Executive Summary
This study focuses on a risk management process for implementing a new IT program to store patient data. The risk management process is defined by a scope statement, which includes different risks, deliverables, risk types, and risk changes, which include software and hardware changes. The critical elements involved include scope creep, dependencies, risk management methods to be applied for risk control, and a process for identifying project risk exposure based on a risk classification document.
The risk management process is implemented by focusing on internal and external risk management processes, software modules to be used, risk management methods, risk identification and evaluation, and a risk communication and consultation plan to ensure conflicts do not arise in the risk management process. There is need to establish a risk management committee at the beginning of the project to take the responsibility of managing the project risks. The entire process of risk management is critical to successfully implement the new IT program to store patient data.
Project Scope of the New IT Program to Store Patient Data Project Overview
According to Andersen (2006, p.12), the scope definition document of the risk management process of implementing a new IT program to store patient data is done to ensure that the overall risk management process is done according to an acceptable framework for the entire project lifecycle. Culp (2002, p.32) argues that the scope statement is a critical document because it provides the project manager and stakeholders with the ability to understand the project risks and enables them to formulate the best strategies to manage and control the risks. This project’s scope statement consists of the project description, the purpose, project completion criteria, project start and finish dates, project purpose, dependencies, staffing requirements, risks, project costs, and the technology to use. This project will be limited to the risk management process throughout the project implementation lifecycle, which is the first and most critical element to consider (Damodaran 2007).
The scope of this project is to implement a new IT program to store patient data and is defined by the risk management plan, which covers different aspects of the program implementation phases (Damodaran 2007). The new IT program to store patient data provides functionalities to capture and store patient data into a repository. It enables patients to consult physicians, by enabling them to capture and store clinical patient data and enables the users to generate accurate and reliable information about for decision making. The purpose of the project is to enable medical personnel and especially physicians to generate information from the system, and enable them to make judments on the best diagnosis to provide for their health problems to improve healthcare service delivery.
The project manager experienced a number of challenges when implementing the program, which included new project risks, which the project team had the obligation to manage. The rationale for managing the risks was to ensure patient data was protected and the system complied with health standards such as HIPAA, and that the risks were appropriately managed (Damodaran 2007).
According to Vose (2000, p.45), the risks involved in the project scope can be identified based on the deliverables in each phase of the project implementation lifecycle and includes change risks, scope creep, hardware defects, changes in the scope gap, dependency changes, integration defects, and software defects. Infrastructure changes that were unanticipated for such as version changes and hardware upgrades were identified to be some of the new sources of project risks (Vose 2000).
Change risks
The implementation of the project is likely to happen if critical issues arise during the implementation process. Vose (2000, p.45) argues that the risk for change is possible and should be a critical factor to consider because changes to the original scope, which often happen in projects is done by minimising the requirements at the initiation stage by using a robust risk management process to control the risks. The possible scope changes that were identified with the system are discussed below.
Scope Creep
This was identified to be a critical risk which has the potential to damage the entire project implementation process. Scope creep depends on the internal factors of the organisation and could result in an average schedule slip of weeks (Six & Kowalski 2005). In this case scope gaps did not cause any significant impact on project progress, but their existence and the frequency of occurrence was thought to have a greater cumulative impact on the project schedule. To address the problem, a detailed project evaluation method was used to provide information about poorly defined risks (Vose 2000).
An analysis of the project showed that the sources of scope creep were from different directions including the inside and outside of the project. A project tracking progress report provided information about the likely sources of project scope creep and the approaches necessary to counteract the risks (Six & Kowalski 2005).
Scope dependencies
Factors that were external to the organisation were the cause of scope dependencies and were inclusive of the changes in scope of the risks. In this case, the timing of the current project constituted one of the critical project risks that the project manager has to consider (Six & Kowalski 2005).
Risk management method applied
While there are a number of risk management methods that can be applied when implementing IT projects, the current project management and implementation team conducted a risk exposure of the project, evaluated and assessed the assets used in implementing the project, evaluated the value of the new information system, and the importance of each project implementation phase to determine the type of risk management methods to apply in each phase of the project (Raftery 2003).
In this case, the risk management method included the technical scope and project implementation scope. It was established that when implementing the information system for capturing, storing, and generating patient data, the risk of exposing patient health data to unauthorised people was high (Raftery 2003). Patient data has to be kept private and confidential and only authorised people can be given access to the data and for a specific purpose only. One of the risk management methods to use was a risk register for documenting all types of project risks. In addition, the risk register showed the impact each risk was likely to have on the project in each phase of the project and when the system was running (Vose 2000).
In this case the project risks were classified into negligible, minor, moderate, major, and catastrophic. According to Frenkel, Dufey, Hommel and (Rudolf 2005, p.34), the risk register consists of risks, which are classified into low, medium, and high. It consists of a risk matrix that shows the severity and extent to which risk applied controls can mitigate the risks. It was also important to create a risk matrix to understand the risk appetite of the company (Frenkel, Dufey, Hommel & Rudolf 2005). The risk assessment grid, which was used to analyse the project risks is shown below.
The risks were classified into external and internal risks. External risks originate from the outside of the organisation and are beyond the control of the organisation while internal risks can be controlled by the project manager are internal to the organisation (Frenkel, Dufey, Hommel & Rudolf 2005).
Establishing the context
The context of the risk management plan for implementing the new IT program to store patient data was established by creating a risk management structure for identify the departments, which could use the system to generate patient information. That included the internal and external context of the risk management plan. It was important to evaluate the risk management process against project success factors. In addition to that, the risk management process included identifying the roles of the different team members within the organisation, the risk control process, risk reporting, and risk reviews as discussed (Frenkel, Dufey, Hommel & Rudolf 2005). Typically, the project risks include management related risks, project risks, technology related risks, and resource related risks. In addition to that, it was necessary for the management to evaluate the return on investment by considering the financial and the human resource requirements to successfully implement the project.
Internal context
According to Lupton (1999, p.34), the internal context of the risks involved in the implementation of the project includes an assessment of the risks associated with organisational unpreparedness. Organisational unpreparedness includes an evaluation of the extent to which the medical facility is prepared to accept the new IT project. In addition, it involves an assessment of the team available to implement the project, and the risks involved if the appropriate team to implement the project is not available. The risk of rushing to implement technology before a complete analysis provides an additional challenge to the project manager (Lupton 1999).
It was important for the project manager to ensure that sufficient funds and resources were made available to carry out the project. Here, the possibility of ignoring the project details could impact adversely on its progress and cause a lot of loss and damage. In this case it is critical to develop standard definitions of key project terms, ensure that standard revision controls are in place and ensure that management issues are approached appropriately (Lupton 1999).
The risks associated with the current project were failure to comply with existing patient record standards, failure to obtain complete management support in implementing the project, a poor estimation of organisational structure, and the failure to redesign the data capturing and information generating methods. In addition, if the project goals, conflict with the management plan, metrics for evaluating project progress, change and risk management plans, motivation of the project teams, and cost and time management strategies, the risk of successfully completing the project will be experienced.
It is important to consider the risk of vendor partnership and support, poorly integrated components of the information system, poor and inefficient automation of the system, the loss of data, and the design and implementation issues that disrupt project progress (Lupton 1999). In the organisational context, the modules involved in the implementation of the system include:
- Clinical and medical records management.
- Medical schemes and insurance claims.
- Theatre procedures and billing.
- Clinics bookings.
- Patient registry.
- Email/SMS.
- Pending appointment reminder.
- Final diagnosis.
- Track procedures and medication prescribed.
- Family planning analytical reports.
- Patient observatory history.
The departments to be served by the new IT program to store patient data include:
- Medical department.
- Pharmacy department.
Other departments are shown in the diagram below.
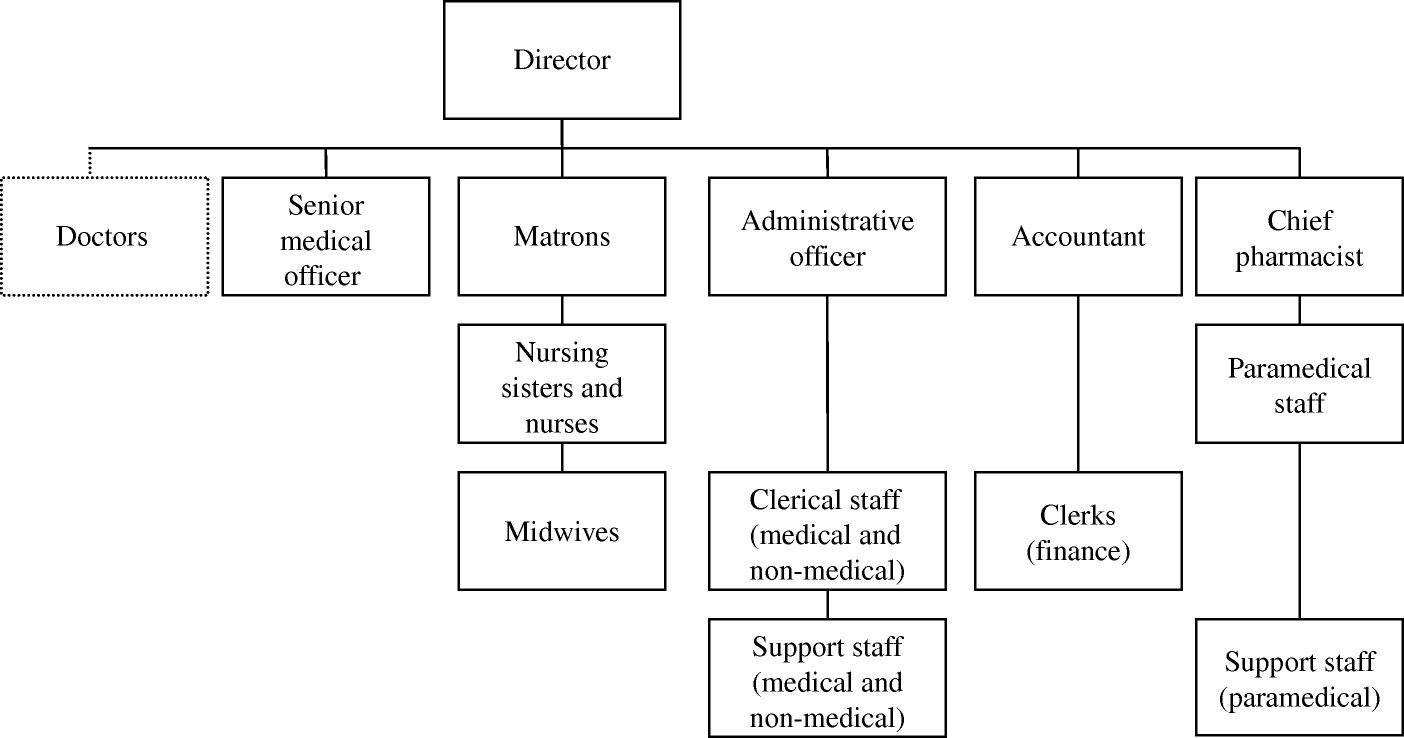
External context
Events which are beyond the control of the management, the project manager, and the organisation itself were identified to be the sources of risks to the organisation, which the project manager was to be prepared to handle. In addition to that, external risks are associated with database risks because it is the repository of patient data. Unauthorised access to patient data using malware such as phishing to penetrate the information systems was another system risk that could affect the effectiveness of the system (Kaplan 2009). In addition to that, malware can infect the repository of data and corrupt patient data, weak audit trails which could compromise the system and expose the system to being at odds with requirements of the Sarbanes-Oxley (SOX), the Healthcare Information Portability and Accountability Act (HIPAA), and the government regulations (Kaplan 2009).
Risk management context
The risk management context was related to the discovery and identification of the information systems project risks when implementing the new IT program to store patient data. In that context, the risk management processes required putting in place risk control measures to ensure that risks were reduced to the bare minimum and were consistent with the risk appetite of the organisation (Kaplan 2009). The project manager ensured that the right risk control measures were selected based on the documentary evidence provided by the use of a risk analysis document, which provides a list of the possible risks and risk control measures. The risk control measures include a number measures that were be put in place to address the risks depending on the classification of identified project risks, which were categorised into remaining risks, current risks, and initial risks (Kaplan 2009).
According to Frenkel, Dufey, Hommel and Rudolf (2005. P43), the most critical element was to ensure that the risks were evaluated and analysed continuously by taking individual measures such as assessing the use of time to control and minimise risk.
Stakeholder analysis
The level of tolerance to risk depends on the risk appetite of the organisation. However, the project was not expected to fail and the success of the project is depends on the internal and external stakeholders (Damodaran 2007). The table shows internal and external project stakeholders. Each of the stakeholders has a unique interest in the implementation of the new system and the following discussion focuses on the stakeholders.
The stakeholder interests are shown in the table with varying intensity as shown in the following diagram.
Communication and consultation
The risk communication plan was put in place to ensure that the risks were clearly understood by the project stakeholders and the risk management strategies were clearly agreed upon (Damodaran 2007).
In any project implementation lifecycle, communication is a critical tool that enables project team members to work effectively to avoid conflicts and wastage of time and other valuable resources. Usually the project “communication plan must consist of the internal and external communication plan so that the project manager can communicate with internal and external project stakeholders effectively” (Damodaran 2007)
Internal communication
In the above case, internal communication plan was put in place to ensure that employees working in the project had sufficient information to work on and were able to work towards achieving the project goals to minimise the risks associated with lack of proper communication channels (Damodaran 2007). The risk communications officer was responsible for communicating different types of risks that arise during the project implementation lifecycle, the type of risks involved, and the risk mitigation strategies with clear, well timed messages, and it allowed for a two way process.
External communication
The project manager experienced a lot of challenges communicating with the outside world especially the public on the type of information to give and the response likely to be received by the public. The communication plan consisted of the following elements (Damodaran 2007).
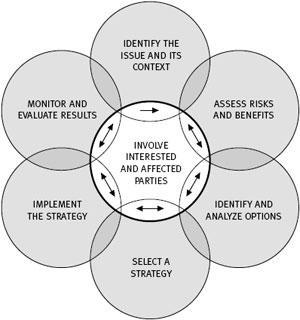
Communciation elements were used to identify the isues realetd to the risks and the impact the issues could casue and to assess the risks and benefits that could result by mitigaitng the external risks, and by identifying and anaysing the options used mitigate, management, and select the most appropriate risk management strategy. That was followed by monitoring and evalaution of the risks, and the entire proecess inloved both stakeholders.
Risk Criteria
The risk management criterion includes the following steps.
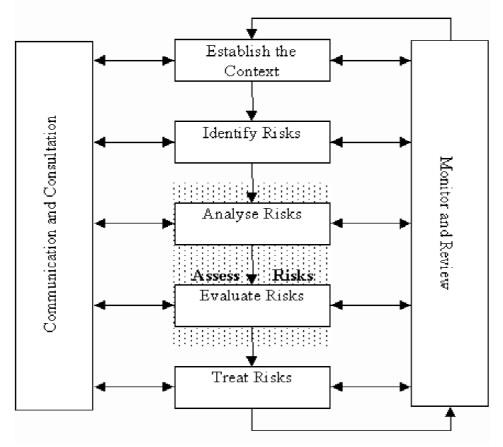
The above framework was used for risk evaluation, review and commucation to the interested parties (Damodaran 2007). In this case the risk management context incldues an external and internal risk management process. In this case, the risk framework shown above consists of the framewok used to in which the risks were evaluated, the risk identification done to ensure that the risks were identified as required in the framework, and an analysis of the risks to ensure that the correct type of risks were identified to ensure that the risk mitigation and management strategies were in place. In the above case, the risk identification was done based on a risk identification method as discussed below.
Risk Identification
Typically, risk identification is the process that was used to identify the type of risks the project could be vulnerable to and the type of strategies to manage the risks (Hillson 2009). The risk identification process in this case covered the major elements associated with the project implementation and includes technical risks, cost associated risks, risks associated with project schedule, and stakeholder associated risks, people, and environmental associated risks as discussed below.
Risk analysis and Evaluation
In principle, there are three risk analysis and evaluation methods used in the project. The methods includes identifying the assumptions and constraints, assessing the constraints and assumptions, and ensuring that the risks were allocated to the risk owners, which lead to formal risk assessment strategy. Typically, this phase involves identifying the structure and ownership of the project risks, estimating the risks, and evaluating the impact of the risks (Raftery 2003).
Project structure answered the questions related to the type of data inputs, outputs and data capture capabilities if they were appropriate to the environment. In this case, the systems are designed to enable the doctors and other authorised users to interact with the system freely in entering and retrieving data (Raftery 2003). The user interface features were designed to be user friendly to allow the users to capture patient data and interact with the system freely and effectively.
A wide range of issues related to project implementation were assessed in this case and included the main objectives of collecting patient data for the medical personnel to enable the doctors, nurses, and other authorised personnel to use the data for effective and reliable service delivery (Vose 2000). The main objective was to allow the medical personnel to be able to capture patient data and store it in a format that can allow the authorised personnel to retrieve and use the data as required. Th other objective was to ensure that the financial status of the stakeholders was sound enough to address the risk of financial problems hindering the implementation progress of the project (Vose 2000).
In this case certain assumptions such as inflation, borrowing costs, and exchange rates in case of importation of some elements of the system were assumed to cause insignificant effects on the project implementation cycle. Additional assumptions included making an evaluation of the assessment constraints which included ensuring that the project stakeholders agreed to the terms and conditions of the contract in case of any risks were encountered (Raftery 2003).
Risk process manager
The risk process manager was assigned the responsibility to routinely assess the project risks and report to the management on risks. When implementing the new project, the risk process manager was assigned the role of facilitating the risk management process by developing the risk management plan, identifying risks and establishing risk control measures, collecting risk information from the project staff, mentoring staff on the risk management processes, facilitating risk reporting , and conducting risk review forums (Vose 2000).
Risk Owner
The risk owner was assigned the responsibility of accounting for the risks that have been identified in the process identification process (Vose 2000). Typically, the risk owners will come from the inside of the organisation and the project implementation team based on their specialised skills and the areas of specialisation and expertise (Raftery 2003). The risk owner takes the responsibility of ensuring that countermeasures are put in place to control the risks involved in the risk management process.
Technical specialist
The technical specialist was identified to be a critical person in the project risk management lifecycle. The technical specialist was assigned the role of identifying risks within each specialised project domain, providing expert opinion for the identification of risks, evaluation of different types of risks, and making recommendations about the type of risk treatment strategies (Raftery 2003).
The executive sponsor’s role
The project sponsor was identified to play a critical role in the project implementation lifecycle. The roles included assessing the risk thresholds and ensuring a monitoring and evaluation program is in place, approving the risk response and control strategies, which may include changing the project scope or cancelling the project as a whole. Approving new risk response strategies, assessing risks to determine the status of the project risks, and reviewing the effectiveness of risk management and response criteria.
Example of risk analysis and evaluation
In this case risk analysis and evaluation process for the implementation of the new IT program to store patient data includes identifying first the risks involved when implementing the project followed by and evaluation of the likely impact of the risks on the project. Different examples that are relevant to this case exist and one of examples is discussed below.
Risk treatment
The risk treatment strategy was put in place as part of the risk management process to ensure that risks were controlled to a level that could not adversely impact on the business and the strategy elements as tabulated below.
Risk monitoring and Review
The risk monitoring and review team was afforded the opportunity to discuss, examine, and establish the status of the risks and to develop a common consensus on the actions to move the project forward. The team ensured that the project risks were identified and controlled without deviating from the project objectives and goals. The agenda for the risk monitoring and reviews included:
- Establishing an overview of risks and any issues arising thereof.
- Establishing the status of existing risks and the control measures that were put in place and how effective they have been.
- Establishing past milestones and predicting future strategic actions.
Risk management team
The most important people in the risk management team have been mentioned above and a summary of them includes:
- Project manager;
- Risk manager;
- Stakeholder;
- Risk owner;
- Executive sponsor;
- Technical specialist;
- Risk process manager;
- Government’;
- Medical personnel;
- System administrator;
- Project team.
Conclusion
In conclusion, the risk management process both at project and at application and resources levels were critical in ensuring the project was successfully implemented. It has been established that different types of risks, such as change risks, which include hardware and software, and stakeholder risks were some of the high level risks which were critical to define in the project scope document, and risk owners were assigned risks according to their specialised skills and the risk appetite of the project manager. A successful completion of the risk management process was based on a comprehensive risk management plan, which included elements such as risk reviews and reporting, and a monitoring and reporting strategy for the successful implementation of the project.
References
Andersen, TJ 2006, Perspectives on Strategic Risk Management, Narayan Press, Koge. Web.
Culp, CL 2002, The Risk Management Process: Business Strategy and Tactics, John Wiley & Sons, New York. Web.
Damodaran, A 2007, Strategic Risk Taking: A Framework for Risk Management, Pearson Education, New Jersey. Web.
Hillson, D 2009, Managing Risk in Projects, Gower Publishing, New York. Web.
Kaplan, RS 2009, Risk Management and the Strategy Execution System. Web.
Lupton, D 1999, Risk, Psychology Routledge, London. Web.
Frenkel, M, Dufey, G, Hommel, U, Rudolf, M 2005, Risk Management: Challenge and Opportunity, Springer Berlin, Heidelberg. Web.
Raftery, J 2003, Risk Analysis in Project Management, Taylor & Francis, New York. Web.
Six, K & Kowalski, E 2005. Developing a Risk Management Strategy. Web.
Vose, D 2000, Risk Analysis: A Quantitative Guide, John Wiley & Sons, New York. Web.