Proposal Overview
The Exchange 2016 environment has introduced new features in its new architecture that includes a hybrid configuration wizard (HCW), a cloud-based configuration, and its improved troubleshooting and diagnostics make it the most appropriate application in the modern society (Leonard, Svidergol, Wright, & Meloski, 2016). Firms that were previously using the Exchange 2010 environment would find the new environment more effective in enhancing internal operations. The Exchange 2016 uses MAPI instead of HTTP as its default protocol, which makes it more reliable than the Exchange 2010. According to SenGupta (2017), in the current competitive business environment, firms must be keen on embracing emerging technologies as a way of improving their operations. In this project, the focus is to upgrade Exchange 2010 environment to Exchange 2016 environment at Temperton Accounting Firm. The project will be undertaken by Bytes to Bits Computer Consulting.
Problem Summary
Temperton Accounting Firm is one of the leading providers of financial solutions in the country. The nature of business and the environment within which this company operates require it to have a platform that allows users to access their emails and share relevant information using any computer as long as it has access to the internet (Stanek, 2017). As an accounting firm, sometimes its officers have to work away from company offices, especially when auditing accounts of clients around the country. These employees would need a system that can enable them to have access to the company database so that they can send data collected for further analysis. The analysis of the company’s system shows that it is currently using the Exchange 2010 environment instead of the modern Exchange 2016 environment. The current system has 2 client access servers, which also have the hub transport role. It is evident that the system has 3 mailbox servers with a database availability group (DAG), unified mailbox databases, and around 1050 mailboxes.
The clientele base of Temperton Accounting Firm is growing, which means that the current limited Exchange 2010 environment is becoming less effective in its operations. The current system uses HTTP as its default protocol, which is less reliable when handling large data. Users of the current system have also explained that in 2010, they have to install a certificate for each server through EMC (Rathnam, 2016). They also complained that they could not see the details of expiry in EAC, which sometimes causes inconveniences. Although the current system is a major improvement to the previous 2007 platform, users feel that it is no longer effective in meeting their needs. The project will not include upgrading of the accounting software at this company as the focus is primarily on upgrading the Exchange 2010 environment to Exchange 2016 environment.
IT Solution
Bytes to Bits Computer Consulting, as the firm contracted to improve the system, has proposed the most appropriate solution to the challenges identified at this firm. The introduction of Exchange 2016 environment will address issues that employees of this firm have identified in the current platform. The architecture of the new system combines the Mailbox, Hub Transport, Client Access, and Unified Messaging into a single component known as Mailbox, unlike the case before when they were separate components (Rathnam, 2016). The Exchange Admin Center in the new system allows users to connect to the database from any location as long as they use a web browser (Stanek, 2017). The new system has a cloud-based application, the HCW, which connects it with various Microsoft applications such as Office in real-time.
When using this new system, one can easily diagnose any problem and find online solutions, unlike the previous system. It means that the new system will not be as demanding to the employees, in terms of technical skills expected of them, as the previous system. Its simplicity and ease of operation mean that the company will not spend a lot of resources and time on training these employees. Another problem that was outlined in the current platform is that one has to install the certificate for each server through the Exchange Management Console (Stanek, 2017). The Exchange 2016 environment solves this problem as one can install certificates in multiple servers at a time using the EAC. Users can also see the details about expiry in EAC (Stanek, 2016). The new system is expected to improve the productivity of employees at this firm.
Implementation Plan
In this project, Bytes to Bits Computer Consulting will help Temperton Accounting Firm to migrate from the Exchange 2010 environment to Exchange 2016 environment. The project will be implemented in phases. The first phase will be to update the current Exchange 2010 environment in preparation for the upgrade. The process involves installing Exchange 2010 SP3 Update Rollup 11 and Exchange 2010 Service Park 3 (Rathnam, 2016). Figure 1 below shows the procedure that should be taken to conduct the update.
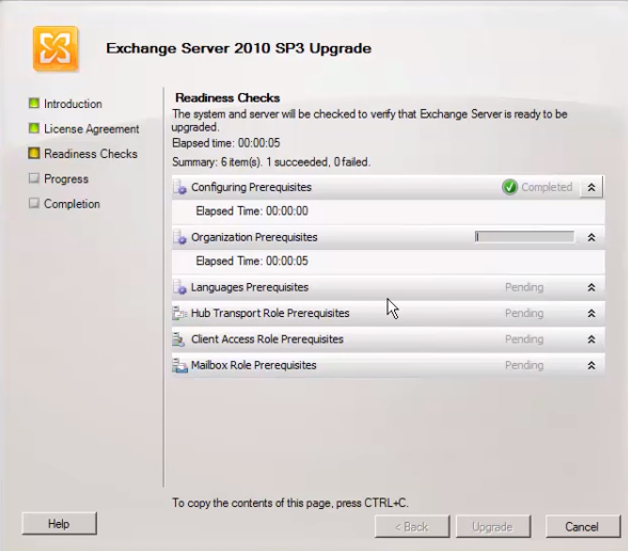
The next phase is the preparation of the system for the Exchange server 2016 (Rathnam, 2016). Various conditions must be met at this stage. It should have Windows server 2012, the Mailbox server role memory should be at least 8 GB in addition to another 4GB for edge transport, with a RAM OF 10-32788 MB (Rathnam, 2016). The disk space should have a minimum capacity of 30GB, with an addition of 500 MB for UM (Unified Messaging) language pack, and a 1024×768 pixels screen resolution. When these and other conditions are met, the team will need to prepare the schema update (Rathnam, 2016). The third phase is the installation of the Active Directory for Exchange 2016, by running the Exchange 2016 setup (Stanek, 2017). Figure 2 below shows how this phase should be conducted as the environment is changed from 2010 to 2016.
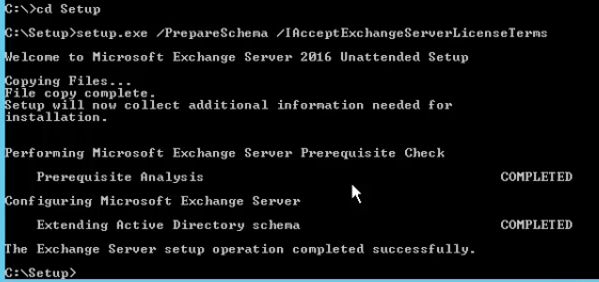
The next phase is the installation of the Exchange 2016. The configuration wizard will undertake most of the activities and one only needs to follow the prompts provided by the system. Once that step is completed, one needs to conduct other configurations under the new 2016 environment such as updating Service Connection Point, updating Outlook Anywhere settings, and configuration of the Receive Connector that would facilitate the relay of email applications (Rathnam, 2016). The final phase will be to test the configuration to determine if it works as per the expectations. The detailed plan about will be carried out in the suggested manner above because it is the standard procedure of upgrading the Exchange 2010 environment to Exchange 2016 environment.
Review of Other Work
In this section, the focus is to review similar upgrade projects that have been conducted in other institutions over the recent past that are related to this project. The review would help guide this project to ensure that desired goals are realized. Practical Options for Deploying Small Server Rooms and Micro Data Centers is one such project (Avelar, 2015). The White Paper describes serious challenges that a small food distributing company was facing in managing data. The interview with the manager of the company revealed that the small server rooms used at the branches of this firm were insecure, unmonitored, unorganized, and space constrained (Avelar, 2015). These challenges led to system downtime, which was a major concern to not only the management unit but also employees who relied heavily on the servers to facilitate their operations.
The unsecured system meant that unauthorized individuals could easily access data and manipulate it or monitor events at the firm. The management needed an improved system that would organize the data, make it more secure, and improve the monitoring mechanism in all the branch offices. The institution introduced a Standardized Micro Data Center to solve different problems at each of the branches based on the local needs. The data management infrastructure was also improved and the management hired IT experts to help in monitoring and protecting the servers. Although the initial cost was high, as shown in the White Paper, the initiative helped improve data management at this firm. Information became more secure and employees were able to share data with ease.
Force Upgrade of a Mobile Application via a Server Side Configuration File was an upgrade project sponsored by Box, Inc., a firm based in Redwood City, California, which offers file sharing and cloud content management services for business entities (Tan, Maynard, Yao, & Cung, 2016). In this project, the primary aim of the company was to develop a new system that would upgrade mobile applications automatically on hand-held devices to enhance their security and stability via a server-side configuration file (Tan et al., 2016). The initiative was meant to address a major concern among clients of this company where it was reported that some mobile devices used by employees were becoming major targets of cybercriminals, especially for the companies offering cloud-based solutions. In this project, the company came up with a new mobile application that would force the device to shut down automatically when it is flagged as being suspicious. The device will then undergo a new configuration, a process that makes it possible to authenticate the current user and possibility of a hack. The device would be restricted to access considered safe until the user can verify its safety by physically visiting the operators at the server. In case the verification is not done, the device would be denied access to the server.
Why Enterprises Should Care about Serverless Computing is an article that explains how large corporations are embracing the new cloud computing technology as a way of improving efficiency and reducing the cost of operation (Janakiram, 2016). One of the companies identified to have migrated to the serverless cloud computing technology is the Coca Cola Company. This firm is one of the largest global corporations, with branches in every continent (Janakiram, 2016). The firm offers beverages widely used by people of all ages. The management of this company has been promoting its vending machines in an initiative meant to increase sales in the market. However, the report shows that the traditional servers were overwhelmed, especially during holidays.
Cases of server breakdown or downtime were becoming increasingly common at the company, causing major inconveniences to its customers and reducing sales for the company. Marketing managers also relied on the information from the sales at these vending machine points to determine the appropriate pattern of promotional messages that should be sent to each market. However, the inefficiency of the servers made it difficult for the department to have access to such information. The management made the decision to migrate to the serverless cloud computing technology to help address the concern.
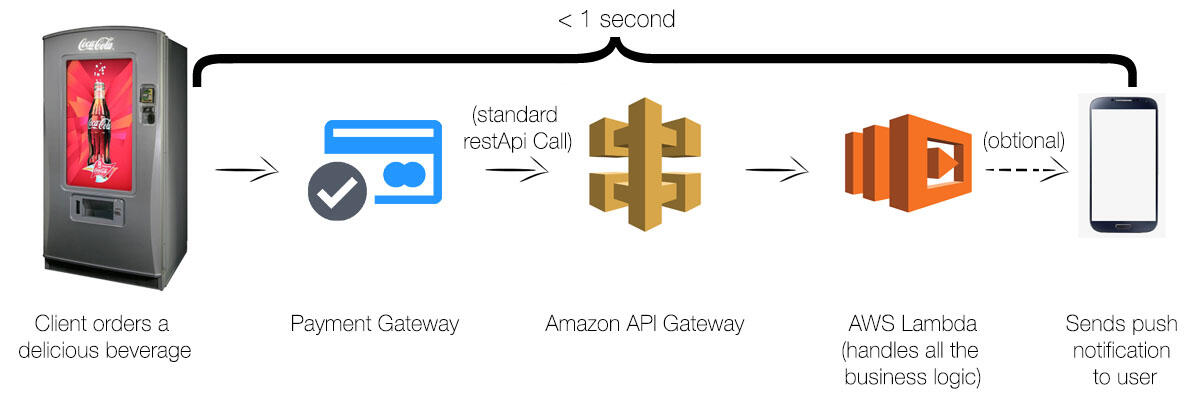
In this new platform, the Coca Cola Company opted to use the services offered by cloud provider instead of using its own server. Amazon Web Services, Inc. (AWS) was considered the most appropriate cloud-computing provider because of its security features and the fact that its architecture is appropriate for online retailing. The design is shown in Figure 3 below. The responsibility of managing the server and ensuring that it works effectively was handed over to the cloud-computing company. Under this upgraded system, the vending machines became more effective and capable of collecting data needed by other departments such as marketing unit, the finance department, and the logistics unit.
When making a purchase, a client uses their smartphone to make an order through the ATM number provided. The machine makes a Rest API call to AWS API Gateway, which would then trigger a lambada (Stanek, 2016). AWS lambada would then process the information, send a payment code to the client’s smartphone, activating an Apple Pay or Android Pay (Janakiram, 2016). The transaction would be complete in less than a minute and the client will have the needed product from the vending machine. Figure 4 below shows the process.
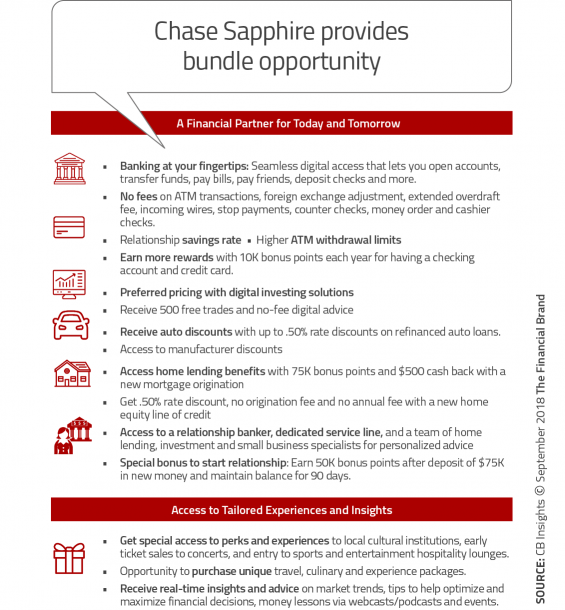
Chase Commits to Long-Term ‘Digital Everything’ Strategy is a newspaper article that explains an ambitious plan by JPMorgan Chase Bank to digitize its operations as a way of improving its competitiveness in the market (Marous, 2018). In 2014, the company revealed that a major data breach had compromised 83 million accounts. It was a major turning point for the company as it sought to strengthen the security features of its servers and all the devices that clients and employees use to access its database. The management realized that although the threat of cyber-attacks was becoming more sophisticated than was the case in the past, it was impossible for the firm to avoid digitizing its operations. After a thorough upgrade of the system that took three years, the firm considered it safe enough to digitize its entire operations. It introduced a Digital Banking System in 2017 (Marous, 2018). Figure 5 outlines the new benefits that customers can access the new system.
Relation of Artifacts to Project Development
The proposed project has a close relationship with each of the upgrade projects discussed in the above section. The first case focuses on a small food distributing company that faces the challenge of data management. The previous system made it difficult to have access to the needed information in its digital platform within the right time. However, the system upgrade helped in improving data management, just as it would if this company upgrades the current Exchange 2010 to Exchange 2016 environment. The second case focuses on a system upgrade at Box, Inc. The main concern was poor security with the previous system. The upgrade improved security, which is one of the benefits that Temperton Accounting Firm will enjoy under the new system. The third case focused on improved the system at the Coca Cola Company’s vending machines upon server upgrade. This accounting firm will offer better services to its customers upon its completion of the system upgrade. The final case focuses on the digitization of operations at JPMorgan Chase Bank. The accounting firm will be able to digitize its operations when it upgrades to the Exchange 2016 environment.
Project Rationale
Companies offering financial solutions face a new challenge in modern society. According to SenGupta (2017), these companies have to ensure that they embrace technology as a way of improving their service delivery. Besides the problem of cyber-attack, which has become a major concern in this industry, there is a need to enhance communication among employees and between a firm and its clients. When accountants are in the field gathering data, they should be able to feed their information into the central database in real time so that other experts can process the information, especially when working under a tight schedule. An analysis of Temperton Accounting Firm revealed that it is currently using the Exchange 2010 environment, which many experts currently view as inadequate in addressing emerging challenges. The rationale for this project is to upgrade this system to the Exchange 2016 environment to address the main weaknesses of the current system. Besides the technical reasons discussed in the proposal overview section above, the new platform also has business reasons why it should be implemented.
According to Stanek (2016), accounting firms are currently under pressure to provide a quick analysis of financial records, especially when trying to trace financial embezzlement. As such, one of the factors that often defines whether a company gets a contract or not is whether it can deliver the service within a given timeline. This new platform not only increases the speed of service delivery but also efficiency. The improved output will open new business fronts for the company, making it possible to expand its market share. Temperton Accounting Firm will achieve a competitive edge over its rivals that are yet to embrace the new system. SenGupta (2017) also notes that other than the initial cost of installation, the new system reduces the overall cost of operation. These economic benefits justify the need for the company to switch from the current Exchange 2010 to the new Exchange 2016 environment.
Current Project Environment
The current project environment should be analyzed to understand the present situation of the firm and the path that it should take to improve the efficiency of its operations in terms of data management. As the company continues to expand in the national market, the management has realized that specific inadequacies needed to be addressed. Temperton Accounting Firm is not introducing the platform for the first time. It had the Exchange 2010 environment, which was already in use. However, the capacity of the current system is inadequate. The current system has helped this firm to improve its efficiency, but as the clientele base for the company continues to expand, it is apparent that it cannot continue to rely on the Exchange 2010 environment. Under the current environment, data loss is a common phenomenon because of the weaknesses of the phenomenon. It is frustrating for employees to go back to the field to collect data once again in cases of such loss. The management opted to have a backup server just to ensure that data can be recovered in case of a system breakdown. It takes time to back up the data.
The current state of the server should define the path that should be taken to implement the proposed solution. Currently, the send and receive connector have a default maximum size of the message of 10 MB (Stanek, 2017). As a firm grows and more employees get to use the server, the volume of the message increases. A limit of 10MB becomes incapable of meeting the demand for the organization. The new server promises to address this major concern by increasing the capacity to a default maximum size of 25 MB. This major improvement means that more users can be accommodated into the system without compromising the speed. The server will process information at a greater speed than it is currently the case if the upgrade is completed.
The current Exchange 2010 environment lacks built-in malware protection. According to SenGupta (2017), one of the biggest concerns accounting firms currently, the face is the threat of hacking. Criminals are currently targeting financial institutions and accounting firms to achieve their selfish goals. Some may want to manipulate data to steal money from the company. Others may manipulate the data to hide a major fraud at the firm. Another group may be interested in discrediting the reputation of an accounting firm by introducing new facts into the data or deleting crucial information in a way that jeopardizes the ability to get accurate facts. Integrity is one of the factors that cannot be compromised at this accounting company.
When contracted to conduct an audit in a government institution, a publicly listed company, or a private firm, one of the legal requirements is that the information that the firm provides must be valid because it will inform the decision that would be taken by various stakeholders. In such an environment, it becomes necessary for the company to have a back-up system, preferably actual paper trail that can be used as a reference just to ensure that data in the system is not compromised. Such an initiative is time-consuming and requires an additional human resource. In the end, the company would spend more on these activities. Exchange 2016 is the right path to take when trying to address this major concern. The new server has built-in malware protection. Data would not be easily manipulated through the planting of malware into the system or any of the computers used to access the server. It can detect and eliminate malware. Users would also get the information about the detected malware so that further measures can be taken to clean the incoming data and the entire server in case it is necessary.
The current 2010 server uses to attach their documents to an email in case they need to share information. Although this function is a major improvement compared with the previous systems, it is time-consuming to attach these documents to the email. It is also easy for someone to forget to attach the document when sending the mail. The issue has been addressed in the 2016 server through the introduction of SharePoint 2016. Instead of attaching files through an e-mail address, one can share documents from one drive to another by having them linked through the common server. This function was made possible because of the introduction of Exchange 2016 OWA, which did not exist in the 2010 version (Stanek, 2017). Users can share data in real time under this system. The introduction of the Outlook Web App (OWA) in this new version also means that employees of this company can now use mobile devices and tablets. The server is increasingly becoming user-friendly, especially for data collection experts who may not find the use of laptops appropriate in their normal duties.
Methodology
When implementing a given project, it is often important to identify an appropriate methodology that would guide the entire process from the initiation stage to the final step when the project is handed over to the owner. The most appropriate method would be PDCA (plan-do-check-act/adjust). The method follows simple steps as shown in Figure 6. In this method, the first step is to conduct a plan by identifying the current weaknesses and the root cause of the problem at Temperton Accounting Firm. The planning process also involved in defining what should be done to address the identified problem. In this case, Bytes to Bits Computer Consulting has determined that the Exchange 2010 environment currently in use at this company needs an upgrade. The second step (Do) is to fix the identified problem. The consulting company will upgrade the current environment to Exchange 2016 environment.
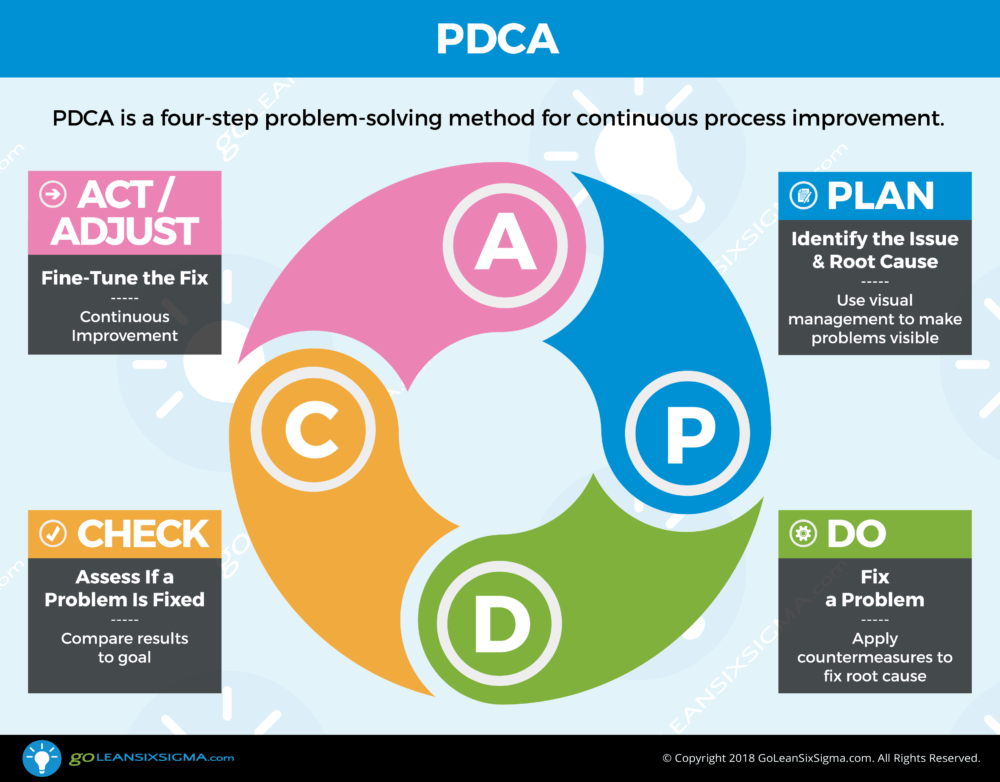
A detailed process of upgrading the server from the Exchange 2010 to Exchange 2016 has been described in the section above. The proposed method identifies the third step as the process of checking if the problem is fixed. The client had outlined the major weaknesses of the current system that compromised data security and slowed operations. The stage involves determining if these issues are addressed once, the new system is operational. The last step is to act or adjust as would be necessary. The process involves fine-tuning the system to meet the specific needs of the company. The Exchange 2016 environment is currently used in different industries. However, SenGupta (2017) explains that it is often necessary to fine-tune it based on the specific needs and expectations of a client.
Project Goals, Objectives, and Deliverables
The project is focused on achieving specific goals upon its completion. Although the upgrade will have numerous benefits to this company, these benefits can be narrowed down to three main goals. The first goal would be to enhance the security of the data used in this firm. One of the current concerns for the management of Temperton Accounting Firm is that its data is vulnerable to possible breaches by hackers using sophisticated systems. The Exchange 2016 environment will address this shortcoming. The second goal is to improve the ability of employees at this firm to share data. The current Exchange 2010 environment forces employees to attach their files to messages they send to colleagues or their superiors.
It means that if one does not send the message with their attachment, others cannot access the information. However, the new system will make data accessible to other parties immediately it is keyed into any of the gadgets in the server. This new application minimizes data loss because the information will remain available in the server even if the gadget is lost, destroyed, or stolen in the field. The third goal would be to improve the archiving capabilities of the system. The Exchange 2010 environment comes with larger and more dynamic storage capabilities than the 2010 version. Table 1 below provides a summary of the goals, supporting objectives, and deliverables enabling the project objectives.
Table 1: Goals, Objectives, and Deliverables.
Goals, Objectives, and Deliverables Descriptions
The first objective shown in the table above focuses on the improvement of security at Temperton Accounting Firm. The industry within which, this company operates is very sensitive and has become a major target for cybercriminals. Any manipulation of data being processed for a client may have devastating consequences. As such, this accounting firm must block any possibility of third parties having access to the data and the capacity to manipulate it in any way. The goal has three main supporting objectives, to ensure that data is only accessible to authorized persons in the company, to protect the data management system from malware, and to inform the data management personnel in case there is a data breach. Each of the three supporting objectives had three deliverables, as outlined in the table. The second goal focused on improving the ability of different stakeholders at the accounting firm to share data in real time. The supporting objectives and deliverables help to explain the benefits of achieving this goal to these stakeholders. The final goal emphasizes the need to improve archiving capabilities at the firm. Given the company’s growth trajectory, it is evident that it would require greater storage capacity, which is offered in the Exchange 2016 environment.
Project Timeline with Milestones
In the implementation plan section above, a detailed explanation of the activities that would be carried out in this project has been provided. The activities will be conducted in different phases. When the project was handed to the consultant, it was made clear that the client wants work done by September 2019. As such, the activities must be planned and executed in a way that would ensure that everything would be ready by the stipulated date. The project should be completed within a period of three months. For the team to ensure that the set activities are completed within the stated duration, it will be important to ensure that the proposal is approved within the shortest time possible. The outlined activities can only be conducted if the client, Temperton Accounting Firm, is satisfied with the proposal. As such, the first activity was to develop the proposal. The client can go through this proposal and have it approved within two weeks after receiving it. However, the team has provided one whole month for the proposal to be approved, knowing that some issues may arise that may delay the process. Table 2 below identifies the milestones that have to be achieved and the projected duration.
Table 2: Project timeline.
The implementation plan above identifies five phases of implementation. Each will define the steps towards upgrading the current Exchange 2010 to Exchange 2016 environment. When the management of Temperton Accounting Firm approves the proposal, activities will be initiated immediately. It is expected that activities will begin on June 1, 2019. Time allocated for each phase depends on the activities that are involved, the complexity of the processes, and individuals who have to be involved. The first phase of updating the current Exchange 2010 environment in preparation for the upgrade will take 14 days. The process is simple and can take just a few hours. However, the assumption made in this case is that employees at this firm would need a smooth transition from the current to the new system.
The consultant is also keen on ensuring that the process does not interfere with normal activities at the firm. The second phase will take seven days, while the third phase, which is one of the most involving processes, will take 21 days. The fourth phase will take nine days, while the final phase of testing the new system will take 21 days. Some form of employees’ training will take place during this phase to ensure that workers at this company can work effectively under the new system. It is important to note that days set in the implementation are flexible and the timeline is longer than would be the case because of the assumptions that issues may arise during the implementation process that may cause delays. The project will be ready by September 1.
Outcome
Upon the completion and handover of the project, it will be important to measure the outcome to determine if the expected goals were achieved. The client, Temperton Accounting Firm, should have a better system that is more secure and allows its stakeholders to process, store, and share data with ease. The proposed framework for evaluating the outcome of the project will be based on the three primary goals discussed above. First, the new system should ensure that data security is enhanced to the highest level possible. Bytes to Bits Computer Consulting, as the consultant in this project, will work closely with employees of this firm to ensure that the server does not suffer any breaches. The unique features of the Exchange 2016 environment assure the security of the database.
The success of the project would be defined by the ease with which employees in the field can share data with their colleagues irrespective of their location. Instead of having to attach files in messages they send, as is the case currently, the new system should make information keyed into the devices available to other relevant users in real time. This function should work as promised and it will be tested if it works within the 21 days of the final phase of the project before the project is handed over to the client. The new system should have a larger storage capacity, as explained in the third objective. As the firm continues to grow, it is expected that its clients would increase in number, and that would require it to expand its storage capacity. This benefit will be tested before the handover period. The team will ensure that the database has the promised capacity.
References
Avelar, V. (2015). Practical options for deploying small server rooms and micro data centers. White Paper, 174(1), 1-11.
Janakiram, M.S. (2016). Why enterprises should care about serverless computing. Forbes Magazine. Web.
Leonard, C., Svidergol, B., Wright, B., & Meloski, V. (2016). Mastering Microsoft Exchange Server 2016. John Wiley & Sons.
Marous, J. (2018). Chase commits to long-term ‘digital everything’ strategy. The Financial Brand. Web.
Rathnam, L. (2016). How to migrate from Microsoft Exchange 2010 to Exchange 2016. TechGenix. Web.
SenGupta, A. K. (2017). Ion exchange: Environmental processes. Hoboken, NJ, Wiley.
Stanek, W. (2017). Exchange server 2016: Server infrastructure. East Olympia, WA: Stanek & Associates.
Stanek, W. R. (2016). Exchange server 2016 & exchange online: Essentials for administration. East Olympia, WA: Stanek & Associates.
Tan, S., Maynard, D., Yao, R., & Cung, D. (2016). Force upgrade of a mobile application via a server side configuration file. Foreign Patent Documents, 61(697), 1-26.