Network Functions Virtualization (NFV) is an architectural concept that uses virtualization technologies at the network, as well as network functions level. To some extent, NFV can be considered a development of the concept of SDN (Software-Defined Networking), but it would be more correct to say that NFV uses SDN. Software-Defined Networking inside NFV can be applied at the network level both in the infrastructure and in the service consumer. The SDN controller can be integrated into the NFV management system; it can be implemented as a virtual or even hardware entity. The conceptual combination of NFV and SDN architectures at a qualitative level is described in Network Functions Virtualization (NFV) document in the Report on SDN Usage in NFV Architectural Framework of the European Telecommunications Standards Institute (ETSI).
Virtualization technologies allow creating several logical systems on a single server – isolated virtual machines with a full set of functions of physical devices. Virtualization is possible not only within the framework of one physical server, but also within the framework of several servers, data centers or even several geographically dispersed data centers of the organization. At the current level of technology development, it is possible to realize the virtualization of not only virtual machines, but also storage systems and a fully functional network, which determines the relevance of the analysis of the current state and prospects for the development and application of this technology.
Brief History of Network Virtualization Technology
The capacity and throughput of communication and data transmission networks have been growing, and the capabilities of networks were developing over a fairly long time. However, by 2019, it has become increasingly noticeable that the increase in network bandwidth is not keeping pace with the ever-faster growth in the market’s demand for bandwidth and new services, and NFV technologies represent the solution to this problem. According to the Cisco Visiual Network Index, network traffic grows exponentially with an average annual growth rate of 26% until 2022, and no further signs of a slowdown are predicted (Basile et al., 2015). This is forcing telecom operators and Internet service providers to expand their networks at an ever faster pace, while service revenue is not growing as fast as the need for bandwidth. Operators are trying to reduce the cost of network development, as well as to increase the speed of development and implementation of new functions for revenue growth.
The traditional methods of network development are relied on the “hardware” principle: “device – function.” In most cases, to enter another function, one must install the corresponding device. However, such methods of developing networks and introducing new services to the market using new physical devices face a number of restrictions: limitations of flexibility; scalability restrictions; long time to market services; administration restrictions; operating expenses; migration (the cost barrier for decisions on migration and network upgrade slows down the offer of new services to users) (Gray & Nadeau, 2016).
Conceptually, server virtualization has been used in data centers for a long; at the same time, physical servers are replaced by their virtual “copies” working on top of hypervisors. This allows, among other implications, to achieve a more efficient use of the physical resources of the data center. NFV extends the concept of virtualization beyond servers to all types of network devices. NFV can be defined as a method and technology that makes it possible to replace physical network devices with certain functions with software entities that perform the same functions on public server equipment. NFV is used as an “umbrella” term to refer to an ecosystem that consists of virtual network devices, management tools, and infrastructure that integrates software entities with standard computer hardware.
In 2012, Network Virtualization technology appeared, providing virtualization at a completely new level – the level of the network segment. In the case of server virtualization with a few caveats, the operating system (OS) inside the virtual machines (VMs) works as if it were virtualnetworks (potentially with overlapping IP addresses) installed on a physical server and was the only OS on this equipment. This abstraction allows running multiple isolated copies of virtual servers on one physical. By analogy, network virtualization leads to the fact that a virtual, or rather, in this context, virtualized network functions as if it were a physical network (Gray & Nadeau, 2016). This level of virtualization allows creating and using many virtual networks, possibly with overlapping or even completely matching IP address spaces, based on the same physical network infrastructure.
Such network infrastructure may include an arbitrary number of physical servers and network equipment. Most of the virtualization functionality can be implemented on conventional equipment without the need to purchase highly specialized hardware or network components. Today, large corporations provide network virtualization solutions, namely: VMware NSX is a network virtualization platform for software data centers; Amazon Elastic Compute Cloud (Amazon EC2) is a web service that provides scalable computing resources in the cloud; Cisco Application Centric Infrastructure (ACI) is an application-oriented infrastructure.
Theoretical Aspects of Network Virtualization
NFV represents a way of virtualizing the functions of network elements of a telecom operator. The essence of NFV is to implement the functions of managing networks and providing services programmatically, instead of using specialized equipment. Chayapathi et al. (2016) present an analogy of the differences between theater and cinema. In the theater, viewers see the “hardware implementation” of the play performed by live actors, using real scenery and a “live orchestra,” while in the movie they see the “virtualization” of the play on film, or see it in a multimedia digital file. The essence of the play does not change, and, in general, it can be said that viewers (subscribers) receive the same service as in the theater. If not to go into the aesthetic differences of various types of art, then the economic advantages of cinema over the theater are obvious – a movie ticket is cheaper than a theater one, and the cost of organizing a movie show is also much less than in case of a theater performance. Thus, hardware networking platforms are “theater,” and NFV is “cinema” (Chayapathi et al., 2016).
The Network Virtualization architecture developed by ETSI (ETSI GS NFV-0010 V0.1.7) is shown in the figure below.
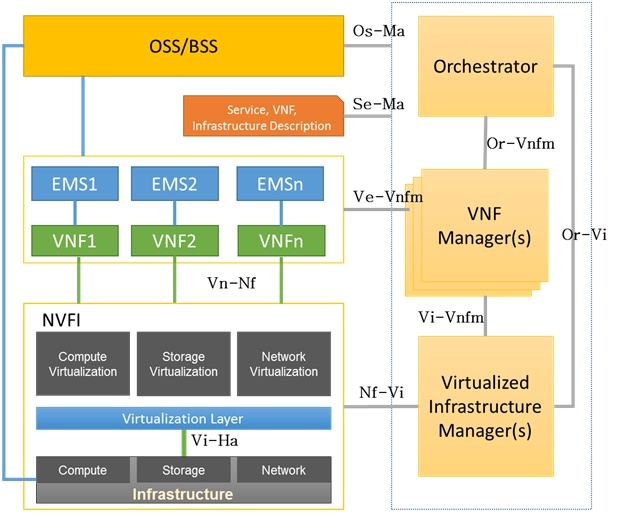
The main feature of this architecture is the possibility of so-called “Service orchestration,” i.e., allocation of virtual resources to one or another service upon request. At the same time, the most optimal use of equipment resources is achieved: servers, storage, and network. For this, the management and orchestration component MANO (Management and Orchestration), which is an essential part of the NFV concept, is provided in the NFV architecture (Pujolle, 2015).
The NFV architecture consists of three main subsystems (Pujolle, 2015):
- Virtualized Network Function (NFV)
- NFVI Virtualization Infrastructure (NFV Infrastructure)
- Management and Orchestration Subsystem MANO (Management and Orchestration)
In addition to NFVI, subsystems represent software, not hardware. NFVI includes both physical equipment (computing, storage, network) and virtual one (servers, storage systems, network devices). The level of virtualization (hypervisors and guest operating systems) makes it possible to deploy virtual machines VM on physical servers that perform any functions prescribed to them. For VM, it does not matter much on which physical server it is deployed and running. Moreover, VMs can move (migrate) from one physical server to another without interrupting their work.
Strictly speaking, it is also necessary to include the subsystem of operations and business support (OSS/BSS) in the NFV architecture, which is part of the traditional network operator communication system. However, the presence of this subsystem in the NFV architecture is temporary, because operators cannot immediately abandon existing OSS/BSS and switch to MANO (this is only possible for new networks operators starting their business from scratch and launching building a network).
The Case of Microsoft Hyper-V
In the previous sections, some theoretical aspects of NV method of combining the network resources of computers into single platforms were discussed. Nowadays it is rational to talk more about some of the nuances of network virtualization using the example of Hyper-V – a hardware virtualization tool for 64-bit systems based on a hypervisor (virtual machine monitor) – in Windows Server 2016. Sekhar and Sam (2015), describing this technology, claim that Microsoft Hyper-V network virtualization allows several virtual networks (potentially with overlapping IP addresses) to carry out their functions in the same infrastructure of physical network, so that each virtual network works like the only one single virtual network.
In Hyper-V Network Virtualization (HNV), a user or a client is defined as the “owner” of a set of IP subnets deployed in an organization. An organization or enterprise with several units in need of network isolation can act as a client. Each client can have one or several virtual subnets, and each virtual network can include several virtual subnets. A virtual network creates an isolation boundary within which virtual machines in a virtual network are able to interact with each other (Sekhar & Sam, 2015).
Each virtual network has its own unique routing domain identifier on the host. This identifier approximately corresponds to the resource identifier needed to establish contact with the RESTFUL resource of the virtual network in the network controller. To specify a reference to a virtual network RESTFUL resource, the names of the universal resource code (URI) are used, to which the identifier of this resource is added (Sekhar & Sam, 2015).
The virtual subnet is responsible for the implementation of the semantics of the third-level IP subnet for the virtual machines of the same virtual subnet. After that, this network forms a broadcast domain (similar to a virtual local area network) that provides strict isolation by using the NVGRE client identifier field or the VKSLAN network identifier. Each virtual subnet refers to one virtual network and is given a unique virtual subnet identifier (VSID), which uses a special key in the header of the encapsulated packet. It is important that the VSID meets the requirements of uniqueness and ranges from 4096 to 2^24–2 (Sekhar & Sam, 2015). The decisive advantage of routing domain and a virtual network itself is that it enables customers to use their own topologies of the network (for example, IP subnets) in the cloud.
One should also mention the architecture of the virtualization of Hyper-V networks. In Windows Server 2016, the implementation of HNVv2 is organized with the use of Virtual Filtering Platform Azure (VFP), which represents an extension of NDIS filtering on a Hyper-V switch. A key principle of VFP is that the identity processing subsystem with the internal API is provided to the SDN agent for programming network policy. The SDN node agent itself receives network policy information through the Open vSwitch Database Management Protocol (OVSDB) and Windows Communication Foundation (WCF) communication channels.
It is important to note that using VFP, not only the virtual network policy (for example, CA-PA mapping) programmed with VFP is applied, but also an additional policy such as ACL, QoS. VFP creates a layer for each type of policy (for example, a virtual network), which is an exclusive set of rule tables or flows. This policy is devoid of any built-in functions until certain rules are assigned for their implementation. Each layer receives priority, after which the levels are assigned to the port according to the increase in their priority (Gray & Nadeau, 2016). Rules are organized into groups for the most part corresponding to directions and families of IP addresses. Groups also get their priority so that one group rule matches one given stream.
To summarize, it should be emphasized that network virtualization technologies based on cloud technology can provide the company using them with many advantages, for example, improved scalability and more efficient use of resources. Realizing these potential benefits requires the use of technology that addresses the challenges of multi-client scalability in a dynamic environment. In this regard, Hyper-V network virtualization is an interesting example of solving these problems by distinguishing between the topologies of the physical and virtual networks.
Overall Implications: Benefits and Challenges
NFV helps reduce energy consumption and costs of hardware; moreover, it contributes to the improvement of operational efficiency and network configuration optimization. It should be noted also that it minimizes the costs of providers to purchase hardware, and helps reduce energy consumption, improves operational efficiency and optimizes network configuration. Virtualization enables simplification of the IT infrastructure operation, at the same time enabling increasing productivity using optimization of the resources use and providing reduction in costs for administration and maintenance.
Organization of a constantly “functioning IT infrastructure that is protected from failures and is resistant to disasters is very important. Due to a well-built virtualization environment, there is a reduction in unplanned downtime and the absolute exclusion of planned outages for servicing servers or data warehouses. At the same time, all IT services can move away from binding to a specific provider” (Chayapathi et al., 2016, pp. 66-69). For companies at any stage of the development of IT infrastructure, there is the possibility to implement process automation, one way or another connected with the computing resources allocation for diverse departments within the company, as well as for their customers.
Among the difficulties of implementing NFV, the problem of managing all virtual resources and their integration with compatibility with existing platforms should be noted. Implementation requirements have been identified in the NFV virtualization specifications (Pujolle, 2015). To ensure service availability and maintain NFV resilience, automatic failover must be enabled (Chayapathi et al., 2016). NFV can be used in many cases, such as incident management systems (IMS), virtualization of home and enterprise networks, virtualization of content delivery networks and fixed-access NFVs (Pujolle, 2015). Cloud computing and the standardization of specialized servers have contributed to the implementation of NFV.
However, main concern regarding NFVs is security. Fundamental NFV security issues include authorization and authentication of users or temporary tenants. Often, NFV security is discussed in three ways: security within VNF, security between VNF, and security outside VNF (Montero et al., 2015). At the same time, security and software management are NFV’s primary goals. Ways to solve the security problems of hypervisors, data transmission and interaction systems remain tasks of increased complexity, which must be addressed when implementing NFV in telecommunication and mobile networks.
Thus, despite the tremendous potential of NFV, security and privacy remain challenges that need to be addressed. In this context, the following tasks are distinguished: separation of services for data matrices and matrix management, prescribing rules and visualizing resources for controlling functions, management and control of the entire network. To ensure security in NFV, flexible monitoring signals must go through trusted function blocks during the setup process, such as NFV Orchestrator, VNF Managers, and Virtualized Infrastructure Manager (Montero et al., 2015). To ensure NFV security, a rather large number of security platforms and architectures are proposed and implemented:
- Policy Admin for NFV is an additional software component that allows users to define security policies using languages, top-level policies (HLP), and mid-level policies (MLP).
- The SECURED architecture ensures user safety when working with applications (Tank et al., 2019). Its main components are security module, security policy manager, authentication system and SECURED application, working together to provide security for NFV.
- OpenNF is the managing architecture for ensuring efficient and secure distribution of information flows among instances of network functions in NFV. It provides effective coordinated monitoring of both the state of all internal network functions and the status of network transmission (Tank et al., 2019). This solves the existing problem of secure control of network functions.
The main advantage of the described concept is the ability to take advantage of centralization, optimize the network with the actual network topology and its structural properties, as well as use algorithms optimized for specific services, that is, provide optimization using various software instead of parameterization. The NFV approach allowed removing some of the shortcomings, but it brought new problems. The complexity of the overall administration of hardware, hypervisor, virtual switch, virtual machines, and network functions inside virtual machines has increased significantly. Due to the complexity of the configuration of the virtual switch, its rules in most cases are set manually, which means the previous binding to the topology and the complexity of administration. In addition, virtualization technology does not imply an abstraction of the level of work with the network, so there are dependencies on equipment that supports special features to increase productivity.
On the other hand, a rapid development of cloud infrastructures offering a standardized approach to computing power management is observed. The ability to use cloud infrastructures for implementing network functions would solve the problems of virtual machines, but tools are needed to automate the deployment, operation, configurability, fault tolerance of a network function in a cloud execution model. In these conditions, the simplification, and, therefore, the cost reduction in creating network functions, while maintaining the same level of performance, including in cloud infrastructures, becomes an urgent problem.
References
Basile, C., Lioy, A., Pitscheider, C., Valenza, F., Vallini, M. (2015). A novel approach for integrating security policy enforcement with dynamic network virtualization. In: Proceedings of the 2015 1st IEEE Conference on Network Softwarization (NetSoft). IEEE, pp. 1-5.
Chayapathi, R., Hassan, S., & Shah, P. (2016). Network functions virtualization (NFV) with a touch of SDN. Addison-Wesley Professional.
Gray, K., & Nadeau, T. D. (2016). Network function virtualization. Morgan Kaufmann.
Montero, D., Yannuzzi, M., Shaw, A., Jacquin, L., Pastor, A., …, Bosco, F. (2015). Virtualized security at the network edge: A user–centric approach. IEEE Communications Magazine, 53(4), 176-186.
Pujolle, G. (2015). Software networks: Virtualization, SDN, 5G and security. Wiley-ISTE.
Sekhar, A. C., & Sam, P. (2015). Microsoft Hyper-V network virtualization. International Research Journal of Engineering and Technology, 02(03), 191-193.
Tank, D., Aggarwal, A., & Chaubey, N. (2019). Virtualization vulnerabilities, security issues, and solutions: A critical study and comparison. International Journal of Information Technology, Web.