TCP/IP Protocol Suite covers a whole family of protocols, application programs, and a network. The architecture of these protocols is necessary for an integrated network, which consists of connected separate heterogeneous packet subnets. They are connected to each other via gateways. Heterogeneous machines are connected to each of the subnets, and each of them operates according to specific requirements and means of communication. However, all subnets can receive data with the appropriate network header and deliver it to the required address (Mundra & El Taeib, 2015).
It is crucial that there is no need for a subnet to have a reliable end-to-end protocol; therefore, two machines on the same network can exchange packets. In an actual business, this Protocol Suite is utilized to ensure communication between computers that belong to one network. Notably, they function within local area network. It is implemented through architecture, the levels of which are “application layer, transport layer, network layer, and data link layer” (Gangane & Kakade, 2015, p. 3713). The purpose of this paper is to characterize these layers in terms of the communication flow between organizational levels.
Application Layer
It is the upper layer of the system, and it contains applications that are needed for the lower layer protocols. With the help of those, data can be delivered to the ultimate destination machines (Mundra & El Taeib, 2015). Every layer has certain functions to be able to perform the required tasks. In an actual business, this layer ensures standard Internet services, which any individual can utilize.
The protocols of this level include such options as FTP (copying files), SMTP (mail protocol), WWW (hypertext service for accessing remote information), and other functions. FTP protocol implements the possibility of remote access to the file. In addition, the user has an opportunity to interact with remote computers, for instance, to print the contents of directories (Mundra & El Taeib, 2015). This protocol also performs authentication since the user needs to enter a password and a login so that the files can be accessed.
Transport Layer
At this layer, two protocols can function, which are the transmission control protocol and the user datagram protocol. The first one provides a stable viral connection between remote application processes. The second protocol provides a similar transfer by the datagram method. This method assumes less overhead since it does not require a virtual connection (Mundra & El Taeib, 2015). Nevertheless, user datagram protocol (UDP) does not perform any additional functions. In actual business, it can be used to send short messages. The user data that comes from the first layer is checked, and the package that has been generated at this layer is sent to the next level.
Notably, the information of this layer should not be lost. When the acknowledgments are not obtained, the packets will be transmitted again. UDP is less reliable; therefore, it is utilized when no extra protection measures are required when sending data. In addition, this protocol does not ensure that the information will be accepted by the host (Gangane & Kakade, 2015). Despite the fact that the data can be lost, it will not interrupt the completion of the task. This pattern can occur in an actual hierarchical business. For instance, if someone attempts to download a video from local area network, some bytes can be lost. Nevertheless, it will not affect the user experience.
Network Layer
The third layer is the level of interaction between networks. It transmits datagrams through local networks, special communication lines and so on. The stack utilizes IP (Internet Protocol) as the main network layer protocol. Its purpose is to move the data by routing it. It is done over the whole network. Other examples include IGMP (Internet Group Management Protocol) and ICMP (Internet Control Message Protocol) (Anand Kumar & Karthikeyan, 2013). The example of its use in an actual business can be linked to the provision of information to the correct host. The layer ensures that sending files or anything else proceeds to the correct destination. This layer also ensures safety of information delivery.
Data Link Layer
The fourth layer is responsible for communication details. An example of it can be the networking between machines that occurs through client server architecture. In this situation, the communication can proceed over local area network. The functions of this level include mapping of IP-addresses into physical network addresses and encapsulation of IP-datagrams in frames (Gangane & Kakade, 2015). In addition, the tasks of this layer are definition of the medium access method, presentation of data to the physical environment, and sending and receiving of the frame.
Concluding Points
Thus, in hierarchical businesses, the server handles the performed requests. At that time, computer users actively interact (Anand Kumar & Karthikeyan, 2013). The Communication Flow Diagram (Figure 1) exhibits the four layers vividly.
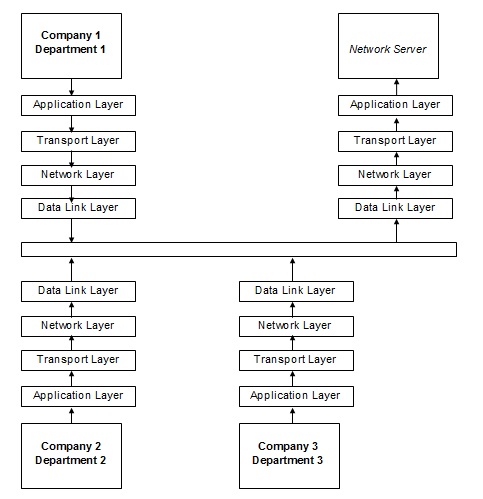
It shows that the corporate network is a complex system, and the main task of networks is that the system should efficiently process information flows and obtain correct solutions for user tasks.
References
Anand Kumar, M., & Karthikeyan, S. (2013). An enhanced security for TCP/IP protocol suite. International Journal of Computer Science and Mobile Computing, 2(11), 331-338.
Gangane, S., & Kakade, V. (2015). Base of the networking protocol – TCP/IP its design and security aspects. International Journal of Innovative Research in Computer and Communication Engineering, 3(4), 3712-3718.
Mundra, S., & El Taeib, T. (2015). TCP/IP protocol layering. International Journal of Computer Science and Information Technology Research, 3(1), 415-417.