Introduction
Network scanning and vulnerability assessment tasks are critical to ensure protection for network resources from hostile attackers to maintain the integrity, availability, and confidentiality of information in cyberspace (Skoudis 1). Attacks from the internet aim to exploit the vulnerabilities discovered in applications, which occur because of weaknesses in system configurations, use of default passwords, and poor software design and implementation (Skoudis 1). GFI Languard Security vulnerability assessment, Tenable Nessus Network Vulnerability assessment, and Saint Vulnerability assessment tools have a suite of tools for vulnerability assessment, which when run on the network generate reports about the status of the security of the network and suggest appropriate countermeasures (“Nessus Vulnerability Scanner” par. 1).
GFI’s Vanguard Security Management Tool
GFI LANguard is one of the best commercially available tools for conducting network vulnerability assessment and scanning to detect and correct application weaknesses based on multiplatform functionalities in one security solution (Comprehensive Network Security for Businesses 1). The term multiplatform implies that GFI LANguard can run vulnerability assessments and port scanning on Mac OS, Windows, and Linux operating systems, which enables IT security professionals, to remediate security threats and identify the resources vulnerable to attacks. In addition, the tool is able to generate information or reports on network vulnerabilities when port scanning is complete to create countermeasures against attacks by providing the functionalities to enable full patch management. Patch management hardens the system against attacks across different operating system platforms in 38 languages. According to Comprehensive Network Security for Businesses (1), GFI LANguard provides a complete security solution to perform hardware, software, and network auditing to create a complete inventory of network assets, applications, and devices. GFI LANguard provides capabilities to enable automatic remote downloads of patches and uninstall applications that have been installed illegally.
Vulnerabilities GFI LANguard Protects Against
GFI LANguard protects against viruses based on an analysis of network scanning, event logs of security holes in the network, missing patches, open ports, missing security patches, and open shares. GFI LANguard protects against email threats, HTML mail with embedded scripts, malware, and email phishing (“Comprehensive network security for businesses” 1).
Features
To effectively provide the required security solutions, GFI LANguard has integrated various components into a single security solution in an architecture that allows for scalability and reliability. Among the features integrated into the GFI LANguard architecture includes a GUI management console to enable one to access administration and functionality tool to initiate network security scanning, vulnerability sessions for remediation, and patch deployment. Using the GFI LANguard GUI, one is able to configure scanning options, view scans in real-time, report filters, and save scan profiles, and run background operations using GFI LANguard attendant (“Comprehensive network security for businesses” 1).
How to Analyze the Threats
Vulnerability Scanning
GFI LANguard enables one to scan the network on different operating system platforms, including Windows, Mac, and Linux, to identify threats and vulnerabilities and generate reports about the security of the network, and take corrective actions. The strategy used to identify the vulnerabilities and threats in the network includes categorizing the information obtained by scanning computers from a single source of data (“Comprehensive network security for businesses” 1).
Patch Management
Patch management is done using GFI LANguard tools, which have the functionality of the tools mentioned above to install required patches in any machine that has been scanned remotely in the network (“Comprehensive network security for businesses” 1). If a patch is discovered to have a problem, it is recalled through patch rollback options and deployment options. It is important to note that GFI LANguard can be configured to provide automatic patch downloads to provide security against vulnerabilities discovered in the network.
The Most Important Features and Why
The most important feature are the graphical user interface because it provides the user without any programming or detailed IT security knowledge to audit the system on their own.
Tenable’s Nessus Network Vulnerability Tool
The Tenable Nessus network vulnerability tool is used for deep vulnerability analysis. The product provides security services in configuration and vulnerability assessment based on industry-standard reports (“Nessus Vulnerability Scanner” par. 2). Tenable Nessus provides services for network IT professional penetration testers and network security auditing. Tenable Nessus can be distributed throughout an enterprise as a tool to test a range of IP addresses and determine whether the IP addresses are static or dynamic. According to the Nessus Vulnerability Scanner (par. 1), Tenable Nessus has an inbuilt capability that allows one to use it to test IPv6 on any operating system. Tenable Nessus operates at speeds that enable one to scan and audit more than 100 hosts in a few minutes using a medium-powered server.
Types of Vulnerabilities
Tenable Nessus is a freely available network scanner updated daily for home use and other non-enterprise uses but is proprietary software for enterprise use with an extensive plugin database. Tenable Nessus can be used to identify various vulnerabilities in a local computer or in computers in a network that allow a hacker to remotely access sensitive data on a computer and control data or information on that computer (“Nessus Vulnerability Scanner” par. 1). Tenable Nessus scans computers for compliance specifications, content policy violations, and vulnerabilities. The program allows for one to assess any misconfiguration done on an application and identify missing patches, can be used to detect denial of service (DOS) attacks, and can be used to conduct an audit of the payment card industry data security standard (Nessus Vulnerability Scanner par. 1). Tenable Nessus has inbuilt capabilities to detect any resource in a network and test the security of that resource appropriately. In addition, Tenable Nessus uses any tool available such as a server banner to test the presence of any vulnerability in a resource and reports the method used to access and test the resource (“Nessus Vulnerability Scanner” par. 2).
Tools/Features
Tenable Nessus has a number of security tools integrated into a single security solution. The tools integrated into the single security solution include intrusion detection, network monitors, malware detection, patch management, web servers, and network devices summed into log correlation engine features. Tenable Nessus is designed with a modular architecture enabling the client to be deployed at a low cost to ensure reduced management costs and enable a single server that can be accessed from multiple numbers of clients. Tenable Nessus scanner includes tools such as Nessus Attack Scripting Language (NASL), which makes the process of writing security tests easy and quick.
How to Analyze the Threats
Tenable Nessus starts to work by doing a port scan using any of the four-port scanner tools integrated into the product. Once the information about the scan is available, it is classified according to the severity levels, which include critical, high, medium, and low (”Nessus 5.0 Installation and Configuration Guide”1). The purpose of the port scan is to identify open ports that can be exploited. In addition, Tenable Nessus analyses network vulnerabilities using the powerful analytics and reporting tool by doing statistical profiling of all devices in the network to identify any anomalous behavior, which then sends an alter about any changes in server behavior (”Nessus 5.0 Installation and Configuration Guide” 2). In addition, how Tenable Nessus uses IDS (intrusion detection) system to alert one on the system vulnerabilities under attack or that has been compromised to create situational awareness. The program provides the features that enable user to customer the application to enable the user to write personal parsers of events.
One of the most important features is that Tenable Nessus provides centralized management capabilities (”Nessus 5.0 Installation and Configuration Guide”2). That allows for easy deployment and configuration. In addition, the application provides abilities to store, compress, and search all the logs for each device that has been scanned in the network, and provide tamper-proof forensic evidence that is admissible in the court of law (”Nessus 5.0 Installation and Configuration Guide”3).
The Most Important Features and Why
The most important feature here is the analysis tool to perform vulnerability assessment, the reporting feature for viewing the reports, and the graphical user interface for configuration management and interactivity.
Saint Vulnerability Assessment Tool
Saint is a pre-configured easy-to-install security assessment tool and has the capability to scan every live port on UDP and TCP service levels (“SAINTscanner® Vulnerability Assessment” 1). The application provides an accurate assessment of the security compliance of the network infrastructure in an enterprise. Saint provides unique services by exploiting the use of two tools, which include Saint Exploit and Saint Scanner to find and exploit vulnerabilities in a computer system. Saint vulnerability assessment tool works based on a wide range of standard references to report any problem identified in a computer system. In addition, Saint is a Linux-based on the installation process based on Linux commands that are available on the product’s documentation (“SAINTscanner® Vulnerability Assessment” 1).
Saint provides real-time progress reports on vulnerability assessment on weaknesses discovered in the system and the resources being scanned. Compared with the other vulnerability assessment tools which provide users with a graphical user interface to interact with the system, Saint is run on Linux commands. The core areas of security solutions provided using Saint include vulnerability assessment, exploits, and zero-day knowledge provision (“SAINTscanner® Vulnerability Assessment” 1). In context, identify the vulnerabilities in a network, web applications, operating systems, and desktop applications. Saint provides tools which can be used to detect and fix any vulnerability in the network to provide security against any hostile intrusions from the internet. Saint has an inbuilt capability to proactively prevent any vulnerability in any application and assess the compliance level of the network devices with government and industry regulations which include HIPAA, SOX, and many other standards and assess the level of compliance of network devices to industry-standard policies ((“SAINTscanner® Vulnerability Assessment” 1).
Saint provides IT security professionals with four main categories of data analysis which include vulnerabilities, reports, trust, and host of information. In addition, the application provides an interactive user interface that allows the user to generate the reports provided after a scan (“SAINTscanner® Vulnerability Assessment” 1).
Vulnerabilities
According to Saint: Vulnerability Management, Penetration Testing & Compliance (1), the areas of concern for Saint Vulnerability assessment tool include cross-site scripting, vulnerable browsers, and information access on a host configuration like finger information and FTP bounce, and privilege escalation (Skoudis 2). Saint checks for application weaknesses that can be exploited by hostile attacker, common application configuration errors which, when discovered in a system provides holes for attacks, system vulnerabilities, database vulnerabilities, and default and weak configuration settings (Skoudis 2).
How to Analyze the Vulnerabilities
Vulnerability assessment is done by setting up the scan, adding the target IP address, and running the scan (Skoudis 2). The tool is configured using the interface provided based on the scan policy shown below.
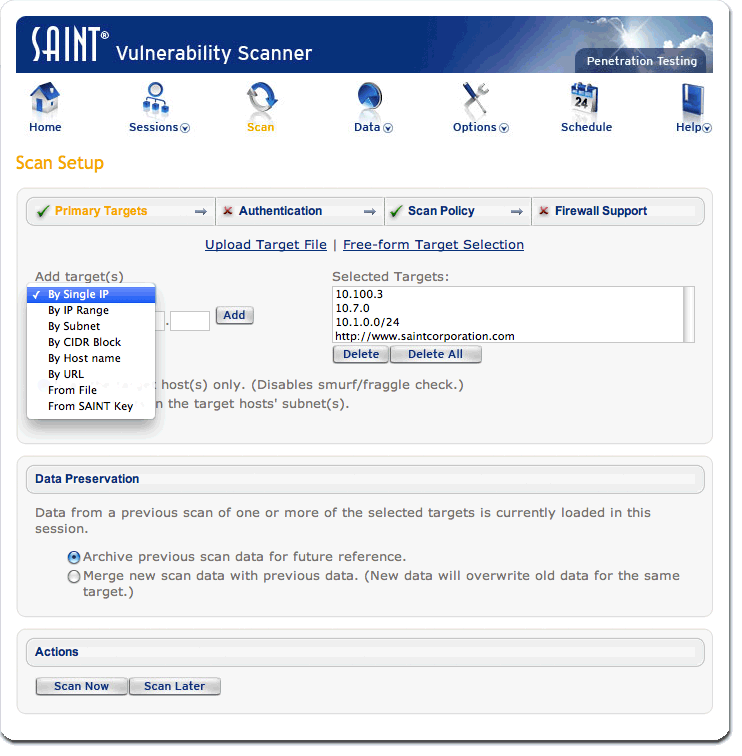
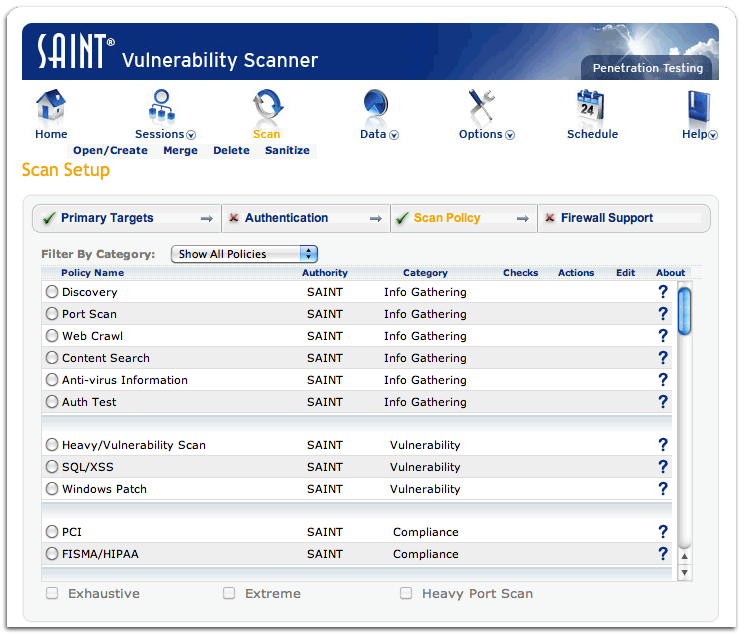
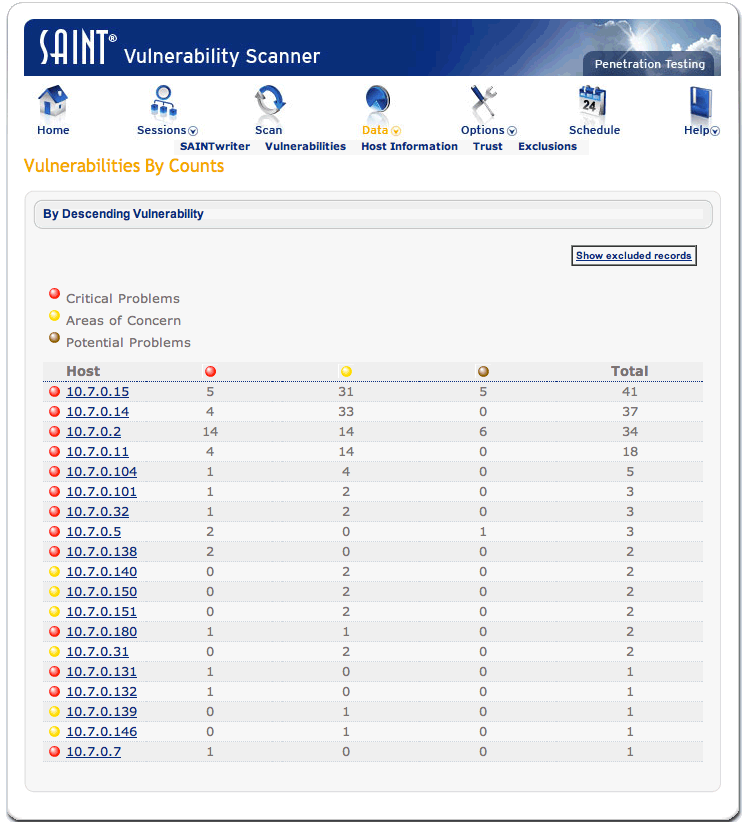
Important Features and Why
The most important feature are the one that allows the user to enter commands and generate reports from the system.
Comparison
Tenable Nessus, GFI LANguard, and Saint provide similar network vulnerability assessment services using a suite of different tools with different graphical user interfaces which run on different operating system platforms. Tenable Nessus and Saint Vulnerability assessment tools generate reports based on industry standard requirements which include SOX and others. Each of the three tools is able to detect and generate reports on anomalies in any network device and allow for remediation. The similarities of the tools is that they come with a suite of tools which can assess and analyze the vulnerability of a network or standalone device, generate reports about the vulnerabilities and threats the network device is exposed to, and suggest solutions to correct any detected anomaly. Each of the vulnerability assessment tools comprises of wide range of tools that serve different purposes.
The tools have significant differences. GFI LANguard patch management capabilities are based on automatic downloads software audit capabilities and vulnerability assessment. GFI LANguard provides an interactive graphical user interface that allows users to easily interact with the software and perform various tasks using the application that is compatible on different operating systems. On the other hand, Tenable Nessus provides vulnerability assessment by scanning computers for compliance to standards. Saint is different from the other vulnerability assessment tools because it runs on Linux servers and can only be installed using Linux commands.
Conclusion
The three vulnerability assessment tools come with a suite of tools that enables one to scan the network for threats and identify the vulnerable points that can be exploited by hostile attackers to compromise the system. The tools are commercially available and have different graphical user interfaces to enable the user run the tool on the appropriate platform. Tenable Nessus and FI’s Vanguard Security Management tools run on different operating system platforms while Saint can only be installed and used on a Linux platform. Tenable Nessus and FILanguard Security Management tools are the best options for network security scanning compared with Saint because of the speed Tenable Nessus and FILanguard Security Management tools run scans and vulnerability assessments on the network and the wider range of tools available on the platforms for use.
Works Cited
Comprehensive network security for businesses, GFI LanGuard, 2013.Web.
Nessus 5.0 Installation and Configuration Guide, Tenable Network Security, 2013. Web.
Nessus Vulnerability Scanner 2013. Web.
SAINTscanner® Vulnerability Assessment, Saint, Vulnerability Management, Penetration Testing & Compliance 2013. Web.
Skoudis, Ed, Vulnerability-Scanning Tools, 2001. Web.