Introduction
Cybersecurity takes up an indispensable place in the security management of each company. Frequently the reasons for the system hacking become non-executive directors, who lack knowledge on the topic of cybersecurity, therefore possessing high risks to the enterprise. Luckily, many preventive and defensive strategies are created in order to inform and protect the employees and the business from any cyber-attacks. Therefore, this essay will elaborate on the most major digital threats that non-executives face while being on their computers and provide practical strategies for preventing it.
Why Non-Executive Directors are Targeted and How They Targeted?
The responsibilities of being a non-executive director in today’s highly connected environment include many risks and challenging tasks. Non-executives are the primarily responsible figures for the correct functioning of an enterprise, ensuring effective governance, therefore, holding accountable for a large portion of secure data on other employees. They have a responsibility in front of the board to convince of high liability, as statistically, most board members are highly skeptical about this matter, as opposed to the executives (Oord, Rothrock, and Kaplan, 2017). Having access to highly valuable data within the organization, especially that includes financial and personal information makes executives the main target of the cyber-attacks.
Being accountable for a vast portion of duties and information includes the possibility of unintentional negligence of certain factors. Non-executive directors frequently manage to work on behalf of several organizations, which makes them more exposed to a variety of security issues. Moreover, such an extensive range of information possession creates more value for these particular workers for hackers, as they can approach a wider spectrum of data. Therefore, non-executives must take more caution In terms of their personal cybersecurity to avoid being hacked, as well as put increasing focus on the companies safety and protection of the informational property.
Holding accountable for a lot of strategically important company information, it was determined that non-executive directors are becoming one of the primary targets of hackers. There are many ways they trick the directors into granting access for invasion, as these employees face high exposure to a range of security issues. The vulnerability of web services, which expose the software that is used, unhidden document properties creates many possibilities for cyber-attacks., which non-executives are responsible for. Research determined that 16% of Forbes 2,000 corporate web servers are vulnerable to cyber-attack due to missing security updates or outdated software (KPMG International, 2015). Through admittance to these properties, hackers have all assets to easily infiltrate corporate systems, including personal identities, financial accounts, and healthcare information from just one person, which most likely be a non-executive director.
Threats Specific to the Non-Executive Directors
Hundreds of cyber attacks have been invented during the Internet’s existence, ranging from random to targeted forms, damaging internal systems of the companies and individual devices. However, some particular hacking threats are especially dangerous for the non-executive directors at the companies. The following threats compromise the security of the enterprise by compromising highly secretive data.
Confidentiality leakage is probably the most dangerous threat that non-executives must constantly monitor. Confidentiality breaches are the most common hacking tactic, targeting weak security systems (Donaldson et al., 2015). Stealing social security numbers, credit card information, healthcare reports, and secret company documents are a shortlist of all the potentially vulnerable information that non-executives have access to. The most dangerous part of such a cyber-attack that the information may be extracted unnoticeably and only discovered upon its leakage to the competitors or the media (Donaldson et al., 2015). Therefore, it is vital to establish a highly protective cyber-security system and have a constant watch over it to prevent any confidential information leakage.
Targeted cyber-attacks such as hacktivism is a severe hazard for the enterprise, primarily lying on the non-executive director’s shoulders. Activist hacking is a targeted attack that is used to make public statements to embarrass their adversaries (Donaldson et al., 2015). Hacktivism is frequently used against enterprises to ruin their reputation or a particular individuals inside the company for various purposes. Non-executives may quickly become the main targets of such crime, as they are accountable for a large portion of sensitive personal data that may be used to jeopardize the reputation.
The last threat lies within simple e-mails and websites, which is commonly known yet often disregarded. Proofpoint research determined that more than 20% of the e-mail addresses are at high risk of containing hacking bugs that access personal information (Proofprint, 2018). As executives daily go through dozens of emails, they must continuously be on the watch to track suspicious addresses and avoid opening them. Attackers take advantage of such inattentiveness, therefore, perpetrating easily entered security defenses, which were failed to be double-checked. Otherwise, the confidential information they are storing may be in danger, as well as other employee’s accounts.
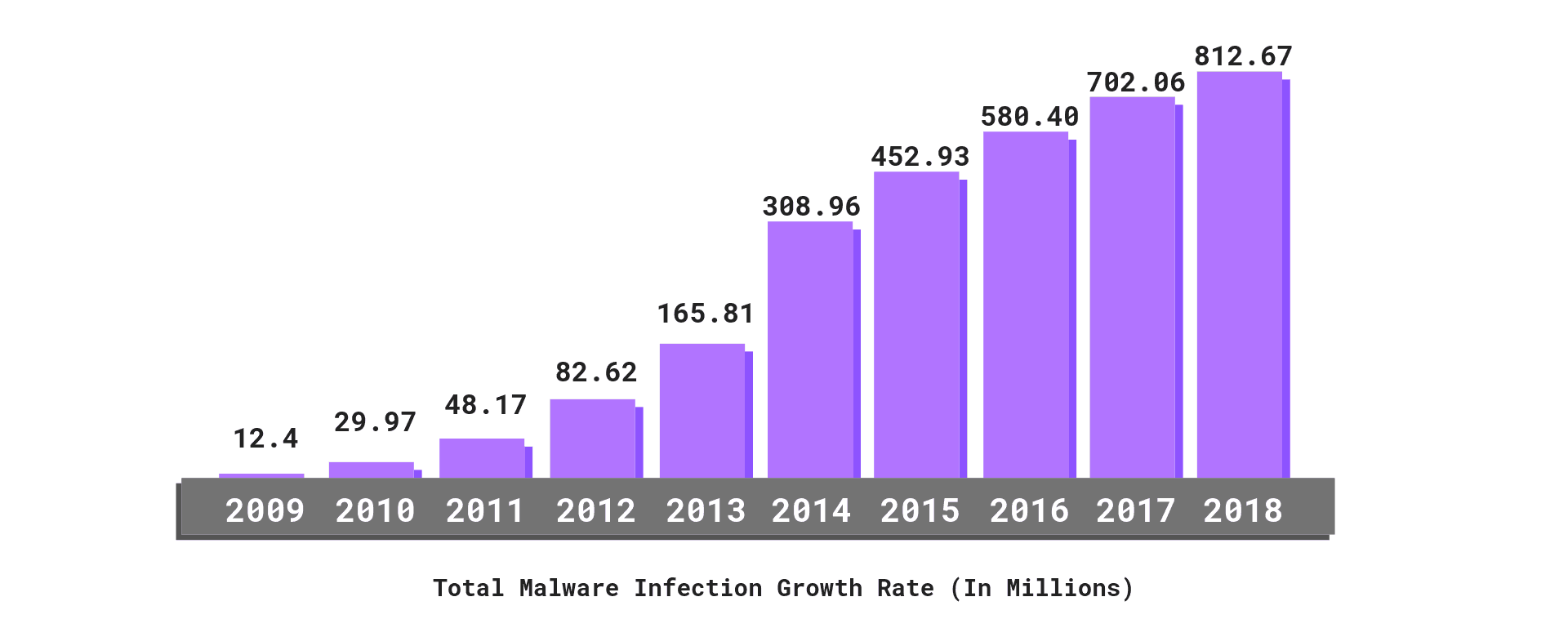
Defensive and Detective Strategies
Effective cybersecurity programs must be highly prioritized at any organization, providing increased protection for confidential information. Confidentiality leakage is the most dangerous cyberattack that the enterprise may face, therefore requiring the application of effective strategies to protect it. The UK National Cyber Security strategy claims that most of the cyber attacks are due to the high vulnerability of the systems (The role of the Non-Executive Directors in effectively overseeing security, 2020). In this case, technology is the most practical way of fighting back the hackers. In the high-tech world, cyber-security is dependent on the establishment and maintenance of the digital security system, which may protect the company and its executives from hackers.
Hacktivism requires specific methods of defense as these hackers tend to work individually or in small groups. Their cyber invasion methods may be primitive; however, they are most likely to extract sensitive data from the companies system (Donaldson et al., 2015). Non-executive directors can frequently be unaware of the volume of material attackers can access, thus failing to restrict admittance to the certain informational property. Therefore, a practical strategy would be using specific software that stores all the company information and encrypts the one that is rarely used. It is essential to continually monitor all company technology activity to promptly detect any suspicious actions.
Establishing information security policies and installing plugins that automatically detect suspicious e-mail content would become a feasible defensive and detective strategy to combat malware in the electronic mail. Cybersecurity guidelines provide step-by-step instruction in identifying potential threats and a need for supporting technologies (Donaldson et al., 2015). Plugins for detecting harmful content significantly decrease the chances of opening mail that contains viruses.

Conclusion
The position of a non-executive director comes with an extensive range of responsibilities and risks, one of them being a threat of cyber-attacks. People with such corporate positions are accountable for a major portion of information regarding employees, their personal data, and evidence of corporate security. Cyber-security is highly essential to manage, particularly for non-executive managers, as they are becoming the primary targets of hackers due to the possession of such a vast spectrum of liable data. Nevertheless, the application of widely available strategies against cyber-attacks, with the help of well-developed programs and personal precautions, significantly decreases the possibility of the attack on informational property. Nevertheless, it is essential to constantly improve cyber-security and be on the lookout for any suspicious actions.
Reference list
Donaldson, S.E., Siegel, S.G., Williams, C.K. and Aslam, A. (2015). Enterprise Cybersecurity. Berkeley, Ca Apress.
KPMG International (2015). Non-Executive Director’s Update Cyber Security Breaches. Web.
Oord, F.V. der, Rothrock, R.A. and Kaplan, J. (2017). The Board’s Role in Managing Cybersecurity Risks. MIT Sloan Management Review.
Proofprint (2018). Protecting People – Cybersecurity Threat Report.
The role of the Non-Executive Directors in effectively overseeing security | Cambridge Cyber Advisers. (2020). Cambridge Cyber Advisers.