Introduction
After many inventions or technology development, threats are also involved in many ways. New technologies give us latest types of crime which directly or indirectly harm us.
Computer is the main source of the online data library. It not only gives us our required information, but when we download some copyright material then that also comes under cybercrime. Cyber and computer crime definition were developed after the enhancement of technology, and it improved after years of making proposals.
A Statement of Problem
Cyber crime is becoming ever prevalent in our society. These days, companies and individuals rely on the services and resources provided through the networks and computers.
Computers can be used in virtually any type of crime, ranging from cyber-stalking and child pornography to financial fraud, espionage and terrorism. Accessing the electronic records is quite important to be protected from such crimes and is not really easy due to its technicality. Necessary actions should be made in order to be on the safe side.
Organizations rely on the data to run smooth activities of their businesses. However, home users save data as per their convenience for their daily personal or professional activities. Due to this, it becomes vital that steps are taken to protect computer systems and the data that users store. Increasingly, criminals are using computers to commit crimes or to keep track of their “business dealings”.
This is very important since some of the most important evidences may be stored on the suspect’s computer.
This paper aims to compare and contrast the cybercrime laws of the United Arab Emirates (UAE) with the European Union (EU0, and the United States of America (USA) to come to the conclusion that the cybercrime law of the UAE needs more improvement and extensive upgrades to meet the UAE progress to have an open economy in the 21st century open market.
This paper would also look at the deficiencies in the UAE cybercrime laws.
Types of Cybercrime
Cybercrime is known by many different names such as computer crime or electronic crime. These crimes are linked to the network, computers or equipment used to attack. Attack mean hit on information that is saved on different locations in a company or organizational accounts. Hackers can steal identity of a person, credit card information and can also conduct robbery. The hacker can not only use the data himself, but can also proceed with blackmailing, etc. Data can be misused in several ways. Forgery and fraudulent activities are also conducted over the internet. Customer identities are not safe and money laundering can also take place.
As the use of computer is increased, the growth of cybercrimes has also being increased in numerous ways. Cybercrime types are:
Spam
Users receive countless unwanted emails in junk folder of their email inbox on daily basis. Such emails are sent as commercial tool. This is not legal by any mean unless the user himself subscribed for such newsletters or advertisements.
Many countries passed new anti spam laws to control unwanted mails and to stop unsolicited communication.
It misleads and provides false information regarding any product which they advertise and this ultimately falls under computer fraud or electronic crime. The computer crime misleads and conveys the information with the intention of inducing users, which results in someone’s loss (Types of Cyber Crime, 2009).
Offensive Content
Many companies and electronic communication websites can be found on the internet, whenever we browse. Those websites can either be useful or obscene, unpleasant or odious for many reasons. That depends on the material provided on those websites. In many countries adult content or nudity websites are banned and cannot be accessed from government (Types of Cyber Crime, 2009).
Harassment
Internet harassment is a common crime these days. Such crimes are conducted in result of the information accessibility over the internet and can be quite harmful in many ways. For example, unwanted email from an unknown sender including videos, photographs or the material that can harm victims, and sometimes it turns out in physical annoyance case. The personal information can be obtained easily by the harasser regarding the victims over the internet. They can easily get the address or a way to contact the victim to harass them. It is also linked with the criminals who consign cyber stalking, and it occurs when the tale begins to infatuate individual in the positive or negative way. They use the internet as a supporting effort to harass their victim to get their way. Today cyber stalking has become a serious criminal offence (Harassment, 2010).
Drug Trafficking
The one of the categories of internet is drugging traffickers, and they use that for trading. They use it by sending emails to their clients or customer and use other technologies, which are available on the internet. Drug traffickers also use internet cafes and courier websites to continue their business by sending illegal drug packages (Types of Cyber Crime, 2009)
Cyber Terrorism
Cyber terrorism can be defined as one’s troublesome behavior intentionally. It can also be defined as threats against networks and computers. The intention of these attacks is to harm victim’s religious, political or ideological theories (Coleman, 2009).
The hacking of official or individual websites, crashing government’s executive data or leaving virus on computers also fall under cyber terrorism. Cybercrime enhancement increases the record of the possibility in the organization security gap (Types of Cyber Crime, 2009).
Fraud
In cybercrime, the credit card fraud is the most common fraud these days. It is quite simple for hackers to conduct credit card fraud with the help of a few viruses. This involves storing the keystrokes in the input device and sending the same to the cyber criminals. When a hacker gets that then social security number, home address and credit card numbers can be easily obtained (Walker, n.d).
Piracy
Privacy on the internet means the copyright of media, distribution and downloading. The best example is going on the internet and writing names of website from where movies or songs can be downloaded, and then users might share such videos, etc on networking sites like face book or twitter. This way, users actually contravene privacy.
It has been illustrated that the activities of a common internet user involves sharing activities, downloading, accessing electronic sources, games, books music and several other things that are stored at unknown servers or personal computers. This can violate copyright Act. The illegal distribution of movies, music, software or games is counted as a violation of federal law and the penalties can be money or end in jail (Types of Cyber Crime, 2009).
Types of Computer Crimes
Computer crimes increased from the development of the internet and technology growth during last three decades. It’s no more a fantasy, but became a nightmare.
Computer crime increased and our normal living standard turned in hard reality of an internet felony. Computer crimes result in the loss in several real ways. Hacking, phishing and piracy are the types of internet fraud. This is really a common computer crime and everyone knows them (Types of Cyber Crime, 2009).
Hacking
Hacking is all about the unauthorized activities to acquire unethical access of someone’s computer by security breach and other hacking tactics. Hackers can easily get the required information once they hack the computer and after that no information is safe. Hackers can easily break the passwords of email accounts either that is civil, private, or government official. If we look around then we usually read in newspapers about the hackers who hack government office computer and steal information. The hacking problem is not only observed in Asia only but also in the United States and the European Union. Everyone tasted their criminal approach. The IP addresses are also not safe, and it can be used to transact the false identity. After hacking the IP addresses, hackers not only remain anonymous, but they can continue their criminal activities (Oak, n.d).
Phishing
Phishing also aims the acquisition of the useful and sensitive data saved of computer users. However, it involves fooling the user to get the useful information like, the credit card number, passwords or other credentials to obtain some financial or other benefits. Internet users mostly receive emails similar to the emails of a few common service providers like PayPal or Moneybookers with a link to be clicked that diverts the users to some fake websites where users are asked to enter their sensitive information of sites like PayPal, etc to actually fool them posing real websites. The interface of such phishing sites look similar to the real sites, of which the criminals tend to access. The security systems of such websites are fooled using users’ credentials that actually passed their credentials to the phishing links that are sent to them by the criminals. Below is the screen shot of such emails containing phishing attempts.
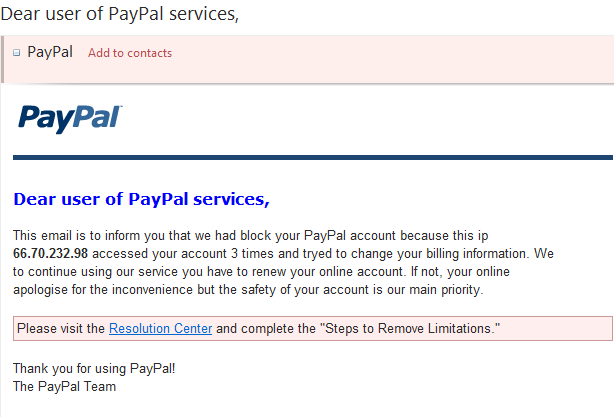
Above email contents are composed posing PayPal. There could be any other message as the contents may differ, but one thing that does not change is the phishing intention. Below is the screenshot of exact email address that is not from the exact domain of PayPal.
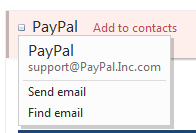
Above screenshot reveals that the email is from PayPal.Inc.com and is not actually from PayPal.com. Such emails are mostly received and are aimed to receive sensitive data.
Computer felony criminals use different websites, which are a forged version of some popular website to gain trust of users and make them feel safer to enter their details (Oak, n.d).
Computer Viruses
Virus is program that moves from PC to PC and hinders or obstructs the operations of one’s computer. A virus can easily damage data stored in one’s computer and it also affects the system’s performance. The common way to spread virus is email attachments or links via chatting messages. To be on a safe side, a user should not open unknown emails, unless he / she is expecting attachments from a specific sender. These viruses can be hidden in program files or software, which are pirated (Virus, n.d)
Cyber stalking
The use of the internet or any communication technology to harm others is a cyber stalking is all about the crimes that are made over the internet to harm others by mean of threat broadcast, manipulating data and counterfeit allegation. Cyber stalking involves damaging the systems of those who access chat rooms and other networking websites to collect the information of different people that can be used as the tools to annoy or harass someone to obtain benefits. Abusive phone calls and obscene emails have somber effects on cyber stalking and for that it falls under computer crime (Types of Cyber Crime, 2009).
Identity Theft
Identity theft is one of the most serious frauds. It is about stealing identity of a user to receive financial benefits. A person who steals someone identity, his information, then he pretends to be someone and use that detail to get benefits one way or other. There are two types of identity theft, one is financial identity theft and second is commercial identity theft. Financial identity means to obtain services and goods by using of false identity. The use of other user’s information is Identity replica, and it is a pretense as a false user.
Robbery, burglary and theft of computers and their Components
Robbery can easily be defined as an attempt of taking a valuable thing from anyone by threat or force. The common name of robbery is stickup and holdup. There are different degrees of robbery. These different degrees differ by state, weapon, or anything thing uses as a weapon and other accessory present at the time of robbery is considered as a felony by law. Motivated robbery is also one expression of robbery, which is common. Aggravated robbery mean when a suspect makes his victim believe that he can harm him with a weapon or a thing that can be used as a weapon. Burglary can be defined as illegal access structure to commit theft or crime. The common names of burglary are’ breaking’ and ‘entering’ or ‘break in’ (Burglary VS. Robbery, 2009).
Financial
Communal assurance in the security of the information process and stored on the computer networks is a conventional environment of strong avoidance for computer crime. It is really dangerous to the development of commercial transactions online or ‘e-commerce’. To participate in e-commerce that entirely depends on company aptitude of reducing e-risk. The online transaction’s risks include cyber attacks, viruses such as in February 2000; it could halt eBay, yahoo and other websites and then e-forgery (Joyner & Lotrionte, 2001).
Child pornography and sexual predators
The secrecy of the user on the internet is also the point of attraction for the hackers and it can also be dangerous for the users because when they use chatting rooms except knowing the credibility then it’s really dangerous. Especially in the case of children, they really can’t differentiate to whom they are interacting. Youngsters are more addicted of chat rooms and unknown websites so are open to various internet scams. Sexual developments of children transpire can happen in every social, economic, cultural or religious group. As the internet explosion transfer into a powerful and dangerous, child from New Jersey to Dubai are not safe. Sexual predators and pedophiles can use internet, exchange their home address and names and harm children (Hughes, 2001).
Drug crimes – customer records, formulas for drug manufacture, financial records
Internet is getting famous day by day and not only the home user or government officials are getting benefits from computers but drug traffickers are also running in the race. Drug traffickers are those who set arrangements at the cyber cafes and also follow the illegitimate consignment through the courier websites. Their packages include pills, exchange formula for amphetamines in restricted access. The drug trades on the internet reduce the chances of in person communication.
Drug dealer’s essential connections allow frightened individuals to comfortably buy illegal drugs. The vague effects that are often connected with drug deal are ruthlessly minimized. The riddle procedure that comes with substantial communication fades away. Drug dealers’ traditional recipes were cautiously kept undisclosed. This information is available on the internet and anyone who has computer access can check this out.
Counterfeiting – use of computers and laser printers to print checks, money orders, negotiable securities, store coupons
Counterfeiting means the deliberate duplication of copyrighted material. It involves bogus stuff with the aim of creating the copy of the real one. One should be aware of the copyright material as it enters in crime to download stuff including songs, videos, game and similar files without proper permission. This actually involves piracy. The internet piracy for the user of home computer is with the use of a P2P (peer-to-peer) program.
The discussion and debate regarding P2P services and file sharing programs in relation to the copyright violation take place to identify and protect the forgery of the available material (Roddel, Piracy and the Home Computer, 2009).
One can utilize P2P programs to share unauthorized files created by the common home users. The internet user gives their authorization for the information they post. They also share their provided information among different websites. P2P networks require internet connections and are all about sharing and connecting systems. For this, both the parties are required to install some certain software on their systems. There are a lot of networks, which are established to share files. The abuser of P2P networks set up free software on their computers. This downloaded software’s allows them to find and download files. This is not necessary that user will use this facility without the intention of damage to the copyright act. All the users do not use the internet clearly or legally, sometimes they use this sharing system in illegal activities. Below are some crimes open to the P2P networks:
Copyright Infringement
It is about the illegitimate sharing, downloading of copyright material that can be digital files including songs and movies or can also be some software or e-journals and e-books.
Child Exploitation
Child pornography is one of common exploitation these days. It is illegal and prohibited to send or receive such contents. Youngsters are open to such porn websites. Such sites are intentionally or sometime unintentionally opened by clicking the mislabeled icons.
Computer Hacking
P2P networks depict systems, files and other stuff to the internet users from various regions on the network. A use can download, share or send any desire file to other networks or users. Those files can be video related, movies, games, software, infectors, virus, pornography and anything else, whatever is available on net.
Telecommunications crime – unauthorized access to telephone systems, cloning cellular telephones, intercepting or creating false communications.
PCS and cell phone fraud can be divided into low and high tech frauds. Subscription is one of the common frauds. According to a source, “80% of the PCS deception is subscription fraud” (Telecommunications Fraud, 1998). An individual can steal sensitive credentials of someone and use his identity or sensitive information including social security number and credit card details, etc for his benefits. It has been stated that “They avail the service by false information but never pay” (Telecommunications Fraud, 1998). Eventually, carrier disconnects the services but his loss is never recovered.
When the services are disengaged, they carry on placing calls by outside of the home carrier’s service area. Roaming frauds are expensive because of the home carrier service remain answerable. They also pay roaming service charges, which are owed by the carrier. Cloning fraud is the most prevailing variety of the high tech fraud. Important information of anybody can be obtained either by unconditional carrier theft or air interception. Whenever a cell phone or PCS telephone is turned on, air interception account information is possible even when individual is not using the device (Telecommunications Fraud, 1998).
The thief after getting victims account, program them into cell phones or PCS telephone by creating a justifiable phone replica. PCS networks or cell phones are susceptible to fraud of low tech.
Reasons for Cybercrime
Man is a social animal. People desire surroundings like cities, neighbourhood and countries to live. Human are vulnerable and when they live in their surrounding they need a law to live and to protect themselves from harm.
Men invented many solutions for their convenience, and they needed law to protect their information or data from getting damaged.
If we apply the above rule of life then computers are also vulnerable and they need protection against cybercrime. Following are the reason for the cybercrime (Pati, n.d):
Capacity to store data
Today people don’t need journals or registers to safe their important data. A person can save data in his/her personal computer with needing more space. Computers have unique ability to store large data in small space. People can safe, delete or retrieve their required data without any hassle.
Easy Access
The difficulty that comes across in guarding the computer system is its illegal contact with every possibility of contravenes.
It is not because of human error but due to the complex technology like key loggers, stealing of access codes, logic bomb, voice recorders and retina imagers (Pati, n.d).
Complex
The computer completes its work in an operating system which is composed of millions codes. As no one is perfect so it’s impossible that there’s no fall at any stage of any invention. Cyber criminals are benefitted from such errors and infiltrate the systems easily.
Negligence
Negligence or carelessness is closely linked with human behaviour. It is not necessary that no error can be found while protecting the computer system. The negligence pays us hard in the form of cyber criminal control on computers.
Loss of evidence
This is the common and frequent fraudulent activity noticed these days. In that situation, all data is destroyed. Loss of evidence paralyses the system and makes a difficulty in crime investigation.
Cyber Criminals
There are several identical classes of cyber criminals. Below are some classes:
Six to eighteen age group children
Youngsters are always inquisitive to explore different things. They tend to do in deep of unknown sources. This is quite dangerous in several ways.
Organised hackers
Such criminals are mostly smart enough and are prepared. These hackers gather sensitive data to obtain financial specific benefits or just for fun.
Professional hackers
Professional hackers are motivated to hack computers, websites and inbox for money. Professional hackers are employed to hack the sites of opposite party.
Discontented employees
Discontented employees are those people who have been employed or currently not satisfied with their current management or boss. To torture or avenge their ex boss, they usually hack their data.
Literature Review
The search for a computer crime definition was needed as cybercrime involved all the categories of a felony. The definition emphasizes on cybercrime individuality on the knowledge and use of computer technology. Computer felony definition as per the Criminals Justice Resource manual (1979) is “any illegal act for which knowledge of computer technology is essential for a successful prosecution” (Schjolberg, 2008). The study on international computer crime aspects in 1983, the definition was defined as “Encompasses any illegal act for which knowledge of computer technology is essential for its perpetration” (Schjolberg, 2008).
In 1986, the OECD declared the computer related crime illegal. They also called computer crime unauthorized and unethical regarding the automatic processing of data transfer. As per the 1989 s Council of Europe Recommendation, the computer-related crime was called the offences. It defined and specifies the proposed recommendation for legislators nationally (Schjolberg, 2008).
In 1995, on criminal procedure law the Council of Europe recommended the term “offences connected with Information Technology”. It further describe computer crime as “Encompassing any criminal offence, in the investigation of which investigating authorities must obtain access to information being processed or transmitted in computer systems, or electronic data processing systems” (Schjolberg, 2008).
A single definition on computer crime was introduced from the European Union commission in 2001 that described computer crime as the use of Information Technology directly or indirectly. Further it is described as the crime that is traditionally performed by the computer technology (Schjolberg, 2008).
In 2000, the Stanford University made a definition on Cybercrime for an International Convention. It defines the crime against any network or individual computer transmits, rely, control communication or coordinate the data or programs without the legal rights will be counted in cybercrime.
The other suggestions made for the European Union Council Framework Decision on harassment in 2002. The commission embraces its functional definition. It defines the computer crime clearly, and they considered it as an attack on the information.
The four different categories on cybercrime were defined in 2001 from Council of Europe Convention in their article 2-10:
- Any offence on integrity, confidentiality and availability of data on computer
- Offence which is a computer related.
- Offence which is content related.
- Copyright related
Many observers not only considered intolerance, copyright infringement, child pornography and xenophobia as cybercrime, but they also took content related issues as cybercrime. Copyright issue is being highlighted but many countries do not consider this as a crime.
Cybercrime legislation in the United Arab Emirates
In 1971, the United Arab Emirates was formed, and it is a federation of seven emirates. The United Arab Emirates got independence from the Great Britain. The Supreme Council sovereign rules the UAE, so as the independence is sustained. After independence from Britain in December 2006, it was the only state in the constituency which was not having elected bodies. The United Arab Emirates lead the Arab world in acceptance of information and communication technology. As per the report of World Economic Forum, the United Arab Emirates was expected to spend about $3.3 billion on information technology and communications.
They planned to invest this amount in hardware for hospitals, schools, and other civil schemes between 2008 and 2011. To control the cybercrimes in their region, the government of the United Arab Emirates issued a federal law in this regard (United Arab Emirates, 2009).
As per the Cyber crime law No. 2 of the UAE the intentional act should be taken seriously as this would eliminate the open access of sensitive, professional or personal data in order to prevent such cyber crimes. The users may stay behind the bars for using the internet to deprecate Islamic places of worship and traditions or insult any religion and promote sinful acts. Individual found guilty by mean of setting up a website that can assist and promote thoughts to violate the common order and public affability, can be imprisoned. The law of the United Arab Emirates persists to stop all the citizens from the access of an important quantity of the Internet and straddling a variety of topics. The immense majority of sites are filtered for those who believe that filtered sites are disgusting in some ways, and few other political sites are also blocked.
The resistance of the United Arab Emirates to the Israel can be seen there. The UAE enhanced its system to the free zones of Dubai. Dubai previously enjoyed unfettered Internet access. In the UAE, Smart Filter software filters and blocks the websites containing offensive stuff relating unethical contents including gambling, drugs, pornography, religious violations or sex. Government of the UAE has been coming up with different attempts and programs to monitor electronic activities. Internet cafés are also being properly monitored in the UAE. They ensure that the provided connections do not bypass national filtering (United Arab Emirates, 2009).
Cybercrime legislation in the United States
Cybercrime or e-crime refers to the criminal activity that involves the computer and the use of the internet. This can be a customary criminal offense which is dedicated with the use of a computer. The newer crimes are instigating with the beginning of networks and computers. Cybercrimes cover an assorted and a very large variety of the offense (Computer Crimes Law, n.d).
Computer or cybercrime is divided in to three categories as per the United States Department of Justice, which is usually known as DOJ.
- The crime which acquired the computer peripherals, hardware and use of software illegally.
- The attempts aiming attacks by the mean of malware, viruses, computer hacking, Trojan horses, logic bombs, sniffers and spyware.
- The crimes committed via the use of computer devices and networks, and meanwhile the committed felony does not target the actual network and the computer. Such as phishing scams, Fraud and identity theft, embezzlement, corporate espionage, movie and music privacy, copyright violation of software, cyber terrorism and child pornography (Computer Crimes Law, n.d).
Congress endorsed Communications Assistance for Law Enforcement Act, known as CALEA on October 25, 1994 in response to apprehension of the rising technologies. Those up-and-coming technologies such as wireless and digital connections were making it gradually more difficult for the law enforcement forces to implement sanctioned scrutiny. Communications Assistance for Law Enforcement Act was intended to preserve the ability of law enforcement organizations to accomplish electronic surveillance.
Telecommunications firms work hard on designing and altering features and services to achieve standard results in surveillance capabilities. In October 1997, The Commission began to implement Communication Assistance for the ‘Law Enforcement Act’ with the release of a notice of ‘Proposed Rulemaking’. Since then, the Commission has released and taken several actions and numerous orders to implement Communications Assistance for the requirements of Law Enforcement Act (First Report, 2005).
Cybercrime Legislation in the European Union
The European Union was founded on November 1, 1993. The European Union was previously known as the European Economic Community usually known as the EEC. The European Union is the combination of twenty seven independent states. The European Union is based on the European communities, and it was established to improve economic, political and social collaboration. The European Union finalized the common currency for the member countries as Euro. The member countries of the European Union are Austria, Belgium, Bulgaria, Cyprus, Czech Republic, Denmark, Estonia, Finland, France, Germany, Greece, Hungary, Ireland, Italy, Latvia, Lithuania, Luxembourg, Malta, Netherlands, Poland, Portugal, Romania, Slovakia, Spain, Sweden and the United Kingdom (Kirste, 2007).
The ministers of the European Union asked the European Commission to appraise the possibilities of centralized agency set up on dealing cybercrime. The European Union wanted to prevent child pornography and the online fraud. The United Kingdom, France and Germany were the biggest opponents of the centralized European Union body on the cybercrime previously.
The intended body was to persuade information distribution between national law enforcement authorities.
The European Union Cybercrime Task Force was created pursuant to the meeting at the Europol Headquarters for two days. The hot issues that are discussed include the strategic and functional aspects of cybercrime tribunal, investigation and worldwide cooperation. They also discussed the major issues on operational exchange of information criminal new trends, case studies of cybercrime, international legal constraints, criminal modus operandi, private industries relationship, law enforcement force trainings and negotiation with organization of law enforcement force of the non European Union (Europol, 2010).
Methodology
In order to evaluate and compare the strength and applicability of the laws and legislation of the two entities i.e. the United Arab Emirates and the Western World comprising mainly of the United States and Europe, it was needed that not only the theoretical but also practical experience and demonstrations be conducted. Such study must be based on close watch and comparison of the laws and legislation of the two different regions.
The methodology of this study involves sites that are banned in the UAE, but they are operational in the United States and the European Union. As the sites that are allowed in the United States and the European Union but banned in the United Arab Emirates and also vice versa would demonstrate that how closely and exhaustively the laws of the two regions aim to monitor the activates related to the cybercrime and whether these policies and procedures that govern the legislation are practicable and implemented. This can be done through relating the literature with practical approach. This would also indicate if there are any gaps in the two approaches towards controlling cyber crimes.
Following data and results were studied from ONI (United Arab Emirates, 2009) that helps in realizing the fact that the internet growth in the United Arab Emirates has grown up tremendously and there is an increasing trend towards focusing on the prevention of cybercrimes. This is supported by the fact figures as mentioned by the Internet Telecommunication Union where they say that the use of internet has grown up to 64% in 2008 compared to 36% in 2006 in the UAE. This follows the fact that effective filtering techniques are being used in order to block and restrict the sites that are undesirable and lead to cyber crimes as anticipated by the regulatory authorities in the region.
Results at a Glance
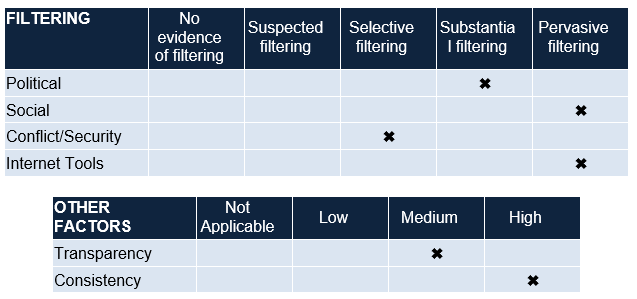
Key Indicators
As mentioned by ONI (United Arab Emirates, 2009), following are the key indicators of United Arab Emirates for the year 2009:
To carry out this job, the websites that are theoretically stated as prohibited are to be checked if these are practically blocked or restricted. From a quick view over the legislation and laws that direct towards in above-mentioned discussion regarding the United Arab Emirates and the Western regions comprising the United States and the European region, it can be clearly observed that the laws related to the sexual harassment and abuse including pornography, nudity and gambling form more concentration of the legislation while in the Western region the law enforces more towards the criminal activities and cyber crimes including viruses, Trojans, hacking, data embezzlement or piracy.
Also, Internet Access Management Policy developed by TRA (Telecommunication Regulatory Authority) in the UAE supports in formulating the procedure I order to restrict and filter the sites that contain explicit or offensive material including pornography, gambling or dating systems. This also addresses the fact that there are least or no provisions for the hackers to hack or send viruses or Trojans in the network. Along with this, online surveillance team has been set by the UAE police in order to monitor and capture the culprits related to the cybercrimes. Likewise, electronic petrol teams have been set that look for information and data about personnel that commit or tend to commit any prohibited activity in order to ensure the enforcement to the regional Cyber Crime Policy.
In order to test and verify the efficacy of the laws of the two regions, it was important to test practically the sites that are banned in the region, specifically in the United Arab Emirates. This would involve listing the domains and web addresses that are blocked or banned in accordance to the legislation designed in the United Arab Emirates, then determining that how these web addresses and domains are monitored and by which technique. This would include that how the filtering of sites is being done in order to restrict the blocked sites without hindering the sites that are not potentially banned or blocked in the region.
Similarly, in the regions of the United States and European Union, assessment of filtering techniques and interrogative software help in analyzing if the effectiveness of the legislation policy is in place and in use. ONIs are used with the list of banned or blocked sites in the region to observe that how much and how consistently the site and URLs (supposed to be blocked in the region) are actually blocked and trapped by the internet filter.
Through the use of advanced technologies and assessing the methodology to prevent cyber crimes from various perspectives, it is made so efficiently and effective that every attempt or most of the attempts made by the cyber criminals to violate the law are trapped and grasped at the right moment. The important thing is grabbing them at the right time, as just identifying the hacker or cyber criminal while he or she has one his damage is of no use and can be disastrous in some situations if not prevented.
One more important thing in designing or making effective and practicable law related to the cybercrimes is to assess the existing networking and internet infrastructure of the region. It might be possible that the internet infrastructure of the United Arab Emirates is different from that of the United States and the European Union having an inherent gaps in fully implementing the laws related to the cybercrimes in that region.
It should also be kept in consideration while assessing the application and enforceability of the laws related to cybercrime for the two regions that the customs, religion, traditions, norms and values are somehow different in the two entities that create main difference in approaching the control mechanism for such kinds of activities. For instance, in the United Arab Emirates the majority of the population and state itself is bearing the Islamic laws that illustrated strong and strict rules for any kind of offensive, violent material including nudity, sexual abuse and harassment thus people in this region are likely to observe such restriction through them at times.
Even the law enforcing mechanism of the region might not be too much strong or effective, while on the other hand, in the Western regions activities like observing pornography, nudity or sexual and offensive content are not much discouraged at the age of 18 or above. Thus, in these regions, there is easy access to such materials and sites and URLs are not banned at all. The only filtering mechanism that can be used there by them is the remote identification of the person if he or she is of appropriate age to see or use such content that involves pornography or offensive material.
Similarly when talking about cybercrimes that involve hacking, phishing, virus and Trojan attacks, it is apparent that the information databases residing in some of the organizations or institutions in the western regions are quite vast and confidential. Thus, in order to secure such data that can cause heavy amount of loss in terms of money or secret information may be dreadful for any of the stakeholders including the United States, European Union or the rest of the world.
Therefore, strong guarding systems on the networking are required there to secure the data from any kind of inappropriate or undesired and unauthorized access. Even in case of authorized access, there may be cases that the authorized individuals take wrong advantage of their authorization and leak the information to the public or to such forces that can somehow create harm for others and lie under the activity of cybercrime. Such recent cases happened where Wiki leaks has actually shocked the whole world with its juicy and shocking information leakages. Such activities may be for any cause or may bear true or false information while leaked, but the fact is that they create panic around the entities and cause the system of the whole region or globe to disturb. This may in fact lead to disastrous effects and aftershocks including relationship breach between countries and regions.
Thus, such activities need to be controlled and the method depends upon how strongly and strictly the laws that are designed to prevent cybercrimes are in practical implementation. This also involves the fact that how exhaustively the laws are made and the law makers have kept in consideration various techniques and directions to hack data and to commit cybercrime. The more exhaustively different approaches to commit cybercrimes are studied; they help more in creating effective law and legislation to prevent from any unseen damages or threats related to the cybercrime.
It was also assessed through past data that how much or how many times the breaches to the laws and legislation that are claimed to be enforced in these two regions have occurred giving a perspective of the enforcement of the legislation. This includes the activities that have impacted in a wider scope including banks, public institutes and organizations as mentioned in the conclusion of this study.
Data Analysis
Comparison and difference between the cybercrime laws of the United Arab Emirates (UAE), the EU (European Union), and the USA
During last many years, the internet addiction around the globe increased by the enormous number of users. As the life became easy the side effects or the disadvantages also increased as the number of benefit improvements.
Through testing and analyzing the consistency and efficacy of the blockage of the sites that are supposed to be blocked in the region specifically in the United Arab Emirates are often blocked showing a “blocked” page while at times, if internet is used by passing the firewall of the region, there are re-directions or lengthy browsing of the page is observed. All these techniques are used to divert the internet user from a particular blocked site or banned page that can lead to the violation of the cybercrime laws of the region.
While assessing the sites that are blocked and observing the error code or heading as a result of the page does not load, it can be analyzed through the error heading whether the error has occurred as a result of intentionally blocking of the site by the state filtering servers or the error is caused due to some other reason not related to the filtering or blocking of the HTTP or site by the state filters. Sites that are completely inaccessible from the local and remote internet connections are regarded to be effectively blocked in alignment to the regional policy and certain law for cyber crimes.
As we discussed the different types of cybercrime and the work done by the United Arab Emirates, European Union and United States of America earlier in this paper, the comparison and the difference in their law are according to their geographical layouts, their customs and the difference in religion as well. If one thing is legal in one country then it is not necessary that it will be working on the same circumstance in the other two.
During last six years, the Middle East started using internet more effectively and actively. The region as compared to the other areas of the globe recorded the largest internet growth. The percentage of internet use is now 600 percent of the Middle East citizens. If we compare this average with other countries then the average is three times. The other sensation of today’s market is the cell phones industry as the regions escort multiple vendors who are the competitors and have been working hard to stay in the market by lowering costs and improving performances.
The more significant than increasing the number of buzzing cell phones and internet admittance, it is the official consciousness to the citizens of the governments of the Middle East at the maximum level. The possibilities to transfer information and communication technology (ICT) policies to citizens as an administrative sideshow are no longer there. The Information and communication technology’s capabilities can overwhelmingly affect their capacity.
For the citizens who are less advantaged, this affects to innovate its competitiveness globally and to improve the socioeconomic prospects. The attention of the information and communication technology is to describe that the regularities are different in cybercrime affected countries. Their ways and methods to control the crimes over the internet are different. A salutary and fundamental change on these issues has become the top agenda to solve. This attention on world’s most dangerous issue is effective or not, but it remains a debatable issue (Dutta, Karake, & Samuels, 2007).
The financial records of the Middle East are just over 1 per cent of hacking as compare to the worldwide cybercrime attack. It’s a gauge about illegal breaking into computer systems that may not mechanically shock the user but it will take a closer look. A source states, “In 2002, the year’s last six months percentage of hacking in the United Arab Emirates was 300 percent. If a closer look is taken over the incidents of 2003” (Kaul, 2003), one ATM hacking fraud incident costs country the loss between $2 billion to $3 billion. Further investigation on this hacking fraud group revealed that in Indonesia, a group got access to the customer’s user identities in bank’s computer. At that time, cybercrime law was not in place to punish those criminals (Kaul, 2003).
Kaul stated, “The Gulf Cooperation Council known as GCC countries, including Saudi Arabia sets meetings to introduce Cyber law to protect their internet services and to stop the cybercrime” (Kaul, 2003). The Gulf Arab countries law was to work together with one another in commerce with cybercrime. To take necessary actions at that time, the cooperation agreement was signed by the US and the EU. As per Kaul (2003), in the US and Israel, there are more than 10, 00,000 people who use internet frequently so are open to cyber crimes. After the incident of 9/11 and then ongoing war against terrorism, the Middle East countries hacking could be on high alert but the government’s tracking system also increased and this saved it (Kaul, 2003).
The United Arab Emirates established its position as a leader in technology and economic values. The majority citizens of the United Arab Emirates are expatriates. The average per annual capital income of the United Arab Emirates in 2007 was US $ 40,000. The report of telecommunication sector of 2009 released the numbers of mobile users that was 7.5 million with the occurrence rate of 192% (UAE, 2010).
The 10% of the population of the United Arab Emirates uses the mobile internet. As per a source, “the figure of land line users in 2008 was 1.365 million and due to this average, the United Arab Emirates was ranked first among the internet users of Arab countries population wise. The internet users exceeded by 2.86 million in mid of 2009. This figure was 50% of the total population of the United Arab Emirates” (United Arab Emirates, 2009).
In 2009, 11% of population reached the high speed of internet usage. The number of internet users at the United Arab Emirates increased and created an active virtual society. They formed virtual society by the mean of chat rooms, blogs and forums. They share the issues open to the citizens of the United Arab Emirates. They also discussed the topics which were not common, and they were a success like cybercrime effects in the United Arab Emirates.
The role of the United Arab Emirates in the Arab world is the technological leadership.
The cyber police of the United Arab Emirates cyber was in charge of keeping an eye on users and monitoring the web since December 2008. As per the cybercrime police authorities, in 2009, they listed 200 cases. Those rated cases were mostly related to hacking (Kaul, 2003).
Findings, conclusions, discussions and recommendations
Cybercrime Cases
21st century was the decade of innovation, world war, crimes, drug trafficking, human rights violation, and it also played an important role in the modern way of human race. Computer invention and then the latest technologies such as internet not only changed the lifestyle, but it has also accelerated it. During the last couple of years, cybercrime as an increase in profit motivated internet crimes it remained front page news for long. The lack of cyber sufficient security measures is about the internet users who are unprotected by the internet crimes. The world is not only facing the fight against terrorism, but also the fight against cybercrime.
Vendors of software security providers are trying to show progress in this regard with some success. Software security providers are successful at some extent, but the majority of the internet users are still unprotected. They are at the same time facing the cybercrime such as phishing, identity theft and fraud on the internet.
One successful attempt of cybercrime further increases the level of more criminals by the means of theft over the internet. We may say that financial cybercrime success worked as fuel to attract criminals and this problem has been shadowed by the other security issues of information technology. The success is increasing the number of attacks in more sophisticated way. The government warfare over the internet or cyber warfare hasn’t drawn any considerable attention to media.
The valid reason for this lack of attention is not an appropriate evidence of cybercrime to connect with government’s actions or policies. During last few years, it has being observed that the cyber warfare was not considered as a serious issue to discuss, and it was associated with conspiracy theories. However, there are few governments investing the vast resources to develop weaponry and awareness on cyber warfare. They are treating cyber warfare as their overall offense and defense strategy. The United States, United Kingdom and Russia are the nations who are leading industrial hub. Iran and China are developing as the cyber nations and trying not to stay behind in this race.
They are under high attack of website hacking. Computer crime cases in Saudi Arabia were around 736,000 and that were 64 percent of the Gulf Countries. In the same time, the computer crime cases of the United Arab Emirates were around 248,000 that were 20 percent of the Gulf Cooperation Countries cyber felony. The website of the al-Watan (a newspaper of Saudi Arabia) was hacked. The hackers were the supporters of a religious cleric.
As per news in the October 2008, the official website of a news channel, Al Arbiya (UAE based channel) was hacked by the criminals who wanted the channel to support Sunni group of Muslims over the Shea group of Muslims. The systems were penetrated by the hackers, but Al Arbiya continued to work. This website was hosted by the US based company (The Free Library, n.d).
As per the publication of Gulf News, “In 2010, the law enforcement authorities of the United States arrested dozens of various nationals citizen such as people from Ukraine, Russia, Moldova, Belarus and Kazakhstan, as a part of their investigation regarding fraudulent activities” (Gulf News Report, 2009). The investigation was on multinational multimillion fraudulent cases and set for prosecution and trial. The majority of charged ones were not in the United States and seventeen were considered as fugitives. They were wanted by the United States officials and the support and cooperation from Moscow was critical. As per the complaint, 11 out of 20 arrested criminals were the citizens of Russia, and their ages were in between 19 to 26.
Margarita Pakhomova, who was 21year old, was arrested in September 2010. She was heading for Russia and was arrested.
In January 2010, 20 years old Sofia Dikova was arrested in the region of New Jersey. A pile of fake passports was found by the officers. Those passports were in use to open bank accounts (so called money mules).
Krastev illustrated a case that took place in December 2009 that a 23 year old Artem Semenov was caught by the authorities on tending to open a bank account using fake details. He was bailed, but caught again after four days when he was trying to open an account with false identity in other bank. His total numbers of complaint were around seven (Krastev, 2010).
Penalties for Cyber Criminal
In the UAE, The laws of cybercrime state:
Article No.2
As per the article No. 2 of the UAE cybercrime law, an action that is deliberately and purposely performed to acquire, harm or misuse credentials, secrets or by some mean, republish the professional, personal or official information will be treated as a criminal act. Individuals who are involved in such activities will be treated as criminal and will be penalized, sent to jail or both.
If a person changes, eliminate, republishes, harms or reveals information will be punished by the mean of jail for at least six months or can also be fined. In case of personal information is misused, then the fine will be Dh 10,000 or put in jail for not less than one year.
If any citizens besides the gender advantage commit prostitution or adultery through the internet will be in prison for five years and fined. Individuals involved in abuse of religious values or anything related to this will be punished for 5 years and fined or both. If someone abuses or attacks Islam then he or she will be sentenced for seven years.
Gulf News disclosed that, “If anyone is caught in setting up groups, which are promoting the program against public decency shall be sentenced to jail for five years” (Gulf News Report, 2009).
Article No.3
As per the article No. 3, anyone who commits a crime as per Article no 2 will be jailed not less than one year, fine of Dh 20,000 or both (Gulf News Report, 2009).
Article No.4
Article No. 4 illustrate the penalty and punishment for manipulating or making changes to the documents and files of the Federal or Local government. This would result in jail, fine or both. Individuals who will be found using such fake documents will be punished. This type of activities is aimed to secure some position or financial benefit by unfair mean. Forgery of documents is not being tolerated by any mean.
Article No.5
As per article No. 5 of the cyber crime law of the United Arab Emirates, if an individual is involved in jamming the service, obstructing, slowing down or breaking in to system software or information sources by any mean, he will be treated as criminal and will be sent to jail, fine or both.
Article No.6
Article No. 6 of the cyber crime law of the UAE states the punishment and fine possibilities for those involved in entering different data over the internet in order to obtain some benefits by obstructing, harming, breaking, changing or deleting tools, software or any system.
Article No. 7
Article No. 7 of the cyber crime law of the UAE is about the attempt using tactics, tools and programs to manipulate or harm medical files, data, reports or status for some reason. People involved in such activities will be sent to jail or will be fined.
Article No. 8
As per article no 8 of the cybercrime law of the UAE, individuals intentionally spying or superseding the data or file over the internet with the use of tools or any other tactics will be sent to jail or fined.
Article No. 9
The use of high tech and the internet by anyone for blackmailing, or threatening anyone to influence him for doing something that he doesn’t want to do shall be sentenced two years in jail and will be fined not more than Dh 50,000, or he will be sent to jail to ten years up or fine or both.
Article No. 10
Anyone by using internet or any high tech sources to take charge of immovable funds or for others fraudulent objectives by assuming the others identity or taking a nick name with fraud intent shall be sentenced not less than one year and Dh 30,000 fine or both.
Article No. 15
As per article No. 15, anyone abusing holy values, shrines or promoting and inciting sins will be punished or fined.
Anyone who is convicted to oppose Islam, abuse its principles or other religious missionary activities, which is for their benefit, shall be sentenced to jail for more than seven years.
Article No. 22
As per the article No. 22, anyone with the intention of acquiring secret information, logging into government websites shall be imprisoned. Actions that are made to harm, delete, or republish the data be sentenced to jail or fine.
Article No. 27
As per the article No. 27 of the UAE cyber crime law, individuals involved in the violation of the legislation can be accused and sent to jail or fined.
Article No. 28
Article No. 28 of the Cyber Crime Law of the United Arab Emirates (UAE) states that, “provisions contradict of this law shall be abrogated” (Gulf News Report, 2009).
Article No. 29
As per the article No. 29, every law will be effective after the first date of its issuance, and it will be published in the official gazette (Gulf News Report, 2009).
Conclusion
The Tackling of cybercrimes is important. From individuals to institutions, companies to governments even the armed forces are exposed to these crimes. Cybercrime is committed on a larger scale as compare to the conventional crime. Technology rapid progress in our society is increasing the awareness of its potential negative consequence. As they are providing the major podium for transactions or data transfer of governments, bank customer personal data and company communications have become a possible area for cybercrime. The technology is improving rapidly, and new advance methods are introduced to use systems. It is also leading the crime to the more effective and dangerous way. Criminals, robbers, hackers are using the computer to consign felony (Harb, 2007).
References
Coleman, K. (2009). Cyber Terrorism. Web.
Computer Crime Law – Guide to Computer Crimes Law. (n.d). Web.
Countries under surveillance. (n.d). Web.
Dutta, S., Karake, Z., & Samuels, G. (2007). Promoting Technology and Innovation: Recommendations to Improve Arab ICT Competitiveness. Web.
Europol. (2010). European Union Cybercrime Task Force. Web.
First Report and Order and Further Notice of Proposed Rulemaking. (2005). Web.
Gulf News Report. (2009). UAE cyber crimes law. Web.
Harassment. (2010). Web.
Harb, W. (2007). Programme on “Strengthening the Rule of Law in the Arab States –Project on the Modernization of Public Prosecution Offices”. Web.
Hughes, D. R. (2001). Sexual Predators Online. Web.
Joyner, C. C., & Lotrionte, C. (2001). Information Welfare as International Coercion: Element of a legal Framework. Web.
Kaul, S. (2003). Computer hacking: potentially a new kind of war in the Middle East. Web.
KEY LEGAL TERMS: BURGLARY VS. ROBBERY. (2009). Web.
Kirste, B. (2007). European Union. Web.
Krastev, N. (2010). In U.S. Cybercrime Case, Track Record Indicates Russia Willing To Cooperate. Web.
Oak, M. (n.d). Types of Computer Crimes. Web.
Pati, P. (n.d). Cybercrime. Web.
Roddel, V. (2009). Piracy and the Home Computer. (B. Nelson, Ed.). Web.
Roddel, V. (2009). The Four Kinds of Software Piracy. Web.
Schjolberg, S. (2008). The History of Global Harmonization on Cybercrime Legislation – The Road to Geneva. Web.
Telecommunications Fraud. (1998). Web.
The Free Library. (n.d). Saudi, UAE top gulf cyber-crime victims: report. Web.
Types of Cyber Crime. (2009). Web.
Types of Cyber Crime. (2009). Web.
UAE. (2010). Web.
United Arab Emirates. (2009). Web.
Walker, J. (n.d). Different Types of Cyber Crime. Retrieved November 21, 2010, from eHow: Different Types of Cyber Crime.
What is a computer virus? (n.d). Web.