Introduction
Nowadays, airport security can be regarded as a challenge and an issue (Kaufmann, 2016), which governments and researchers all over the world attempt to resolve with varied success (Bonfanti, 2014; Stewart & Mueller, 2014). Apart from the challenge of security, which is difficult and costly to achieve (Stewart & Mueller, 2014), the unintended consequences of the practices used in the area need to be taken into account (Kaufmann, 2016). In particular, the issue of balancing security and privacy is very acute (Bonfanti, 2014; Mitchener-Nissen, Bowers, & Chetty, 2011). It is noteworthy that privacy is actually a part of security, which highlights the importance of its consideration (Kaufmann, 2016). The complex problem of finding the way to ensure airport security while also protecting the privacy of airport visitors is going to be considered in this paper.
A common means of improving both the safety and privacy protection of airport visitors is technology, but it is apparently not enough. Specialists may be optimistic in their assessment of technological possibilities (Mitchener-Nissen et al., 2011), or they may be wary (Kaufmann, 2016), but in any case, they highlight the fact that technology requires appropriate policies that can ensure safety and protect dignity (Bonfanti, 2014; Kaufmann, 2016; Mitchener-Nissen et al., 2011). It may be suggested that modern technologies can contribute to the improvement of the situation if they are combined with reasonable policies that are developed with attention to and respect for human dignity. While the focus on dignity and privacy instead of security may appear precarious, modern studies suggest that the current focus on security is not only potentially harmful (Kaufmann, 2016), but might be not entirely necessary (Stewart & Mueller, 2014). As a result, the present paper advocates for a slight but meaningful shift in the focus while acknowledging the importance of both security and privacy and identifying technology as an important vehicle for change.
Airport Security: Global Societal Problem
The notion of airport security can be included in that of the war on terror, which dates back to the tragedy of September 11, 2001 (Leese, 2015; Stewart & Mueller, 2014). It is noteworthy that terrorism did not appear in 2001; in fact, the word was first used to define violent activities by Robespierre (Edwards, McMenemy, Stapley, Patel, & Clasper, 2016, p. 1). However, the events of September 11 served to demonstrate the importance of airport security to the world and attracted the public attention to it (Stewart & Mueller, 2014).
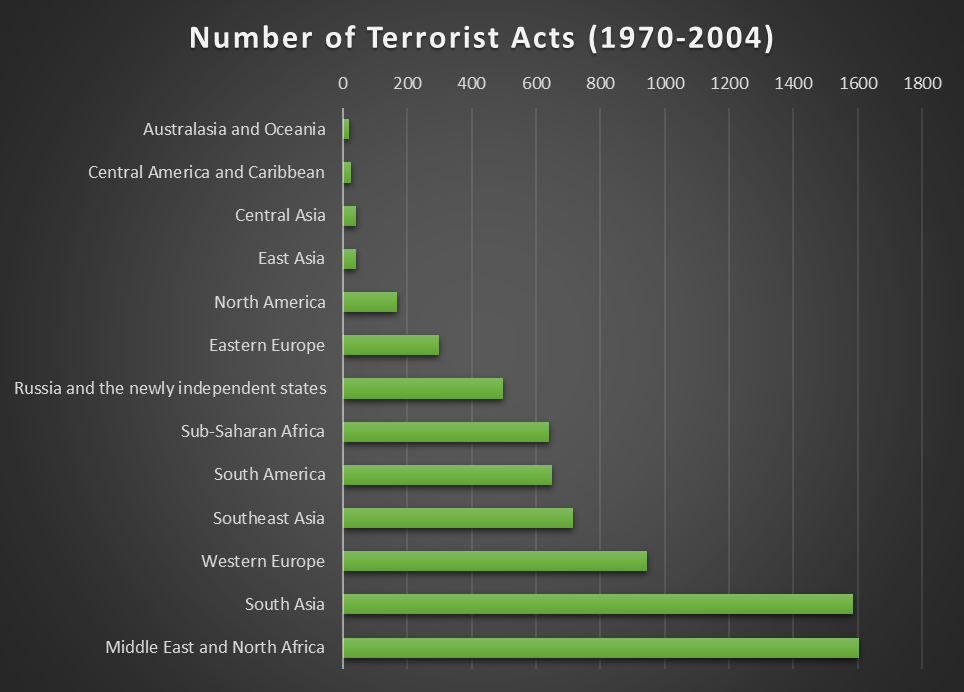
The problem of airport security, just like that of terrorism, is a global one, even though some regions (especially the Middle East) are more prone to attacks (Gao, Guo, Liao, Webb, & Cutter, 2013; Edwards et al., 2016). Hardly any region is immune to attacks, however (see fig. 1). For example, between 1998 and 2011, 51 airport-related attacks that resulted in the total of 64 deaths took place in the US and Europe (Stewart & Mueller, 2014). As a result, airport security is one of the globally acknowledged issues that are specifically considered in domestic security programs (Bierwisch, Kayser, & Shala, 2015).
According to the National Consortium for the Study of Terrorism and Responses to Terrorism [START] (2016), terrorism presupposes violent acts that are aimed at “attaining a political, economic, religious, or social goal,” violating the International Humanitarian Law in targeting non-combatants, or intimidating and attracting the attention of people other than victims with the goal of manipulating them into doing or thinking something (p. 2). The security measures that can be employed by airports to protect them from all these activities include construction- (for example, the layout of the lanes or the use of shatterproof materials), equipment- (for instance, body scanners), and personnel-related ones (SWAT-standards training for police, for example) (Stewart & Mueller, 2014). Thus, the dependence of airport security on research and technology is apparent.
Airport security can be considered from different points of view. From the point of view of governments, security is a significant priority, and modern practices clearly show that it is valued over privacy or dignity (Bonfanti, 2014). At the same time, the marketization of security takes place: private firms grow to dominate the area, which, from the neoliberal point of view, is a positive phenomenon that introduces competition to the area (Leese, 2015). In other words, airport security is increasingly becoming a business, which means that governments’ control over it slips. Unfortunately, from the utilitarian point of view, the phenomenon has negative consequences, including a chase for downsizing and other methods of cost-cutting, which might result in understaffing and tends to transform some of the security jobs into low-paid ones; overall, the process is likely to negatively affect the quality of security (Leese, 2015).
From the public point of view, security measures are a necessary evil, which people are willing to tolerate to a point. The point is specific for every person, but negative experiences that are related to airport security measures are a common issue (Bonfanti, 2014), which significantly decreases customer’s satisfaction. Given the fact that the latter is extremely important for a marketized airport, the solution of the challenge of finding the balance between security and privacy is not only an ethical but also a profitable thing to do. Finally, it is necessary to remember that the protection of privacy is an important part of ensuring the security and safety of civilians. As pointed out by Kaufmann (2016), modern security measures often result in insecurities that are caused, at least in part, by neglecting the value of protecting privacy. Thus, the notion of privacy is not limited to those of dignity and comfort (even though they are important); it is also an essential component of safety and security.
While it is apparent that airport security is a significant and global concern that calls for security measures, the question of whether these measures are appropriate remains open and is often answered negatively. Modern technologies are criticized for potential misuse and danger for privacy (Kaufmann, 2016), and modern policies are criticized for ineptitude and outdated features (Bonfanti, 2014). To resolve the problem, the following solution is proposed.
Solution
Of the solutions that are typically proposed for airport security, technology appears to be very promising. Indeed, the examples of technology that helps to improve security while respecting privacy include technological “sniffers” that substitute dogs (Bonfanti, 2014) and the introduction of whole body scanners instead of pat-downs (Mitchener-Nissen et al., 2011). Both substituted activities are admittedly capable of infringing one’s privacy and psychological comfort, which is why Bonfanti (2014) points out that airport customers are more likely to favor technological interventions than traditional ones. At the same time, both inventions have a greater potential for security improvement than the traditional approaches.
Also, the public opinion is of importance: the delays that are caused by security checks negatively affect customers’ perceptions of the quality of airport service and, apart from that, invasive activities (for example, pat-downs) cause discomfort and dissatisfaction (Mitchener-Nissen et al., 2011; Stewart & Mueller, 2014). It is noteworthy that the majority of customers recognize and acknowledge the need for security measures, but they demonstrate greater willingness to engage in activities that are less time-consuming and rude. In particular, the study by Mitchener-Nissen et al. (2011) demonstrates that more than 90% of respondents prefer body-scans over pat-downs because the procedure is less intrusive and is likely to be faster. Thus, technology is an important and potent component of the proposed solution.
It should also be mentioned that even nowadays people can be wary of technology, which may discourage them from choosing to use it. This tendency is also noted and described by Mitchener-Nissen et al. (2011), and the authors demonstrate that the problem can be resolved if the customers are provided with information on the technology that they are going to use. In other words, if a policy that is aimed at providing people with some accurate and understandable information on technology is developed, this problem is going to be resolved. This example is only one illustration of the way correct policy can improve technology use.
Unfortunately, technology is not a panacea. Moreover, technology is a tool that can be used for positive and negative purposes. Kaufmann (2016) deduces that the negative and unintended consequences of the use of security technology are predicted by the actors and their purposes as well as the rules that define its use and the extent to which these rules can be bent. The author also mentions that surveillance is among the technologies that can have significant negative effects when misused and demonstrates that the lack of privacy concerns is among the factors that make security technology more prone to producing insecurity. For example, Bonfanti (2014) emphasizes the fact that sniffer devices can and are likely to store sensitive data. As a result, a customer is rendered potentially more vulnerable by a sniffer device than by a sniffer dog. It is apparent that opportunities for misconduct are different for the technological solution and the traditional one, which requires different approaches to ensuring the security of customers.
Bonfanti (2014) studies the case oft he UK airport security and highlights the fact that the existing policies might not be applicable to technology-related issues, especially where new technology is concerned. Stewart and Mueller (2014) point out that the current approach to airport security in the US, as well as the countries of Europe and the Asian Pacific region, often cannot be called cost-efficient. In particular, the authors demonstrate risk assessment calculations that suggest an unexpected conclusion: modern airports are overprotected. While in the case of security, overprotection may be considered a reasonable decision, the authors emphasize the fact that the lack of efficiency can hardly be regarded as a positive feature, especially given the costs of airport security. Also, they refer once again to the issues of privacy and customer dissatisfaction to suggest that a revision of the modern approach to airport security might be required.
Bierwisch et al. (2015) stress the fact that the multiple drivers and barriers to technology development and adoption include societal and political factors. Therefore, policies can be regarded as a vehicle for improved control over the technology that can help to improve the quality of security and privacy protection (Kaufmann, 2016), but to this end, they need to be reasonable. From the information presented above, it can be suggested that the criteria of a reasonable policy involve its efficiency (including cost-efficiency), appropriateness (including the lack of outdated features and the requirement to correspond to the challenges of the technologies that it is supposed to control), and being centered around privacy concerns.
As emphasized by Bierwisch et al. (2015), technology should not be considered on its own mostly because it does not exist on its own: it exists in the security system as one of the multiple factors that interact with each other and produce varied effects, including that of the extent of security. As a result, a solution to the problem that is likely to improve the situation consists of two parts: the use of modern technology, which enhances the quality of service by responding to the security and privacy concerns, and the development of reasonable policies, in which privacy matters are paid particular, increased attention.
Evaluation of Evidence
The evidence that is used in this paper is gained from a governmental source that provides the most recent statistics on terrorism, multiple peer-reviewed articles, and one book published by a reputed publisher. The sources are recent (no source is published before 2011), which excludes the possibility of outdated information. The fact that the sources are reputable, recent, and peer-reviewed suggests that the evidence is reliable, even though there still may be limitations to it.
The limitations of the studies are typically mentioned by the researchers. They may include, for instance, a study that is carried out in particular country or with a sample that might not be considered sufficiently large (Mitchener-Nissen et al., 2011). Apart from that, the methodology can have inherent limitations; for example, the study by Leese (2015) is based on interviews and opinions, which limits the generalization of the results. In every source, the authors specifically mention and explain the reasons for the limitations of their works and ensure that their conclusions do not make assumptions and statements that are not supported by the evidence that they have found.
Several sources that are used in the paper contain statistics that can be interpreted to the benefit of the argument. One of the works that contributed the most to this paper is that by Stewart and Mueller (2014). It suggests an unexpected and alarming conclusion that modern airports are overprotected, which highlights the need for policy revision in the field. The authors point out the fact that the cases of airport-related terrorist attacks are relatively rare (0.5%) with attacks on aircraft accounting for about a half of those. They employ a risk assessment methodology that includes the considerations of the threats, vulnerabilities, and consequences of possible attacks, which makes their conclusion quite reliable.
It should also be pointed out that the authors acknowledge the fact that the protection of airports is of supreme importance. They do not call for leaving airports unprotected, but they invite for a critical analysis of the measures that are currently used, highlighting the fact that given the current risk probabilities, the majority of measures do not appear to be cost-effective, which is not a reasonable course of action. Apart from that, it is noteworthy that Stewart and Mueller (2014) mention being biassed against their conclusion (that airports are overprotected) and constructing their analysis by tipping the balance towards security (p. 27). Still, their calculations clearly indicate the need for reviewing the way airport security measures are perceived nowadays, and the statistics that they mention can support the results of their study.
Edwards et al. (2016) provide a statistical analysis of the terrorist activities that have occurred in the past 40 years. They extracted the information from the Global Terrorism Database, which was launched by START (2016) and used peer-reviewed medical literature to make some connections between the threat of terrorism and its impact on medicine. Among the significant conclusions drawn by the authors is the fact that terrorist attacks have been increasing in their number per year and that suicide attacks have been typically more dangerous and resulted in greater damage and deaths than non-suicide ones. The majority of incidents have been occurring in the Middle East; the region accounts for more than a quarter of all terrorist attacks throughout the studied period. Gao et al. (2013) also focus on the space-time analysis of terrorism and use the same Global Terrorism Database, which is an educational resource that provides information on the global cases of terrorist attacks since the 1970s. The results indicate that Australia and Oceania account for the least number of terrorist attacks and the North America is relatively non-prone as well while the Middle East, Africa, and Western Europe are subjected to the issue rather often.
Finally, a very comprehensive (and most recent) statistical summary on the global trends in terrorism is provided by START (2016) in its Annual Report. In particular, the source shows that the total number of attacks and deaths caused by then decreased in 20015 by 13 and 14% respectively, which breaks the previous tendency for increases in the numbers that was mentioned by Edwards et al. (2016). However, START (2016) points out the fact that the decrease is largely the result of fewer attacks and deaths in certain regions (Pakistan and Nigeria); for other areas, the changes may be less noticeable, and in some (for example, Syria, Egypt, Afganistan) countries, the numbers increased. Iraq, Afghanistan, Nigeria, Syria, and Pakistan are the five countries that are responsible for almost 75% of deaths from terrorist attacks all over the world.
Also, the ISIL is becoming more active, and the number of its attacks in Syria increased by 39%; it is currently responsible for about a third of attack in Iraq. Thus, the problem of terrorism is very region-dependent (see fig. 1), which provides some evidence to the conclusions of Stewart and Mueller (2014). Morveover, START (2016) points out that airports and aircraft are a relatively unpopular target for terrorists, and in 2015, the attacks on it decreased by 60% to 23 attacks globally, which also supports the ideas of Stewart and Mueller (2014). To sum up, it may be more reasonable to spend resources on more terrorism- and disaster-prone areas for the countries that are less susceptible to attacks. Finally, it should be mentioned that the statistics can be used to prove the idea that terrorism is a very severe issue, which means that inefficient spending is not an appropriate solution to it.
Limitations and Future Research
There are several limitations to the present paper. The sources were chosen for the paper with the intention to consider different views, including those of the government, the researchers (opposing attitudes included), and the public. However, the paper does not claim that it has constructed a full picture of the challenge, and it might be complemented with the help of additional details. It is also apparent that the present paper does not propose a detailed solution to the issue, primarily because the recent evidence that is provided here indicates that a very considerable review of current practices is required to this end. Therefore, further research in the area would include the criticism of the existing practices and policies and, eventually, the construction, proposal, and criticism of possible changes. It is a very extensive opportunity for future research that appears to have been undertaken by Bierwisch et al. (2015), Stewart and Mueller (2014) and, to an extent, by Bonfanti (2014). Also, this research is required to ensure the safety and efficiency of airport security, which highlights its importance and suggests that it is worthwhile.
Ethical Outcomes of Solution
It is apparent that the suggestion to shift the focus of policies’ attention from security has negative ethical outcomes and opens the opportunity for criticizing the approach. Human rights are a major value in modern society, but ethical theories that are based on rights may be problematic. In particular, if rights are placed above every other value, unexpected phenomena can be justified and regarded as an ethical thing, especially if the boundaries of rights are not very well-established and they do not have coherent well-established definitions. For instance, it is not atypical for the human rights to be used to justify unethical activities and even crimes. For example, freedom of expression is used to justify violence and pornography, and the right to privacy is used to prevent the society from taking action against domestic violence (LaFollette, & Persson, 2013).
As a result, the call for the protection of human privacy, for a greater consideration for human dignity can be deemed unethical and even perilous. The statistics presented above can be used to demonstrate the significance of the issue of terrorism and the need for protecting civilians. Apart from that, one might argue that the high level of security could account for the low number of airport attacks and even serve to reduce the attractiveness of airports as perceived by terrorists. However, it should be pointed out that the comparison of the proposed solution with the examples of the misuse of the notion of human rights is hardly justified. The solution does not presuppose justifying or ignoring the issue of terrorism: it looks for more efficient and humane ways of resolving it. Similarly, it is not correct to argue that by shifting the focus towards privacy, the society will necessarily trigger the slippery slope, which must eventually result in ignoring airport security: there is no intention to let the events develop in such a way, and it is hardly imaginable that any policymaker could interpret the solution in such a way.
On the other hand, the positive ethical outcomes of the solutions are apparent. The primary one is related to the greater attention that is supposed to be paid to human rights. As discussed above, human rights can be regarded as a very important value for modern ethics, especially in Western countries (LaFollette, & Persson, 2013), and their protection is likely to be considered a positive ethical outcome of the solution. Apart from that, from the utilitarian view, the maximization of human well-being is a primary value as well as the main criterion for decision-making (LaFollette, & Persson, 2013).
The proposed solution is aimed at the maximization of human well-being from the point of view of the protection of their dignity and the right to privacy, which makes it justified from another ethical perspective. Moreover, the fact that the lack of privacy protection is, technically, an issue that results in insecurities and potential for power abuse and technology misuse (Kaufmann, 2016) implies that shifting the focus to privacy is the useful and even the “right” thing to do. It is also noteworthy that the reconsideration of the policies and cost-efficiency of the methods is likely to have a positive impact on human well-being, but these aspects of the solution outcomes can be regarded as side-effects, even though they are apparently positive and well-justified from the utilitarian point of view.
To sum up, the solution is supported by at least two views on ethics while the possible negative ethical effects are mostly the result of misunderstandings and the slippery slope fallacy. The potential reconsideration of current airport security measures is extremely unlikely to result in significant damage to safety given the fact that nowadays airports are overprotected. At the same time, the advantages of returning the attention of policymakers to privacy and the stimulus to respect human dignity are likely to have a noticeable positive effect on human well-being and, indirectly, security.
Conclusion
One of the most important and difficult elements of airport security consists of balancing out the security and the privacy of the people who are supposed to be protected. Privacy is not only a matter of psychological comfort, even though this aspect is also important. In fact, the lack of respect for privacy is also likely to result in noticeable issues with security, which leads to the paradox that Kaufmann (2016) defines as insecurities created by security measures. Given the fact that the primary reason for the development of airport security (terrorism) is a global issue, the problem of balancing out privacy and security is similarly global, and the current measures that are used to this end (including technology and policies) have not managed to resolve it for the time being.
Additional research reveals that the likely obstacle that prevents these measures from being effective consists in unreasonable policies. In this case, reasonability presupposes efficiency, appropriateness, and a particular focus on human security and dignity as opposed to the current focus on security. While the solution may appear ethically ambiguous, the arguments against it are mostly caused by misunderstandings and fallacies; at the same time, the solution can be justified from the point of view of utilitarianism and human rights value. To sum up, the dilemma of security and privacy can be resolved with the help of reviewed and reasonable policies that are employed to control the use of modern, improved technologies while paying increased attention to human privacy and dignity.
References
Bierwisch, A., Kayser, V., & Shala, E. (2015). Emerging technologies in civil security—A scenario-based analysis. Technological Forecasting And Social Change, 101, 226-237. Web.
Bonfanti, M. (2014). From sniffer dogs to emerging sniffer devices for airport security: An opportunity to rethink privacy implications? Science And Engineering Ethics, 20(3), 791-807. Web.
Edwards, D., McMenemy, L., Stapley, S., Patel, H., & Clasper, J. (2016). 40 years of terrorist bombings – A meta-analysis of the casualty and injury profile. Injury, 47(3), 646-652. Web.
Gao, P., Guo, D., Liao, K., Webb, J., & Cutter, S. (2013). Early Detection of Terrorism Outbreaks Using Prospective Space–Time Scan Statistics. The Professional Geographer, 65(4), 676-691. Web.
Kaufmann, S. (2016). Security through technology? Logic, ambivalence and paradoxes of technologised security. European Journal For Security Research, 1(1), 77-95. Web.
LaFollette, H. & Persson, I. (2013). The Blackwell guide to ethical theory (2nd ed.). New York, NY: John Wiley & Sons.
Leese, M. (2015). Governing airport security between the market and the public good. Criminology And Criminal Justice, 16(2), 158-175. Web.
Mitchener-Nissen, T., Bowers, K., & Chetty, K. (2011). Public attitudes to airport security: The case of whole body scanners. Security Journal, 25(3), 229-243. Web.
Morris, N. & Slocum, L. (2012). Estimating Country-Level Terrorism Trends Using Group-Based Trajectory Analyses: Latent Class Growth Analysis and General Mixture Modeling. Journal Of Quantitative Criminology, 28(1), 103-139. Web.
National Consortium for the Study of Terrorism and Responses to Terrorism. (2016). Country Reports on Terrorism 2015. Web.
Stewart, M. & Mueller, J. (2014). Cost-benefit analysis of airport security: Are airports too safe? Journal Of Air Transport Management, 35, 19-28. Web.