Introduction
This is a technical IT proposal for implementing Windows network infrastructure for Global Advertisement Inc. (GAI). GAI is a new advertising firm that will start operations with 90 employees spread across different departments such as Executives; Accounts and Sales; Advertising; Human Resources and Finances; and IT.
The company will have two sites located in Los Angeles and New York. The proposal provides GAI with a solution that describes the implementation and configuration of its core IT services. It involves the deployment of Windows Server 2012 Operating System for all aspects of the solution. This proposal provides GAI with the right solution to fit its needs now and for the next 2 to 3 years. It covers six core areas in Windows Server 2012.
New Features of Windows Server 2012
Windows Server 2012 comes with some great new features for users. The major improvements focus on private cloud infrastructures. At the same time, the OS offers opportunities to integrate traditional Data Centers. While these new features are numerous, the most notable ones are Hyper-V Virtualization and File and Storage management (Brown, 2012).
Hyper-V Virtualization
- Hyper-V Replica feature is enhanced for replication of virtual machines across Data Center, Clusters and storage systems
- Storage Migration allows users to migrate virtual hard disk to another physical location while the machine is in motion
- Storage on SMB2 file shares now supports SMB2 file sharing in virtual machine storage systems
- Virtual Machine Snapshots allow users to delete a snapshot and create more space without shutting down the machine
Improved File and Storage Services
- Data Deduplication: users can now store one copy of similar data
- Storage Spaces and Storage Pools: users can now create virtual disks or storage space by grouping similar disks into a single or more storage pools.
- iSCSI Target Server: the server can provide block storage to other different servers within the network through the iSCSI systems.
Domain Controller Cloning
The Active Directory Domain Services (AD DS) now allow users to add other additional domain controllers through cloning the available virtual domain controller. Users create copies and allow the source domain controller within AD DS to be cloned. This eliminates repetitive processes and time required in such processes.
Server Core
The new feature allows users to change between a Server Core install and GUI install by avoiding reinstallation of the OS. In other words, users can still perform administration roles when administering applications for GIU and then move to Server Core without interruption.
Deployment and Server Editions
GAI will require two servers and combine server roles. All roles that relate to Active Directory Certificate Services (AD CS) would be combined alongside Application Server, Desktop Experience, Failover Clustering, the File and Storage Services server, the Group Policy feature and Hyper-V role. Other combined roles shall include all Network roles, Print and Document Services, Remote Desktop Services, Security and Protection among others.
Per server mode is preferred with 90 authenticated users (90 CALs). These users will be able to gain simultaneous access to servers. The system shall deny any additional user access (Gilbert-Knight, 2012). Per Server mode will serve the company better because it is a small organization with limited access requirements (Gilbert-Knight, 2012). User CALs would allow employees to gain access to specific contents within a given server irrespective of their access devices. In other words, employees would be able to gain access to servers through their laptops, desktops, smartphones and tablets.
GAI will use Server 2012 Datacenter Edition. This edition works better in highly virtualized environments. In addition, it will also support unlimited number of virtual applications. The Server 2012 Datacenter Edition would have two physical server processors (Deuby, 2013). The company will purchase adequate Datacenter licenses to support the two processors (Deuby, 2013). Additional licensing information from Microsoft will explain all different types of all licensing.
Server Core would be used for administration roles and navigation between GUI install and Server Core install. The core OS requires minimal command and shall offer low maintenance with a reduced attack surface.
GAI would run an automated Windows Server 2012 to ensure compatibility with other applications and support smooth system upgrade.
Active Directory
GAI requires a single Active Directory to run its highly virtualized system. Windows Server 2012 has an Active Directory with simplified processes. It will enhance flexibility, support systems and provide simplified administrative experiences (Joos, n.d). The Active Directory would also improve virtualization of domain controllers.
The company will install Read-Only Domain Controllers (RODCs). RODCs shall offer alternative to other writable domain controllers. This would support other locations in which a server may not be found such as a secure remote location in case of any expansion. RODCs will offer roles of domain controllers without necessarily exposing AD DS applications to several system risks. Users, however, will not be able to alter the domain database on the RODC.
The AD DS database on the RODC shall not allow any modification requests from other applications and users. Users will send their requests to a single writable domain controller. Replication of the Active Directory changes will only take place through a writable domain controller in a single way.
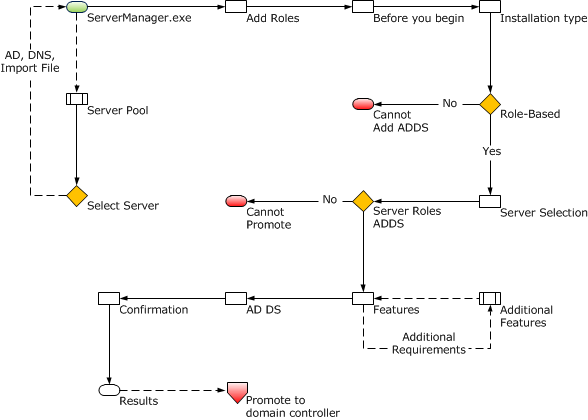
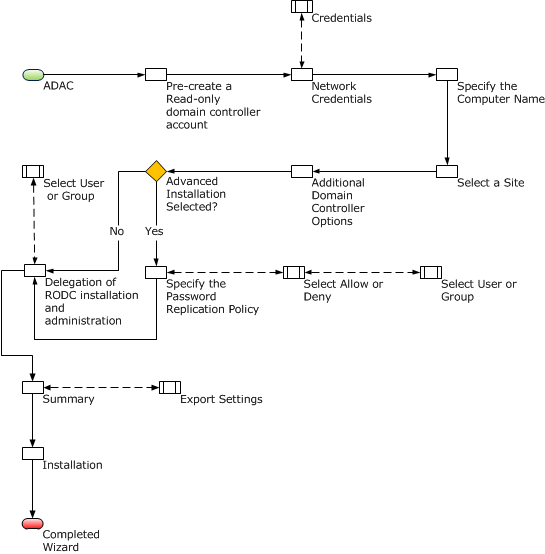
During configuration, the Additional Domain Controller Option dialog allows users to specify that a DNS Server and a Global Catalog are required. However, in Microsoft Windows, it is recommended to use Read-Only Domain Controllers so that both options are installed by default. In this regard, the Read-Only Domain Controllers would account for the branch offices, which may lack wide area network connections, as well as DNS and global catalog services. Therefore, such computers may lack AD DS resources and functionality.
By considering the group policy, the system will replicate employee and computer credentials to Read-Only Domain Controllers by default. In this sense, users must configure a Password Replication Policy (PRP) for clarification of credentials that can be cached to minimize security risks. Any users not included in the cached passwords may not gain access to a writable domain controller and other functionalities controlled by Active Directory (Install a Windows Server 2012 Active Directory Read-Only Domain Controller (RODC) (Level 200), 2014).
DNS and DHCP
DHCP scope design
DHCP would automatically distribute critical “IP configuration settings to network clients, eliminating the tedious and burdensome task of manually configuring hosts on TCP/IP-based networks” (Lanz, 2013). In addition, DHCP shall provide “configuration information and interact with other networking services such as domain name system (DNS), windows deployment services (Windows DS) and network access protection (NAP)” (Lanz, 2013).
Lease time will be increased to 12 days because of the large number of IP addresses available. Increased lease time shall reduce cases of lease renewal queries. Consequently, there would be reduced network traffic originating from renewal requests.
The fastest client transaction rate of at least 500/sec will be considered when defining the number of scopes of the DHCP. The address range will include 192.168.1.1 to 192.168.1.100. Additional ten addresses could be included to support portable devices while specific range would be defined for such devices.
The system will increase fault tolerance by dividing the DHCP scopes. The scopes shall be split between the two servers at the ratio of 20:80 for optimum benefit. This ratio would allow servers to handle DHCP traffic flood faster. Moreover, any failure in the servers may not affect the network.
DHCP reservations will be used for servers to define IP addresses for various access devices (desktops, laptops and mobile) available in the company while all IP address processes will be defined at the scope level.
DNS namespace design shall be defined before the deployment of the DNS system. Internal namespace is recommended for the company so that it only remains accessible to employees within the internal network. An administrator shall maintain and manage all other functions. The DHCP and DNS infrastructures will be integrated to allow for system updates, particularly for additional or new devices or when IP addresses of devices change on the network. GAI shall have split DNS for Internet/intranet to eliminate administration burdens and system complexity involved in host configuration. DHCP Server service would offer alternative automatic configuration.
The second site will have DNS service for user login to reduce traffic directed to the VPN. Configuration shall allow users to gain access to the DNS Server, which would serve as the main DNS.
Application Services
Application Server is a part of the OS that provides an integrated platform for deploying and operating customized server-based software. Running applications handle all requests from remote users or from other applications.
Active Directory will be used to deploy applications within the Group Policy. Group Policy would ensure network security. GAI shall rely on user or computer assigned applications in the Group Policy. This is a simple process involving a group action, which ensures that users see new installed applications when they login into the system.
An administrator shall create MSI file before the system deployment to support other applications in the shared network. In addition, all authorized users shall have permission to share files and printers. The Group Policy would remain hierarchical. Therefore, the administrator shall be careful to ensure that established policies only affect the right users.
Some of the software packages that will be installed include Windows Installer packages (.MSI files), Transform Files (.MST files) and patch files (.MSP files).
File and Printer Sharing
GAI shall have file and printer sharing capabilities across its departments. Windows Server 2012 has File and Storage Role as a default setting. Therefore, users can create file sharing with limited interventions in a new server.
It is necessary to include DFS for reliability and supportability. DFS will rely on direct field and MS Support results. Server scale-out for data application shall be included in the configuration. This platform would allow users to store application such as “Hyper-V virtual machine files and on file shares, which are online on all the nodes simultaneously” (Bruzzese, 2013). Server scale-out would benefit from file sharing from all nodes through SMB 3 clusters.
Windows Server 2012 ensures data and file availability when required and therefore, there will be no need for a dedicated SAN (Bruzzese, 2013). Scale-out and continuous availability would enhance file sharing while “NIC teaming, multipath I/O, support for offloaded data transfer (ODX), and single-root I/O virtualization (SR-IOV) support shall highlight some of the Windows Server 2012 benefits.
Quotas/FSRM configuration shall account for File and Storage Services, File Services and File Server Resource Manager. In addition, there will be notification limits, storage reports, report locations, file screen audit, automatic notification and access denied assistance. Setting quotas will ensure that users can control disk space for various folders and sub-folders. Soft quota shall be used to monitor disk space and provide reports.
Summary
This technical IT proposal for implementing Windows network infrastructure for Global Advertisement Inc. (GAI) has captured the most important aspects of Windows Server 2012. The proposal has shown that GAI will benefit greatly from new advanced features available in Windows Server 2012. Some of these new features include Hyper-V Virtualization and File, Storage management, Server Core and Domain Control Cloning among others.
It is imperative to recognize that Windows Server 2012 for the company shall run on Datacenter, which could provide a highly virtualized environment for the company. This strategy would reduce costs in servers, enhance network security and system scalability for future expansions. In addition, it will cater for various access devices.
Users will experience flexibility in defining their preferred settings. Moreover, the system shall provide greater security through various applications and user restrictions based on the Group Policy, Read-Only Domain Controllers and automated updates with compatible applications. Overall, GAI will achieve greater benefits by installing Windows Server 2012.
References
Brown, M. (2012). Windows Server 2012: An Overview of New Features. Web.
Bruzzese, P. (2013). Windows Server 2012 brings high-availability file shares. Web.
Deuby, S. (2013). Windows Server 2012 Deployment. Web.
Gilbert-Knight, A. (2012). An Introduction to Microsoft Server and Client Licensing. Web.
Install a Windows Server 2012 Active Directory Read-Only Domain Controller (RODC) (Level 200). (2014). Microsoft. Web.
Joos, T. (n.d). Better Active Directory with Windows Server 2012. Web.
Lanz, W. (2013). Windows Server 2012 DHCP (Part 1). Web.