Introduction
This paper will use a medium-sized business offering highly specialized, high-quality business development education services as an example. Table 1 illustrates how the mixed data can be managed in the company. Keys here are customers’ full names, customers’ identification keys, and their respective sales orders. In the latter, the first three digits show the course: 100 stands for business analytics, 200 stands for the social media marketing course.
Table 1. Example of mixed (internal and external) data management: Customers and respective sales orders
Table 2 demonstrates a way of managing internal business data. This example shows the employees’ PII storage.
Table 2. Example of internal data management: Employee data
Finally, Table 3 illustrates an example of external data flow management. Here, the coded answers of an online survey are presented. The two questions presupposed a yes or no response and, thus, were coded in a binary form.
Table 3. Example of external data management: Coded satisfaction survey results (binary)
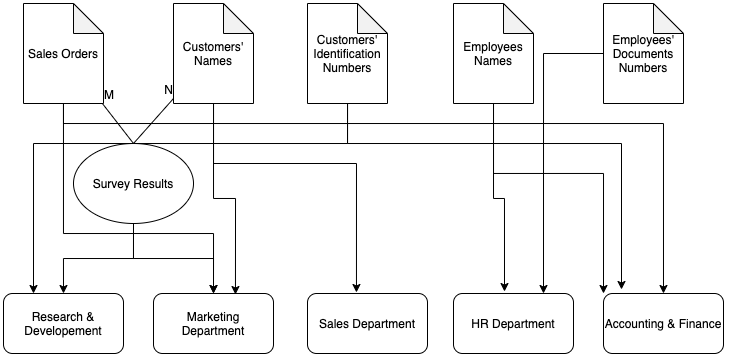
Data flow in the business
The diagram illustrates the relationship between the mentioned data entities and the major departments in the company. It is visible that internal data like employee information is directed to several departments since it is essential information for the HR department and the Accounting and Finance department.
The data will be stored on cloud storage since such storage is more suitable for small and medium businesses (Attaran & Woods, 2019). The main criteria by which data storage on the cloud or server is distinguished are availability, safety, and security. Cloud storage is less expensive, but large enterprises may require a server that provides greater privacy. Thus, in the course of business expansion, it is likely that there will be a need to switch to local servers. At the moment, the advantage of cloud storage is that it is an ideal solution for working remotely.
Personally Identifiable Information (PII) Security
Not only personally identifiable information is subject to protection, but the entire information system, that is, the programs with which the personal data are processed and the computers on which they are stored. If the computer is connected to a local network, it is necessary to protect the network equipment, cables, and server. For each employee working with personal data, it is required to create a separate account to log into the computer. To work, they must enter their name and password (and this password should not be visible on the screen) or attach an electronic key.
Computers must be configured so that after several incorrect password attempts, the user account is blocked. Each user should have the right to perform only those actions that are determined by their job responsibilities. Of course, dues must be cut within reasonable limits because a situation may arise when one employee has to replace another. An encrypted communication channel must be organized between their computers and the company’s server for the employees working remotely.
Wi-Fi, if not needed, must be turned off. If it is required, then access to outsiders must be closed with a long, hard-to-guess password. That is, the password must be a meaningless or random set of letters, numbers, and other symbols, preferably at least eight.
Information security events (for example, user login, failed login attempt, attempt to log on under a locked account) should be recorded in a unique log. In Windows, such a log is kept automatically. If there was an attempt to steal data, viewing the log will help to understand what happened, for example, who was working at the computer at that moment.
Reference
Attaran, M., & Woods, J. (2019). Cloud computing technology: improving small business performance using the Internet. Journal of Small Business & Entrepreneurship, 31(6), 495-519.