a physical breach of security results in actual loss of the computer system and other hardware in addition to the media on which information were stored. A logical breach of security on the other hand affects the data stored and software used without involving any physical damage to the hardware. Review of the relevant literature reveals the results of a number of studies conducted on the cost of information security incidents (Anderson, 2001; Butler, 2002; Tarr, 1995). The major problem in assessing the extent of damages from breach of information security is that the damage is often invisible. This makes the job of the managers difficult for providing justification for the investment on security. Literature suggests theoretically the optimum level of investment in information security measures should not exceed one third of the extent of potential loss which is expected to result from any breach (Gordon & Loeb, 2006). Cost effectiveness analysis has been found to be the favorable analysis method when the costs and benefits differ widely from each other (Orlandi, 1989). It is aruged that effectiveness is easy to apply as there is no need to find the prices of adverse events. Instead it is necessary to find the monetary value of potential saving by way of prevention of loss against a specific amount of investment in dollar terms. Economic reasoning and analysis can be thought to be a solution to the issues arising from information systems (Blackley et al., 2001; Schneier, 2002). For example, the success of firewalls is due to the insistence of the auditors rather than its cost effectiveness as an information security tool and this fact could as well change the cost of investment on system security measures by the companies. Even though adding a firewall adds cost and is also a user annoyance, the cost of not having firewall would be an audit qualification. From this observation it may be stated that assessing proper monetary impact of information security can solve both business and technical issues for the information security industry.
Results/Findings
Responses to the Questionnaires
The questionnaires were completed by senior managers in the organizations comprising mainly of Chief Information officers and IT managers having the responsibility of information and system security in their respective organizations. Based on the information of their positions in their respective organizations it can be inferred that the respondents have adequate knowledge on the activities associated with information security in their respective industries. The response rate for completed questionnaire is shown in the following table:
Table: Breakdown of Responses
This response rate can be considered as a typical of an information technology questionnaire survey. In the past for similar types of survey by Burd, (2008) evolved an average response rate of 30.0%. Japan Network Security Association, (2004) reported that the response rate for their study was 17.98% Baker, (1997) suggested that it is possible to obtain statistically reliable conclusion from a sample population of 20 or more. However it is a fact to be remembered that the relative response rates do not guarantee the reliability of the survey results as representing the viewpoints of the population. It is the content and reliability of the information that add up to the value of the findings of any social science research.
Characteristics of Respondent Organizations
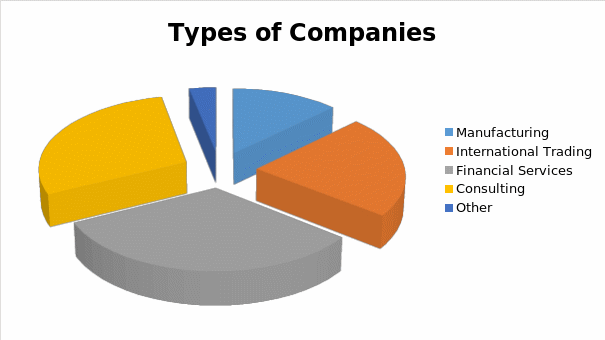
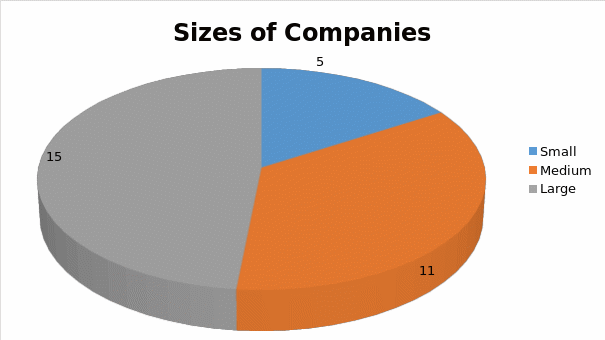
From the answers to section 1 of the questionnaire, the information on the characteristics of the respondent organizations has been compiled for presentation. Based on the number of employees the size of the organization has been categorized into small, medium and large companies. Organizations with less than 50 employees were classified as small, with 51 to 250 employees as medium and organizations having more than 250 employees as large. The results indicate that a majority of the firms were falling under medium and large sized organizations. 72% of the organizations were having turnover between £ 20 million and above £ 50 million. 78% of the organizations were involved in international operations. The following figures represent type and size of the organizations responded to the survey questionnaire.
Information Security and Measures for Protection
Section 2 of the questionnaire contained questions on the perceptions of the respondents on various aspects information security and the measures adopted by their respective companies for controlling information security breaches.
Exposure to Networks/Large Information Systems
Table: Exposure to Networks/Large Information Systems
The question on exposure to networks/large information systems of the organization evoked the above response from the samples.
It is clear from the table that a majority of the respondent organizations are exposed to information networks having large computerized information systems with only 2 organizations responded as having low exposure to networking. From the standpoint of the researcher this chances of the respondent organizations to get exposed to information security threats are high based on their working environment. It is normal that organizations with this kind of exposure to networking should expect some kind of information security threats resulting in loss or damage to business. The attitude towards protection against the risk of information security breach is one aspect that top management of the organizations should consider and devise appropriate control measures for protecting the information resources of the organizations. A review of the literature points out this responsibility on the part of the management (Whitman et al., 2005).
Table: Level of Risk towards Information Security Breach
One of the major factors that have made the protection against information security breach is the potential loss that any breach can cause to the company. According to the response to the survey almost 71% of the respondents are of the view that their organizations are carrying a higher risk towards information security breach making the adoption of some form of control measure imminent (Straub & Welke, 1998). Without the institution of an effective control measure the organizations are sure to have potential loss or harm to the information resources of organizations (Pfleeger, 1997).
Table: Importance of Information Security Control Measures
From the table it is clear that almost all the respondents have understood the importance of adopting some form of information security control measure in their organizations. Any organization having an attitude of attaching less importance to the threats to their information security would cause organizational systems to be less secure than they otherwise might be. The neglect by the management also results more frequent and intensive security breaches causing resultant damages above the normal level (Whitman, 2003)
Threats of Different Attacks on Information Systems
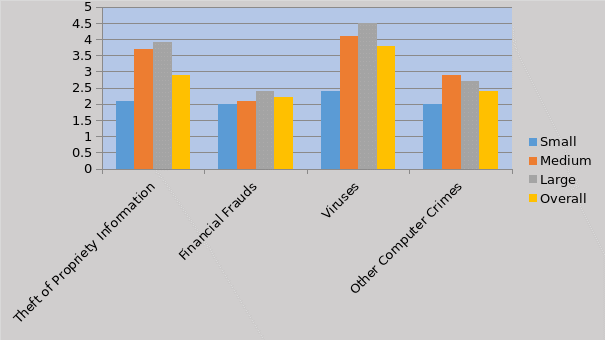
The question on the extent of different attacks affecting the information security has evoked a mixed response with medium and large sized companies finding theft to propriety information and viruses having a large impact from the breach of information security. This finding is consistent with the findings from 2002 CSI/FBI Survey which suggests that among the different kinds of information security breaches, most organizations tend to make huge financial losses with the theft of propriety information. The findings also suggest that viruses which harm computer systems and software could not be eradicated totally by installing anti-virus software in the computers and networks. The findings also suggest that security breaches involving unauthorized access to corporate information are different from attacks from viruses as the former results in large financial losses to the companies (Campbell et al., 2003). It appears that small sized companies are affected more by virus attacks then theft of propriety information.
The graph is prepared based on the mean values assigned to the responses received from the participants.
Information Security Protection Measures
On the utilization of information security protection measures large and medium sized companies have indicated that they employ more firewalls and virus scanners for protecting security breaches to their information systems and resources. Most of the organizations use password protection. Use of other protection measures such as access control and systems log is preferred by large companies as compared to medium and small companies. Encryption and intrusion detection systems are not in very much favor as the security protection techniques, perhaps because of the cost involved in installing these sophisticated systems and training the staff to utilize these features. Smaller firms opt for password protection as the major technique for protecting their information systems in addition to establishing firewalls. The relevant results obtained out of the survey have been tabulated based on the mean values of responses and presented in the following figure.
In the matter of evaluation of the results for the question of degree of utilization of particular security protection techniques it was inferred that the mean value below 3.0 indicates that the frequency of utilizing these techniques is from ‘occasional to never’. Out of the 8 techniques listed only four techniques have mean values more than 3.0. Password protection and firewalls have been reported to be the most used information security techniques in the respondent organization irrespective of their sizes.
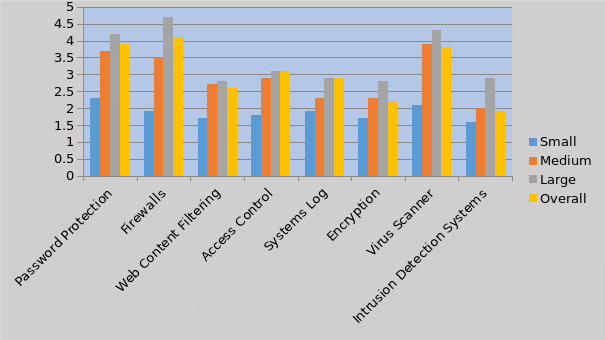
Anderson (2001) and Butler (2002) found similar trends in their studies, relating to information protection techniques where most of the respondent organizations followed firewalls and passwords for protecting their information systems leaving other scientific techniques. This indicates the nature of the industry professionals and managers towards identifying and adopting security protection techniques more based on their judgments and cost of installing suitable protection techniques (Gordon & Loeb, 2006).
Sources of Threats to Information Security
Source of threats to information security is one of the important factors in deciding on the appropriate security protection technique to be adopted by the organization. Therefore the question concerning the sources of threats to information security assumes greater significance in the context of any business organization and the application of the technique for securing the information. Disgruntled employees and improper password protection appear to be the most frequent source of threat to information security in the case of large organizations with a mean value of 4 and 3.7. Factors like viruses and unintentional errors and omissions closely follow. Threats from viruses and denial of service are less in larger organizations because of better protection through firewalls and anti-virus software application. Cracking of passwords appears to be the most serious threat to information security in the case of medium and small sized companies in addition to viruses and online denial of services. Cost might be the main factor preventing the small sized organizations from engaging suitable protections to the information security.
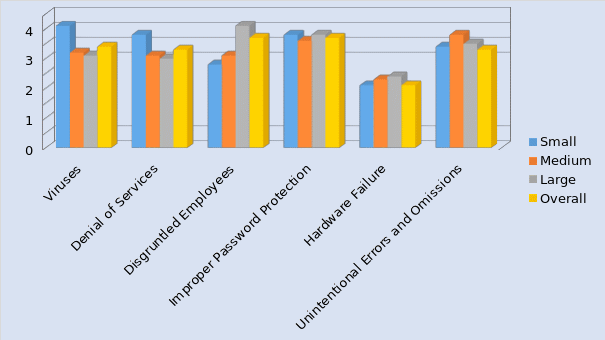
The large organizations adopt information security protection techniques through the suggestions from the consultants appointed by them or from the advice of IT firms to whom they have subcontracted their information system developments. On the other hand, the medium and small sized companies have to depend on their own judgments and experiences to decide on the appropriate protection measures. This will enlarge the risk for the firms on account of serious threats from information security breaches.
Risk Assessment Factor for Deciding on Information Security Control Measure
The objective of this question is to gather information from the participants on the factor that they will consider for implementing a particular security protection control techniques to prevent any unauthorized use of information in possession of the organization. The data collected is presented in the table appended below.
Table: Risk Assessment Factor for Deciding on Information Security Control Measure
On the question of the number of times the respondent organizations have experience threats to information security, the participants replied that they had none to one major attack per month and average of one intrusion every six months. The respondents were of the view that they are likely to experience at least one incident of information security breach in the next twelve to twenty-four months causing financial loss to their respective organizations. Almost all respondents have replied that access control as the most preferred and effective control measure to combat a security threat to information. A combination of firewalls and access control was preferred by some of the respondents. None of the respondent organization had a proper system of assessing the cost implications of potential loss to their organizations on account of any possible breach of information security and deciding on the control measure based on the cost of potential loss. As a suggestion some of the respondents have opted for shifting the financial risk to insurance companies. Although insurance can be considered as one of the possible means of transferring the risk to a third party, there are issues concerning such coverage like formal method of damage assessment, deductibles, covered items and confusing policies of coverage. Periodic security audit and certification was another possible means suggested by the respondents.
Analysis
It has been observed by the security community that in most of the organizations, a major security threat to their information systems emanate from within the organization from insiders. Research has proved that in 70% of the cases of corporate identity thefts, employees of the same organizations have been found to be responsible for such identity thefts (Hind, 2002). The employees in these cases have been found to act with malicious intention of stealing the company information and selling them to competitors. Majority of the companies are not in a position to cope with such attacks originating from internal sources; nor in a position to detect the unintentional drawing of information by their employees. In the light of increasing corporate identity thefts, the protection of confidential personal information of clients and other affiliates by organizations has become a serious issue much more than of a compliance nature. It necessitates the creation of awareness among the organizations to become more active on the ways of detecting and preventing identity thefts. Regulatory compliance with the applicable legislation should be made an important aspect of information security policies of the organizations and embedded in the security architecture.
The detection mechanism should comprise of an authorization procedure, internal auditing of the safety control measures and whistle-blow hotlines to alert the employees about any breach of security committed or a potential identity theft or other computer fraud underway. From a technological point of view, it is advisable to use automated detection systems which are able to process large volume of data and at the same time highlight any suspicious action to draw information in an unauthorized manner deviating from the usual patterns used to retrieve information from the system. In addition to protecting theft of information from external sources, organizations should also focus on the protection of corporate information with reference to identification and related information of clients and affiliates from insider threats. Organizations should treat such information with utmost confidentiality to prevent any untoward incident happening from the action of their own employees. Solomon et al (2003) prescribe protection in the form of restricted access to such confidential information so that the information assets containing personal and sensitive information might be protected from unauthorized access and destruction or disposal of such electronic information with malicious intentions.
The most common method of protecting unauthorized access to corporate information stored in a computer network is through using passwords. However passwords cannot be considered as strong protection, as passwords selected with easy and guessable words could be cracked by the hackers within no time. In addition there is the necessity of changing the passwords very often leading to forgetting of the passwords or noting down them in places of access to those intend to steal information. File encryption is a commonly used method to prevent data theft, as most database software packages offer in-built encryption and decryption of data facilities. In addition, hardware and software firewalls are found to be widely used and are absolute necessity in the context of corporate information protection for limiting the risk of intrusion in to the information network. System access logs can be used to for accessing information in those files containing personal and private data. Internal auditors should carry the authorization to evaluate the system access logs to find out instances of any unauthorized access with dishonest intention. With the proliferation of Internet as the medium of communication such instances of corporate identity thefts have become a serious issue demanding focused attention from the corporate undertakings in the form of precautions to protect any loss of information which will seriously reflect on the reputation of the organization in addition to causing huge financial losses.
Summary
The findings from the questionnaire survey identified threats such as theft of propriety/disclosure of information and virus attacks as the most common type of security threats faced by the respondent organizations. The findings also report that large companies use different means of information security protection techniques like multiple intrusion detection systems, access control, firewalls and systems log. Small and medium companies normally resort to password protection and firewalls as the best measure of information security control in their respective organizations. While all the respondents expect a serious breach to their information security in the next twelve to twenty four months, none of the companies have a proper system of assessing the potential financial loss to the organization in the event of a security breach occurring. Therefore the large companies decide the measure of control based on the recommendations of the consultants and small and medium companies decide based on the cost of such measure and use their own judgments in deciding the measure of security control they want to implement in their organizations.
Conclusion and Recommendation
Conclusion
This study reveals that there are a number of vital factors which have been identified as being essential for an organization to achieve the desired level of information security. The results suggest that it is vitally important for the organizations to institute concrete information security policies so that unauthorized users are prevented from accessing the organizations’ information sources. It is also highly essential that the organizations take necessary steps to train the employees so that awareness is created among them about the information security issues and their financial impact on the organization in case if there is a serious breach of information security. Moreover, theoretical review undertaken by this study suggests that the ethos of information security should come from the top management to motivate the employees to have a similar serious attitude towards complying with the organizations’ information security policies and procedures. Another important aspect relating to the information security discussed under the study was the cost of instituting control measures. It is important that the organizations provide for sufficient budget for the implementation of appropriate protection mechanisms within the organization.
It is highly likely that the factors identified by this research would have a significant impact in enabling the organizations to achieve effective information security. When strictly followed the control measures suggested would be able to protect the organizations from serious security breaches. While the study has highlighted the basic requirements for a good and effective information security practice, it also underpins the importance of a continuous evaluation of these practices to implement suitable improvements wherever necessary as there are rapid developments in the ICT and the corresponding unscrupulous ways of accessing the information sources of corporate undertakings by fraudulent means.
The current research based on a questionnaire survey has identified the order of importance of threats to information security of the organizations in (i) theft of proprietary/disclosure of information, (ii) virus attacks, and (iii) other computer crimes such as denial of service attacks. Respectively this research has identified password protection, intrusion detection systems, system logs, access control and firewalls as control measures for the theft of propriety information and access control and virus scanners for the second type of threat. Access control, firewall, and other proactive control measures would prevent the happening of other computer crimes such as denial of service attacks. It is observed that the Chief Information Officers and other managerial staff do not possess adequate knowledge in assessing the effectiveness of existing control measures. This study observed that the large firms invariably follow the recommendations of the consultants in employing the information security control measures without really assessing the potential cost of losses to the company or the justification for the cost of investments in the protection control measures recommended by the consulting firms. In the case of small and medium sized companies the managers consider their own judgments in making decisions on installing protection techniques. Cost of investment in these tools and techniques is a major factor which guides the small and medium firms in this respect.
Limitations
In the current research there were several limitations faced in the data collection. First selection of the respondent organizations was a mammoth task with a large number of organizations presenting as the right type of organization for sending the questionnaire. However, it was necessary to apply several criteria for selecting the right sample population to maintain homogeneity. Secondly getting the questionnaire back duly filled was a difficult task, as the executives and managers were busy in their own schedules with no time to spend on filling the questionnaire. With a close and persistent follow up only the researcher could achieve this response rate. Several executives did not even acknowledge the receipt of questionnaire. Another tough task was to analyze and tabulate the findings of the research. Despite the limitations the findings of the research were close to the findings of the previous studies conducted in the area of information security and control measures. The research gave a thorough insight into the realm of information security which is of more practical value in the real life situations.
Recommendations
Since the cost of potential loss to the organization because of any breach in information security will be enormous, research may be undertaken to review the security control measures implemented in different organizations purely from a cost perspective by estimating the potential loss to the company in the event that the security measure is not implemented. An industry-specific study; for example the implementation of control measures in financial service companies to protect information would throw further light in this field of research.
References
Anderson, R., 2001. Why Information Security is Hard-An Economic Perspective. In 17th Annual Computer Securitiy Applications Conference., 2001.
AusCert, 2002. Australian Computer Crime and Security Survey. Web.
BBC, 2007. Nationwide Fine for Stolen Laptop. Web.
Blackley, B., McDermott, E. & Geer, D., 2001. Information Security is Information Risk Management. In Proceedings of the 2001 Workshop on New Security Paradigms., 2001.
Brown, J.S. & Duguid, P., 2002. The Social Life of Information. Boston: Harvard Business School Press.
Burd, S.A., 2008. Impact of Information Security in Academic Institutions on Public Safety and Security in the United States, 2005-2006. Web.
Butler, S.A., 2002. Security Attribute Evaluation Method: A Cost-Benefit Approach. In Proceedings of the 24th International Conference on Software Engineering ACM., 2002.
Campbell, K., Gordon, L.A., Loeb, M.P. & Zhou, L., 2003. The Economic Cost of Publicly Announced Information Breaches: Empirical Evidence from the Stock Market. Journal of Computer Security, 11, pp.431-48.
Cranor, L. & Garfinkel, S., 2005. Security and Usability. O’Reilly and Associates.
Creswel, J. (1994). Research Design: Quantitative & Qualitative Approaches. Thousand Oaks NJ: Sage Publications.
Doherty, N.F. & Fulford, H., 2005. Do Information Security Polciies Reduce the Incidence of Security Breaches: An Exploratiry Analysis. Information Resources Management Journal, 18(2), pp.21-39.
Ernst&Young. Global Information Security Survey 2004.
Etter, B., 2001. The Forensic Challenge of E-Crime. Web.
Garbars, K., 2002. Implementing an Effective IT Security Program. As part of the Information Security Reading Room GSEC Version 1.4. SANS Institute.
Gollmann, D., 1999. Computer Security. New York: John Wiley & Sons.
Gordon, L.A. & Loeb, M.P., 2006. Budgeting Process for Information Security Expenditures. Communications of the ACM, 49(1), pp.121-25.
Graham, T., 2002. Dispute Resolution: E-Fraud and Jurisdiction. Web.
Graycar, A. & Smith, R., 2002. Inquiry into Fraud and Electronic Commerce Emerging Trends and Best Practice Response. Web.
Grow, B. & Bush, J., 2005. Hacker Hunters: An Elite Force takes on the Dark Side of Computing. Web.
Guba, E. G., & Lincoln, Y. S. (1994). Competing paradigms in qualitative research. Chapter 6 in N.K. Denzin & Y.S. Lincoln (Eds) Handbook of Qualitative Research. London: Sage.
Hind, S., 2002. Security Surveys Spring Crop. Computers and Society, 21(4), pp.310-21.
Hirschheim, R., Klein, H., & Lyytinen, K. (1995). Information Systems Development and Data Modelling: Conceptual and Philosophical Foundations. Cambridge: Cambridge University Press.
JapanNetworkSecurityAssociation, 2004. Fiscal 2003 Information Security Incident Survey Report. Web.
Kansal, R., 2006. Insider Threat to Information Security – a Primer. Web.
KPMG, F., 2000. E-commerce and Cyber Crime: New Strategies for Managing the Risks of Exploitation. Web.
Lampson, B.W., 2006. Principles of Computer Systems. Web.
Luehlfing, M., Daily, C., Phillips, T. & Smith, L.M., 2003. Cyber Crimes, Intrusion Detection and Computer Forensics. Internal Auditing, 18(5), pp.9-13.
Madgina, E.M., Petrulish, C. & Motuk, K., 2004. The cost of Non-Compliance-When Policies Fail. In Proceedings of the 32nd annual ACM SIGUCCS conference on User services. USA, 2004.
Orlandi, E., 1989. Computer Security Economics. ICCST.
Pfleeger, C.P., 1997. Security in Computing. New Jersey: Prentice Hall.
Power, R. 2002 CSI/FBI Computer Crime and Security Survey. Web.
Sandhu, R., 2003. Good-Enough Security toward a Pragmatic Business-driven Discipline. IEEE Computing Society.
Schneier, B., 2002. No We Don’t Spend Enough. Workshop of Economics and Information Security.
Sebastian, H., Solhms, V. & Eloff, J.H.P., 2003. Information Security. New York: B & D Printers.
Smith, L.M., Smith, K. & Kerr, D., 2003. Accounting Information Systems 4th Ed. Boston MA: Houghton Mifflin.
Straub, D.W. & Welke, R.J., 1998. Coping with System Risk: Security Planning Models for Management Decision Making. MIS Quarterly, 22(4), pp.441-70.
Tan, H., 2002. E-Fraud: Current Trends and International Developments. Web.
Tari, F., Ozok, A.A. & Holden, S.H. (2006) A comparison of perceived and real shoulder-surfing risks between alphanumeric and graphical passwords. Pittsburg PA USA: Symposium on Usable Privacy and Security (SOUPS).
Tarr, C.J. Cost Effective Perimeter Security, Security and Detection. In European Convention on Security and Detection., 1995.
VonSolms, R., 1996. Information Security Management: The Second Generation. Computer & Security, 15, pp.281-88.
Wand, Y., & Weber, R. (1993). On the ontological expressiveness of information systems analysis and design grammars. European Journal of Information Systems , 3, 217-237.
WebcenterforResearchMethods. (2006). Research Methods Knowledge Base. Web.
White, B. (2000). Dissertation skills for Business and management students. London: Cassell.
Whitman, M.E., 2003. Enemy at the Gate: Threats to Information Security. Communications of the ACM, 46(8), pp.91-95.
Whitman, M.E., Caylor, J., Fendler, P. & Baker, D., 2005. Rebuilding the Human Firewall. In Information Security Curriculum Development Conference. Kennesaw GA USA , 2005. ACM.
Zviran, M. & Haga, W.J., 1993. A comparison of password techniques for multilevel authentication mechanisms. The Computer Journal, pp.227-37.
Appendix 1 Questionnaire
Questionnaire
This questionnaire is presented to you as a part of a research study leading to ——————-degree from…………………..University. The questionnaire intends to gather information on the subject of information security. Any information you provide will be kept strictly confidential. Please try to answer all the questions with the options provided against each. A ‘remarks’ column is provided at the end of the questionnaire to provide additional information you would like to add. Thank you for your cooperation.
Section 1
General Information
Nature of Business:
- Manufacturing
- International Trading
- Financial Services
- Consulting
- Other
Scope of Activity:
- Domestic
- International
Size of the Organization:
Please indicate the turnover of your organization for the year 2008
- Less than £ 1,000,000
- Between £ 1,000,001 – £ 10,000,000
- Between £ 10,000,001 – £ 25,000,000
- Between £ 25,000,001 – £ 50,000,000
- Above £ 50,000,000
Number of Employees:
Please indicate the number of employees of your organization for the year 2008
- Less than 50
- Between 51 – 100
- Between 101 – 200
- Between 201 – 500
- Above 501
Your Organizational Position:
- CIO
- Senior Manager IT
- Manager IT
- Supervisory
Section 2
Information Security and Measures for Protection
Please indicate your organization’s exposure to Networks/Large Information Systems:
- High
- Medium
- Low
Please indicate the level of risk towards Information Security Breach of your organization:
- High Risk
- Medium Risk
- Low Risk
In your opinion how important is information security control measures in your organization?
- Is of great importance
- Is of some importance
- Is of no importance
What is the extent of the following attacks affecting the information system of your organization? The scale 1 indicates ‘low’ and 5 indicates ‘high’ impact.
1 2 3 4 5
Theft of Propriety Information
Financial Frauds
Viruses
Other Computer Crimes
What is the degree of utilization of various information security protection measures used in your organization. The scale 1 indicates ‘low’ and 5 indicates ‘high’ utilization.
1 2 3 4 5
Password Protection
Firewalls
Web Content Filtering
Access Control through Supervisors
System Log
Encryption
Virus Scanner
Intrusion Detection Systems
What is the degree of threat from various sources in your organization? The scale 1 indicates ‘low’ and 5 indicates ‘high’ impact.
1 2 3 4 5
Viruses
Denial of Services
Disgruntled Employee
Improper Password Protection
Hardware Failure
Unintentional Errors and Omissions
In your opinion what is the best risk assessment factor for deciding on any information security control measure?
- Monetary cost of potential losses due to system breakdown
- Cost of Investment in security control measure
- Sophisticated nature of control measures
- Recommendation by consultants/marketers
- Experience of your peers
- Your own judgment on different measures
- Based on relative data from other organization
- Risk assessment is predicting future and hence difficult
How many times you have experienced threats to information security from different sources?
If you have not experienced any threat so far, what is the likely time in months within which you expect such an incident to happen?
What is your preferred combination of control measures for protecting the information?
Is there a system of assessing the cost implications of potential loss to the organization on account of any possible breach of information security and deciding the control measure based on the cost of the potential loss?
What is your suggestion for improvements in the area of information security?
Remarks:
I thank you very much for your time in responding to this questionnaire which will help me complete an important part of my studies.