Abstract
The proposed project is devoted to the comprehensive analysis of threats that affect the work of the aviation industry. The relevance and topicality of the selected issue come from the strategically important role of civil aviation in modern society and the critical need to create the safe framework by evaluating and assessing all risks that might precondition undesired outcomes. The paper discusses the nature of existing threats, their roots, and the possible solutions that can be used to identify, detect, and manage them. Qualitative research methods and inductive approach are employed as the tool to ensure appropriate data collection and conduct the research of the selected question. The findings prove that the aviation industry faces multiple threats that emerge every day and become more complex, which means that there is a need for an appropriate change in organisation and employment of innovative methods of risk management to protect passengers.
Introduction
The pivotal aim of the presented study is the in-depth analysis of threats the modern aviation industry faces today, their impact on its functioning, and solutions that can be integrated to ensure practical risk management. The topicality of the problem is linked to the fact that today, aviation is a strategically important mean of transport that supports the functioning of the contemporary highly-globalised world and offers multiple opportunities for the further development of the international discourse. Due to its fundamental role, aviation attracts the attention of malefactors aiming at the destabilisation of the situation and damaging people. That is why international agencies emphasise the fact that there is a need for the improved management of all emerging threats that can be achieved by their evaluation and analysis (U.S. Government Accountability Office, 2017). The paper offers information related to the topic acquired by analysing the relevant literature and reports of international agencies responsible for the effective and safe functioning of the civil aviation sphere. The given section suggests that background knowledge is required to understand the nature of the research, and the scope of problems touched upon in the study. The research questions, justification, and rationale for conducting the study are also offered within this part.
Background of the Research
Contemporary society critically depends on the effective functioning of the aviation sphere. The increased speed of life, availability of information, and the need for fast travelling create the environment beneficial for the further development of air transport. For this reason, the number of passengers using airlines’ services increases every year. According to the statistics provided by the International Civil Aviation Association (ICAO) (2019a), the total number of passengers carried on scheduled services constituted about 4.3 billion individuals. The number evidences the significance of aviation for the modern sphere, and all domains of human activity, including business, tourism, politics, and military ones. Moreover, there are forecasts that the industry will continue to evolve, which means that it will become even more critical and attract additional attention to different actors.
At the same time, the fast growth of civil aviation means the sophistication of the sphere and multiple processes peculiar to it. To meet all demands of passengers, airlines have to introduce many services and opportunities that can satisfy clients with various requests. For this reason, the existing airports can be viewed as complex units with developed infrastructure and numerous departments responsible for the accomplishment of different tasks. This fact explains the need for practical management tools that provide an opportunity to avoid undesired outcomes or mistakes that can precondition accidents. However, regardless of multiple attempts to establish the environment characterised by the absence of risks, there are still factors that can worsen outcomes and deteriorate the functioning of airport and companies. These aspects introduce the primary concerns for both regulatory agencies and airlines as they remain responsible for protecting passengers and guaranteeing that they will be able to reach various areas without any accidents. In such a way, the modern aviation sphere faces the need for the continuous collection of information about the new ways to cause damage to be ready to resist them and introduce new measures.
Another tendency peculiar to aviation today is its becoming an essential tool of international relations, which also means that it attracts the attention of multiple organisations interested in destabilising the situation, showing their activity, and spreading chaos. In numerous cases, these terrorist groups have substantial financing and resources sufficient for using the most innovative tools to destroy existing security systems and damage aircraft or passengers (ICAO, 2019b). For this reason, specialists are sure that having entered one of its significant evolution stages characterised by the rise and multiple opportunities, civil aviation has also made itself extremely vulnerable because of these very features (Stewart and Mueller, 2017). In other words, the fast rise is followed by a high level of interest and the emergence of loopholes that can be used by malefactors. For this reason, ICAO, IATA, and other regulatory agencies are interested in initiating the dialogue about the future of aviation and improved management of new threats that emerge every day and might precondition damage.
Finally, the coherent society can be characterised by the increased attention to human lives and the recognition of its unique value. It means that the demands to security become stricter every year with the primary goal to create an extremely safe environment with the absence of risks (Benny, 2016). For this reason, the task to remain informed about new threats acquires the top priority as the only way to be ready to respond effectively and avoid serious accidents.
Altogether, the situation in the civil aviation sphere remains complex today. There are multiple options for its further development and evolution, which means that it can benefit from a substantial rise and becoming even more meaningful aspect in the life of people, communities, and countries. From another side, the unique strategic importance means that aviation becomes one of the main aims of malefactors and terrorist groups trying to invent new ways to damage aircraft and passengers. For this reason, a better understanding of emerging threats and ways to cope with them is vital at the moment.
Justification of the Research
The choice of the theme of the project comes from several factors. First of all, as it has already been stated, the aviation industry plays a fundamental role in the modern globalised world as it serves as the facilitator of international relations and potent political tool. For this reason, the stable work of the sphere is a guarantee of the future evolution of the global society and states’ ability to cooperate. Correctly realising the importance of the given field, multiple agencies try to establish a working environment characterised by the absence of threats and effective functioning of security systems that will guarantee safety to all actors involved in it. However, it is impossible without the constant monitoring of the current situation and the continuous collection of data needed to be informed and respond to new changes. Under these conditions, the project acquires specific importance as it is an attempt to create a list of threats topical at the moment and the ways to solve them.
Furthermore, the choice of the topic can be justified by the fact that the current stage of technologies development can be called a revolution. The sophistication of technologies and new devices mean the radical changes in the way aviation functions and how the most significant processes are organised. It helps airlines to function more effectively and provide its services to the increased number of passengers every year. Moreover, the extensive implementation of innovative technologies, applications, and systems create the basis for new improvements and empowerment of civil aviation. The scope of changes is substantial, and it is expected that the speed of alterations will increase in the next decade because of the digitalisation of society (Arcurio, Nakamura and Armborst, 2018). This tendency is critical, and it is vital to realise how aviation functions today, which is one of the pivotal purposes of the whole project.
Unfortunately, the emergence of new ways to perform tasks also means that there are new ways to damage civil aviation and spread havoc, damage aircraft, and hurt passengers. In the recent decade, the number of threats duplicated and continues to grow as such a phenomenon as cybercrime and terrorism become more topical for the modern world (Price, 2018). Malefactors also use innovative devices and applications to create loopholes in security systems and organise accidents. For this reason, the industry faces multiple challenges presupposing the need to introduce new methods of managing emerging threats and minimising risks associated with them. For this reason, the importance of the given research project becomes evident as it focuses on new hazards, their impact on civil aviation, and methods to resist them.
Finally, existing ICAO and IATA’s reports also emphasise the need for the investigation, data collection and research, as the only effective ways to be prepared to face new problems and solve them effectively. For this reason, the enhanced information related to emerging threats is fundamental for civil aviation sphere as it creates the framework for building new security systems and selecting tools to resist attacks, various types of risks, and avoid accidents. From this perspective, the choice of the topic is justified by the fact that it can help to enhance the existing understanding of the problem and initiate its discussion. Altogether, the selection of the research topic comes from the factors mentioned above. There is a need for the collection of information related to new threats with the primary goal to process it and discuss the effectiveness of existing methods to resist them.
Research Questions
The scope of the project and its importance for the improved understanding of the current state of civil aviation, threats, and ways to solve it impact the formulation of several research questions that will guarantee the credibility and relevance of findings, their practical utility, and the ability to facilitate the following research of the topic.
- What are the state and central concerns of civil aviation today?
- What are the most important threats that should be given specific attention because of their complexity and substantial harm associated with them?
- What is the current approach to managing threats and minimising risks associated with them?
- What are the new methods of managing threats that appear as a response to new hazards and risks associated with the following evolution of technologies and aviation sphere?
- Can the new approaches to organising security cope with emerging threats and be effective enough to guarantee safety to individuals?
- What are the possible future challenges and changes to the process of organisation and managing of threats that should be considered?
The presented research questions are supported by objectives that drive the course of the research and should be accomplished to ensure that the topic is analysed and the major issues are discussed. These are:
- to analyse existing threats that affect the work of the aviation industry
- to create the theoretical framework for the project by reviewing the relevant and credible literature and collecting data
- to research methods, tools, and approaches that can be used to detect, identify, and manage existing threats
- to evaluate the possible use of drones, improved security systems, and innovative software as measures to attain better outcomes
- to discuss the nature of these measures and opportunities for their integration in the work of airlines
- to conclude about the current state of the problem and create the basis for new projects related to the same question
The given research questions and objectives form the framework of the whole project. They ensure that the most relevant themes and ideas will be included in the discussion and analysed with the primary goal to improve the knowledge of the problem and provide new details that are vital for the enhanced understanding.
Literature Review
Introduction
The first section of the presented report is devoted to the analysis of the current literature that is related to the selected issue. The review creates a theoretical basis for the discussion as it outlines the existing threats and challenges the modern aviation faces, the current approaches to managing these hazards, and other problems that might be associated with the topic under discussion. With the primary goal to establish the framework, there is an in-depth analysis of academic and scholarly sources touching upon the similar issues, ICAO and IATA reports, and other secondary sources that contain the needed knowledge and can be used to enhance the existing vision of the theme. The literature review also helps acquire a better image of how current security systems function and the most relevant threats managed. For this reason, the following section offers information collected from relevant sources.
Another important aspect about literature review is its ability to shed light on options and newest ideas related to organising the work of airlines and minimising the level of risk in the sphere. In such a way, the selected sources outline how innovative technologies, such as drones, new applications and devices can be employed with the pivotal aim to create a perfect security system with the absence of loopholes or the ability to respond to new threats effectively. All sources selected for the review should be considered credible, relevant, and scholarly as they come from research databases. Moreover, the section contains information from international organisations’ reports and their findings. For this reason, it is an essential part of the project offering the knowledge needed for the further discussion and analysis of the problems mentioned in the previous paragraphs.
The Major Themes Related to Civil Aviation and Emerging Threats
The modern globalised world critically depends on the stable functioning of the aviation industry. It is the only mode of transport that offers passengers an opportunity to achieve distant locations in short terms and with a high level of comfort. Additionally, it is considered the safest mode of transport with the lowest rate of deaths or accidents (Price and Forrest, 2016). These advantages attract travellers, and millions of people use airlines’ services every year, which contributes to the fast evolution of the sector. However, this tendency introduces additional complexity of basic operations and attracts the attention of malefactors who might use violent acts to spread panic. It means that today, aviation faces diverse threats, and there is a need for their effective determination and management.
The modern attitude to the organisation of security in the aviation sphere is mainly preconditioned by the rise of terrorism and the appearance of a significant threat to passengers’ safety. The 9/11 attacks triggered a vigorous discussion between various agencies regarding the methods to check passengers, monitor vulnerabilities, and minimise risks (Price & Forrest 2013). The given terrorist attack showed the existence of many gaps in security systems and evidenced the need for the reconsideration of the majority of approaches to make them more useful. The tendency towards the further rise of terrorist threat and emergence of new radical organisations along with the growing number of maleficent actions and cybercrime contributed to the shift of priorities towards a full risk-based paradigm that can consider all possible factors and create a safe environment (A risk-based approach to aviation safety regulation, no date). Today, there are still many debates around the ways to make security systems more reliable and the main elements of the discussed approach that can be improved.
From another perspective, the methods that emerged after the 9/11 attacks and systems that appeared as a response to the high level of risk gradually become outdated today because of the massive digitalisation of society and the complexity of tools that can be used to harm airlines or passengers. Under these conditions, ICAO and IATA insist on the establishment and introduction of an innovative, flexible, and updating approach that would be able to ensure the protection and consider all hazards topical today. That is why the constant improvement of systems is one of the major themes related to civil aviation today. Specialists working in the field and researchers emphasise the critical importance of this aspect for the successful evolution of the sphere. At the same time, this process is followed by the classification of threats and hazards that play a vital role in the aviation industry and should be addressed first of all.
The need for the correct understanding of relevant threats and their nature is linked to the necessity to develop effective protective measures and avoid deterioration of the sphere’s functioning. For this reason, the existing ICAO’s reports are updated and outline new hazards that should be taken into account along with the traditional ones (ICAO, 2011). For instance, the terrorist threat, which has always been viewed as the main concern, preserves its critical importance; however, the number of issues related to this term is diversified. Today, the cyber threat is one of the vital emerging risks that can be both linked to terrorism and other malefactors acting separately. The complexity and importance of this phenomenon are evidenced by the fact that the modern security systems are designed with the primary goal to resist attacks from other servers via the Internet or other networks (Price, 2018). Moreover, there is also an insider threat that becomes more topical today as attackers look for an opportunity to create loopholes by using employees and their knowledge. In different cases, insider threat can be associated with the activity of single specialists trying to achieve their own goals.
The list of emerging threats can also be extended because of the growing availability and affordability of drones which can be used for different purposes. These unmanned aircraft possess an opportunity to reach various areas and remain unnoticed, which is critically important both for security specialists and attackers (Hall, 2015). Under these conditions, it is necessary to organise protective measures considering the high risk of being attacked by drones, which introduces additional complexity for specialists and airlines. The first rise of the given technology demonstrates the scope of the problem as the digital era establishes multiple challenges to airlines.
The modern civil aviation sphere has several concerns that should be addressed. These include the increased importance of a safe environment and the need to organise and manage new threats that appear every day. The list of threats is updated and remains diverse, however, in terms of the given project it is vital to consider a terrorist threat, cyber threat, human factors including insider threat, technologies and drones as the central problems that should be solved to avoid issues in the future.
Current Approach
Due to the complexity of challenges that emerge every day and the need to consider multiple aspects, the modern aviation sphere adheres to the risk-based approach that is taken as one of the most potent frameworks among the existing ones. International Civil Aviation Organisation (ICAO) encourages the adoption of a Risk-Based Surveillance (RBS) to aviation regulation as the method that can help to minimise potential threats and find appropriate measures to work with them (ICAO, 2017).
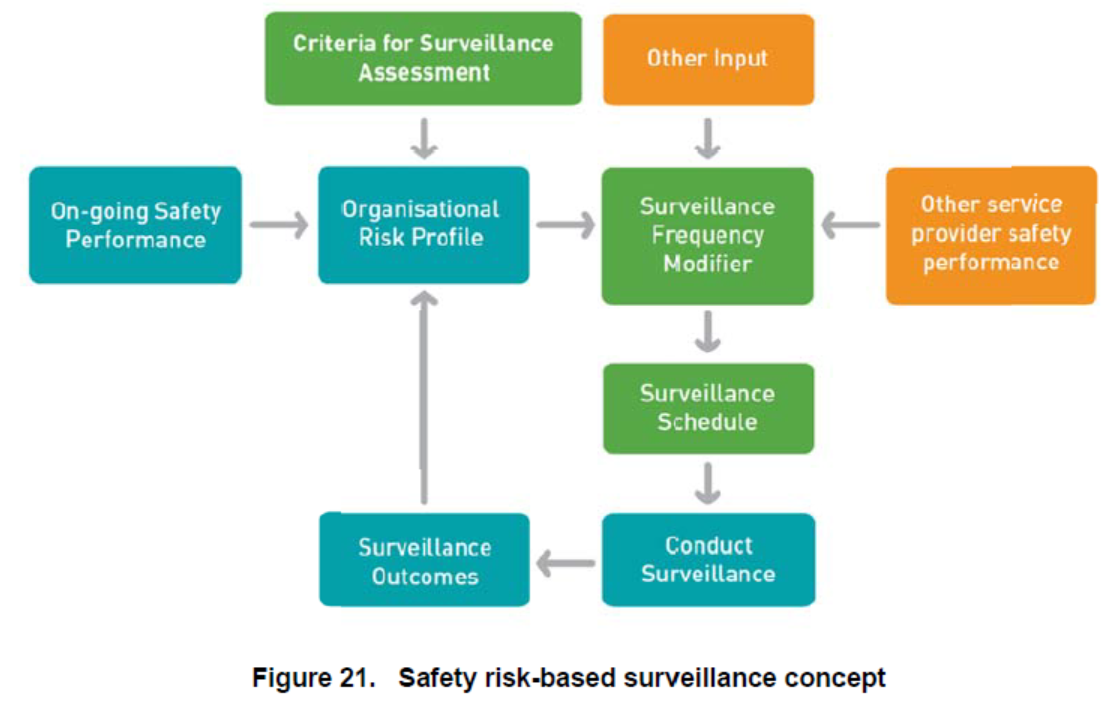
In accordance with this paradigm (see Figure 1), the on-going safety performance can be achieved by combining specific criteria for assessment, effective surveillance schedule, analysis of outcomes, and creation of organisational risk profile vital for the consideration of new threats (A risk-based approach to aviation safety regulation, no date). Decision-making related to the assessment of new hazards and introduction of appropriate measures should rest on data acquired to create the framework for the discussion and investigation (see Figure 2).
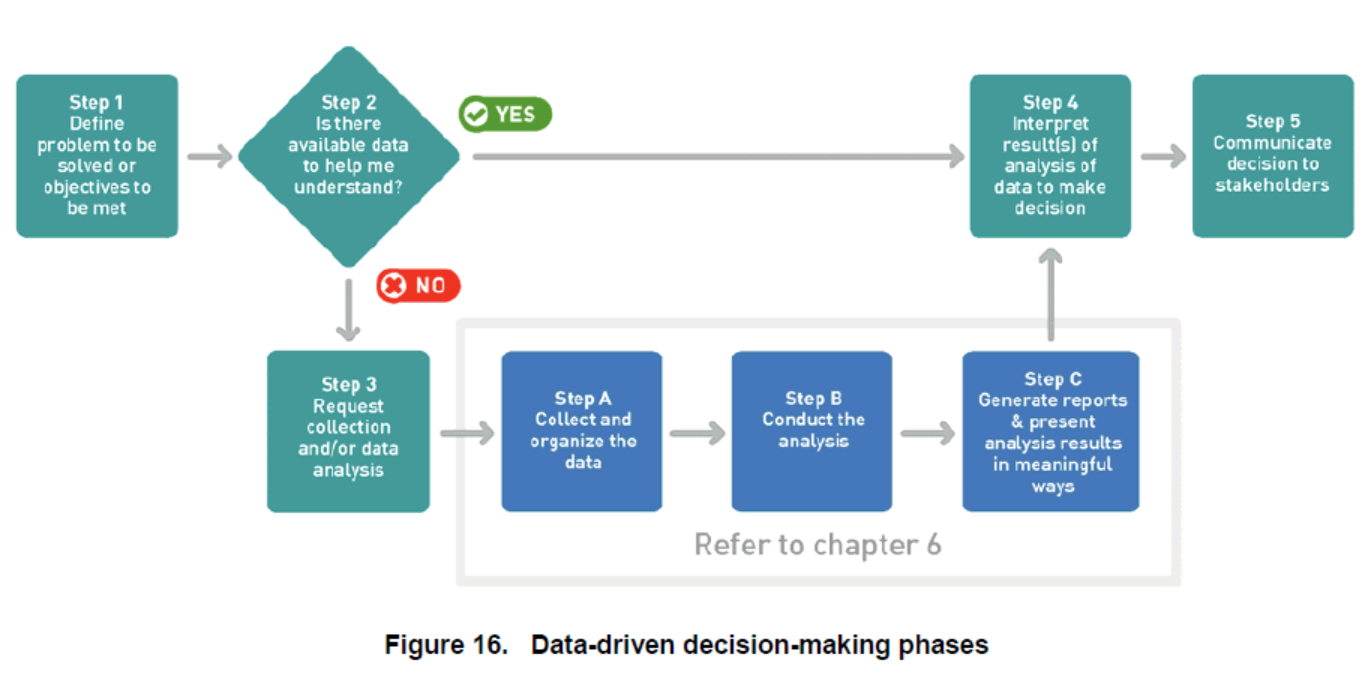
In accordance with these recommendations, the modern civil aviation sector is expected to become more effective in resisting already known and new threats. Moreover, the International Air Transportation Association (IATA) (no date) accepts the importance of the outlined paradigm and promotes the implementation of continuously improving security management systems. In this regard, one of the fundamental elements in the functioning of any airline is the fostering and establishment of a dynamic and risk-based approach to security to guarantee the absence of serious vulnerabilities and creation of the safe environment needed to protect passengers (ICAO, 2017a). It means that the potent character of the discussed strategy is accepted at the international level with no alternatives that can replace it at the moment.
To resist existing threats effectively and create a system that will be able to cope with all problematic issues that emerge today due to the rise of technologies, it is critical to acquire an improved understanding of the concept of risk and its basic components. The dominant perspective focuses on the probability of incurring some type of loss (Elias, 2014). In other words, it is a chance for the appearance of undesired situations that might deteriorate the work aircraft, personnel, or the whole airport and pose a threat to the health of passengers and their lives. Regarding the context of security and the requirement to minimise all possible complications, the concept of risk is taken as a complex phenomenon consisting of three elements such as threats, vulnerabilities, and consequences (UK CAA, no date). The main advantage of a full risk-based practice is that it offers multiple categorical techniques and approaches that help to reveal, determine, and quantify threats and vulnerabilities and secure individuals. It also becomes a potent measure as regardless of the increased sophistication of the contemporary aviation sphere, a set of dangers and undesired events in the aviation environment remains limited.
Considering the given definition, risk-based aviation security aims at eliminating or mitigating all three elements mentioned above to guarantee the high level of protection to all passengers. The first broad category includes all existing threats that might deteriorate the work of civil aviation and lay the ground for the emergence of critical situations. The current threat framework offered by multiple agencies such as Transportation Security Administration and Office of Intelligence (OI) includes information about main problematic issues that should be taken into account when aligning the work of the security system (Price & Forrest 2013). Being the part of the risk-based approach, it helps to create effective measures in advance and act in appropriate ways when emergencies occur. That is why it has become one of the most popular methods accepted by airlines and agencies such as IATA and ICAO (IATA, 2019). For instance, risk-based screening is offered as a fundamental element of all security systems as it helps to reveal and eliminate dangers.
The in-time detection of existing vulnerabilities and their elimination is another vital element of the modern risk-based paradigm. The fact is that the development of the aviation sphere stipulates its further sophistication and appearance of several complex processes that are required to ensure well-aligned work of the sector. In its turn, this situation gives rise to new opportunities for malefactors to use appearing gaps in security systems and damage aircraft or airports (U.S. Government Accountability Office, 2017). In this regard, the work with vulnerabilities, their classification and suggestion of effective measures to eliminate them is a core component of the risk-based approach, which guarantees its high effectiveness and the ability to meet all requirements to safety that exist today. ICAO and IATA continuously renew the list of all possible loopholes in frameworks and provide measures to mitigate them (ICAO, 2017b). It makes a fully risk-based approach one of the best possible alternatives for the modern aviation sector.
As for the consequences associated with multiple risk factors, they are also taken as a part of a risk-based approach. The main task of any security system is not only to prevent the appearance of critical situations (though it holds the top priority), but also be able to work with negative results, assist passengers or workers who face a threat, and restore the work of airlines (Price & Forrest 2013). For this reason, the discussed approach incorporates the existing methods of working with any outcomes that might appear because of various undesired issues or risk factors. The constant monitoring of information in different countries and cooperation between agencies contribute to the generation of a broad knowledge base that might be used in situations to decrease the negative impact and mitigate consequences. That is why it should also be taken as another critical element of the risk-based approach that contributes to its increased effectiveness in the modern environment.
Risk-based surveillance and security models have proven their effectiveness in multiple cases and are still viewed as the fundamental aspect of civil aviation. However, the literature recognises that need to continue working on their enhancement to remain capable of resisting new challenges and threats (Price & Forrest 2013). For instance, using AI technologies as data collection and processing methods, specialists can boost their effectiveness and attain better risk assessment and identification results (ICAO, 2017b). The current approach is characterised by the gradual shift towards more digitalised and software-dependent solutions that can help to remain flexible and effective in resisting all hazards that arise today. Numerous sources acknowledge that the risk-based framework should be supported by new technologies as the only way to follow the progress, which also provides malefactors with new strategies for damaging airlines and interfering with their functioning.
Terrorism
Speaking about the threats modern civil aviation faces, it is impossible to disregard terrorism as one of the problems of contemporary society. The anti-terrorist war in the Middle Eastern region, and activity and power of ISIS, and the recent violent acts aimed at destructing airlines and causing much harm to civilians show that airlines remain vulnerable to external threats (IATA, no date). Moreover, as stated previously, the technological evolution and creation of new devices can be viewed as a two-edged sword also providing the new opportunities and tools for attackers to look for loopholes and destroy security systems (Price, 2018). Under these conditions, organisation and management of terrorist threat remain one of the major concerns today.
Multiple authors, as well as ICAO and IATA, warn that today, the nature of terrorism alters and the traditional attacks presupposing the use of explosives, weapon, and force become replaced by other, more sophisticated tools (ICAO, 2017b). Accepting the need to remain informed about these risks and create systems capable of resisting theme, specialists also insist on the necessity of collecting information related to new forms of terrorism and its analysis (ICAO, 2017b). Because of the centralised attack planning, today, terrorist groups have the chance to collect resources and skills to introduce new sophisticated tactics against effective systems and hardened targets (ICAO, 2017b). At the same time, the decentralisation also poses a problem as there is diversification of tactics, techniques, and weapons that can be used to damage easier targets including public areas in airports, terminals (such as attacks in Belgium on 22 March 2016, Turkey 28 June 2017) (IATA. 2019). For this reason, the threat coming from terrorist groups remains high and should be taken into account as one of the central issues.
From another perspective, the radicalisation of individuals and groups in different regions of the planet results in the increasing risks for fields that have not had such issues previously (ICAO, 2017b). The terrorist organisations are capable of attacking airlines across a broad geographical area by using their forces, or by hiring foreign fighters or recruiting workers having access to critically important information (ICAO, 2017b). It means that the given threat evolves and becomes more significant today. The use of cyber means to perform acts of violence is a comparatively new form of aggression with the high potential risks to air traffic management, aircraft and airport systems, and management (ICAO, 2017b). In such a way, the development of terrorist threats is a source of significant concern stipulating the emergence of the demand for new transport networks that are safer and can resist a new wave of cyberattacks (ICAO, 2020). Recent actions of this sort precondition multiple delays and confusion in schedules, which should be taken as a reminder of the high level of risk and the chance of causing even more substantial harm to aviation (ICAO, 2017b). Under these conditions, the whole aviation community should be vigilant about the given issue and be ready to secure the most valuable information, communication technology systems and data from interference resulting in the decreased effectiveness of measures used to protect individuals. This task is becoming one of the integral parts of the risk-based approach and demands specific resources and attention of specialists working in the sphere.
The evolution of terrorist threat results in the need to continue upgrading the existing security systems and preparing them for a new wave of attacks. ICAO and IATA (ICAO, 2017b) are united in the opinion that the diversification of the existing means and their innovative character cannot be unnoticed and should result in the change in the approach used to organise and manage existing issues. For this reason, the current recommendations view terrorism not only as acts of violence performed by using rude force but also as any actions that might create the basis for the deteriorating of the existing working environment (Stolzer, 2015). The updating frameworks with the ability to learn and become more effective are given preference as the most relevant ones. They should also be ready to function within the risk-based approach and change if new hazards and loopholes are detected.
Another problem that is usually linked to terrorism is the use of absolutely new strategies and their sophistication. The emergence of developed infrastructure among terrorist groups means that they acquire new funds and means to cause damage to airlines. They can recruit workers of airlines, hackers, and other specialists and plan attacks several years to hide illegal activity and guarantee results (ICAO, 2017b). For this reason, agencies and security managers acquire a new task of constant monitoring the functioning of workers and all elements of systems to check whether there are signs of maleficent actions or attempts to create loopholes in existing frameworks (ICAO, 2017b). The complexity of this challenge is evidenced by the fact that there are still multiple cases of attacks detected and reported every year (Stolzer, 2015). That is why existing approaches should be able to possess information about all potentially dangerous factors and use it to avoid severe damage.
The existing body of evidence demonstrates that in times of fast technological process, the terrorist threat still remains a fundamental concern that also develops and acquires new forms. The radicalisation, globalisation, and diversification of terrorist groups provide them with new strategies and means of attacking airlines and causing harm to them (ICAO, 2017b). The use of technologies changes the existing environment and introduces the need for more effective monitoring of risks and possible damage associated with them. There is a set of innovative solutions that are offered as a response to the problem, and that will be discussed within the paper.
Cyberthreat
As stated previously, technologies can be viewed as a two-edged sword that improves the work of civil aviation and cultivates the growth of the cyber threat. ICAO (2019a) defines the issue as the possibility of causing damage or disrupting a computer network of systems by using specific devices. The scope of the problem is evidenced by the fact that the concept of Aviation Cyber Security acquires the top priority nowadays and is viewed by ICAO as an integral part of the overall security system (Department for Transport, 2018). It is considered a convergence of individuals, processes, and technologies coming together to protect civil aviation organisations, operations, and individuals from digital attacks (SenseCy, 2016). ICAO, IATA, Airports Council International (ACI), and the Civil Ari Navigation Services Organisation (CANSO) are united with the attempt to collaborate and facilitate the creation of a unified approach related to cyberthreat (CANSO, 2014). The need for the given strategy is justified by the fact that for over decades an effective process of regulation has been created to protect civil aviation from mechanical risks, collision, human error, and terrorist attack (CANSO, 2014). However, today, the industry heavily depends on complex and networked electronic communication systems that remain vulnerable to hacker attacks and cybercrime (CANSO, 2014). Under these conditions, these frameworks should be protected against different breaches, maleficent actions, and intrusions as they might cause substantial harm to airlines and passengers. That is why ICAO (2019a) introduces specific goals for the strategy that should be achieved by 2021/22, such as the creation of the secure environment resilient against malicious and unintended interference with information systems. Achievement of success in this field is vital for the demonstration of the transformation of the whole approach to cybersecurity that should acquire the ability to deter and protect against all types of already known threats and against the new hazards that will emerge in the future (ICAO, 2019a). Moreover, speaking about this issue as about one of the fundamental emerging risks, ICAO (2019a) admits that effective protective systems should possess the ability to contain, mitigate the effects, and recover from any attack in short terms as it is a key to the stable functioning of the industry and safe flights. The operational success of new measures can be evidenced by the safe and secure operation of the whole civil aviation, regardless of the region, in the face of new cyber threats, their diversification, and constantly appearing vulnerabilities. Under these conditions, the existing literature evidences that cyberthreat and security become essential concerns that should be given much attention because of their importance for the sphere.
One of the major factors which increase the importance of this aspect is the radical reconsideration and reorganisation of workplaces with the primary goal to increase the effectiveness of workers (Ferguson and Nelson, 2013). For this reason, today, all specialists belonging to civil aviation use devices, applications, and electronic systems to share important information, experience, and communicate. This change in the working process results in the emergence of an entirely new digital environment characterised by multiple opportunities both for better collaboration and, at the same time, risks associated with cybercrime (Ferguson and Nelson, 2013).
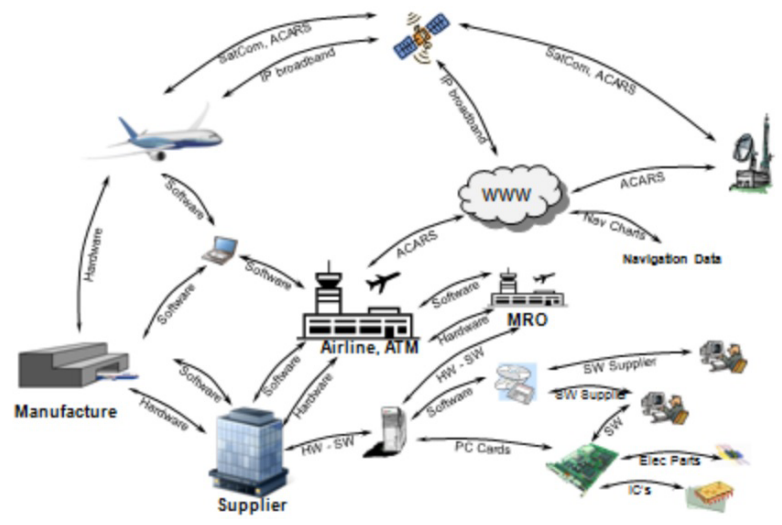
As it can be seen in Figure 3, there is a significant reliance on software, hardware, and different applications that are used at different stages and with various purposes. The aircraft, ground services, pilots, and security systems depend on the correct functioning of digital devices, supplements, and satellites which manage the work of all departments and their cooperation (Ferguson and Nelson, 2013). The complexity of the given environment demonstrates that the attack can occur at any stage, starting from the manufacturing phase and ending with the work of pilots. Under these conditions, the industry should remain vigilant about the new threats linked to the use of computers, devices, and applications with the primary goal to cause harm to airlines. The creation of universal and secure approaches and cybersecurity frameworks acquires the top priority as a way to guarantee the stable functioning of fundamental elements of civil aviation.
The severity of the challenge is also proven by the fact that ICAO persuades all Member states to introduce appropriate legislation and regulations to use them in different situations lined to cybersecurity (ICAO, 2019a). This goal should be achieved before establishing a national cybersecurity policy for civil aviation; otherwise, airlines will lack tools to solve problems arising because of this factor (ICAO, 2019a). The establishment of the legal field will drive the appropriate rise of means and guides for states and industries to offer a strong response to new risks and problems (ICAO, 2019a). International agencies also recommend including cybersecurity within a State’s aviation security and safety oversight as the vital element of risk management framework as it will create the basis for the further enhancement (IATA, 2019; ICAO, 2019a). There is a critical need for the provision of guidance materials about risk assessments and management to prepare specialists for new challenges that emerge because of the continuous increase in the number of hacker attacks and substantial harm caused by them.
The majority of sources selected for the literature review emphasise the idea that the threat of cyberattacks should be viewed as one major emerging problems peculiar to aviation today. One of the most dangerous features of this issue is the diversification of the nature of this problem and the vulnerability of all airlines and companies related to the functioning of aviation, regardless of the region and security systems used to protect individuals. That is why the introduction of a consistent approach to reveal, organise, and manage the emerging threats becomes the pivotal task for specialists and agencies such as ICAO, IATA, CANSA.
Human Factor
Previously, we mentioned the idea that human factors should also be included in the list of relevant threats that should be considered. Speaking about the concept in terms of aviation, ICAO determines it as a multidisciplinary attempt to create knowledge describing human skills, experiences, and limitations and apply it to the industry with the primary goal to establish a safe, effective, and comfortable human performance (FAA, 2014). The given concept is not new to the aviation sphere, and it has always been topical because of the critical importance of individuals and their solutions for the safety of passengers and aircraft. For this reason, there have always been multiple measures and recommendations aimed at decreasing risks and probability of mistake made by specialists and the creation of the environment characterised by their improved functioning. ICAO (2016) includes human error and inappropriate decision making in the list of top five threats to aviation, which means that the concept remains extremely important today. The work of all existing security systems also critically depends on human factors, for this reason, there is a critical need for their consideration as one of the possible threats to the industry.
Another element evidencing the need for improved attention to human factors is the statistics of accidents and crashes. ICAO (2019a) reports that 72% of all failures and problematic situations in the industry are associated with errors made by specialists working in civil aviation, including pilots, representatives of ground service, personnel responsible for the maintenance. The given number is too high for the sphere presupposing the high level of responsibility for people’s lives. With the sophistication of technologies, systems, and software, the problem acquires a new meaning. From one hand, new systems mean that the opportunity of mistake decreases because of the evolution of Artificial Intelligence (AI) and the employment of innovative solutions that help to reduce the risks. However, from another hand, the implementation of complex applications and software means that specialists working with it demand the increased level of skills, knowledge, and competence to operate and make correct decisions. For instance, pilots today work in an extremely stressful and complex environment with multiple devices surrounding them. At the same time, during accidents, they remain responsible for decision-making and outcomes. It means that entering the new phase of its evolution, the aviation industry also faces new challenges and threats associated with the concept of the human factor.
The current body of evidence states that the majority of mistakes occur under the impact of three domains: environment, technology, and human. They impact each other and precondition the emergence of dangerous situations that might decrease the effectiveness of a worker and create the basis for an accident (Tommaso, d’Amore and Di Camillo, 2016). In such a way, with the growth of technology domain, means that risks linked to human factors also grow and should be followed by an appropriate change in the current approach to managing and organising the given issue. Among all challenges, IATA (2018) outlines the chance of existing protection systems’ failure due to the inability of workers to perform their duties correctly. It becomes a serious concern in terms of the diversification of terrorist threat and the requirement for measures to protect people from emerging threats.
The existing airports rely on the work of security systems that can determine, analyse, and respond to a known threat by using available resources and mechanisms (Ferguson and Nelson, 2013). However, regardless of the innovative solutions integrated into their functioning and risk-based approach that dominates today, the work of individuals remains central for the creation of protected areas and guaranteeing the stable work of airports and airlines (ICAO, 2019a). The low level of preparedness, weak motivation and concentration, and lack of attention can result in the appearance of loopholes and their use by attackers to cause harm. For this reason, the rise of technologies should be followed by the reconsideration of the approach to human factors management to decrease the number of vulnerabilities and threats.
Professional burnout is another crucial aspect related to the human factor. The existing statistics show that in civil aviation fatigue combined with burnout syndrome increase the risk of a crash up to 50% (Sheridan, 2016). Moreover, in accidents preconditioned by inappropriate actions of pilots or other specialists, burnout was one of the factors that impacted their decision-making and use of wrong strategies. Under these conditions, agencies such as ICAO and IATA, emphasise the need for sufficient burnout identification and the use of strategies that will help to cope with work-related stress (ICAO, 2019). The development of anti-burnout practices and their implementation should be preconditioned by the local factors and stressors affecting specialists at their workplace. This knowledge is fundamental for improved management of human factors and depreciation in the number of mistakes linked to the inappropriate decision-making or inability to act effectively in complex situations.
Altogether, human factors have always been topical for the civil aviation sphere, and multiple approaches are used to manage the topic. The existing literature accepts the fact that the fast growth of aviation introduces new challenges to the given sphere as innovative solutions and approaches demand the improved understanding from specialists working in airlines. That is why the given threat should be considered one of the issues vital for the creation of a safe environment and protection of passengers.
Insider Threat
Analysing the existing issues in the sphere of civil aviation, it is critical to mention insider threat as one of the factors given much attention by specialists and appropriate literature. One of the factors preconditioning the high relevance of the given issue is the increased sophistication and effectiveness of existing security measures that are employed by civil aviation (Coles-Kemp and Theoharidou, 2010). The combined efforts of various regulatory agencies such as IATA and ICAO and the cooperation with governments contributed to the creation of a practical approach to managing all known hazards, minimising risks, and preventing terrorist acts (ICAO, 2018; IATA, 2018). The correct understanding of the nature of vulnerabilities, methods utilised by terrorists, and other problematic issues contribute to the creation of a knowledge base and framework that is used to design innovative security systems deprived of drawbacks and protected from outside attacks (Coles-Kemp and Theoharidou, 2010). Malefactors look for new methods to bypass all countermeasures and damage civil aviation. Under these conditions, an insider threat acquires the top priority as it is one of the possible ways to destroy barriers from inside and create new loopholes offering opportunities for attackers. The importance of the given problem is evidenced by the fact that it is recognised by the IATA and ICAO and other authorities that provide guidelines for the minimisation of these risks and the creation of appropriate strategies to resist them.
There are multiple approaches and definitions of the insider threat and its nature. In general, it can be described as the existence of one or a group of individuals who possess or have access to insider knowledge that can be used to exploit vulnerabilities of the current security systems with the primary goal to cause severe damage (Bean, 2017). The given problem firstly appeared in the late 80s with the first attempts to sabotage aircraft and transformed into one of the growing concerns with the tendency to rapid self-radicalisation that is observed in many states today (Cole and Ring, 2006). One of the difficulties associated with this question is that there is a variety of forms that can be peculiar to insider threats, and there is a need to consider this diversity (Bean, 2017). Malefactors can share data crucial for the work of the protection system, corrupt information systems, smuggle goods or people, outline all existing loopholes or enter terrorist groups to help them perform violent actions aimed at the destabilisation of the situation (Bean, 2017). The broad scope of the issue shows the necessity for appropriate interventions to avoid the collapse and help aviation to survive and resist attacks.
The vigorous discussion of the problem is also linked to the idea that insider threat can be associated with terrorist groups. Because of the complexity of security systems mentioned above, and their effectiveness, malefactors change their tactics and start to analyse objects that are selected as the aim for new attacks. The data collection presupposes the use of their own agents. The latter work in airlines and have access to essential data that can be employed to find or create a loophole which can be later used for various purposes (Probst et al., 2010). That is why IATA (2018) aims at the creation of increased awareness among companies, partners, and authorities about the insider threat to engage in cooperation and create a framework that can help to eliminate potentially problematic areas. Moreover, due to the diversification of methods used by insiders and the use of innovative technologies to corrupt the work of the sector, an appropriate change in the approach to cybersecurity should also be aligned to ensure the positive outcomes and guarantee the high level of protection to all stakeholders.
The literature shows that there are various types of insiders, which is critical for the ability to introduce appropriate responses and eliminate a potential threat. Differences among this cohort include the physical and logical presence, as there can be malefactors working in different environments (Neman 2010). Moreover, there are various degrees of insiders regarding the level of their access, the information available to them, and their role in the company (Neman, 2010). In such a way, the ability to work with essential data portions or impact decision making creates the basis for the appearance of multiple chances to intervene with the work of systems and corrupt them (Siao, 2017). Both categories of malefactors possess an opportunity to cause severe harm to the company and make it vulnerable to terrorist attacks. For example, a multi-level security system can be bypassed by using insider data available both for logically or physically present malefactors (Neman, 2010). It means that there are no effective measures to resist attacks if the company disregards the given sort of threat and avoids additional security measures.
Additionally, there are different types of insider misuse, such as intentional and accidental ones. Although both these forms are dangerous for airlines, more attention should be given to the first one as it poses a serious threat to existing security systems. The occurrence of accidental insider threats can be explained by the human factor and mistakes that can be found in the work of any specialist because of such factors as tiredness, low motivation, stress (Neman 2010). Unfortunately, it does not reduce the severity of harm that can be done by such actions and the complexity of the situation (Neman 2010). The accidental insider threat remains one of the causes for incidents as the inappropriate use of data, or its sharing creates the loopholes in security systems and safety measures. The professional burnout, fatigue, high level of stress, and poor working conditions affect specialists in various departments and increase the risk of insider threat (Neman 2010). The report states that regardless of some attempts to improve the situation, the accidental insider threat remains a significant factor that should be taken into account by agencies and security specialists working in the sphere.
The intentional insider misuse indicates the existence of the desire to cause serious harm to the company or passengers either by providing information to third parties or by using it on his/her own (Neman 2010). In some cases, it can be hidden or concealed by emphasising its accidental nature, which can help to reveal existing vulnerabilities and how companies cope with them to find the most effective way to use the current loopholes. The significance of the given problem comes from its scope, the existence of various forms, and challenges in detecting the source of maleficent actions if it comes from employees who possess critical information or access to it. There is a need for the reconsideration of the existing approaches to safety management to ensure that new environment characterised by the absence of risks is created and functions in accordance with the guidelines.
Drones
Unmanned devices can be considered another issue that acquires increased topicality nowadays. For a long period, drones have been viewed as a less meaningful technology that can be used by amateurs with different purposes. With the fast rise of technologies, the modern devices of this sort acquire the opportunity to perform multiple functions and cope with tasks. Today, drones are widely used by armies, intelligence services, and aviation as the way to collect information, protect specific objects, and ensure that a strategically important area is controlled (Zhang, 2018). They can be equipped with various tools regarding the existing goal and function in different environments. For this reason, researches admit the growing topicality of unmanned aircraft for all spheres of human activity, including aviation.
The rising importance of unmanned aerial vehicles (UAVs) for civil aviation can also be evidenced by the increase in the number of accidents that are caused by these devices. For instance, there are recently verified aircraft collisions involving drones and resulting in some damage. On September 21, 2017, a civilian UAV preconditioned the crash of a Black Hawk helicopter, and its parts were found at the bottom of the rotor system (Zhang, 2018). Another case happened on October 12, 2017, when a Beech King Air A 100 collided with UAV close to Quebec City, Canada. The aircraft managed to land safely; however, its wing was seriously damaged, and there were multiple risks of a disaster (Drone crashes, no date). Moreover, in 2016, the pilot of flight BA727, British Airways reported a collision with a UAV, and fortunately, none of the passengers and members of the crew were injured (West et al., 2019). The given examples evidence that even civilians with no maleficent intentions can precondition damage to airlines and aircraft and precondition a collapse and multiple victims. With the following development of the technology and UAVs becoming more complex, the given threat will continue to grow.
The existing literature shows that ICAO, IATA, and other agencies responsible for the secure work of the aviation sphere demonstrate their concerns related for the use of drones by terrorist groups and radicals to cause severe damage to aircraft or strategically important areas. The recent events in the Middle Eastern region and the war against terrorism demonstrate that organisations such as ISIS have enough resources to acquire UAVs and utilise them with various purposes (Lin, 2017). These might include a collection of information, spying, coordinating attacks, and causing damage by using weapons or crashing aircraft (LaFlamme, 2018). At the same time, drones can be hard to detect and classify as according to the Federal Aviation Administration, only in the USA there are about 1.1 million of UAVs used by individuals as a part of their hobbies (III, no date). Globally, the number of drones can estimate more than 4 million and continues to grow annually because of the evolution of technology and its becoming cheaper and affordable to diverse populations (Argrow, 2016). Under these conditions, the civil aviation sphere today has to face a new emerging threat associated with the use of UAVs by different groups and the need to create effective measures to manage these risks.
Drones can also be viewed as a way to empower existing security systems and make them more effective in collecting data and detecting threats. ICAO and IATA agree in the opinion that civil aviation today should be ready to make UAVs an integral part of its protection measures because of the promising nature of this technology and its future (Marcellin, 2020). Among possible areas that can benefit from the integration of drones, the existing literature most of all emphasises inspections of places and aircraft, especially locations that are hard-to-reach by people (Susini, 2015). There is a specific strategy that is proposed as a possible solution to emerging threats which can be viewed as a new approach to risk management.
Civil aviation sphere can also benefit from using drones to manage the environmental factors. Today, drones are employed to gather data about weather conditions, its recent changes, and whether there are some factors that should be taken into account by pilots and ground personnel to guarantee the increased safety of flights (Hoggan, 2019). The given option is central for areas with complex meteorological conditions, characterised by the high risk of storms, or situations with low visibility (Hoggan, 2019). The use of drones will contribute to the increased accuracy of forecasts, and the reduction in the number of accidents cause by the environmental factors (Hoggan, 2019). For this reason, the existing body of evidence accepts the critical importance of drones for civil aviation and views it as an integral part of the sector’s future.
Drones should be included in the list of emerging threats that become a nagging problem for civil aviation because of the risk of using them by malefactors and terrorist groups. Their growing number and diversification of strategies can increase the level of risk and destroy security systems. UAVs can also be used as powerful tools to manage and organise new hazards and remain prepared for various scenario and attacks.
Solutions
As stated previously, the need for improved management and organising of emerging threats becomes the central concern of civil aviation today. The possible solutions to this problem should focus on the most problematic areas and include technologies and approaches that can be used by attackers. For this reason, the existing literature focuses on several solutions such as the use of drones as a part of defence strategy, creation of improved security systems which benefit from the integration of innovative technologies, and the use of innovative software that is designed with the primary goal to collect up-to-date information, process it, and respond to new threats by selecting the most appropriate decision or recovering fast after damage. The given measures should also be able to consider human factors and the high level of insider threat as other concerns which preserve their topicality and can precondition sever harm to the whole industry.
Improved Security Systems
Previously, we have stated that a risk-based approach can be viewed fundamental part of next improvements and achievement of the desired level of safety within the aviation sphere. The irreplaceability of a risk-based approach is all modern security systems that are used by airlines in their work are designed regarding this framework (Hildebrand, 2019). Resting on the existing understanding of cyber threats and other risks, any unit of that sort aims at adopting a flexible risk-based approach to the protection by the implementation and further improvement of management approaches (IATA, no date). The main objectives also include the necessity to adhere to this very paradigm and cultivate a method that will incorporate the fundamental elements of the discussed model as they ensure the high performance levels and constant renewal of data, which is a key to the successful work. There are also several strict demands to modern and future security systems that should be observed to guarantee that they are capable of managing new threats and protecting people. It means that the improved security framework should be intelligence-driven, adaptable, layered, evolving, and unpredictable (Elias, 2014). Integrating all these qualities, specialists will be able to create an approach that meets all modern requirements to the creation of a safe environment and contribute to the increased level of protection. At the same time, they guarantee that all emerging threats will be covered and managed appropriately.
Intelligence Driven
Analysing the outlined elements, the vital character of intelligence information should be admitted. For instance, Israel, a country that faces the high level of terrorist threat because of the complex relations with its neighbours, employs demographic profiling intelligence and specialised databases to identify passengers who might pose high risks and minimise the level of threat (Elias, 2014). This method rests on information provided by intelligence services that monitor the current situation and respond to emerging dangers. As a result, the country has avoided serious terrorist acts in the aviation sphere for 40 years (Elias, 2014). This example evidences the ability of the risk-based approach to create a safe environment and resist threats assuming that it remains intelligence-driven, and there is a constant exchange of critical information between various airlines and airports. Sharing experiences and best ways to avoid undesired situations, agents or security specialists acquire an opportunity to protect passengers and benefit from the offered paradigm.
Unpredictable
The unpredictability of any security system that is used by airlines is another key component of a modern risk-based approach. As it comes from the main idea of the contemporary vision of safety, all expected and unexpected complications should be taken into account to protect individuals (Elias, 2014). For this reason, a method that is employed at the moment should be ready to work in stressful situations. This can be achieved in several ways, and one of them is the avoidance of predictability in risk evaluation and analysis. In other words, security systems should possess random screening techniques or assessment procedures that will help to confuse malefactors (Elias 2014). It will also help to minimise chances to discover loopholes or vulnerabilities by performing multiple attempts (ICAO, 2017b). That is why unpredictability becomes a critical element of a fully risk-based approach providing new opportunities to puzzle individuals who want to damage airlines or aircraft.
Adaptive
As far as aviation is one of the most fast-growing spheres of contemporary society, the majority of airlines have to work in changing conditions and be ready to face new challenges or problematic issues that might deteriorate their functioning. Every security system should not be rigid to respond to all risks on very short notice (Elias, 2014). It means that the ability to adapt to a changing threat picture is a core quality of risk-based approach that serves as the basis for the organisation of security in airports. Fast and effective elimination of dangers and provision of appropriate measures to mitigate negative consequences and save lives are fundamental for the modern aviation sector. Implementation of any frameworks should adapt to the existing culture, societal constraints, legal basis, and passengers’ demands to the work of security services (Elias. 2014). It will help to avoid complications in the future and create a highly protected environment characterised by the high level of clients’ satisfaction.
Layered
Any existing security system should also be layered as it is one of the main aspects of a risk-based approach. As it has already been stated, the definition of risks includes threats, vulnerabilities, and consequences that are taken into account. To work with every aspect separately, it is critical to incorporate several elements within a single approach. Moreover, they should remain isolated and independent to ensure that the failure of one system will not affect other ones and reduce their effectiveness. In this regard, the layered character of the utilised approach is one of the requirements to protective measures peculiar to airlines of airports (Elias, 2014). It helps to segment and classify any threat and its elements and find the most effective ways to work with each of them, which is essential regarding the high level of demands to the quality of protection and safety.
Evolving
Finally, a security system should not stop in its evolution. Research about the effectiveness of various protective measures evidence, that overly rigid approaches show an unacceptably low level of performance as they lack information about new threats and risks (Price and Forrest, 2013). Moreover, the risk-based approach emphasises the need for constant evolution and the discovery of new potential dangers and ways to respond to them (Elias, 2014). That is why a modern security system should be capable of developing and achieving new levels of excellence (Elias, 2014). It can also be achieved by incorporating new technologies, devices, and utilising knowledge about continually changing threat landscapes (Elias, 2014). The continuous evolution of protective measures minimises the probability of intervention as malefactors have to look for new ways to interfere with the functioning of airports or aircraft because previous ones turn out to be obsolete. It ensures fast and effective responses to any attempts to trigger the appearance and development of undesired situations.
In such a way, the incorporation of all these attributes within a single security system and with regard to the risk-based approach helps to consider the majority of emerging risks and contribute to the increasing effectiveness of employed protective measures. This fact evidences the high potential of the discussed method and its ability to work with the fast-changing environment or threat landscape by acquiring information about possible dangers, evolving, and offering new responses to them. The literature also emphasises the fact that the full risk-based approach supported by the use of the improved security systems should become a new trend in civil aviation because of its ability to discover and trace problems emerging in the sphere. At the same time, the adaptive and layered nature of such systems means that they will remain more resistant to outsider and insider threat, which is vital for the achievement of current goals. The qualities mentioned above should be used as the major determinants of all security systems used in the civil aviation sphere by airlines. Furthermore, the systems that already exist should be reconsidered and reorganised to be able to meet the growing need for better security and safety management. That is why the unpredictable and adaptive systems are the future of civil aviation today.
Drones
Another effective measure that can be employed to improve the current situation, increase airlines’ preparedness and awareness of attacks, and protect passengers are UAVs. The use of drones is viewed by specialists as a potent and promising way to remain vigilant and responsive as their constantly updating characteristics along with the emergence of multiple opportunities to use them can guarantee improved results in the future. For instance, one of the most attractive ways in which drones can enhance airport operations and minimise input is their use for maintenance operations and inspection activities (Price, 2018). Precision Approach Path Indicator (PAPI) activities have always been performed by special flight inspection aircraft and have been an expensive method to guarantee the stable functioning of the industry (ICAO, 2020). However, drones can be equipped and employed to assess PAPI units and their functioning in terms of all regulations such as transition angles, symmetry, and horizontality as it is stated by ICAO (2020). This strategy shows that using UAVs civil aviation can save costs, and, at the same time, improve maintenance operations which is critical for outcomes and creation of the safe environment.
Speaking about maintenance sphere and procedures, Price (2018) states that micro drones also have a strong potential and can be used to make the industry safer. For instance, the existing statistics show that there is a comparatively high risk that a defect in hard-to-reach will not be noticed by inspectors (Marcellin, 2020). It increases the risk of a crash significantly, which is also proven by numbers as about 25% of crashes happen because of the faults of some systems in aircraft (Tiller and Bliss, 2017). That is why today there is a positive experience of using micro-drones during the visual inspection as they help to save time and improve outcomes due to the increased accuracy (Uriondo, Esperon-Miguez and Perinpanayagam, 2015). Rolls-Royce reports a positive experience of using micro-versions of camera robots to increase the effectiveness of inspection of components placed in difficult-to-reach areas (Zhu, Li and Tong, 2013). EasyJet has a similar strategy presupposing the use of completely autonomous UAV, collecting information about the state of an aircraft and outlining all issues that should be solved (Esposito et al., 2019). Ultra-sound investigations can also be performed by drones to detect defects in materials and improve the safety of flights by repairing these issues (Esposito et al., 2019).
The interest to drones in civil aviation is also explained by the fact that there are multiple variants of their usage. For instance, UAVs can become a meaningful part of security systems and be employed for patrolling and securing areas guaranteeing that there are no intruders or attackers (Esposito et al., 2019). In this regard, the military experience is nowadays examined and used by airlines when planning their security systems which rely on unmanned aircraft. In the army, drones can monitor a certain location and protect it by using different devices (Tiller and Bliss, 2017). For civil aviation, it means that this sort of robots can check the airport area and prevent attacks of other drones, or collect information about suspicious objects or individuals (Shappell et al., 2007). The effectiveness of UAVs can be increased by using X-Ray technology for several purposes. First of all, it can help to discover defects in surfaces and materials that are used in aircraft. The given module can be helpful when evaluating the content of various packages and provide detailed information to security officers responsible for decision-making and protection (Mitroff, Ericson and Sharpe, 2018). It means that drones can change the current approach and ensure that a higher level of security is achieved.
Another advantage of drones is the high variability of equipment that can be installed on them. For instance, thermography is one of the possible technologies that can guarantee multiple advantages for civil aviation. Drones with these modules can examine the state of the aircraft, look for details that should be replaced, and warn specialists about the necessity of repair (Esposito et al., 2019). It will help to increase the accuracy of examinations, reduce costs, and ensure the absence of defects which can impact the plane in the air. Due to these benefits, the civil aviation sphere is concerned about implementing UAVs in its functioning to create a new, more effective and secure environment.
Agencies such as ICAO, IATA, and FAA are aware of the growing number of civil drones, and of UAVs that can be used by terrorists and attackers. For this reason, they introduce measures regulating the flight areas and introducing strict prohibitions of using drones in airport areas (Madan, Banik and Bein, 2019). The recent events and accidents involving this sort of devices show that they can be potentially dangerous to aircraft. For this reason, there is a need to ensure that strategically important places will be protected from any interventions, including unmanned vehicles (National strategy for aviation security, 2018). ICAO (2020) establishes a new framework presupposing that no drones except for those belonging to airlines can fly in the airport area, which is a key to better security systems. UAVs have the opportunity to intercept other drones and destroy them if there is a risk of intrusion.
Innovative Software
The diversification of existing risks and the constant emergence of new threats means that modern security systems should also change to remain capable of detecting and responding to all possible hazards or attacks. One of the possible ways to achieve the demanded levels of protection is the use of new software that is less vulnerable and guarantees improved security levels. Moreover, as stated previously, cyberthreat and cyberwar are rising concerns for modern aviation, which means that there is a new for software that will be able to resist different types of threats and guarantee the stable functioning of airports and their security systems. In this regard, the leading international aviation organisations, such as ICAO, IATA, ICCAIA, ACI, and CANSO agreed on the cooperation, and exchange of data, their visions, and perspectives, with the primary goal to create a Roadmap outlining the primary purposes for the achievement of better resistance to cyberthreats and creation of innovative and practical software (Tunnicliffe, 2020). Among other vital assumptions, the Roadmap emphasises the need for the promotion of robust cybersecurity culture, mechanisms of data sharing, employment of best practices, and increased situational awareness (CANSO, 2014). For this reason, the innovative software that is expected to replace the old one should possess all these qualities and be capable of responding to all threats and risks that emerge, collecting data, and using it to improve.
One of the most promising ways to achieve the desired goal is to use Artificial Intelligence (AI) as a basis for new applications and software used in security systems. The term refers to the simulation of human intelligence in machines that are designed to think similar to human beings and possessed improved learning and problem-solving patterns (Natale and Ballatore, 2020). The advantage of this technology is the ability to process a giant amount of information in short periods of time and select the most effective solutions to some problems. Moreover, its ability to learn is crucial regarding the complexity of the sphere and the constant emergence of new threats that might deteriorate the work of aircraft and precondition serious crashes (Tunnicliffe, 2020). That is why the integration of AI into the functioning of civil aviation sphere is one of the central ways to manage new threats and guarantee its stability.
Speaking about airport security, numerous authors state that machine learning and AI can be employed to process massive amounts of data and identify threats much faster than any individual can (How can AI help speed up airport security?, 2019). It means that scanning and security checks become more effective. Items that previously had to be investigated separately, such as notebooks, smartphones, and other devices containing information or potentially dangerous applications, can remain in luggage because of the AI’s capability of evaluating and scanning them (Hättenschwiler, Mendes and Schwaninger, 2019). It significantly reduces the time needed for a complete analysis, improves outcomes, and reduces the level of passengers’ dissatisfaction caused by delays and too high level of security officers’ attention (U.S. Government Accountability Office, 2017). AI is also widely used nowadays in the airport environment in different states as a tool to identify threats coming from passengers. For instance, self-service passenger check-in robots equipped with AI have better facial recognition characteristics, which is critical for custom workers and areas (Brock and von Wangenheim, 2019). It helps to detect criminals, terrorists, and other malefactors who try to change their appearance and enter a secured place. AI becomes a potent tool that helps to minimise risks by noticing the strange aspects of human behaviour and reporting them to appropriate services.
The existing AI technology is also capable of identifying the most dangerous threats and weapons. For instance, 3D imaging devices can scan passengers to identify the smallest weapon starting from knives and ending with guns to protect the crew and other passengers (Hoggan, 2019). Bombs, suicide vests, and chemicals can also be found by using the most innovative equipment that is gradually added to modern airports as a way to attain better outcomes and guarantee that no damage will be caused to aircraft and security areas (Hoggan, 2019). In such a way, AI becomes a critical part of innovative software that should replace the old one as an effective way to resist emerging threats.
Turning back to the ability to learn, it should be said that this feature plays a central role in ICAO and IATA’s recommendations about innovative software and its use in airports. Hoggan (2019) states that with the diversification of risks and hazards, systems with a low level of flexibility lose their importance and cannot be viewed as sufficient measures to remain aware and resist new challenges. They can work only with already known issues and demonstrate the limited capability of detecting and signalling about new hazards. At the same time, AI-equipped applications and systems continue to learn by collecting information about recent cases, risks, and ways to overcome them, which makes them extremely important for civil aviation (Swann et al., 2019). Machine learning becomes an answer to multiple questions as it creates new strategies for recovery and resistance. Moreover, today airlines should balance between the creation of robust and effective aviation security frameworks that protect all individuals and guarantee that large numbers of travellers can pass through checks with no delays (Sheridan, 2016). Under these conditions, AI becomes a perfect solution to both these issues as it combines effectiveness and speed along with the opportunity to learn.
In general, the role of AI is viewed as fundamental today. ICAO and IATA recognise it as a game-changer in aviation as it offers multiple tools and strategies to improve safety, adaptability, optimisation, and capacity (ICAO, 2019a). Because of the diversity of proposed solutions and applications today, there is a demand for certification and qualification standards to ensure that AI will meet the existing demands to quality and stability (ICAO, 2019b). Because of the high speed of digitalisation, there is a need to move from old regulatory requirements and establish new ones, which take into account the trustworthiness of AI, its exploitability, and correctness (Department for Transport, 2018). The use of these approaches in selecting AI and its integration into the security systems will significantly reduce the risk of failure and its inability to work effectively under the high pressure or in real-life conditions.
Altogether, the use of innovative software to create secured environments is one of the effective methods to manage and respond to emerging threats. AI’s ability to acquire and process new information becomes critically important for civil aviation. ICAO, IATA, and the majority of authors recognise new applications with AI and machine learning features as a critical part of future aviation. It can increase passengers’ satisfaction levels, and, at the same time, guarantee that malefactors will be detected and prevented from harming aircraft, passengers, or strategic areas.
Conclusion
The given literature review shows that civil aviation is one of the strategically significant means of transport that plays a critical role in the modern world today. Its importance and irreplaceability in terms of international relations create the basis for its fast and stable rise and the increase in the number of passengers who use the different airlines’ services every year. However, because of this significance, aviation is often a target for attacks and actions aimed at the destabilisation of its functioning and spreading havoc. Under these conditions, using information from various sources, it is possible to conclude that the sector also experiences one of the hardest periods of its development because of the emergence and diversification of multiple threats. Because of the critical importance of the preservation of the safe environment and protection of human lives, security officers should be capable of managing and organising all types of new hazards. That is why the existing body of evidence emphasises the fundamental role of data collection and exchange as one of the possible ways to remain aware of the current situation and be able to function effectively.
Among relevant threats, the researchers traditionally accept the danger coming from terrorist, as one of the forces that continuously evolves and acquires new means of attacking and causing severe damage to aviation. The rise of technologies provides malefactors with tools that can employ loopholes in security systems and create the basis for accidents. Another concern is a cybercrime that becomes more topical today because of two factors. First of all, the digitalisation of the environment in airports meaning that there are multiple systems and software that can be attacked by hackers to steal data or cause problems in management. Second, the evolution of cyber threat is linked to the sophistication of devices and applications that are used by terrorists to attack aviation.
Human factors remain another critical concern that becomes topical due to the high responsibility levels and the need to use more complex software needed to ensure the appropriate security. For this reason, the probability of mistake remains high and, moreover, new risks emerge every day. The literature emphasises the emergence of a new type of threat which is the use of drones, or UAVs to cause damage to aircraft or airport areas, or to collect strategically important information to destroy security systems. Unmanned aircraft becomes more popular today, which means that there are multiple civilians who also use it, which makes the task of identifying a potential threat even more complex. Additionally, the opportunity to use different equipment and perform multiple tasks makes UAVs even more dangerous for civil aviation.
Considering the given threats, the current literature offers a set of possible solutions and recommendations that can help to improve the current situation and help to manage all new risks more effectively. First of all, ICAO and IATA insist on the employment of innovative, constantly updating systems that function resting on full-based approach and the ability to collect information and evolve. The intelligence-driven, adaptive, layered, and developing systems should replace the old ones and become the central method of organising and managing threats. It will also ensure that the data acquired from previous cases will be processed and analysed correctly to create an appropriate response to existing risks. Moreover, drones should also become an integral part of existing security systems and maintenance procedures as they help to reduce costs, time, and attain higher efficiency levels. Being equipped with X-Ray devices UAVs can examine luggage, scan faces, and prevent other drones from entering the area or attacking aircraft. In such a way, the literature recognises the critical importance of drones and offers a set of recommendations for their use with defensive purposes. They can also bring significant change to civil aviation as multiple opportunities associated with drones are vital for the sector.
Finally, the possible way to manage new threats is the use of innovative software, including AI with machine learning. This feature is vital for security systems today as the ability to acquire information, process it, and share contributes to the in-time detection of all possible threats and creation of measures needed to protect individuals and avoid accidents. AI should be used for better security checks and monitoring of hazards. However, because of the diversity in new applications and systems created by unknown developers, regulations and quality standards should be established to check the trustworthiness of applications, their ability to meet current demands, and function in real-life conditions.
The relevant literature outlines a serious number of threats that emerge today and offer the use of innovations as one of the possible ways to resist them and guarantee safety to all individuals who use services of airlines or specialists working within a sector. ICAO, IATA, and other regulatory agencies work on the development and introduction of guidelines that will be able to consider the diversity of new threats and help the Member States to cope with them. It also means that data collection, processing, and its exchange can also be viewed as a central element of modern security systems as it helps to create measures that consider new barriers and limits, and are capable of their mitigation and management. New security systems should also possess enhanced information and knowledge sharing options as the fundamental component of their functioning in modern sophisticated and changing environment.
Methodology
Introduction
This part of the project presents the methods that are employed in terms of the study. It justifies the choice of these very methods to acquire the needed information, discuss it and process appropriately. The appropriate choice of the methodology is fundamental for research as it preconditions the credibility of findings and guarantees that acquired results can later be used in other projects. Moreover, the goals and the research questions formulated at the beginning of the study should be followed by the appropriate methodology and investigation approach to ensure that there are no flaws and the selected issue is analysed comprehensively (Bloomberg and Volpe, 2018). Under these conditions, the given section provides a detailed description of a paradigm, approach to data collection, analysis, and its discussion, as well as the explanation why the given method meets the goals formulated in the first section.
Explanation of the Approach
The scope of the investigated problem presupposes the use of specific research paradigm that will guarantee that only relevant and non-biased data will be used as the basis for the analysis and discussion. The chosen methodology preconditions outcomes of the whole project, its practical utility, and applicability of results. That is why the given section is critical for the discussed project as it aims at the in-depth investigation of existing threats, and ways to manage them. The work presupposes the employment of the inductive approach and the qualitative research methods to acquire all data vital for discussion.
The central idea of the inductive framework is that theories related to the investigated issue are offered at the end of the research as the result of observations and data processing (Creswell, 2013). It means that by utilising this research paradigm, we can make premises resting on information, facts, and pieces of evidence collected in the course of research. At the same time, the inductive approach gives more space for theorising and offering multiple visions of the problem and how it can be managed by using innovative solutions and methods (Billups, 2020). Moreover, using the results of the literature review, and adhering to the inductive approach, it is possible to formulate the basic assumptions and predictions about how the sphere will evolve in the future. For this reason, the adherence to this method can be considered advantageous for the study as it will promote the in-depth analysis of the selected problem due to work with secondary data sources.
The choice of the qualitative framework can be justified by several factors. First of all, it can be considered a more flexible approach, if to compare with the qualitative one, as it is less dependent on numbers. Instead, the context and the current situation in the investigated sphere acquire the top priority (Creswell, 2013). For civil aviation sphere and challenges it faces at the moment, it becomes a more advantageous option as it provides a chance to view the scope of the topic and changes which happen in the sector (Billups, 2020). The qualitative methodologies are more effective in collecting contextual data which describe the rise of particular trends and their impact on the functioning of specialists, which is one of the prior tasks of the research (Billups, 2020).
Second, the employment of this method guarantees the preservation of focus on a selected topic and its evaluation from different perspectives, which is vital for the comprehensive analysis of the issue (Creswell, 2013). Revolving around the challenges civil aviation faces today, it is critically important to consider all possible stressors and aspects that might impact its further evolution. By using the qualitative research design, we acquire an increased degree of flexibility to assess all factors and use this knowledge in research (Maxwell, 2013). For this reason, the preference for this mode is given.
Finally, the qualitative methodology contributes to the generation of a better vision of some points that are related to the chosen question and offers numerous research tools that are necessary for data collection. The adherence to this research paradigm can help to integrate human experiences in the research and use them as the factor that explains the effectiveness of some measures (Merriam and Tisd, 2015). That is why the use of the qualitative data collection methodology becomes justified by the advantages that are associated with this option and the nature of the research, which presupposes the contextual information that might change under the impact of different factors.
The project also presupposes the use of a literature review as one of the central methods of information collection. It is a beneficial way to gather facts about the existing threats from credible research works or other sources that provide different visions of the current risks and ways to mitigate them (Creswell, 2013). Additionally, the literature review is capable of establishing the basis for debates and discussion as it uses credible and relevant data from various sources (Yin, 2017). Researchers admit the high effectiveness of the given tool and its positive impact on results (Yin, 2017). For this reason, we view literature analysis as the potent data collection and processing tool that would help to determine the main threats. The topicality of the selected problem guarantees availability and access to multiple other research projects that are related to the question, and that can be used to create the background for the discussion.
The project presupposes the use of inductive research paradigm supported by qualitative methodology and literature review. It is expected that the employment of this approach will help to avoid biases in conclusions or collection of corrupted or irrelevant data. At the same time, the nature of the project, the need to determine current threats and the ways to manage them precondition the need for specific research tools. For this reason, the choice of methodology comes from the goals and vision of the project. It guarantees that information needed to conclude about the existing threats and ways to resist them will be collected and processed appropriately.
Data Collection
Adherence to the paradigm mentioned above impacts the choice of data collection methods. Firs to fall, it is critical to focus on existing perspectives on the topic of emerging threats in aviation by analysing the current body of evidence, facts, and ideas offered by other researchers as it creates the framework for the discussion (Price, 2018). For this reason, case studies, agencies’ reports, academic articles, and relevant and credible sources are taken as a source of information vital for the project. It is considered that a literature review is a potent method that helps to structure all knowledge acquired from sources mentioned above, organise and present it for the discussion.
Secondary sources used for the paper, such as reports, and researches’ perspectives on the issue help to understand all existing concerns related to the discussed problem and incorporate them within a study with the primary goal to discuss the emerging threats from different perspectives. There is also statistical and numerical information that demonstrates the current tendencies and explains the effectiveness of methods (Bloomberg and Volpe, 2018). The choice of the sources for the project was impacted by the following criteria: credibility, relevance, and feasibility. For this reason, mainly books, scholarly articles, governmental and agencies’ reports, and reliable websites are used to collect information.
Altogether, the data collection method meets the objectives of the study. The employment of the qualitative paradigm, along with the inductive approach, helps to discuss the problem and select among the best possible recommendations and the most promising protection methods. At the same time, it creates the basis for following discussions and debates about the future of aviation, nature of emerging threats, and ways to resist them. For this reason, the methodology and data-collection approach are sufficient regarding the goals of the study and expected outcomes. They help to investigate the problem comprehensively and provide the topical attitudes to the issue of interest.
Findings
Emerging Threats, Their Organisation and Management
The information from the literature review proves the idea that today the civil aviation sphere faces multiple threats that come from different groups and individuals. Because of the growing strategic importance of the sector, it remains in the highlight and attracts the attention of diverse organisations, agencies, governments, and political forces. The fast speed, high level of comfort and security, and the ability to reach various places ensure that civil aviation is the major force that drives globalisation of the modern world. Unfortunately, this factor also becomes a source of anxiety as it means that new threats emerge as the method to destabilise the situation, cause damage, and gather the public interest. For this reason, ICAO, IATA, and other authorities outline the terrorist threat, cyber threat, human factors, drones, and insider threat as the fundamental concerns that should be addressed by using innovative security methods and approaches.
The existing body of evidence recognises several main ways of how the new dangers should be organised and managed. These include the use of revolutionary security systems with vital elements, such as the ability to adapt, multi-layered nature, intelligence-driven character, and the opportunity to remain resistant; the integration of drones as potent tools to collect information, secure the area, and prevent other UAVs’ intrusions; and the integration of innovative software into the work of existing security systems to improve them by implementing AI and machine learning. The literature states that the use of these measures can help to increase the effectiveness of existing protective measures up to 70% and make airport areas safer (Yağdereli, Gemci and Aktaş, 2015). Moreover, the use of recommended tools can also help to reduce the level of risk associated with emerging threats and help to protect all individuals involved in the functioning of civil aviation.
Unfortunately, at the moment, there are still multiple issues that should be solved. One of the factors that stimulate the appearance of new hazards is a technology that can be viewed as a two-edged sword as from one hand it increases the effectiveness of airlines by offering new methods to solve different tasks; however, from another, it equips malefactors and attackers with numerous opportunities and tools to interfere with the work of aircraft or security systems and damage them. For this reason, every new stage of the airports’ environment digitalisation, should be followed by the appropriate reconsideration of the approach to security and threats management. Only following this scheme, it is possible to remain informed about new risks and be vigilant regarding their diversification and growing complexity.
Furthermore, the comprehensive investigation of the literature demonstrates that in the future, the nature of threats will become more complex as the use of drones and specific equipment provides multiple opportunities for malefactors. The existing security systems might be effective enough in managing already known risks and hazards as they were created as a response to them and should protect civilians effectively. In the future, they might not suffice mainly due to the emerging issues discussed in the project. Under these conditions, ICAO and IATA state that there is a need for a continuously updating approach to organising and managing threats that rest on improved data collection, its processing, and creation of new ways to resist threats and recover.
Altogether, the new emerging threats give rise to multiple debates about the current security systems, their effectiveness, and what methods should dominate in the future to guarantee that passengers and specialists are protected from all possible risks. For this reason, the solutions discussed here can be viewed as universal measures that can help the sector to remain capable of detecting and preventing attacks. It is expected that in the next several years, security systems will function in a new paradigm that presupposes the use of AI, drones, and continuously learning frameworks that can remain effective in a challenging and evolving environment.
Discussion
Now we can answer the research questions formulated previously. Speaking about the first one, it is possible to conclude that civil aviation experiences is in the period of its evolution. Its safety, speed, and the ability to link different regions attract people and passengers, which guarantees its further rise. Moreover, the rise of technologies preconditions the change in the working environment and increased effectiveness of various processes. As for the prior concerns, they remain traditional and include security and passengers’ satisfaction issues. It means that to continue its evolution, the sphere has to find appropriate solutions that will be able to manage all these aspects and create the basis for future development. However, the given task can be viewed as a complex one due to the extremely changeable nature of society and the framework that impacts the work of civil aviation.
As for the second research questions, the analysed literature gives a direct answer to it. Today, the diversification of the environment and the rise of technologies contribute to the increased topicality of such traditional threats as terrorism and because of the appearance of new tools and approaches that can be used to damage airlines and aircraft. The radicalisation of various groups, their centralisation, and, at the same time, the increased destructive power of individuals precondition the increased level of risk that should be considered by security officers today. It is complicated by the growing risk of cyberattacks because of the digitalisation of processes in civil aviation and reliance on innovative software. The human factor can also be included in the list of concerns as there are still mistakes that affect outcomes and might reduce security levels. Moreover, the insider threat can also be related to human factors and might cause substantial harm to aviation because of the data leaks and its used by malefactors. Finally, drones or UAVs are another threat that is becoming more important today due to the diversification of technologies and equipment that can be used.
Answering the third research question, the risk-based approach to safety and regulation is employed today as the method to organise and manage threats today. It demonstrates the high effectiveness due to the employment of information about existing hazards and its processing with the primary goal to create a robust approach to dealing with new hazards. A risk-based approach also considers all known factor that can precondition accidents and offers a wide range of measures that can be used to minimise the possibility of a failure or disaster.
The given method can be improved by adding new strategies and means of dealing with emerging threats. Answering the fourth research question by using information from literature, it is possible to state that the shift to innovative software with AI and machine learning, along with the implementation of drones can be viewed as new methods of managing risks that appear as an effective response to them. ICAO and IATA recommend using these technologies because of AI’s ability to adapt to new conditions, collect and process data, and demonstrate better outcomes regarding different activities, such as security checks and examination of luggage. Drones are used to secure the area, improve the maintenance and overhaul procedures, collect information and prevent other UAVs from damaging aircraft. These measures are expected to demonstrate better outcomes and contribute to the creation of a new, safer environment.
The analysed literature also states that these new approaches can be sufficient enough to cope with new dangers and guarantee the demanded level of protection for passengers. The innovative methods of security checks, monitoring the area, and analysis are capable of resisting malefactors who use cyberattacks, drones, or other tools to cause substantial damage to airlines, aircraft, or people. The effectiveness of new approaches comes from their flexibility, innovativeness, and the use of relevant knowledge vital for fast reaction and recovery. At the same time, the whole sphere should remain vigilant of new threats and engage in the continuous process of updating and improving already existing security systems as it is the only guarantee of their ability to protect civil aviation.
Finally, the literature demonstrates that in the future, the number of threats will continue to grow and new, more sophisticated and diversified risks will emerge. It comes from the digital revolution we observe today and the war against terrorism. Civil aviation, because of its strategic importance, will always attract attention and suffer from multiple attacks. For this reason, in the future, the process of organising and managing threats should continue to evolve to detect new types of risks and hazards. It can be achieved by the cooperation at different levels and use of new technologies before they are employed by malefactors for their purposes.
Altogether, the literature review and data collected from various sources helps to answer all research questions formulated above. The civil aviation sphere faces a challenge today because of the diversification of threats and new ways to cause harm to people and aircraft. For this reason, new strategies are fundamental for protecting people from potential attacks and saving their lives.
Conclusion and Recommendations
In conclusion, the civil aviation sphere faces numerous challenges today. Being one of the most important means of transport, it links different parts of the world and increases the speed of cooperation and interaction. Due to its importance, it attracts the attention of radicals, terrorist groups, and individuals who want to spread panic. Under these conditions, security officers and organisations responsible for the functioning of the sphere has the main task of correctly identifying, analysing, and responding to new risks to create the safe environment and protect individuals and their lives. The complexity of this challenge is evidenced by the fact that the existing body emphasizes the need for improved measures to remain vigilant and capable of managing all new issues.
The collected information demonstrates that there are strategies aimed at the improvement of the situation. The use of drones, innovative software, AI, and risk-based security systems can drive positive change and make airlines more effective in resisting all threats. However, the level of risk remains high because of the constant emergence of new risks. For this reason, it is recommended to continue the discussion of the theme with the primary goal to remain informed about the topical issues and be ready to provide a new strategy that will help to improve the situation and increase awareness levels. The key to success is the continuous collection of data to create the framework for future disputes and the creation of effective security models.
Reference List
A risk-based approach to aviation safety regulation (no date) Web.
Arcurio, M., Nakamura, E. and Armborst, T. ‘Human factors and errors in security aviation: an ergonomic perspective’, Journal of Advanced Transportation, 2018. Web.
Argrow, B. (2016) ‘Unmanned aircraft system design’, in Marshall, D. et al. (eds) Introduction to unmanned aircraft systems. London: CRC press, pp. 159-173.
Bean, B. (2017) Mitigating insider threats in the domestic aviation system: policy options for the Transportation Security Administration. Master’s thesis. Naval Postgraduate School. Web.
Benny, D. (2016) General aviation security: aircraft, hangars, fixed-base operations, flight schools, and airports. London: CRC Press.
Billups, F. (2020) Qualitative data collection tools: design, development, and applications. 1st edn. New York, NY: Sage Publications Inc.
Bloomberg, L. and Volpe, M. (2018) Completing your qualitative dissertation: a road map from beginning to end. 4th edn. Thousand Oaks, CA: Sage Publications Inc.
Brock, J. K.-U. and von Wangenheim, F. (2019) ‘Demystifying AI: what digital transformation leaders can teach you about realistic Artificial Intelligence’, California Management Review, 61(4), pp. 110–134.
Civil Air Navigation Services Organization (CANSO) (2014) CANSO cyber security and risk assessment guide. Web.
Cole, E. and Ring, S. (2006) Insider threat: protecting the enterprise from sabotage, spying, and theft. Rockland, MA: Syngress Publishing, Inc.
Coles-Kemp, L. and Theoharidou, M. (2010) ‘Insider threat and information security management’, in Probst, C. et al. (eds) Insider threats in cybersecurity. London: Springer, pp. 45-70.
Creswell, J. (2013) Qualitative inquiry & research design: choosing among the five approaches. Thousand Oaks, CA: SAGE Publications, Inc.
Department for Transport (2018) Aviation cyber security strategy. London: Department for Transport.
Drone crashes (no date) Web.
Elias, B. (2014) Risk-based approaches to airline passenger screening. Web.
Esposito, M. et al. (2019) ‘Innovating the maintenance repair and overhaul phase through digitalization’, Aerospace, 6(53), pp. 1-14.
Hall, R. (2015) The transparent traveller: the performance and culture of airport security. Durham, NC: Duke University Press Books.
Hättenschwiler, N., Mendes, M. and Schwaninger, A. (2019) ‘Detecting bombs in X-ray images of hold baggage: 2D versus 3D imaging’, Human Factors, 61(2), pp. 305–321.
Hildebrand, J. M. (2019) ‘Consumer drones and communication on the fly’, Mobile Media & Communication, 7(3), pp. 395–411.
Hoggan, K. (2019) Will artificial intelligence improve airport security? Web.
How can AI help speed up airport security? (2019) Web.
Insurance Information Institute (III) (no date) Facts + statistics: aviation and drones. Web.
International Air Transport Association (IATA) (no date) Safety report. Web.
International Air Transport Association (IATA) (2018) Insider threat in civil aviation. Web.
International Air Transport Association (IATA) (2019) Air transport security 2040: and beyond. Web.
International Civil Aviation Organization (ICAO) (2011) Security, 9th edn. Montreal: International Civil Aviation Organization.
International Civil Aviation Organization (ICAO) (2017a) General overview: emerging security threats in the aviation industry. Web.
International Civil Aviation Organization (ICAO) (2017b) Aviation security manual, 10th edn. Montreal: International Civil Aviation Organization.
International Civil Aviation Organization (ICAO) (2018) Insider threat awareness. Web.
International Civil Aviation Organization (ICAO) (2019a) Aviation cybersecurity strategy. Web.
International Civil Aviation Organization (ICAO) (2019b) Cyber security and resilience symposium. Web.
International Civil Aviation Organization (ICAO) (2020) New PNR Data Standards amendment to improve global counter-terrorism efforts. Web.
LaFlamme, M. (2018) ‘A sky full of signal: aviation media in the age of the drone’, Media, Culture & Society, 40(5), pp. 689–706.
Lin, W. (2017) ‘Sky watching: vertical surveillance in civil aviation’, Environment and Planning D: Society and Space, 35(3), pp. 399–417.
Madan, B. B., Banik, M. and Bein, D. (2019) ‘Securing unmanned autonomous systems from cyber threats’, The Journal of Defense Modeling and Simulation, 16(2), pp. 119–136.
Marcellin, F. (2020) Good drones: the UAVs changing airport operations for the better. Web.
Maxwell, J. (2013) Qualitative research design: an interactive approach. 3rd edn. New York, NY: Sage Publications Inc.
Merens, M. and Murad, N. (2019) Becoming risk based. Lima: ICAO.
Merriam, S. and Tisd, E. (2015) Qualitative research: a guide to design and implementation. 4th edn. New York, NY: John Wiley and Sons.
Mitroff, S. R., Ericson, J. M. and Sharpe, B. (2018) ‘Predicting airport screening officers’ visual search competency with a rapid assessment’, Human Factors, 60(2), pp. 201–211.
Natale, S. and Ballatore, A. (2020) ‘Imagining the thinking machine: technological myths and the rise of artificial intelligence’, Convergence, 26(1), pp. 3–18.
National strategy for aviation security (2018) Web.
Neman, P. (2010) ‘Combatting insider threats’, in Probst, C. et al. (eds) Insider threats in cybersecurity. London: Springer, pp. 17-45.
Price, M. (2018) Current and emerging trends in the aerospace sector. Web.
Price, J and Forrest, J (2016) Practical aviation security: predicting and preventing future threats. 3rd edn. Cambridge, MA: Butterworth-Heinemann.
Probst, C. et al. (2010) ‘Aspects of insider threats’, in Probst, C. et al. (eds) Insider threats in cybersecurity. London: Springer, pp. 1-17.
Siao, D. (2017) The aviation insider threat: an assessment of vulnerabilities and countermeasures. Web.
SenseCy (2016) Cyber threats to the aviation industry – 2014. Web.
Shappell, S. et al. (2007) ‘Human error and commercial aviation accidents: an analysis using the human factors analysis and classification system’, Human Factors, 49(2), pp. 227–242.
Sheridan, T. B. (2016) ‘Human–robot interaction: status and challenges’, Human Factors, 58(4), pp. 525–532.
Stewart, M. and Mueller, J. (2017) Are we safe enough? London: Elsevier.
Stolzer, A. (2015) Safety management systems in aviation. 2nd edn. London: Routledge.
Susini, A. (2015) ‘A technocritical review of drones crash risk probabilistic consequences and its societal acceptance’, Risk Information Management, Risk Models and Applications, 7, pp. 27-38.
Swann, L. et al. (2019) ‘Airport security screener problem-solving knowledge and implications’, Human Factors.
Tiller, L. N. and Bliss, J. P. (2017) ‘Categorization of near-collision close calls reported to the aviation safety reporting system’, Proceedings of the Human Factors and Ergonomics Society Annual Meeting, 61(1), pp. 1866–1870.
Tommaso, Z., d’Amore, F. and Di Camillo, F. (2016) The defence of civilian air traffic systems from cyber threats. Web.
Tunnicliffe, A. (2020) Is it right to use artificial intelligence in aviation security? Web.
UK Civil Aviation Authority (UK CAA) (no date) Risk based surveillance. Web.
Uriondo, A., Esperon-Miguez, M. and Perinpanayagam, S. (2015) ‘The present and future of additive manufacturing in the aerospace sector: a review of important aspects’, Journal of Aerospace Engineering, 229(11), pp. 2132–2147.
U.S. Government Accountability Office (2017) Aviation safety: improved data quality and analysis capabilities are needed as FAA plans a risk-based approach to safety oversight. Scotts Valley, CA: CreateSpace Independent Publishing Platform.
West, J. P. et al. (2019) ‘Citizen support for domestic drone use and regulation’, American Politics Research, 47(1), pp. 119–151.
Yağdereli, E., Gemci, C. and Aktaş, A. Z. (2015) ‘A study on cyber-security of autonomous and unmanned vehicles’, The Journal of Defense Modeling and Simulation, 12(4), pp. 369–381.
Yin, R. (2017) Case study research and applications: design and methods. 6th edn. New York, NY: Sage Publications Inc.
Zhang, M. (2018) Drone causes aircraft crash for first time in the US: report. Web.
Zhu, H., Li, D. and Tong, Y. (2013) ‘An ontological knowledge-based system for maintenance, repair and overhaul services’, International Journal of Digital Content Technology and its Applications, 7(5), pp. 76-84.