Introduction/Literature Review
Cybercrime is an illegal activity that targets computer users and networks of devices for malicious reasons. Most cybercrime activities are undertaken by hackers and crackers who want to manipulate the online system to make money or for social and political initiatives. The phenomenon can be done by a person or organization, such as governments using advanced techniques which require competency in the internet of things (IoT), a tool powered by artificial intelligence (AI). According to Saini et al. (2012), cybercrime is “an act committed or omitted in violation of a law forbidding or commanding it and for which punishment is imposed upon conviction”. Therefore, it means the word carries a wide array of issues related to criminal activities facilitated by the intensive utilization of millions of computers and related systems in the contemporary world.
It is not easy to curl cybercrime issues in the businesses nowadays. Broadhurst (2006) says, “Controlling crime involving digital technology and computer networks will also require a variety of new networks: networks between police and other agencies within government, networks between police and private institutions, and networks of police across national borders.” Therefore, it is difficult to end the criminal activities done online without collaboration between agencies involved in cyber issues. For example, the Council of Europe’s Cyber-crime Convention (CoECC) shows efforts to build the global significance of the fight against cybercrime activities (Broadhurst, 2006). Other examples include the United Nations Convention (UNC) against transnational organized crime which deals with world criminal networks where a significant cyber safety risk is involved.
Methodology
This report used various articles that were available for consultation on cybercrime issues. A total of 14 sources were used to compile the data and bring conclusions based on the findings. Most of the sources used ranged between 2012 and 2020, with many being scholarly, meaning they have been peer-reviewed. The key terms for the search were the effects of cybercrime in businesses, types of cybercrime, and how to control cybercrime. The report is presented and arranged in professional and academic prose.
Types and Examples of Cybercrime
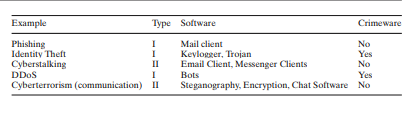
This type of cybercrime happens when an attacker monitors information streams from a given end where the details are collected for personal gain. It comprises sniffing into data network traffic and observing the streams such as radio (Choo & Grabosky, 2013). This requires the attacker to be consistent in monitoring frequent communications or may initiate an established data stream that probes users to get into the trap by participating in various online programs. The attacker can read the content from the explicit data channels. in this case, data can be intercepted or modified and distributed to third parties who tamper with it to gain their leads. For example, when an online user changes dollar amounts in a transaction from $100 to $10,000, an entire set of valid data may interject onto the network, repeating as many times as the attacker wants (Saini et al., 2012). An evident example is phishing emails, as seen in Figure 1 below, where hackers send emails to random users with links that can be useful in redirecting them to access financial data for the victims, which may end up robbing them virtually.
Network Crime
This type of cybercrime is one in which a computer network is interfered with where the attacker inputs, transmits, damages, and deletes a given network data, suppressing the information contained in the data set. For this type of crime to occur, a network must be interfered with or altered in a sabotaging manner for the user to dominate the network usage on their end (Choo & Grabosky, 2013). For example, identity theft is a common occasion where users fakes themselves to represent other parties without their official verification or consent. Various software that can undertake this type of cybercrime includes keyloggers, Trojans, bots, and mail clients (Gordon and Ford, 2006). For example, IM and FTP software can commission various functions. Hence, they cannot be fully said to be crimeware.
Access Crime
This type of cybercrime is where unauthorized access or virus dissemination is executed successfully. An insider’s view of a computer cracker underground is rampant in unauthorized access whereby a user can separate computer screens from manipulating files or media they want. Malicious software may attach to other software, such as Trojan Horse, Logic Bomb, and Rabbit (Tendulkar, 2013). In this case, a victim’s system is destroyed and may incur the cost of either changing the system or rebooting it to start from scratch, depending on the level of attack. Distributed denial of service (DDOS) is an example under this category where crackers access a host machine and freezes it such that no intended user can access it (Tendulkar, 2013). This threat harms organizations since there could be financial implications that may result adversely from access crime.
Impacts of Cybercrime on Businesses
Modern businesses are influenced highly by digital tools that transform or drive enterprises to meet revenue and profits. There are many aspects of how business is related to cyber activities. For instance, in the United Kingdom, 7% of the population, representing about 4 million individuals, have been the victim of identity fraud which has financial implications (Lagazio et al., 2014). Due to cybercrime, many companies have been exploited financially, making their online business transactions vulnerable to hackers and crackers. Increasing revenue is set to deal with access crime or network sabotage, which is commonly experienced in businesses (Lagazio et al., 2014). The digital innovations for upcoming business giants have been affected as the firms fear losses that may incur if attacked financially.
Additionally, when a company falls prey to cyber-attacks, the customers do not have the confidence to transact with the enterprise for fear that they might fall on the same track (Lagazio et al., 2014). Thus, it means businesses continually lose valuable leads due to uncertain events caused by cybercrime. There are trust issues where buyers may not be able to positively perceive an existing e-commerce channel, as seen in figure 2 below (Apau & Koranteng, 2020). Moreover, consumers have changed their attitude toward businesses, meaning the intention to purchase on e-platforms can vary due to rampant cybercrime issues. The conceptual framework of the above idea can be seen in Figure 1.
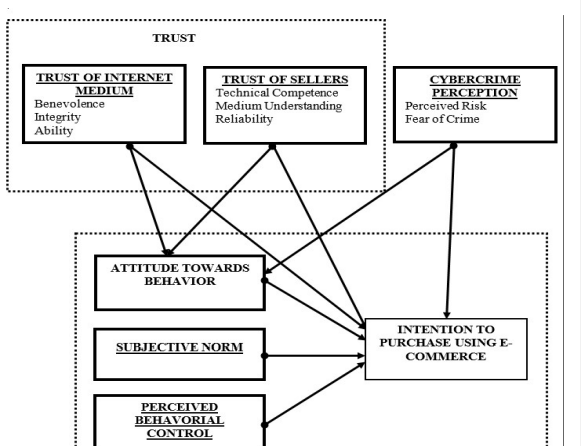
There is a major problem when it comes to combating issues that are brought about by cybercrime. The consequences can be felt in private businesses where alteration of financial planning can be rampant. According to xxx, a study undertaken on US companies shows that the “median annualized cost of cybercrime for 50 organizations is $5.9 million per year, with a range of $1.5 million to $36.5 million each year per company” (Das and Nayak, 2013). That comes despite the awareness of cyber threats on financial consequences in the said organizations. Therefore, cybercrime has brought financial strains when companies try to combat or respond to online attacks. Businesses fall victim to cybercrime but at different levels, and there is an economic impact.
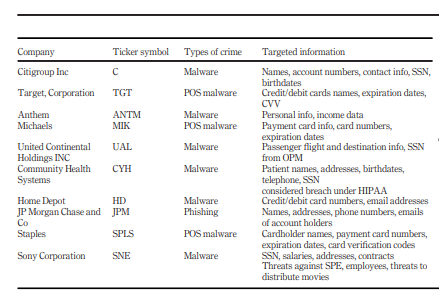
From the above details, the cost of protection, loss of sales, and uncertain business sustainability are the key effects of cybercrime on businesses. For example, Target Corporation announced been breached its cyber security in 2013, where more than 40 million credit card data was accessed (Smith et al., 2018). Many accounts were affected, and the customer’s credit and debit card details were sold in the black market for about $53 million (Smith et al., 2018). Table 1 shows a list of companies affected by cybercrime and its effects on their daily operations.
Table 1: Companies and cybercrime
The Cost of Cybercrime
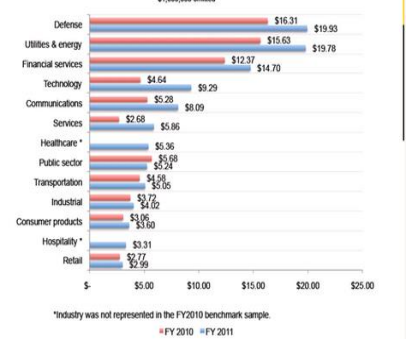
Combatting cybercrime is costly to organizations because the monetary implications for preventing and dealing with attacks is increasing daily. As seen in Figure 3 below, various industries have been affected by cyber-attacks worldwide as per the 2010-11 data. According to United Nations Security Agency (USA), the cost of cybercrime was approximately $385 billion in 2014 (Watkins, 2014). In the UK, the National Audit estimated the cost to be 18 billion Euros per year, whereas the US figures indicate roughly $100 billion per annum (Watkins, 2014). As of now, the cybercrime cost is around $6 trillion, which is projected by 2021. According to Morgan (2020), it is expected by 2025, the cost will go high by 15%, reaching an approximated figure of $10.5 trillion. That will be one of the most significant transfers of economic wealth since time immemorial, with risks towards innovation and investment in the business.
The costs are based on destroyed data, stolen funds, low productivity, and intellectual property theft, among others. The biggest contributor to this cost includes ransomware, which has reached epidemic levels. Morgan and Calif (2020) say, “A 2017 report from Cybersecurity Ventures predicted ransomware damages would cost the world $5 billion in 2017, up from $325 million in 2015 — a 15X increase in just two years. The damages for 2018 were estimated at $8 billion, and for 2019 the figure rose to $11.5 billion.” Thus, cybercrime is one of the drawbacks that may affect the world’s technicalities, economies of scale, and political realms.
Additionally, cybercrime has led to significant loss of business and intellectual property, which means increased costs in leveraging security, workflows, and company reputation for companies. In this case, firms that report major attacks end up dropping by 1.5% value of their stock (Watkins, 2014). For example, a Canadian-based company, Nortel Networks Limited, has fallen prey to Chinese attackers for many years, and it went bankrupt in 2009 (Watkins, 2014). All the impact was from the theft of critical data for the company due to cybercrime. Intellectual property theft has accounted for almost 75% of financial losses in businesses (Watkins, 2014). The US insurance sector grew by less than 100 million USD for yearly premiums (Watkins, 2014). Many Asian and European companies are observing a similar trend as cyber-attacks continue to cost their market values.
Actions Taken to Combat Cybercrime: How to Stop Cybercrime
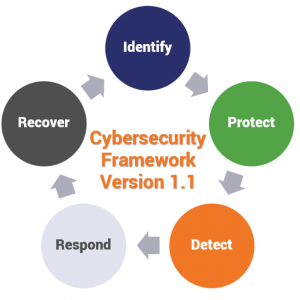
Cybercrime framework revolves around a series of processes that can curl online attacks. A company needs to identify, protect, detect, respond and recover any measure attempting to limit their cyber safety, as seen in Figure 4 below (Crane, 2020). Firstly is combatting through collaborative initiatives such as using investigative agencies such as the Federal Bureau of Investigations (FBI) to examine computer intrusions (Smith et al., 2018). Secondly, there are reporting mechanisms that effectively address the matter where the public can get reliable techniques that comply with a crime. That means operational and investigative support is considered while boosting research and innovation to counter the attacks. Various preventive measures can be employed to protect the cyber-related attacks. For example, keeping firewalls on to protect malicious users is important (Setiawan et al., 2018). Furthermore, an organization or a user should install antivirus software that is up to date to spy on any ransomware technology.
For instance, knowledge of how to use digital platforms is required to enlighten users about the dangers of using foreign private networks to download or transact online. Use of full-service internet security protocols is encouraged, such as using Norton 360 software that offers in-one protection for networks and handsets (Van de Mark, 2020). Lastly, it is important to protect devices or networks using key-in values that are not easily authenticated without the user’s consent. That includes suggesting strong passwords for various useful logins in a digital platform. For large organizations, offering training to employees and creating a system security plan (SSP) is recommendable since the practices keep data secure (Van de Mark, 2020). Enforcing a strong password policy is required for the employees or users in various levels of organizational business.
Conclusion
Cybercrime includes illegal computer usage, which targets organizations and users. An example of cybercrime is phishing, identity theft, and DDOS. Businesses have lost sales, incurred high protective costs, and experienced changes in consumerism trends. The cost of cybercrime is approximately $6 trillion, and figures may double by 2025. The preventive measures for cybercrime include preventive measures and a cybersecurity framework that uses a calculative strategy to monitor intrusions. Organizations must follow compliant measures that will enable effective combatting of cybercrime issues.
References
B. Watkins, “The impact of cyber attacks on the private sector,” Association for International affairs, 2014.
C. Crane, “How to prevent cybercrime: 9 helpful tips,” Hashed Out by The SSL Store, (Online). Web.
H. Saini, Y. Yao, and T. Panda, “Cyber-crimes and their impacts: A review,” International Journal of Engineering Research, vol. 2, no. 2, pp. 202–209, 2012.
K. T. Smith, A. Jones, L. Johnson, and L. M. Smith, “Examination of cybercrime and its effects on corporate stock value,” Journal of Information, Communication and Ethics in Society, vol. 17, no. 1, pp. 42–60, 2019.
K.K. Choo and P. Grabosky, “Cybercrime,” Oxford Handbooks Online, vol. 2, no. 3, pp. 23–34, 2013.
M. Lagazio, N. Sherif, and M. Cushman, “A multi-level approach to understanding the impact of cybercrime on the financial sector,” Computers & Security, vol. 45, no. 21, pp. 58–74, 2014.
N. Setiawan, V. cita emia Tarigan, P. buana Sari, Y. Rossanty, P. Nasution, and I. Siregar, “Impact of cybercrime in e-business and trust,” International Journal of Civil Engineering and Technology, vol. 9, no. 7, pp. 652–656.
R. Apau and F. N. Koranteng, “Impact of cybercrime and trust on the use of e-commerce technologies: An application of the theory of planned behavior,” International Journal of Cyber Criminology, vol. 13, no. 2, pp. 228–254, 2020.
R. Broadhurst, “Developments in the global law enforcement of cyber-crime,” SSRN, vol. 29, no. 3, pp. 1–26.
R. Tendulkar, “Cyber-crime, securities markets and systemic risk,” World Federation of Exchanges, vol. 3, no. 7, pp. 3–56, 2013.
R. Van de Mark, “Industry of anonymity: Inside the business of cybercrime by Jonathan Lusthaus,” Osgoode Hall Law, vol. 61, no. 5, pp. 1–8, 2020.
S. Das and T. Nayak, “Impact of cybercrime: Issues and challenges,” International Journal of Engineering Sciences & Emerging Technologies, vol. 6, no. 2, pp. 1–12, 2013.
S. Gordon and R. Ford, “On the definition and classification of cybercrime,” Journal in Computer Virology, vol. 2, no. 1, pp. 13–20, 2006.
[14] S. Morgan and S. Calif, “Cybercrime to cost the world $10.5 trillion annually by 2025,” Cybercrime Magazine, (Online). Web.