Criminal Justice System and Information Technology
Technologies have a considerable effect on the daily lives of people since they facilitate workflow, streamline processes, and introduce efficiency. The criminal justice system benefited from technological advancements because they allowed individuals serving the law to have more tools for identifying perpetrators and managing them even after making an arrest. One of the main technologies utilized with the purpose of reducing the risk of criminal activity is crime mapping, which incorporates collecting data on criminal incidents and assessing it with the purpose of detecting problems. CrimeStat is an example of software that conducts both statistical and spatial analysis in order to determine which areas have a high degree of criminal activity and make forecasts about future events (Hunt, 2019). There are also systems such as the Next Generation Identification, which constitutes an electronic repository containing criminal history and biometric information, which is utilized by many members of the criminal justice community (Next Generation, n.d.).
Additionally, police vehicles also often have installed systems that expand the capabilities of officers and provide them with full control of their cars. The iForce computing system developed by Rockwell Collins is an example of an advanced technology that simultaneously incorporates several functions in one interface, including the land mobile radio controller and radar systems (Brewer, 2011). Such mobile devices do not occupy much space inside police vehicles, increase efficiency, and as a result, grant officers the ability to respond to calls faster. Yet, there are also software solutions that allow law enforcement to utilize databases containing important information, especially for specialists in certain fields. For example, the National Institute of Justice provides funding to the developers of the Ignitable Liquids Database and Reference Collection, which lets forensic professionals conduct fire debris analysis (National Institute of Justice, 2020). Thus, technological solutions serve as an important factor in the work of the criminal justice system.
Here is a photo of the iForce system installed in a police car.

System Software
Software is a collection of data and various programs which enable computers to perform certain tasks; essentially, it is responsible for telling the computers what to do. Professionals discern two types of software; these are system software, such as operating systems, and application software, such as spreadsheets (Kaur & Sharma, 2018). The latter constitutes a program or a number of programs that control and run the hardware of any computer, as well as applications that are installed on it. Another example of system software includes drivers for devices that establish a connection between a piece of hardware of a computer and the operating system. Drivers function as translators who receive information from software and convey it to the hardware (Fisher, 2020). Finally, the firmware is also considered system software and presents software that is already integrated into a piece of hardware by being programmed into its memory.
Application Software
While system software is created for the purpose of establishing stable work of hardware, application software is developed specifically for the needs of the end-user and helps them perform their tasks. Every piece of application software can be installed on a computer only if it has an operating system. Application software is designed by various companies and has different objectives and functions, which, nevertheless, have the same purpose of assisting users with achieving their desired results (Fingent, 2020). The most popular application software is word processing software, such as Microsoft Word, which allows users to create and format texts. Other types of application software include spreadsheet software such as Microsoft Excel, database software, including MySQL, and multimedia software, for example, Adobe Photoshop.
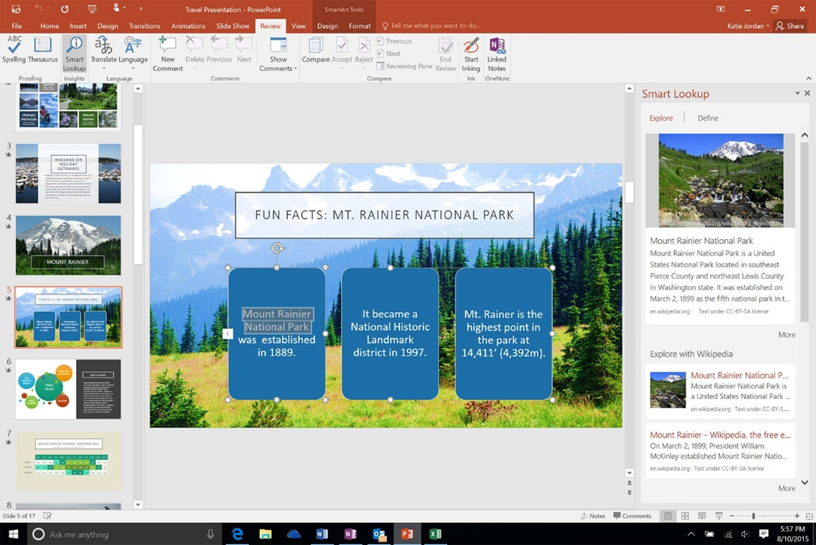
Here is a screenshot of Microsoft Power Point’s interface, popular application software for making presentations.
Primary Functions of the Operating System
As it was mentioned before, operating systems present a type of system software that is necessary for running a computer and executing applications. Nevertheless, apart from that, operating systems perform far more functions; for example, they provide users with an interface that allows them to navigate their computer and interact with their applications (Silberschatz et al., 2018). The function which controls opening applications is called program execution, which maintains a computer’s capacity to load any application into memory and then run it.
Moreover, operating systems are also responsible for ensuring multitasking, which is necessary when launching several applications at the same time. Another function is file-system manipulation, which allows applications and other programs to write files, as well as read them. Additionally, operating systems provide users with the capability to delete their files, rename them, search for them or restrict access. Finally, operating systems also can detect and correct errors, and this function is vital for stable computing.
Secondary Functions of the Operating System
Nevertheless, the previous functions primarily concerned users and helped them successfully interact with the computer, but there are also the ones that ensure stable operation of the whole system. The most important of them is resource allocation, through which operating systems control and distribute resources according to the needs of any process currently running on a computer. As it was mentioned before, operating systems ensure multitasking, and during such situations, they decide which application has to receive more resources (Silberschatz et al., 2018). Additionally, operating systems are responsible for keeping and updating information about how many resources are utilized by different applications, and this is called logging. Based on the gathered statistics and data, users can make decisions about changing the current configurations of the system to make it run better or faster. Finally, operating systems also have a protection and security function, which is performed by ensuring that processes do not interfere with one another and controlling access to system resources.
Three Types of Memory Chips on the Motherboard
Every motherboard contains a variety of modules and important electronics, but the main ones are the memory chips, which include dynamic random-access memory, static random-access memory, and read-only memory (Rubens, 2019). The first one constitutes the most common type of random-access memory utilized in the production of computers. It can hold large amounts of data and has low manufacturing costs, which makes it most suitable for use on motherboards. The static random-access memory, on the other hand, is a much faster alternative, yet it is expensive and, therefore, generally not utilized. It is primarily employed in a CPU as a data cache or server computer, which has a high price (Rubens, 2019). Moreover, compared to static random-access memory, dynamic random-access memory uses larger volumes of energy due to the fact it has to be refreshed to ensure that the data it stores is not lost. The static option does not have to be refreshed.
Here is an image of a circuit board with dynamic random-access memory chips.

The read-only memory constitutes a type of memory that cannot record any data but has a function that allows information to be read from it, possessing fast speed. It typically gets installed near the CPU. Compared to dynamic random-access memory, it is not volatile, meaning that any data it contains will be saved and kept even after rebooting a computer (Rubens, 2019). The CPU reads data, which the read-only memory stores when the computer is working, and this process is performed without the help of any additional drivers or programs needed to establish a connection between them. The read-only memory plays a major role in the process of running a computer since it has pre-recorded code, which constitutes a number of instructions necessary for the computer to recognize an operating system. Basically, the read-only memory contains firmware, which makes it possible to be used on other devices.
References
Alba, D. (2015). Power Point [Image]. Wired.
Brewer, B. (2011). Rockwell Collins iForce nextgen mobile computing. Law & Order, 59(12), 48–51.
Electronics Notes. (2015). Printed circuit board containing DRAM chips. Web.
Fingent. (2020). A detailed guide to types of software applications. Web.
Fisher, T. (2020). What is a device driver? Lifewire.
Hunt, J. (2019). From crime mapping to crime forecasting: The evolution of place-based policing. National Institute of Justice.
Kaur, R., & Sharma, E. S. (2018). Various techniques to detect and predict faults in software system: Survey. International Journal on Future Revolution in Computer Science & Communication Engineering, 4(2), 330–336.
National Institute of Justice. (2020). NIJ-funded software tools, apps and databases. National Institute of Justice.
Next Generation Identification (NGI). (n.d.). Web.
Rockwell Collins. (2010). iForce [Photograph]. Officer.com.
Rubens, P. (2019). Types of computer memory. Enterprise Storage.
Silberschatz, A., Galvin, P. B., Gagne, G. (2018). Operating system concepts (10th ed.). Wiley.