Introduction
The research will mainly deal with finding out a convenient network security technology that will suit corporation business operations. One of the network security concepts includes authentication, once a user is authenticated (allowed access to a computer) a stateful firewall puts in place administrative policies. Firewall security is the most popular technology used by most corporations to provide security to their networks, although it is effective it has a few flaws which include; failure to verify potential destructive substances such as worms transmitted through the network, failure to discover and stop the exploit of malware (malicious code), firewalls also can not be able to supervise the network to test for unsuspicious substances such as unpredicted traffic and other anomalies (Zamboni, 2000).
A corporation can enhance its network security by adopting emerging network security technologies that are more competent and encompass all security features in its platform. Network intrusion detection system (NIDS) is one of the examples of such technologies. It is different from a firewall in that while a firewall search externally for intrusions so as to stop them from taking place, a network intrusion detection system (NIDS) evaluates an alleged invasion once it has occurred and reports by signaling an alarm. A network intrusion detection system (NIDS) as well watches for invasions that begin in a system; this is conventionally achieved by investigating network interactions, identifying heuristics and structures of familiar system invasions, and alerting operators. An example of a network intrusion detection system that is recommended for organizations is Snort. It is highly recommended for organizations because; it is able to identify unauthorized attempts that access, manipulate, and disable computer systems, mostly via a network, such as the Internet (Zamboni, 2000).
Firewall protected network of a corporation
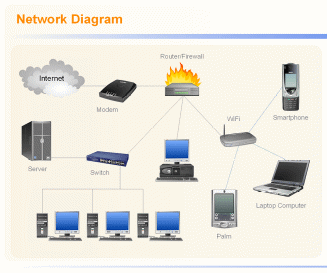
A probable network structure for an organization will be as shown above. Several workstations will be joined together to a switch to form a local area network. Depending on the size of the network, it will be divided into domains with each domain having a server. The switch for a local area network will be connected to a router which in turn connects to a modem that connects the corporate network to the internet. Wireless networking devices can be introduced to the network via a wireless access point.
The firewall which offers security to the network is applied at the router level which will authenticate users who wish to have access to the network and administer policies such as what services will be available for network users.
Snort components
Snort consists of a range of components that work jointly to execute the work of detecting attacks the major components include;
Packet decoder: Takes packets from a range of network interfaces and prepares the packets for preprocessing or sends them to the recognition engine.
Preprocessor: Preprocessors investigates data packets for anomalies and generate alerts in case it detects any. They can as well be used for packet defragmentation i.e. breaking down a large packet into smaller pieces that are manageable.
Detection engine: The detection engine in Snort is in charge of detecting an invasion in a packet. It carries out Snort rules to accomplish this task. The Snort rules are converted into interior data structures where they are harmonized alongside all packets. If a packet matches one of the rules, suitable action is carried out, if no the packet is dropped. Suitable action may be logging the packet or producing alerts. The pace of snort depends on the pace of a node and the number of rules defined by a user.
Logging and alerting system: A packet possibly produces an alert or log action depending on the discovery of the detection engine. The log and alert files are stored beneath diverse folders.
Output Modules: Carries out diverse operations depending on how a user wants to save output generated by the log and alert system. Generally, the modules manage the type of output produced by the log and alert system. Output modules functions may include; logging to a file, sending traps, sending messages to a Syslog facility, logging to a database, generating extensible markup language, modifying router and firewall patterns, and sending server message block messages to Microsoft based machines. Other apparatus may be used to propel alerts in other formats such as email messages or viewing alerts using a web interface.
Snort rules
Fake actions have some signature; the fake signature information is used in the formation of snort rules. Imposters use a database of recognized weaknesses to launch an invasion; these recognized invasions are used as signatures to discover if there is somebody who wants to utilize them. The signatures may exist in the heading or body of a packet. The snort recognition system is based on rules and in turn, the rules are based on fake signatures, the rules are used to verify the different parts of a data packet. A rule may be used to produce an alert message, log a message, or pass a data packet. Snort rules are drawn using a simple syntax in a single line though they can be divided into numerous lines using a backslash makeup at the end of lines. They are typically reserved in a pattern file by including them in the major pattern file. Snort rules function on network internet protocol level and transport control protocol level; there is also the existence of numerous methods which are used to discover anomalies in data link level and application-level protocols (Crosbie, 1995).
First bad rule: This rule tests if Snort is functioning fine and is capable of generating alerts. It will produce an alert message intended for each Internet protocol packet captured. The rule is thought to be bad because it does not pass any information; it examines if Snort is functioning appropriately once it has been installed. The examination involves conveying a packet to a user’s gateway address or some other host machine on the network using a specified control (Crosbie, 1995).
Each Snort rule has two rational parts, rule header and rule options. The rule header has information regarding what action a rule executes and the criteria to be used for harmonizing a rule alongside data packets. The options part typically has an alert message and information regarding which part of the packet should be used to produce an alert message; it also has extra criteria for harmonizing a rule besides data packets. The action portion of a rule determines the type of action to be carried out when a criterion is met and a rule is accurately harmonized besides a data packet. Classic actions involve generating an alert or log message or triggering an extra rule (Crosbie 1995).
The protocol part is used to relate the policy on the packets for a given protocol only; it is the initial criterion declared on the policy. The address partdescribesethe basis the and target addresses. Address maybe of a single host, many hosts or network addresses. A user can employ these fractions to bar some addresses from an entire network. It should be important to note that there are two address parts in the rule i.e. basis and target address which are determined by the track field. In case it is a transport control protocol the port fractions determine the basis and target ports of a packet on which the rule is practiced while in case it is a network-level protocol like internet protocol port numerals have no importance, the track part of the policy determines which address and port numeral is used as a basis and which one as target.
Rule actions: The action is the initial part of a Snort rule; it shows what actions will be executed when rule conditions are met. An action is executed when all the circumstances named in a rule are factual. There are five predefined events though a user can describe his events as he desires. It is of significant importance to keep in mind that different Snort versions relay rules in different ways that are, in some snort versions. If many rules correspond to a given packet only the first one is practiced; after practicing the first rule, no more events are taken by the packet though in other versions, all rules are applied before producing an alert message and the main strict message is then produced. Some of the events generated by Snort include; Pass which is an event that informs snort to pay no attention to the packet, log event which is an event that is used to log a packet, Alert event which is used to propel an alert memo when rule situations are factual for a given packet, an active event which is used to produce an alert and then to invoke an additional rule for scrutinizing more situations, Dynamic event rules which are called up by the trigger event and finally user described events which are described by a user (Crosbie, 1995).
Protocols: A protocol is the third part of a snort policy; it displays which kind of packet the policy will relay. Snort supports numerous protocols; the major protocol is the Internet protocol (IP). In an Internet protocol, snort investigates the link-level header to decide the packet type and if any other protocol is used. Protocols participate in the function of specifying criteria in the header part of the rule. The options part of the rule may have extra criteria unconnected to the particular protocol.
There are two address parts in a snort rule. The addresses are used to verify the basis from which the packet came from and the target of the packet. The address may be a solo internet protocol address or a network address. A user can use one keyword to relay a rule on all addresses. The address is followed by a slash of a character and a number of bits in the network mask. Snort offers means to keep out addresses by the use of a reversal sign, an exclamation tip. The sign is used together with the address to direct snort not to investigate packets originating from or heading towards that address. The rule is significant when a user needs to check packets that do not originate from his home network.
A Port numeral is used to relay a rule on packets that originate from or head to a given port or a range of ports. Port numerals are helpful when a user needs to relay a rule merely for a given type of data packet for example if a weakness is linked hypertext transfer protocol (HTTP) web server, a user can use port number 80 in the rule to sense anyone attempting to use it; by this way, snort will relay that decree merely to the web server transfer and not extra transfer control protocol packets. A user can also use a range of ports in place of one port in the port field. In addition, while cataloging port numbers, a user may use merely the beginning port numeral or the ending port numeral in the range. A reversal sign can also be used with port numerals to keep out a port or a variety of ports from the span of the snort decree.
How snort works
Snort detects numerous types of malicious characters that can threaten the security and confidence of a system. This includes; network invasions against weak services, data motivated invasions on applications, mass based invasions such as freedom appreciation, unlawful logins and access to confidential files, and malware which include Trojan horses, viruses and worms.
Snort is made up of several elements which include; Sensors which create safety measures, Console which monitors proceedings and alerts and directs the sensors, and a central Engine that records proceedings given access by the sensors in a database and uses a coordination of rules to create alerts from safety proceedings received (Crosbie: 1995).
Snort is an intrusion avoidance system and intrusion recognition system and is able to carry out packet sorting and instantaneous traffic scrutiny on Internet protocol networks. Its functions include; carrying out protocol scrutiny, substance probing/harmonizing, and is mostly used to vigorously obstruct or submissively spot a range of invasions and probes for example; buffer overflows, craftiness port scans, web application invasions, and operating system fingerprinting trials, amid extra features. The software is typically meant for intrusion avoidance purposes by plummeting invasions as they occur.
Snort is highly recommended for business corporations because it can be shared among other softwares for example SnortSnarf, sguil, OSSIM, and the Basic scrutiny and Security Engine to offer a visual illustration of intrusion data. With patches for the Snort source from Bleeding Edge fears, support for packet stream antivirus scanning with ClamAV and network abnormality with SPADE in network layers 3 and 4 is possible with historical observation (Crosbie, 1995).
LAN integration issues
The deployment of Snort into a LAN will be determined by the duration a corporation wishes to deploy it, we categorize the deployment in to three categories; short term, mid term, and long term deployments.
For short term deployment, Snort will be administered outside the perimeter firewall to act as an invasion detector and early warn the system against an invasion. Snort can also be administered inside the perimeter firewall to detect invasions that pass the firewall. It can be administered on DMZ servers and on servers with highest security demands (Crosbie, 1995).
For mid term deployment Snort should be administered on all points where data leave or enter the borders of the corporate territory that is where corporate local area network is connected through leased lines or where dial up services provide remote access. Snort should also e administered on internal servers with high security demands.
For long term deployment Snort should be administered on all servers which are important for corporate communication and access to corporate data such servers include domain name servers, data warehouses and file servers. Snort should also be administered at local area network core switches fro maximum coverage at reasonable cost (Crosbie: 1995).
Snort Technical specifications
Snort technical specifications define the tools and plugins that are required for it to run on both Windows and Linux operating systems. Some of the plugins and tools required include Query-builder and search interface for discovering alerts and harmonizing alert meta information (e.g. name, discovery time) on top of the fundamental network proof (e.g. basis/end address, ports, load, or flags); the second one is Packet viewer which graphically demonstrate the level three and level four packet information of logged alerts; and lastly, Alert management which offers constructs to sensibly cluster alerts to generate incidents (alert clusters), erase the handled alerts or fake positives, transmitting to electronic mail for cooperation or archiving of alerts to transport them among alert databases, Chart and information creation based on time, feeler, name, set of rules, Internet protocol address, Transport control protocol ports, or classification (Crosbie:1995).
Analysis Console for Intrusion Databases (ACID): This is a scrutiny engine which searches and processes a database of safety incidents produced by Snort.
Database Plugin: Is an output plug-in which permits Snort to register its alerts to a range of databases.
XML Plugin: Is an output plug-in which permits Snort to produce alerts in XML layout and log them over a range of mediums.
Snort Rules: This are Snort set of laws file analyzer which gets rid of irrelevant set of laws (Crosbie: 1995).
Snort feasibility study
Before an organization can begin using Snort, a few changes in the organization have to take place which at the beginning will be costly for the organization. First the organization has to change its network structure i.e. there some new devices that support Snort that have to be added to the network for example a new network intrusion detection machine may be added to the existing network. The organization structure also has to change this will be due to the need of recruiting skilled employees who have knowledge on Snort operations. The organization will use a lot of money in training its current staff on the operations of Snort (Langendorfer: 1995).
Although at first a corporation introducing Snort will have to incur added expenses there are long-term benefits, some of the benefits include; Snort is an open source software so snorts updates will be provided free and the organization can download them from the internet for free, Snort updates come frequently therefore a corporation network security system will be able to handle new threats, finally the organization security structure will be made stronger because potential network security threats will be reported in advance and be halted before they occur (Langendorfer: 1995).
Operations Plan
The best place to locate snort will be behind an existing firewall or router so that all internet traffic will be visible to Snort just before it enters the switch or hub connecting an organization local area network. Incase the organization uses a switch to connect its local area network then Snort machine will be connected to the spanning port of the switch. This will ensure that all data flowing among the corporation servers will be visible to the Snort machine. Incase hubs are used for connection of the local area network then the Snort machine will be connected to the network hub right behind the firewall in this case all in coming and outgoing traffic will be visible to the Snort machine(Spanford: 1995).
The network diagram shown at the beginning of the research shows that the corporation’s Local area network uses a switch to connect all the nodes in the network and a firewall lies right behind the modem and the switch. It will be advisable in this case to introduce a Snort machine and connect it to the local area network via a spanning port of the switch. This means that the change made to the previous network will only be the inclusion of a snort machine right behind the firewall.
Another technology that is suitable to use would be Untangle because it offers a wide variety of services to a corporation the services include;Anti-spam, Web Content Filtering, Antivirus, Anti-phishing, Anti-spyware, Intrusion prevention, Firewall, Open Virtual private network, Router Protocol Control, Attack Blocker, Reporting, Policy Manager, and Kaspersky Virus Blocker (Spanford: 1995).
Conclusion
This research covers the importance of using emerging security technologies to traditional setups used by most corporations. From this research a user can learn on the various components that make up Snort, some of the rules that snort applies to perform its functions, how snort carries out its functions, some of the integration factors a corporation has to put in to mind before it considers using snort for network security purposes and lastly the technical specifications of snort.
A corporation will benefit greatly if it adopts Snort this is because, snort will evaluate an alleged invasion once it has occurred and report by signaling an alarm. It will also watch for invasions that begin in a system; this will be achieved by conventionally investigating network interactions, identifying heuristics and structures of familiar system invasions, and alerting operators. This in turn will help the corporation save on the cost of employing intensive data backup’s cause of the fear of its network security.
References
- S.Petri and H.Langendorfer. Load Balancing and Fault Tolerance in Workstation Clusters. Pearson Prentice Hall. 1995, pp.25-36.Spafford, E. H.; Zamboni, D.: Intrusion detection using autonomous agents, in Computer Networks. Elsevier, Volume 34, Issue 4, 2000, 547-570.
- Crosbie, M.; Spafford, E. H.: Applying genetic programming to intrusion detection, ResearchIndex/CiteSeer. Nov1995
- Crosbie, M.; Spafford, E. H.: Defending a Computer System using Autonomous Agents, Baltimore, MD, 1995, pp549 – 558 Ulf Lamping: Ethreal developers guide.