Though providing its users with a range of efficient tools and opening new opportunities for communication, digital technology has become a part and parcel of not only casual communication, but also business interactions. However, due to the dents in the security of the digital data, the necessity to upgrade security analysis consistently emerges.
At present, an array of tools is used for enhancing the security of online data. Specifically, the tool such as the Web Security Threat Classification, contributes to a major enhancement of the security rates for a certain database. The Web Application Security Statistics tool created by the Web Application Security Consortium (WASC) uses the statistical data gathered from the Internet in order to create a framework for detecting the potential threats to the security of databases by identifying the existing vulnerability classes and designing testing methodologies for locating these vulnerabilities.
The tool in question allows for both manual and automated processing of data with the following compilation of the representative statistical data. The latter, in its turn, allows for differentiating between the vulnerabilities found based on their risk level.
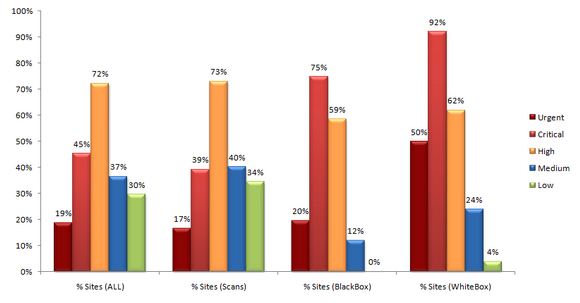
The graph provided above shows that the methods adopted are applied successfully to detecting the key types of safety issues by splitting them into urgent, critical, high, medium and low.
The above-mentioned theory of numbers plays a huge part in enhancing online data security. Particularly, the theory in question provides the methods for designing the tools in question and carrying out the analysis of the existing threats. To be more exact, the number theory allows for carrying out the cryptographic computations, which support secure communication and eliminate the existing vulnerabilities. For instance, by creating a digital signature to a message, one is capable of verifying the integrity of the message in question, therefore, protecting one’s personal data from a possible exposure. The design of a digital signature, in its turn, is carried out with the help of the cryptographic processes (encryption/decryption).
The confidentiality issue, which is often identified as the key problem in the process of online communication, in its turn, can be resolved with the help of the RSA cryptosystem, which is also an essential concept in the number theory. Though the RSA approach itself has already been washed away by the sands of time, the principle, which it is based on, i.e., the fast Fourier transform, is still adopted in designing modern strategies for detecting threats and preventing them within online environment. To be more exact, the aforementioned approach qualifies for creating digital signatures with the help of the following formula:
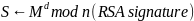 .
.The verification of the signature, in its turn, is carried out with the help of the following formula:
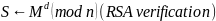 (Goodrich & Tamassia, 2010).
(Goodrich & Tamassia, 2010).Though the effects of the WASC’s activities may not be as evident as they should, the work that has been done is still beyond impressive. As the Table 1 below shows, a total of 178764 vulnerabilities have been detected with the help of various tools for a mathematical analysis designed for detecting issues in the security system.
Table 1. Vulnerabilities Statistics (2010) (WASC, 2010, para. 11).
Reference List
Goodrich, M. T. & Tamassia, R. (2010). Chapter 10. Number theory and cryptography. In Algorithm design foundations, analysis, and internet examples (pp. 453–508). New York, NY: John Wiley & Sons, Inc. Web.
WASC. (2010). Web application security statistics. Web Application Security Consortium. Web.