Introduction
It is hard to disagree that the success of any company partly depends on its vendors. Their critical importance is that they ensure the ability of the organization to achieve profit goals and revenue and drive new growth within the particular industry. Therefore, vendors are at the heart of an extended number of the company’s activities and processes, so it is crucial to manage and improve the relationships with them. Since an organization may have over a hundred various vendors, this process of controlling them may become rather complex and challenging. It may even appear that the company is losing money on several hidden costs or overpaying for services and goods, that is why proper vendor management is crucial. Vendor management is a unique process of sourcing and researching suppliers, paying them, evaluating their performance, managing vendor relationships, negotiating contracts, and obtaining quotes. Paying proper attention to these essential steps can help the company save both its reputation and significant amounts of money.
Overview of Vendor Breaches
Data Breaches
There are several types of vendor breaches that may occur while a company works with suppliers. One such problem is identified as a data breach and “refers to a confirmed incident, in which sensitive, confidential, or especially protected data has been accessed and/or disclosed to unauthorized third parties” (Kallberg, 2019, para. 2). The exposures of data may include certain important information like trade secrets, intellectual property, and any other personal data (Davidoff, 2019). Since third-party vendors are the company’s trusted partners, the collaboration with them may create “an increased risk of exposure to a potentially serious data breach” (Kallberg, 2019, para. 2). Therefore, working with suppliers requires any company to follow certain rules and make sure that the necessary safety steps are completed properly and in a timely manner.
Minor Vendor Breaches
As for minor vendor breaches, they refer to those problems that were caused by either party’s failure to fulfill a certain part of its obligation. It may happen even though the deliverable of the contract itself was eventually received by the other party (Kallberg, 2019). In cases like this, a legal remedy can only be pursued if the party that suffered the breach is able to prove that the result of the breach was the financial loss (Kallberg, 2019). For example, a late delivery will not remedy if the delay did not result in economic consequences.
Statistics
In the current world of businesses, an extended number of companies and organizations are using third-party vendors more than ever before. Hence, it is evident that there is a higher level of access to internal systems with sensitive information and private data available to these sellers. Researchers note that “the 2018 Ponemon statistics show that at least 56% percent of organizations have experienced a data breach due to a vendor’s security shortcomings” (Kallberg, 2019). Unfortunately, vendor breaches, even those that seem insignificant, are able to damage the business and its performance. Moreover, a survey across various industries found that the number of cybersecurity incidents related to third parties is increasing, which is demonstrated in Figure 1 (Kallberg, 2019).
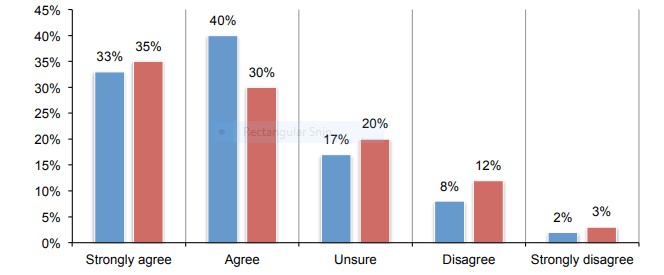
- Cybersecurity incidents involving vendors is increasing
- Cybersecurity incidents involving vendors is difficult to manage
Seminal Vendor Breaches
As for especially severe vendor breaches, they typically cause significant damage to either party, and their consequences can affect the company to such an extent that it may have to stop its activity. Seminal vendor breaches include those challenging issues that have already occurred (Cloutier et al., 2016). In other words, they are precisely those breaches that were caused by a party that has either performed its obligations improperly or incompletely or refused to fulfill its duties by the due date. A vast number of types of remedies pursued by the party that suffered the breach may, for example, include compensatory damages.
Overview of Vendor Management
Frameworks
A vendor management framework is a specially created logical system that is aimed at the development of a vendor management program. The framework typically consists of communicating and determining the value each vendor brings, managing vendors, recommendations for creating the program, and divesting and acquiring vendors (Ncontracts, 2018). Financial institutions are more often to use vendors, especially for those responsibilities and tasks that may be accomplished through technology.
The purpose of the framework is to describe in detail how to choose and evaluate vendors, as well as correctly negotiate with them. What is more, the ways of making an agreement and managing the vendors’ performance and the relationship with them are also provided by the framework. Finally, “vendor risk management is also considered within a vendor management framework” (Ncontracts, 2018, para. 4). As for particular examples, “the integrated conceptual framework includes antecedents, moderators, and mediators of vendor management” and is considered one of the most effective in this area (Verma & Girdhar, 2020, p. 63). Moreover, such a framework plays a central role in project management paradigm improvement.
Various Approaches
Since vendor management is such an enormous issue and a severe process, it is evident that various scientists and analysts have diverse opinions on the ways of finding an approach to it. Therefore, there is an extended number of different methods that are considered to be useful in vendor management (Cloutier et al., 2016). They generally include external assessment, interpretive strategy, the Kraljic Matrix method, and the Deloitte priority model. All these and some other approaches are proven to be effective and have certain positive and negative features that determine what procedure is more useful in a given situation.
External Assessment as Vendor Management Approach
As mentioned above, there are several methods and approaches that help companies manage their vendors successfully and effectively. For example, one of them is an external assessment approach. It is aimed at evaluating certain factors and forces that may either positively or negatively influence vendor management (Cloutier et al., 2016). In order to get a better idea of external assessment, it is necessary to discuss the usefulness, advantages, and disadvantages of this approach.
Description of the Approach
This method of external assessment is carried out by either third parties or stakeholders directly involved with the organizations. The purpose of this approach is to critically and independently evaluate the current and/or future suppliers, possible hidden or unnecessary costs, as well as other valuable information regarding vendors. Moreover, the external assessment technique assists in revealing the threats and opportunities of the company and its contract with suppliers.
The usefulness of the Approach
External assessment in vendor management helps to make this process more comfortable, beneficial, and effective. Thanks to this method, it becomes possible to reveal hidden threats and eliminate upcoming breaches unless they become too dangerous (Cleary & McLarney, 2019). Moreover, some unobvious opportunities that may increase the performance and overall success of the organization may be discovered with the help of this approach (Cleary & McLarney, 2019). Finally, external assessment is useful not only in vendor management but also in an extended number of other areas.
Advantages
Since external assessment is a necessary technique, it is hard to disagree that there are many positive features of this method. To begin with, people who carry out this evaluation typically look at matters from a new perspective and take a neutral standpoint (Cleary & McLarney, 2019). In other words, in most cases, such an approach can guarantee impartiality and objectivity of assessment (Cloutier et al., 2016). Second, a relatively simple but, at the same time, beneficial advantage is the fresh look and the creativity of an external assessor. The person or the company not involved in the organization’s processes may provide a completely new and fresh opinion that would be as close to reality as possible but still not noticed by the internal assessors. Finally, another advantage of this method is its breadth of experience (Cleary & McLarney, 2019). Since external assessors work with a variety of organizations, they are believed to be quite skilled. Moreover, most situations tend to repeat from time to time, so an experienced external assessor may be completely sure what should be done to eliminate a particular vendor breach.
Disadvantages
Unfortunately, this approach is not entirely perfect, and a number of serious disadvantages make it not suitable for some vendor management situations. For instance, it was mentioned above that the performer of external assessment is typically objective. However, this advantage can turn into a shortcoming if the external assessor lacks cohesiveness and involvement. It is hard to disagree that these two concepts are usually rather necessary to understand, influence, and change the company’s internal processes. That is why their absence may have a negative impact on the assessment results and the company’s vendor management itself (Cleary & McLarney, 2019). Another shortcoming is that performing an external assessment may be much more expensive but without any significant difference in the results. Finally, such an approach requires collaboration, which means extra time for explanations, questions, and possible misunderstandings.
Viability to Managing Vendor Risk
This approach seems to be both useful and weak in managing vendor risks, and it totally depends on the specific situation. First, it may happen that a fresh look of the external assessor is able to notice and evaluate previously hidden vendor threats or risks that seemed rather safe (Cleary & McLarney, 2019). However, a completely opposite situation may happen, and to spot a vendor hazard, it may become necessary to be familiar with the internal processes, secret or rare information, or some specific conditions of the company. In this case, some other approaches, including the internal assessment, would be more useful.
Conclusion
To draw a conclusion, one may say that vendor management is indeed an enormous and challenging issue. The power and influence of the work of the suppliers over the company are hard to overestimate, and the consequences of vendor breaches are global. Fortunately, most of them are easy to predict and escape, while a number of others do not pose a severe danger. Various methods are useful in defining and evaluating vendor risks and the ways of solving them. The external assessment appears to be a practical approach to vendor management and breach elimination, but just as in any other method, its advantages and disadvantages are equally significant.
References
Cleary, S., & McLarney, C. (2019). Organizational benefits of an effective vendor management strategy. IUP Journal of Supply Chain Management, 16(4), 50-67.
Cloutier, T. L., Gray, S. B., Peckham, J. T., & Pierce, D. R. (2016). Vendor management system and process. U.S. Patent No. 9,317,824. Washington, DC: U.S. Patent and Trademark Office.
Davidoff, S. (2019). Data breaches: Crisis and opportunity. Boston, MA: Addison-Wesley Professional.
Kallberg, J. (2019). Top 7 vendor related breaches of all time. Web.
Ncontracts. (2018). Vendor management framework. Web.
Verma, S., & Girdhar, P. (2020). Integrated framework for vendor management: An interpretivist approach. Journal of Management Research, 20(2), 63-74.