Introduction
With the nature of the information handled by Metropolitan Police and the number of staff authorized to access this information, there is a great need for the institution to ensure that every staff has access only to the information he or she is authorized to access. Identity and access management is vital in the institution due to numerous intrinsic shortfalls associated with information sharing. This underlines the need for the institution to strongly dedicate its time to ensure that they have produced a viable management system. This will ensure secure storage and access of information by all staff.
Reasons for managing multiple identities
The department responsible for ensuring the security of stored information has to bear in mind the ever-evolving problems associated with controlling information use as well as ensuring user accountability. With the presence of different databases storing varied information in the Metropolitan police service (MPS), those who access this information must do it efficiently and at their specific levels of authorization.
Without appropriate management of information access, the security of the institution’s information, as well as personal information for particular staff, would be significantly compromised. The institution needs to critically address the varied challenges attributed to a massive amount of information access as well as user authentication. This goes spontaneously with challenges attributed to assigning multiple passwords to information users.
Employing new technologies such as identity integration, the organization can be able to integrate multiple identities leading to a fast and more dynamic working environment. Introducing a single sign-on mechanism can help the organization in bringing together the different passwords hence eliminating the need for staff to remember many passwords. This would not only help in controlling access to information but also physical access to offices within the organization (Oracle Par. 3-8).
Identity administration through an integrated approach will help MPS in addressing employees’ lifecycle for the case of those who leave, join or get promoted within the institution. For instance, if staff are removed from the remuneration list, their usernames will be automatically removed from the database hence denying them any further access to the organization’s systems. Using multiple passwords poses several security vulnerabilities to the Metropolitan police service. Since staffs have to always remember the passwords, some might opt to write them down or leave their systems unclosed for faster entrance to the system.
Other staff may use this opportunity to access information from these systems. In case of misconduct, these events have severe effects leading to innocent employees being punished for mistakes done by their fellow workers using their identity. The cost incurred by the organization in managing information as well as supporting infrastructure is also drastically reduced. Employees can be able to carry out their operations quickly and securely. Their efficiency would be greatly improved due to the reduction of password related problems as well as time wasted while employees wait for the password to be reset (Edmondson Par. 1-10).
Biometrics
Biometrics are automated modes of identifying a person concerning physiological or behavioural properties. Some of the physiological properties considered include hand or fingerprints, iris detection and facial appearance. Dynamic signature confirmation, voice recognition and keystroke variations make some of the behavioural properties considered. Authentication through this technology requires comparing already collected biometric tests against newly acquired samples.
The biometrics properties of an individual are then stored in a database and used for identification purposes. Through the biometrics method of authentication, the Metropolitan police service would be able to control the way its staffs access the stored information. Supplementary methods of substantiation such as snap ID cards, Magnetic bar cards, smart cards and others can be misplaced, stolen, easily replicated or even unconsciously left at home. Biometrics provides a remedy to these problems (Globalsecurity.org Par. 2-7). Even though the technology consists of numerous authentication instances, the procedure is quick and easy to a degree that users are not troubled by the process. MPS would also be able to reduce challenges faced in providing multiple levels of authentication.
Biometrics can cater for both physical and logical access thus protecting staff from logging into the organization’s systems when out of duty. Some of the biometrics used includes iris recognition, fingerprints and voice recognition. Biometrics technology ensures that each person has one and only one identity. This ensures that only one person can access this identity hence reducing cases of repudiation within the organization. This would ensure that all the Metropolitan Police service staffs are responsible in their daily activities within the organization as it is possible to track anyone involved in malpractices within its systems.
Cases of staffs’ conspiracy would be greatly reduced. Staffs efficiency would also be enhanced by using biometrics due to fast access to the system. This is because as staff might forget their passwords or smart cards, fingerprints or iris will always be readily available. It is also possible for MPS to limit its staff to only the information that pertains to their areas of specialization. This would help in handling sensitive documents within the organization by allocating them to specific staff (Volner and Bores pp.55-57). The following diagram shows some of the procedures followed in authenticating a person using biometrics.
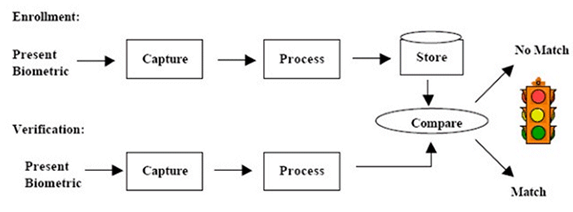
Iris scanning
Iris-scan uses various unique features of the human iris in confirming a person’s identity. A special camera that uses an infrared imager is used to take photos of one’s iris. The inner part of the iris is positioned by an iris-scan algorithm which outlines the unique figures and features of the iris. An algorithm is a set of commands that directs biometric systems on how to construe certain problems. The method is highly immune to identity theft and false matching. Statistics show that the acceptance rate for false iris identification is one for one and a half million people. The efficiency of iris recognition is rarely impaired by glasses or contact lenses.
Due to its fast comparison speed, it is suitable for one-to-many classification. As the technology stores personal data in a database, it is possible for MPS to hold a huge amount of data within one database as the organization grows. This does not require the organization to alter any of its infrastructures as the system performance is not compromised. There are different software that supports the technology on both stand-alone computers and networked computers. With this, MPS is saved the cost of having to purchase software for each computer. The technology is also fast in authentication hence saving the company a lot of time that could be wasted while trying to insert passwords that might have been forgotten (Daugman pp.21-30).
Fingerprints
The fingerprint authentication method is another biometric technology that is widely used. It has proved to be the most advanced method of all the available biometric technologies. This is because as most other personal features change with time, fingerprints remain unchanged throughout one’s life. Also, it is possible to take fingerprints and digitize them using cheap devices. The fingerprint identification method involves two important steps which are registration and authentication. Fingerprints samples are taken and stored in a database. Various features of the fingerprints are then identified to uniquely classify the owner.
The corrected fingerprints are compared with already existing fingerprints within the database to ensure that they are unique. The stored fingerprint information is then used to identify people by matching their obtained fingerprints with what is stored in the database. The result of the matching process is whether the input fingerprint is similar to one stored in the database or not. The precision of the matching process is determined by comparing the rate of rejection and acceptance (Raviraj technologies Par. 2-6).
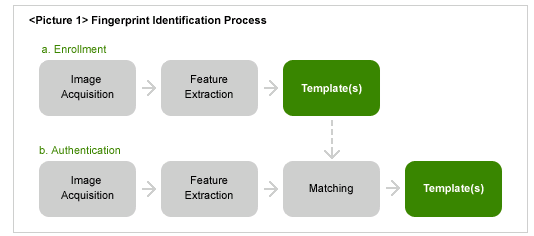
Bearing in mind that MPS is subject to growth, the technology would be of great benefit due to its scalability. Various software has been developed that is possible to use on both personal computers and computers connected in a Local Area Network (LAN). For instance, Tutis Technology has developed software that uses fingerprint authentication methods. The software is capable of supporting a wide number of computers within a network. Fingerprint authentication technology allows secure data transfer through data encryption. For the data to be decrypted, one has to provide his or her fingerprints for authentication. The technology would help MPS from loss or alteration of data on transmission. The technology does not require staff training as they are only required to produce their fingerprints and can access the system.
Difference between biological identity and multiple digital identities
Digital identity refers to an online depiction of someone within a community. It is what people use to identify themselves to acquire the right to access information stored online. A person may have numerous digital identities in a range of databases. As digital technology improves, many people are coming up with numerous identities for various uses. On the other hand, biological identity refers to the unique characteristics exhibited by an individual and used in identifying that person. These characteristics include hair colour, fingerprints, iris properties and others. The problem arises in managing these multiple digital identities.
Identity management entails the process of purveying and synchronizing digital identities. For instance, an officer in the Metropolitan police service working in a computer crime department might have one digital identity for accessing the information on crimes committed through computers. As the same officer participates in normal police duties when not in a computer crime department, he or she might have a different digital identity for accessing other information relating to normal operations. Controlling these identities becomes a problem. To help this, the officer can use biological identity. This identity uniquely identifies a person without having to provide different identities for every department. It is also possible to assign different levels of information access to officers who work both in the computer crime department and as normal police officers (Al-Khouri and Bal pp. 361-367).
Public key infrastructures (PKI)
Public key infrastructures provide security mechanisms like confidentiality, reliability, validation and non-repudiation. To effectively use this security method, the Metropolitan police service needs to establish a supporting infrastructure. The technology provides mechanisms for data encryption and digital signature which helps in ensuring proper authentication and security of the stored data. The digital signature helps in ensuring data integrity.
If the receiver can identify the sender’s signature, then the receiver knows that data was not altered. Through data encryption, the Metropolitan police service would be guaranteed the security of its sensitive information during storage as well as when on transmission. Public key infrastructures provide functionalities that reduce the threat of deliberate and inadvertent compromise and modification of data. The technology supports user provisioning helping organizations manage a large number of users at a lower cost. PKI works well with other digital identity mechanisms that provide for provisioning in managing users identities.
This helps in maintaining uniform security across users and systems. Public key infrastructure has been designed to meet the needs for large scale distributed authentication. Through its implementation MPS can be able to avert the cost incurred in establishing and maintaining passwords for all its staff. The infrastructure provides users with a tool that facilitates in production of a pair of mathematically associated keys: the private and public keys.
The public key is availed to any user who wishes to use it and can be stored in any database or computer. Private Key on the other hand is assigned entirely to its owner and can not be used by other users. When one is sending information, he or she includes the recipient’s public key. Information can only be then decrypted using the recipient’s private key. This would ensure the confidentiality of information transmitted within MPS. For various authentications required within MPS which includes logging into the system, signing of documents digitally and ensuring the security of e-mails being transferred, there is a need for the organization to have a scalable system (Shinder Par. 3-6).
PKI supports this as the organization can achieve this through the use of multiple certification authorities (CA). This can be attained by establishing a hierarchical form of PKI. Here MPS can have a topmost CA acting as the master and the others acting as subordinates. The master CA then authenticates all the subordinate CAs which then assigns certificates to end-users. There are various certificate services available for use by different organizations. MPS can use enterprise CA. This technology requires the organization have a directory where all people using the organization’s system have their accounts.
As the organization grow, MPS can come up with varied master CAs comprising of multiple hierarchies. The technology can also help them authenticate other systems that are not members of the hierarchy through the use of independent CAs. With different staff being transferred from their initial lines of duty, there is a need for the organization to change their system access authentication. PKI supports the scaling up of the certificate revocation by providing a list of revoked certificates that are updated regularly (Storch Par 5-7).
As the technology encrypts transit information, it requires users to provide a clear identity as well as providing a digital signature for data integrity, it has proved to be the most secure means of transferring classified information. Unlike in situations where hackers can download information on transit and access users’ passwords, it is hard to access passwords from encrypted data within PKI. This is because the technology uses a private key that is never transmitted across the network hence hard to attack it. In case hackers attack the system, they are incapable of gathering enough information that could help them access protected sites within the organization. The database used to store authentication information of all users does not store users’ private keys making the technology more secure.
With all the benefits acquired through the use of cryptographic techniques, the government can rest assured that their sensitive information will be relayed with minimal interruptions. This underscores the need for Metropolitan police to use this technology in all its communications within and without the organization.
Works cited
Al-Khouri, A. M. and Bal, J. “Digital Identities and the Promise of the Technology Trio: PKI, Smart Cards, and Biometrics.” Journal of Computer Science 3.5 (2007): 361-367.
Daugman, John. “How iris recognition works”. IEEE Transactions on Circuits and Systems for Video Technology 4.1 (2004): 21–30.
Edmondson, Paul. “ID cards and access control: addressing the problem of digital identities in the NHS.” 2008. Web.
Globalsecurity.org. “Biometrics.” 2009. Web.
Oracle. “Segregation of Duties.” 2008. Web.
RaviRaj Technologies. “Iris Recognition Biometric Authentication Information.” 2007. Web.
Raviraj technologies. “Biometrics Fingerprint Technology.” 2009. Web.
Shinder, Deb. “Build a scalable Public Key Infrastructure.” 2005. Web.
Storch, David. “Technology Brief: Public Key Infrastructure (PKI)-A Primer.”2002. Web.
Volner, R. and Bores, P. “Biometric Techniques in Identity Management Systems.” Electronics And Electrical Engineering 7.95 (2009). Web.