Abstract
For the sake of Identification, the hospital administration should be the only one with the right of issuing IDs, if Identification is not issued by the administration, then it should be irrelevant, Identification should include fields like, Name, ID number, and category for instance patient, cardiologist, General practitioner and Researcher.
After taking the preposition of the method to apply so as to come up with Hillside health information system the. Hospital management allowed a test program that would see a six moth trial of the proposed system.
It took roughly three months to program the software that would be able to accommodate vast data, with various levels of authorization and be able to make data secure, credible and available to all the necessary parties. Necessary hardware was put into place; Hardware includes the Router to connect into the net, the server, which is the main storage of all the data and switches that allow computers to be joined to the server. The system was started and tested to ascertain that the system would achieves its goal
After six moths the back up server was accessed to verify that it was duplicating all the data in the main server, all the data that was in the main server was found in the offsite back showing that incase the main server broke down no data would be lost. The issue of ascertaining the credibility of the software was done by entering wrong data into the system, for instance entering wrong fields to observe the behavior of the user
Introduction
The success of diagnosing and offering treatment does depend highly on the history of the patient’s Electronic Health Records (HERs), (HERs) is currently the most suitable solution to medical records, Electronic health records are flexible (Mor, 2008, 4) they have capacity to evolve with the requirements of changing time, however challenges are posed by the ever advancing malicious techniques, In the medical world records are crucial even more crucial is record management. Data security, credibility and Authenticity are elements that cannot be compromised in critical institutions such as hospitals (Sebastian, 2011, 3).
Privacy of data in Hospitals can not be implemented without putting the issue of data security into consideration. Data security has increasingly become more efficient with the advance of technology in the Information Technology industry; even though there is no Information system that is full proof the current technology putts immense complexity on malicious systems or individuals that might have the intention of breaching security. Health data in most cases is confined within particular structures that can only be accesses within a health facility, to make data distribution effective it calls for centralization of health records which allows multiple institution to access patients’ data enterprises with the relevant expertise carry out this task (Terry, 2005, 5), it also allows patients to have the right to add data about their own health status, it makes it some form of a personalized health record, It is clear here that the patient has acquired some form of control over their personal data, with this wonderful innovation comes some level of exposure because it means that the full control by health professional is a thing of the past, hence a loop hole for malicious attack is created.
Some of the regulations that govern how data is to be managed states that data must of integrity and should also be available, with this in mind it is easy to conclude that this rules are important for enterprises that manage health records, however it should not be forgotten that in the process this data is of extreme importance, that extreme caution should be practiced as far as the issues of confidence and integrity are concerned, faulting on these issues could be fatal, however data availability is as crucial just as integrity is because multiple institutions need comprehensive history of their patients regardless of where data of a patient was corrected. With all of this in mind then it is clear the enterprises managing this data should have no privileges of particulars of a patient, only authorized medical practitioners and the patient should have access to this data, the responsibility of enterprises should only be to ensure that medical data is centralized and that it is not accessible by non authorized parties, Regardless of whether data is restricted to authorized entities there is still a loop hole that data from different sources can be combined to gain information about an individual.
Hillside hospital desires to develop its own health information system which will fulfill security requirements of the hospital, though this project is unique to the hospital the requirements are similar to any other hospital and its dynamics are similar to what is discussed above.
Literature review
To understand clearly how a security system is to be developed it is important to understand the security threat and where these security threats come from (Collmann, 2005, 2). Security threat in database systems arise from various sources; there are natural sources that human beings have no control over like lightening and earthquakes (Martin, C. 2010), there are human threats that are caused by malicious individuals and also non-malicious without any wrong intent for instant entry of wrong data into the database (Andrew, 2007, 4), there are threats that come from the environment that entail occurrences like chemical leakages, and pollution.
Developing an analyzed listing of threats is important so as to come up with conclusions of what is to be included in designing a security information system (Ganthan, 2011, 6) considering what activities take place and what their results are can be used as basis for producing an analyzed list of threats, activities can include observation, destroying, modifying, emulation of threats. Results can be disclosure, wrong presentation, and threat of repudiation, compromised integrity and execution Gianluigi, 2007, 5). From these security threats can also be put in the categories of interruption, fabrication, modification and interception, assets that are involved can be use to develop these categories.
In addition security threats can be viewed from two perspectives, one is the agents of threat agents of threat lay under authorized and non authorized user and factors of the environment and the second perspective is the techniques applied in penetration which cloud be related to personnel, software, hardware and procedural (Guy, 2008, 2). Some other studies have identified other categories like, intentional attacks on software, human error or human failure, failing hardware/errors, natural occurrences, and obsoleteness of technology (Gary, 2005, 2).
In some related work, looking at a research done by Mor Peleg whom referred to what Welch, an M.D. working in Massachusetts General Hospital in Boston, had stated that “Insurers use identifiable medical records for risk rating, employers use them for hiring and firing, health systems for quality assurance, pharmaceutical firms for marketing, banks for assessing loan risk, and the government for the detection of fraud.” There are other stake holders that have interest including, personnel in hospitals and physicians that give primary care, member of families, physicians in various expertness, workers in labs, Institutions of health and also pharmacies(Mor, 2008, 2)
In regard to this views Mor Peleg’s research was focused on developing an approach and also a method that would maintain privacy in the health care sector, and also at the time maintain a balance between the requirement of preserving patient privacy an also see that the quality of medical service provided is of high standard.
Literature relating with the issues of privacy can be categorized into three divisions
- Preservation of privacy by protecting identity e.g. voice recognition system
- Preservation of privacy by anonymity,
- Preservation of privacy by access restriction
Mor Peleg‘s research is based on the third category, he wished to attain preservation of privacy by access restriction. To achieve this he had interest in identifying where there were scenes of access request. Scenario being a specific process of description for requesting data of a patient. He expresses scenario in a way that is semi-formal, way of interruptible computer. It allows the protection of the patient’s privacy by exposing only individual’s data that in only relevant to a particular given case(Mor, 2008, 2).
His approach took into mind that the decision to reveal the data of a patient was affected by numerous facts that included the situation access of a patient’s data, and one of this of course is the party that requests for the said data, this alone is not the only factors, so he called his research situation-Based Control (SitBAC), Mor Peleg‘s research included abstracts for modeling of entities that were involved in a situation- patient, requestor of data, Tasks, Authorizations that are legal, Electronic Health records and along Response together with some other attributes and their relationships, arguing that by using health data that were related. SitBAC focused on scenarios, instead of making use of a model that focused on roles.
The research argued that it would result to better coverage of the numerous privacy issues of which organizations in the health care sector were expected to handle. Therefore SitBAC was likely to also improve the outcome of issues of privacy. Mor Peleg‘s model of access control model was deigned to enable actualization of an organization’s policies. From modeling data access situations, he was able to achieve specifications that were detailed concerning various data accessing situations. Models that were obtained were precise hence able to serve as a foundation by which organizations could implement their policies upon, stating who should do what, for instance the particulars of a patient can be made available to a specialist who requires to treat only if a referral has been administered to the said specialist and also if the said specialist is accessing data in his normal place of work. Mor Peleg‘s built scenarios like this, he was able to maintain the patient’s privacy an also enabled high quality care provision (Mor, 2008, 2),
In Mor Peleg‘s work he used two research methods, the methods included qualitative that would elicit the required data, the other was modeling conceptually so as to develop structure and give specific scenarios, Mor Peleg‘s Long term goal was to make the model of SitBAC a knowledge base situation, so that every new request for access would represent a situational instance, which would be compared with knowledge based situation with the aim of determining if the request could be granted or if it would be declined
Mor Peleg‘s research was motivated by privacy preservation while gaining access to EHRs(Mor, 2008, 2).
In another related literature, Jun Choe’s Research argues that health data that is managed on the internet requires extensive focus on offering secure data, this is to prevent intrusion form malicious sources, and also be able to uphold the introduction of health record requirements to make it possible to for heterogeneous repositories that are held at various Health care institutions.
Jun Choe research he proposed a multi-agent model that would access health data over the net from heterogeneous repositories that were multiple. His proposed system was organized into a four entities that were of an integrated architecture that consisted of applications that were client based consisting and a central control (server) for accessing and access control systems that were local and information systems in hospitals. He used extensible Markup Language (XML)and the role-based access control (RBAC) systems that were put together for an effective management of repository, Jun Choe did this by providing methods that were for access control, exchange of information, authentication of users, integrity of data and encryption that was selective(Jun, 2008, 1)..
Jun Choe’s research achieved a multi-agent model by applying XML. And Role based access- control and able to connect the heterogonous repositories with different standards and different policies of hospitals and they were able to interact securely. For instance an authorized client would be confirmed and given accessing privileges, would have the capacity to retrieve relevant data in an XML-bases mutual data format with embedded privacy(Jun, 2008, 1).
Jun Choe’s research is only useful in internet based exchange of health data that are reacted to cooperative healthcare and creation of lifetime health data.
Deducing from these two researchers it is clear Hillside hospital only requires internet to connect to the Hillside Medical centre hence an elaborate internet structure is not necessary because only data is confined within the same institution this calls for a simpler model, suitably like that of Mor Peleg, which supports preservation of privacy by access restriction. To achieve this he had interest in identifying where there were scenes of access request. Scenario being a specific process of description for requesting data of a patient. He expresses scenario in a way that is semi-formal, way of interruptible computer. It allows the protection of the patient’s privacy by exposing only individual’s data that in only relevant to a particular given case. This is clearly what Hillside Hospital desires to
Risk Management
Risk comes from all the exercises that are vulnerable, probability and the effects of occurrences are used to reduce these risks (Jun, 2008, 4). In developing a system such as Health information security, motivation arises from risks that are eminent as far as management of data is concerned. The process of eliminating these risks while building such kind of a system should be analyzed carefully (Terry, 2005, 6).
The objectives of having a risk management analysis is to make the goals of an organization or an institution to be achieved (Jingyue, 2008, 5), this is done by ensuring better security as far as IT is concerned, giving the institution’s or organization’s management well informed decisions of risk management by showing the rationale of estimated budget on IT and by enabling the management to give proper authorizations to an IT system based on the support of the resulting documentation.
Risk management targets the top management officials that make the final decision on the security budget of IT. The teams responsible for the last decisions of whether to allow an information system to operate, the program manager, the team responsible for the security of IT, owners of hardware or software, owners of the data, the team in charge for procurement process for IT, the technical team, the system programmers. Quality assurance team, IT system auditors, system consultants (Lu-Chou, 2009, 5).
Putting into mind the requirements for setting up such a system then it is possible to come up with a conclusive risk management analysis. Requirements here will include, development of a customized software to fit the requirements of Hillside Hospital, Hardware to carry the software, skilled personal to maintain the system, from these requirements it is possible to deduce how to handle risks associated with management,
As far as software development is concerned, a software programmer has to be acquired to design the system the risks associated with this is that the developer might, have the right of property if no license is issued by the programmer, The system developed by the programmers might not be compatible with machines, the developed system might prove to be non user friendly if the after the completion of the project, The system might develop complications long after the system has been tested. As far as hardware is concerned the, skill is required to understand hardware that are compatible, If any hardware breaks down, or is not compatible the entire network might not work well, personnel without relevant IT knowledge can recommend rectification of the entire system, where else that is clearly not necessary. The users of the system might view the change negatively and find it hard to work with the system.
Methodology
The requirements of the Hillside hospital for a Health information security can be clearly drawn by looking at its activity structure. For instance there are various specialist and allied health providers in the hospital that work in different departments, there are general practitioners from the Hillside Medical Center that can admit their patients to the Hillside Hospital and there are also staff members in the hospital that are involved in medical research and clinical trial and they also need to use patients information from the system, sharing the data of its patient is crucial to facilitate diagnosis for its patients.
From this kind of a setup it is evident that Hillside Hospital is not a big project compared to large scale or state hospitals hence reduces the level of complexity to be applied in developing the a health security system.
The practitioners associated with the Hillside hospital need to share their patient’s data for the sake of wholesome diagnosis and proper research to be carried out by the staff members that are involved in medical research and clinical trial, in doing so, security, integrity and availability of data should not be compromised.
What is required is a system that only allows authorized parties to access data; this system should have the capacity to account all activities that take place, where they take place , when they took place and who did what, to increase accountability and responsibility among its user. Different levels of access authorization should be issued differently for instance, a patient has only the authorization of accessing his or her own details and can add any necessary information, specialized practitioners to be given authorization to access any data and be able to add data to the existing data, the general practitioners in the Hillside health center should be given authorization to access data for any patient but no capacity to manipulate data in any way, allied health workers in the hospital should only have access to data and no capacity to modify any. For the staff members in the hospital that are involved in medical research and clinical trial should have access to the data and no capacity to modify the data in any way, a small unit within the main unit can be used for research purpose that the staff involved medical research can be able to store there work.
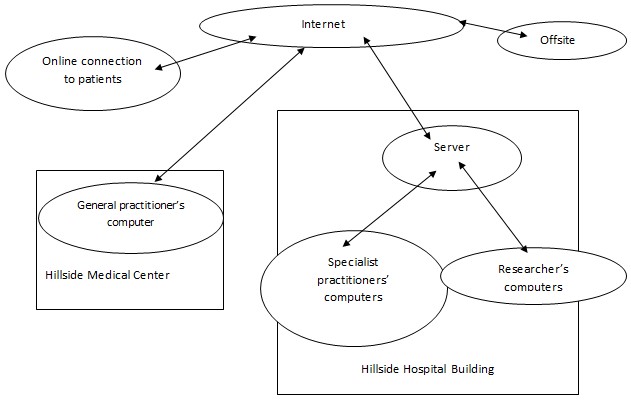
Hillside Hospital requires a small structure that allows the Hillside Medical Center to access data from the Hillside Hospital, the rest of the personnel requiring this data are within the Hospital building. This means a main server should store all the data, for the sake of centralization an offsite back up system (A duplicate server that contained similar data in a different secure location in case the main server fails ) should be implemented this server should have links to the internet with a fire wall which can be used to allow Hillside medical Centre to access the required data, the rest of the practitioners should have computers that connect to the main server connected using an Ethernet connection by a using a cabling system.
For the sake of Identification the hospital administration should be the only with one with the right to issue IDs, if Identification is not issued by the administration, then it should be irrelevant, Identification should include fields like, Name, ID number, and category for instance patient, cardiologist, General practitioner and Researcher.
After taking the preposition that detailed what method to apply, so as to come up with the Hillside health information system, the Hospital management allowed a test program that would see a six moth trial of the proposed system.
It took roughly three months to program the software that would be able to accommodate vast data, with various levels of authorization and be able to make data secure, credible and available to all the necessary parties. Necessary hardware was put into place; Hardware includes the Router to connect into the net, the server, which is the main storage of all the data and switches that allow computers to be joined to the server. The system was started and tested to ascertain that the system would achieves its goal
Results
Six moths later after the system had been tested, various activities were carried out to ascertain that the system had achieved its objectives, these activities included, Verifying that the back up server was functioning optimally, testing the credibility of the system, Carrying out interviews asking all the relevant personnel involved questions relating to the functionality of the system.
After six moths the back up server was accessed to verify that it was duplicating all the data in the main server, all the data that was in the main server was found in the offsite backup system , showing that incase the main server broke down no data would be lost. The issue of ascertaining the credibility of the software was done by entering wrong data into the system, for instance entering wrong fields to observe the behavior of the user interface. It was found that the system could not accept wrong data into the system also the system could not allow entities that were not given ID by the administration could not be allowed in to the system. Interviews carried out included talking to patients, the question asked were, if they could access their data and if they could edit their data, there was no negative answer meaning that the system worked just fine as long as patients were concerned. The general practitioner were asked if they could access their patients data and if they could modify it, their response was, they could access necessary data from the Hillside Medical Centre but could not modify it in any way. Specialist practitioners confirmed that they could access their patients’ data and that they could modify it, the researchers confirmed that they could access patients’ data but could not modify it.
Discussion
The desire for Hillside to come up with a health security system is well aligned with the ever evolving world of managing data; IT has become the foundation of managing data in today’s world. Old methods preserving data are way overdue and over stretched (Mor, 2008, 4); IT has seen a major paradigm shift in the way data in the health sector is being managed. Using IT to manage data has made it easy to access records from centralized location to various health facilities; this has boosted the health service capacity to offer unbeatable level of diagnosing of patients. Health Information systems have revolutionized how and who has a say in patient’s data, Today patients have access to their own health records and have the capacity to modify their data accordingly. However the world of IT is created by man and that means that a human has capacity also to find its weakness and use it to cause harm to others, with this in mind then the issue of data security is critical.
It is from this deduction that it is safe to suggest that Hillside Hospital has perceived this and requires a system that offers assurance that the records of the hospital are safe and credible at the same time without limiting accessibility to its data. Sharing of data will be beneficial both to medical practitioners in the hospital and the patients. The hospital is likely to see better response from the patients and limit time required to inquire into the history of a patient, the patients coming into the Hospital facility might find it better to receive diverse health services from the same hospitals because of the feeling of an integrated system that gives their history to the various practitioners regardless of the department of service
From the results it is clear that this kind of system will be effective in achieving the objectives for installing a Health information system. It will be much easier for the various health specialists to be able to diagnose their patients. The data security will be maintained because of the hardened platform of accessing data, data security will be assured whether an attack comes from human or environmental factors, there is a back up system that can be used incase the main server fails. Researchers in the Hillside Hospital can access data easily and it will remain unaltered.
Therefore Hill side Hospital’s Health information security is functional and is fully applicable. Hence it is recommendable to initiate the a trial phase that runs parallel to the old system, as a measure to ensure that it runs well and that in comparison to the old method of data management it has more advantages.
References
Andrew, D. 2007. An’Honest Broker’ mechanism to maintain privacy fir patient care and academic medical research. Miami: Elsevier.
Collmann, J. 2005. Assessing information security risk in dual-use health information systems. Georgetown. Elsevier.
Ganthan, N. 2011. Security threats categories in healthcare information systems. Wollongong: SAGE.
Gary, S. 2005. Recommendations of the National Institute of Standards and Technology. Gaithersburg: NIST.
Gianluigi, R. 2007. Chief medical officer actions on information security in Italian rehabilitation Centre. Milan: Elsevier.
Guy,P. 2008. Prioritizing Clinical Information Systems project risk factors: A Delphi Study. Montreal: HEC.
Jingyue, L. 2008. A State of the practice survey of Risk Management in development with off the shelf software components. Trondheim: IEEE computer society.
Jun, C. 2008. Web- based secure access from multiple patient repositories. Korea: Elsevier.
Lu-Chou, H. 2009. Privacy preservation and information security protection for patients’ portable electronic health records. Taipei: Elsevier.
Martin, C. 2010. Defense mechanisms.London: The definitive guides,
Mor, P. 2008. Situation-Based Access Control: Privacy management via modeling a patient data access scenarios. Haifa: Elsevier.
Sabastion.H. 2011.Aspects of privacy for electronic health records. Freiburg: Elsevier.
Terry, L. 2005. Information security policy’s impact on reporting security incidents. Huntington: Elsevier.