Summary
Temperton Accounting Firm was interested in upgrading Exchange 2010 environment to Exchange 2016 environment to help address challenges that had been identified in the system. The firm handed over the upgrade project to Bytes to Bits Computer Consulting because of its reputation as one of the firms that understand the changing trends in digital data management in the country. The management of Temperton Accounting Firm wanted the upgrade to be completed within the shortest period possible to ensure that its operations would not be affected. The consulting firm came up with a proposal of how the project was to be implemented, the resources required, and the time within which it would be completed. The proposal was discussed with the client and approval was given.
Immediately after getting the approval, Bytes to Bits Computing Consulting embarked on the implementation of the proposed plan. It took the firm a shorter period than what was proposed to complete all the activities. They managed to upgrade the firm’s data management system from Exchange 2010 to Exchange 2016 environment. Although the project was completed earlier than was expected, the team did not compromise on quality. The system met the expectations and currently, Temperton Accounting Firm is focusing on employees’ training to ensure that they have the technical knowledge to operate using the Exchange 2016 environment. The paper focuses on a detailed discussion of the outcome of the project.
Review of Other Works
The emerging technologies have made it necessary for firms to move from traditional ways of managing information using physical files to the use of digital data. Digital data simplifies the process of acquiring, processing, storing, retrieving, and sharing information in a given organization (Marous, 2018). Exchange 2016 environment has become popular because of its improved storage capacity, security features, and the ease with which people can share information. Temperton Accounting Firm has successfully upgraded its system from Exchange 2010 to Exchange 2016 environment as a way of improving operational efficiency. However, not all stakeholders believe the move was necessary. It is important to look at case studies, research studies, or the industry’s best practices to understand the relevance of this new system that the company has introduced. The following reviews support the actual development of this project.
Microsoft Exchange in University of Pennsylvania Case Study
The University of Pennsylvania is one of the institutions of higher learning in the country, which are focused on digitizing its data management system. According to Zimbra Community (2010), the student population at the institution has been growing steadily over the years, which means that the firm also has to consider hiring more employees in different departments. Managing data through the traditional method of physical files was becoming less effective. The finance department was the first to identify the major weaknesses of the traditional design when managing various portfolios, especially students’ financial records. The human resource management unit at the institution also felt that it was increasingly becoming frustrating to use the traditional methods. It would force the firm to hire more employees. As such, the management decided to digitize its data management system. The firm introduced the Exchange 2007 environment platform to enhance the system.
In 2010, the management of this institution decided to upgrade the system to Exchange 2010 as a way of meeting new demands. The main problem with the previous system at the University of Pennsylvania was that security features could easily be compromised. The 2010 Exchange environment was intended to enable departments to share data automatically without having to attach files and send them to other departments in the form of e-mails. It meant that if the academic affairs wanted access to the financial information of the student, the authorized officer would only need to visit the right database and get the information instead of the long process of contacting the finance department and waiting for them to relay the information. The new system was also more dynamic than the previous one. Currently, the institution still uses this system in managing its data. Although it has also embraced the use of Zimbra, which offers the same system, the fact that the management of the institution opted to retain the Exchange 2016 environment shows that it is trusted to offer the desired quality.
Paul Cunningham’s Implementation Guide to Migrating to Exchange Server 2016
In this article, Cunningham (2016) explains the migration process, from Exchange 2010 or 2013 to Exchange 2016. The author uses a hypothetical scenario of Not Real University as the institution that is involved in the migration/upgrade process. Currently, the institution is using both Exchange 2010 and 2013 to support its operations (Cunningham, 2016). The initial intention was to upgrade the system from Exchange 2010 to Exchange 2013 environment. However, the technical challenges that the institution faced made it difficult to complete the full migration. As such, the management decided to drop Exchange 2013 and upgrade directly to the more secure and more reliable Exchange 2016 environment.
According to Cunningham (2016), one of the first steps that should be made during the migration process is to conduct a review of the existing environment. The review will help in obtaining the information needed to have an effective plan for the migration. The process helps in determining the current capacity of the system, major weaknesses, and issues that should be addressed to achieve the desired goals. In the case provided, it was established that Not Real University had an Exchange 2010 SP3 UR14 server that hosted a database for 78 mailboxes, Exchange 2013 CU13 server hosting another database for 33 mailboxes, and Exchange 2013 CU13 Edge Transport server that facilitates the outbound-inbound flow of emails (Cunningham, 2016).
The review went ahead to analyze the current needs of the institution and identified various inadequacies with the new system, especially based on the increasing demand. As such, a decision was made to introduce the more advanced Exchange 2016 server that could support the increased data at the institution. The goal of the team was to decommission the two previous servers (Exchange 2010 and Exchange 2013) and instead have Exchange 2016 as the primary server. The management was convinced that the new system would meet the new demand. The issue of improved security was another major motivation for migration. The report shows that the management of Not Real University was convinced that the new version of the server was more secure than the previous server. Figure 1 below shows the migration process.
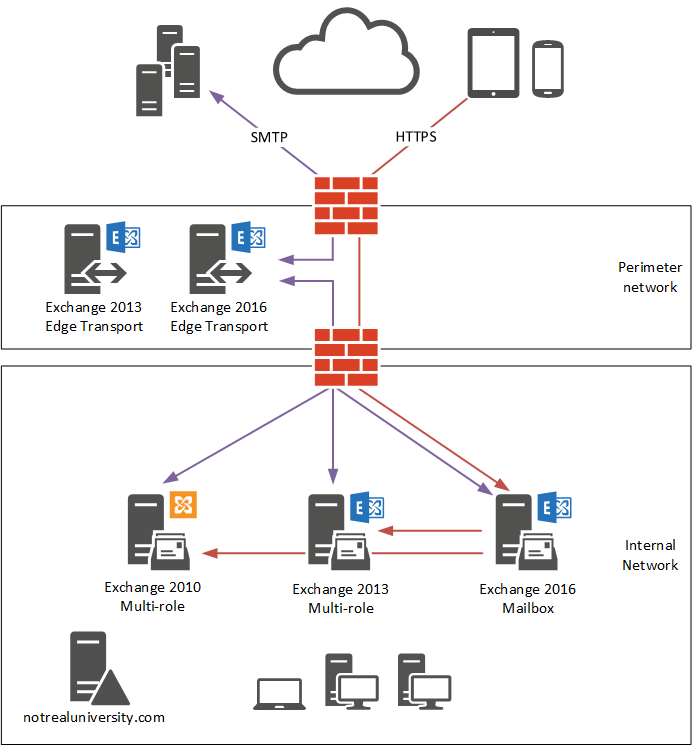
Swap Up to Microsoft Exchange 2016: 5 Threats to Your Email Server
In this article, Adams (2018) focused on explaining specific reasons why an institution needs to swap up from the older versions of Microsoft Exchange servers to the new Exchange 2016 environment. In the digital data management world, it is crucial to remain relevant and up to date. Sometimes a firm may be satisfied with the older versions because it meets the current needs and eliminates the cost of upgrading. However, the problem arises when it comes to security. As cybercriminals become sophisticated, providers of these systems such as Microsoft often try to come up with a tight security measure in their upgraded systems. Failing to upgrade would mean remaining with a server that is vulnerable to possible attacks. Adams (2018) explains that when cybercriminals have access to the database of a firm, they can steal sensitive information, manipulate the data, or even wipe out the entire database, crippling the operations of a firm. The article identified specific threats to email servers for firms that fail to swap up to Microsoft Exchange 2016 environment.
The Exchange 2010 environment has a weak password. In this server, a hacker can easily download emails of different users and their respective passwords through the phishing process. It is also possible for them to guess the passwords once they have the email address of the intended victim. The system does not report such intrusions and the hacker has the opportunity to make several guesses of the password. Two-factor authentication is one of the best ways of protecting data in an environment where cybercriminals are often keen on breaching security measures. It created an environment where one has to use a code sent automatically to their phones once they enter the correct password to their email or when trying to access the database. The 2016 Exchange environment has this important security feature that the previous versions lack. The new server also makes it possible for employees of a firm to have access to the database via encryption without falling victim to what Adams (2018) refers to as a man-in-the-middle attack.
Data leakage is another major concern when using Exchange 2010 environment. According to Adams (2018), leakage can happen in various ways. One of the common ways of data leakage is through phishing. Others use malware to have access to data. They would send a file to an unsuspecting user and when it is opened, the criminal would have access to critical information of the victim almost instantly. Another common way of data leakage is by gaining physical access to the email server (Adams, 2018). One of the easiest ways of gaining such physical access is through stolen or lost phones. If they get the password, it would be easy for these cybercriminals to access any information they desire in the database.
Denial-of-service (DoS) is another common problem with the older servers, especially the Exchange 2010 and previous versions. In this case, an attacker would flood servers with heavy traffic, making it difficult for users to have access to the information they need and ruining its reliability (Adams, 2018). In most cases, the server would crash when the traffic is too heavy to bear. The goal of such an attacker is not to steal important data from the victim but to compromise on their ability to operate. When the system is flooded with junk information, it becomes almost impossible for employees to have access to the information they need. It forces them to suspend their operations for a while, a move that may have a devastating impact on the ability of a company to meet customers’ needs. They are some of the reasons that make it necessary for a firm to swap up to the more secure and reliable Exchange 2016 environment.
Changes to Project Environment
In this project, Bytes to Bits Computer Consulting had to take specific steps to ensure that Temperton Accounting Firm’s servers were upgraded from the Exchange 2010 environment to Exchange 2016 environment. As Rathnam (2016) notes, when making an upgrade, specific steps have to be followed to ensure that the migration is a success. In this section, the focus is to discuss the steps and milestones during the implementation process.
Architecture
The analysis of the Exchange 2010 at Temperton Accounting Firm revealed the Mailbox, Unified Messaging, Hub Transport, and Client Access were separate components responsible for different roles in the server (Avelar, 2015). In such an environment, it was not easy to integrate different activities done by various employees of the firm. It also slowed the ability to share data among different stakeholders at this accounting firm. As such, one of the first steps taken during the upgrade was to integrate these different components into a unit. The architecture of the new system combined the Mailbox, Hub Transport, Client Access, and Unified Messaging into a single component known as Mailbox to improve speed and efficiency (Stanek, 2016).
Exchange Admin Center
The Exchange admin center (EAC) was another area where a major upgrade was made when changing the system from Exchange 2010 to Exchange 2016 environment, like Tan, Maynard, Yao, and Cung (2016) recommend. EAC makes it possible for users to have access to the database of the company from anywhere as long as they can use a web browser. It facilitates on-premise, online, and hybrid Exchange deployment (Janakiram, 2016). This major change in the system was intended to make data collected by accountants in the field accessible to other officers at the premises of Temperton Accounting Firm in real-time. It also meant that those accountants in the field could have access to the database to retrieve the information they need to facilitate their operations. The improved data sharing system was critical in improving the overall performance of the company.
Hybrid Configuration Wizard
Hybrid Configuration Wizard that comes with Exchange 2016 did not exist in the previous Exchange 2010 version. According to Tan et al. (2016), this tool provides a method through which administrators can configure hybrid deployments. The wizard is the aspect of the new server that integrates the on-premise Exchange Online setups to support the deployment (Marous, 2018). It also includes the Edge Transport server to enhance sharing of data among different users who have access to the database irrespective of their physical location (Leonard, Svidergol, Wright, & Meloski, 2016). It facilitates the security of the emails shared in the server, facilitates online archiving of data, and improves the organization of emails in the archives. The HCW also makes it possible for two or more users to have access to the same information simultaneously when it is necessary. Its new function known as MailTips provides informative messages when end-users are composing their messages.
MAPI over HTTP
The Messaging Application Programming Interface (MAPI) over Hypertext Transfer Protocol (HTTP) was another major area of improvement during the upgrade from the 2010 to 2016 Exchange environment, as Avelar (2015) suggests. In the previous server, HTTP protocol was used to facilitate messaging among the users of the database. However, it was replaced by the more versatile MAPI, also known as Outlook Anywhere, which is capable of connecting clients to Exchange Online and Microsoft Exchange (SenGupta, 2017). MAPI is simpler to use than HTTP and it eliminates the need to have two long-term TPC connections for each of the Exchange and Outlook connections (Tan et al., 2016). The authors note that activities that could not be done in Exchange 2010, such as pausing connections, changing networks, and resuming hibernations, were enabled under the new system. It is important to note that MAPI over HTTP that was introduced does not prohibit clients of this system from using other protocols. It means that if an individual finds the new outlook complicated or less desirable, they can switch to RPC (Remote Procedure Call) over HTTP. The security of the data will not be compromised in such cases.
Update the Existing Environment
After the initial preparations discussed above, it was time to update the existing environment in readiness for the new system. The team opened the Exchange Management Shell and ran this command, Get-ExchangeServer: Format-List Name, Edition, AdminDisplayVersion, as Janakiram (2016) suggests. It indicated that the current version was the Exchange 2010 environment. The team then installed Exchange 2010 SP 3 and Exchange 2010 SP3 Update Rollup 11 (Tan et al., 2016). These are basic preparations, which make it easy to upgrade the system from 2010 to higher versions. Avelar (2015) also emphasizes the need to update clients, which in this case were individuals within Temperton Accounting Firm, to a minimum of Exchange 2016 Support Outlook 2010 before starting the migration process. The team involved in the upgrade of the system ensured that they met that requirement.
Preparation of the System for Exchange Server 2016
When the update was completed, the team focused on preparing the system in readiness for the introduction of the Exchange 2016 server. The team ensured that the system was operating under Windows 2012 R2, a RAM of 32GB, and that the Mailbox server role had a capacity of 12GB with an additional 4GB for edge transport, as Tan et al. (2016) advises. The Disk space was set at 80GB with an additional 500MB for each of the Unified Messaging language packs (Rathnam, 2016). The team ensured that the resolution of the screen was set at 1024×768 pixels and NTFS (New Technology File System) was used to format disk partitions. The team then went ahead and installed an active directory for Exchange 2016, as Stanek (2016) suggests. The step was completed by simply running the Exchange 2016 setup, following the prompts at every stage.
Installation of Exchange 2016
The final stage was the actual installation of the Exchange 2016. At this time, an appropriate environment had been set up for the new server at Temperton Accounting Firm. The migration process was simple because the configuration wizard undertakes most of the responsibilities when the environment is set appropriately (Tan et al., 2016). The team only had to run the Setup.axe file to start the installation of the new system. The team only needed to select the Mailbox role upon receiving the prompt when the installation started. It took a few minutes and simple selection clicks for the setup process to be complete. After clicking the Finish button, a new Exchange Admin Center was loaded on the browser, and the migration was complete. Figure 2 below shows the 2016 Exchange admin center.
Methodology
The researcher used the methodology that was specified in the proposal. Avelar (2015) explains that it is always critical to follow the approach that has been approved by a client when undertaking a major project. Temperton Accounting Firm had approved the steps proposed in completing the project. The most appropriate method that was chosen was PDCA (plan-do-check-act). PDCA is a simple method of implementing a project that identifies specific steps that should be followed to achieve the desired outcome. The first step when using this approach was to conduct a plan by identifying the existing weaknesses of Exchange 2010 and the root cause of the problem at Temperton Accounting Firm when it comes to data management. The planning process also involved defining what was to be done to address the identified problem. The consulting firm was able to determine that the Exchange 2010 environment that was in use at the company needed an upgrade. It was becoming difficult for workers to share data and security was a major cause of concern. The second step (Do) involved fixing the identified problem. The consulting firm upgraded the previous server to Exchange 2016 environment to meet the company’s needs.
The detailed process that the consulting firm took to upgrade the server from Exchange 2010 to Exchange 2016 has been explained in the previous section. The methodology that was chosen states that the third step should involve checking if the problem is fixed based on the specifications of the client. The management of Temperton had identified major weaknesses of the previous system that included compromised data security, the complexity of sharing information, and slowed operations. This stage involved determining if these weaknesses were addressed when the new system was operational. The final step was to act upon or adjust the system based on the outcome of the assessment.
The process involved fine-tuning the new system to meet the specific needs of the company in the best way possible. The previous analysis had revealed that Microsoft Exchange 2016 is used in different industries and by different firms. However, it is often necessary to fine-tune it based on specified needs and expectations of a given company (Stanek, 2016). As such, before handing over the project to the client, the consulting team ensured that the client was satisfied with what it offered. The team also took time to train the firm’s employees on how to use the new system. It was evident that a significant number of these workers did not understand how to operate in the new environment. For instance, most of them were used to attaching files to emails upon completing the process of data collection. They had to learn how to input their data directly to the database under the new system.
Project Goals and Objectives
When undertaking a given project, Avelar (2015) explains that it is necessary to have specific goals and objectives that should be realized. As such, the team has developed a set of goals that had to be achieved by the end of the project. As explained above, the speedy implementation of the new system and the fact that the Microsoft Exchange 2010 worked as was expected pleased the client. During the testing process before the project was finally handed over, the system worked well and it was evident that the client was assured that the investment made was worth its value. Table 1 below identifies specific goals and objectives that had to be achieved. Each of the objectives had various deliverables, stating what was specifically expected out of the project. It was necessary to determine if the deliverables were achieved.
Table 1: Goals, Objectives, and Deliverables.
According to Rathnam (2016), when setting up project deliverables, it is important to remain realistic and avoid making promises that cannot be achieved based on the outcome expected. In this case, the team of consultants had to define goals and objectives based on the known capacity of Exchange 2016. The team had implemented the system in other firms before undertaking this project. As such, the individuals involved are aware of the system’s capacity. During the planning stage, the deliverables were set based on the expected output. As shown in the table above, the deliverables were achieved in the project. It was a further confirmation that the project was implemented successfully at Temperton Accounting Firm.
Project Timeline
When developing the proposal, the team had anticipated numerous challenges in the implementation process because most of the employees did not understand the Microsoft Exchange 2016 environment. The team expected that the management would have to consult employees and other stakeholders, discuss the possible outcome of the project, before making the approval. Avelar (2015) explains that when introducing a new system, it is often prudent to consult all the relevant stakeholders, especially the employees who would be directly affected by the new system. As such, the team had anticipated that the project would start in mid-June.
The team approved the proposal a day after it was presented. However, they had one major request to the consulting firm that was assigned the role of upgrading the server from Exchange 2010 to Exchange 2016 environment about time. They wanted the project completed in less than one week, and that explained the reason why they approved the proposal almost immediately. The management noted that the firm had several tasks for its clients that it had to complete within the next three months. As such, they could not afford prolonged interruptions with its servers. The work started immediately after the approval because the management provided the needed resources almost immediately. Table 1 below shows the timeline of the activities.
The new request
Table 2: Project timeline.
Unanticipated Requirements
During the proposal development phase, the scope of the project was defined in clear terms, explaining the requirements that had to be met upon completion of all the activities involved. At the project approval stage, Bytes to Bits Computer Consulting had to reaffirm the expectations to ensure that the client understood what was to be delivered. The client, Temperton Accounting Firm, just had one main unanticipated requirement. The client wanted a system that would enable the management to know if its employees were using their privilege to access the database to share sensitive information with other parties. As Avelar (2015) observes, such rogue employees who are willing to sell the company’s critical information exist. The consulting company explained to the client that it was not easy to determine whether an employee was misusing such privileges. The only time that such information would be made public is when the third parties act upon the information wrongly acquired. However, the team had to find a way of managing this unanticipated request.
The consulting firm provided different strategies through which the client could address the concern. One of the ways that the consultant offered was limited access to data by junior employees, especially those who are yet to gain the trust of the management. The strategy would ensure that employees could only access the data they needed to facilitate their normal operation. Every time they needed information classified as sensitive, they would have to get the permission of a specific superior officer who will assess the relevance before authorizing access. The strategy meant that these employees could not be hired by other companies to help them infiltrate the accounting firm’s database. The consultant also created a system where specific people would be responsible for handling specific aspects of the database. This strategy was important in ensuring that in cases of a breach, it would be possible to identify specific individuals who could have been involved in the process. Marous (2018) argues that such a system also improves a sense of responsibility. Employees would know that in case they engage in fraud, they can easily be traced based on their digital footprint and be subjected to the necessary punishment, including a possible jail term if that may be necessary.
As shown in the timeline above, another unanticipated request made by the management was the need to complete the project within a short period. In the proposed plan, it was expected that the entire project would take approximately two months. The process of consultation and the need to engage employees of the firm closely during the process of upgrading the server was expected to take more time. However, the management took only one day to approve the proposal and made available all the resources needed for the project. The firm then requested that the project should be completed in less than one week. The timeline was readjusted significantly to meet the new requirement. The team managed to complete the project in exactly seven days.
Conclusion
When Bytes to Bits Consulting completed the project and handed it over to the client, Temperton Accounting Firm, of interest was to ensure that expectations would be met. The migration from Exchange 2010 to Exchange 2016 was completed earlier than was scheduled because of the quick approval of the proposal and the effort put in by the employees of the consulting firm. The client had requested that the migration should be completed within the shortest time possible to allow the accounting firm to continue with its normal operations. The result of the project was an improved data management system that was secure, dynamic, and capable of meeting the emerging needs of the firm. It was evident that the client was satisfied with the system as it exceeded its expectations. It is important to discuss the specific effects of the completed project on the firm.
One of the main effects of the project on Temperton Accounting Firm was improved sharing of data. As had been promised during the proposal development stage, the new server made it possible for employees of this firm to share data in real-time irrespective of their location, as long as they were connected to the browser. They did not have to attach their files each time they were sending messages to the headquarters. Instead, the information they were feeding into their devices would be reflected on the server instantaneously. Most of the employees were pleased with this new application and so was the management. The capacity for sharing data remotely was considered critical in this accounting firm to enhance credibility. Any changes made in the files after being created would be easy to trace, making it difficult for the accountants to modify data.
Security was another factor that had a positive effect on the firm after introducing Exchange 2016 at Temperton Accounting Firm. The management of this accounting firm noted that security was a major concern. It had experienced cases where its database would be hacked and information adjusted without the knowledge of the management when it was operating under the Exchange 2010. When the migration was complete, the company hired known professional hackers to try and have unauthorized access to the system. These hackers attempted to have access to the database with no success. It was an assurance that it would not be easy for cybercriminals to have access to information in this system. During the first week of operation under the new system, the management noted that the system had identified several attacks on the firm’s database but they were unable to have access to the information they needed. The two-factor authentication system was also a new security feature introduced that improved security.
The project was a success based on criteria that were set in the aim and objectives set during the proposal stage. One of the main goals that had to be realized through this project was the improved speed at which users could share information. The Microsoft Exchange 2016 that was installed at this accounting firm helped realize this goal. The database had a larger RAM, which meant that activities such as data storage, processing, retrieval, and sharing could be done at a greater speed. The client also wanted to have an improved storage capacity because of the increasing number of clients.
The goal was realized through the new system. Ease of sharing files among different departments and employees in the office and those in the field was another objective that was achieved as discussed in the paper. Finally, security was a major goal that this project had to achieve. Credibility is a factor that defines the ability of this client, as an accounting firm, to achieve success in the market. The firm can face litigation if it is established that it has provided misleading data to its clients. The new server system introduced several security measures that made it difficult for unauthorized individuals to have access to the database. The client was satisfied with the overall outcome of the project and the speed with which activities were conducted.
References
Adams, J. (2018). This week: Swap up to Microsoft Exchange 2016. CBT Nuggets. Web.
Avelar, V. (2015). Practical options for deploying small server rooms and micro data centers. White Paper, 174(1), 1-11.
Cunningham, P. (2016). Migrating to exchange server 2016. Practical 365.
Janakiram, M.S. (2016). Why enterprises should care about serverless computing. Forbes Magazine.
Leonard, C., Svidergol, B., Wright, B., & Meloski, V. (2016). Mastering Microsoft Exchange Server 2016. John Wiley & Sons.
Marous, J. (2018). Chase commits to long-term ‘digital everything’ strategy. The Financial Brand.
Rathnam, L. (2016). How to migrate from Microsoft Exchange 2010 to Exchange 2016. TechGenix.
SenGupta, A. K. (2017). Ion exchange: Environmental processes. Hoboken, NJ, Wiley.
Stanek, W. R. (2016). Exchange server 2016 & exchange online: Essentials for administration. East Olympia, WA: Stanek & Associates.
Tan, S., Maynard, D., Yao, R., & Cung, D. (2016). Force upgrade of a mobile application via a server side configuration file. Foreign Patent Documents, 61(697), 1-26.
Zimbra Community. (2010). Zimbra TCO bests Microsoft Exchange in University of Pennsylvania: Case study. Zimbra.